
How To: Shh… How to Make Yourself a Silent Film Character for Halloween
2011's The Artist was the first silent film to win an Academy Award since 1927. It was old school versus new school, and it won in unprecedented fashion.


2011's The Artist was the first silent film to win an Academy Award since 1927. It was old school versus new school, and it won in unprecedented fashion.

Why unlock your Samsung Galaxy S3 to use with a different SIM card? One possible reason is that you love your phone, but not your cellular provider because of the poor service or an unreliable connection. If you purchased a Samsung GS3 with AT&T, T-Mobile, etc. on a contract, it might be locked for a specific amount of time called the contract period.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

If there's one way to get a visceral response from someone, it's bringing up the DMV. Regardless of the reason, whether it's the long lines, disgruntled employees, or just general inefficiency, I have yet to meet a single person who doesn't mind the trip. Just look at all those happy faces.

Unlocking your Samsung Galaxy S4 so you can use a different SIM card isn't the easiest thing in the world. In the states, unlocking cell phones was actually illegal, despite the White House's disapproval, though, a recent bill has making its way to the House floor and has made it legal again.

Why can't all electronic devices be waterproof like my watch? There are watches worth three times as much as my iPhone that I can wear into the hot tub without a worry in the world, but cleaning most of my electronics requires a lot of caution.

"What is dead may never die." That's easily one of the best lines (and episode title) from HBO's Game of Thrones series. While the saying may ring true for the Ironborn, it's not quite as catchy when it comes to batteries.
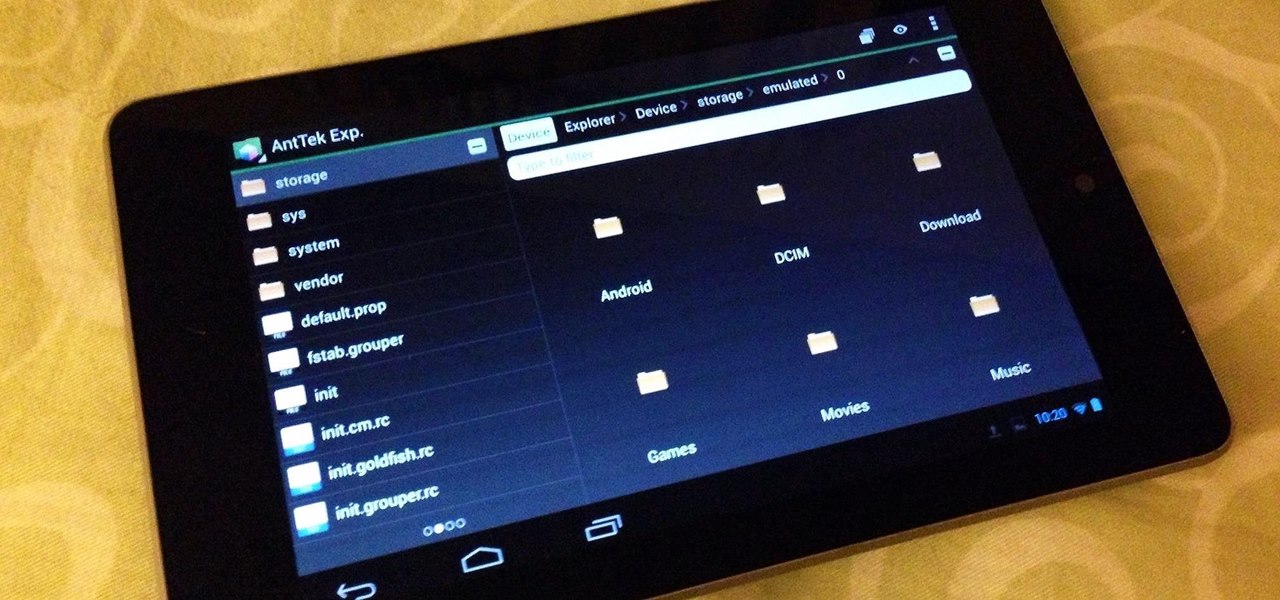
If you're always on the go, the Nexus 7 is a godsend for having everything you need at the tip of your fingers—music, videos, text documents, photos, and more. Unfortunately, as good as that is, it also means one hell of a messy tablet.

