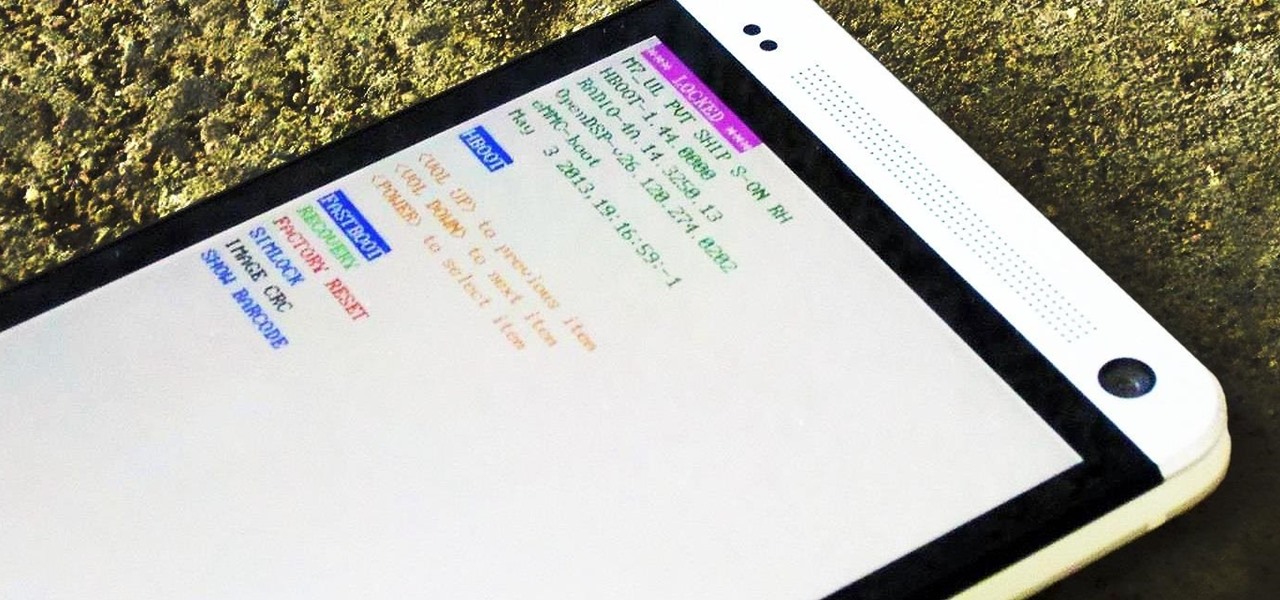
Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

Recently, many manufacturers have started offering phones with a clean, stock Android UI. Motorola, Essential, Nokia, and OnePlus are probably the biggest names that have listened to user feedback and shifted more towards AOSP. But if your phone still has a bloated OEM skin, there are a few things you can do about it.

Super Bowl LII will bring millions of football and non-football fans together to watch the big game on the big screen. But without a cable subscription, this process can be a little daunting. Luckily, the Google Play Store and the iOS App Store offer a few ways to accomplish this — no cable contract required.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

The holidays are stressful. Between traveling, family, and dinner, Thanksgiving weekend can feel like weeks. Many families have traditions that make the days long, but some of us would rather curl up somewhere and watch our favorite shows. But all is not lost — our phones do so much for us now that they can help make the long stressful weekend much more bearable.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

After previously learning how to make the material of an object change with the focus of an object, we will build on that knowledge by adding new objects through code. We will accomplish this by creating our bounding box, which in the end is not actually a box, as you will see.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Just like your gastrointestinal tract, and the soil we walk on — a dust storm has a collection of bacteria, fungi, and viruses all its own called a "dust microbiome."

Who said sports need parity to be fun? For the third year in a row, the Cleveland Cavaliers are facing off against the Golden State Warriors on the NBA's biggest stage, and basketball fans everywhere couldn't be more excited.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

If you're reading this, chances are you're a softModder, someone who doesn't let anything stand in his or her way from ultimate customization.

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.