In most countries, there is one single emergency telephone number that allows you to contact local emergency services when in need of assistance. In the United States, that number is 911, which most of us know by the time we're able to speak, unless you're Buckwheat and Porky.

I spend practically all day surfing the web and writing on my laptop, and just as much time texting and checking emails on my smartphone. So, it's only natural for me to charge my iPhone using the USB port on my MacBook Pro.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Particles, such as electrons, have a property called spin which can be measured at any angle, but when measured always results in one of two answers—up or down.

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...

The Geminid meteor shower happens every December and has been observed for over 500 years. It's is also known as Winter's Fireworks because when viewed from the right location, there are enough meteors to light up the whole night sky, and some of them can even be different colors. The shower appears to come from the Gemini constellation, but is actually caused by Earth passing through the tail of dust and debris left behind by the comet 3200 Phaethon.

You may or may not care about this, but sometimes it physically upsets me when I see gears stuck together haphazardly, with no concern for whether their teeth interlock. I mean, what do you do with non-interlocking gears?

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

The cost of movie tickets in North America are currently at an all-time high, but with so many great films coming out, just not going doesn't seem like a probable option. Luckily, there's more than a few resources on the Internet to help you mitigate some of those costs.

Here's how to build a sexy looking water-fuel generator that will convert your tap water into an extremely powerful, clean burning gas!

Did you know that there's a way to start a fire by squishing air? In this project, I'll show you how to build a tool that does exactly that—and I'll give you a sneak peak into the principals of how a diesel engine operates!

So, this idea was born from a necessity to save. My household uses tissues a lot. I have two small kids, so they are extremely useful. The problem with tissues is that they seem to disappear in no time. So, whenever we ran out in-between shopping visits, my family would just use toilet paper.

Brushing your teeth is a necessity. You don't want to walk around with yellow teeth and stinky breath, and it's common courtesy to those around you to care about your personal hygiene at least that much.

In last week's guide, we covered the best places to purchase digital copies of computer games online. This week we'll cover another type of downloadable content: those available for video game consoles. Every major console out today either has or plans to have a DLC platform, but which one is the best? If you don't like leaving your house and want to play console video games, which console should you get? Below I will break down what the online marketplace offers so you can decide which conso...

Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.

Email accounts can quickly get out of control, and important emails can easily get lost if you don't have time to look at them right away. In Apple's Mail app, there's a simple way to be reminded of emails you want to read later, whether it's an email with tasks you need to complete, upcoming event details, or a message you need to reply to, and it works no matter the email account.

There's a quick way to see who you or somebody else has been chatting with the most in the Messages app for iOS and iPadOS. More specifically, it shows which conversations have the most attachments, such as photos and videos, giving you an idea of which chats are the most active visually.

There's no denying that adding more programming languages to your arsenal is crucial to boosting your career, but learning a new language in the literal sense is just as enriching and mentally stimulating. Not only will you be smarter — those who know more than one language are known to have better reasoning, problem-solving skills, and creativity — but it'll also open you up to more job opportunities.

In the tech world, our data is always under attack. When you download and install a new app, it can be difficult to know what information the app is actually accessing. Thankfully, a new emphasis on privacy in iOS 14 changes the game, exposing more of what your apps want access to — and even changing some behavior along the way.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Anything from work or a missed flight to a worldwide pandemic (COVID-19, anyone?) can make it difficult or nearly impossible to see your loved ones. You can make phone calls or send iMessage, text, or email messages, but nothing compares to seeing family and friends right in front of you. That's where FaceTime comes in.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now.
The Pixel 4 isn't for everyone, but it does have its appeal in several specific use cases. Thanks to Instagram, YouTube, and other social media platforms, the fitness industry and smartphone world are now intertwined like never before, and it appears Google's aware of this.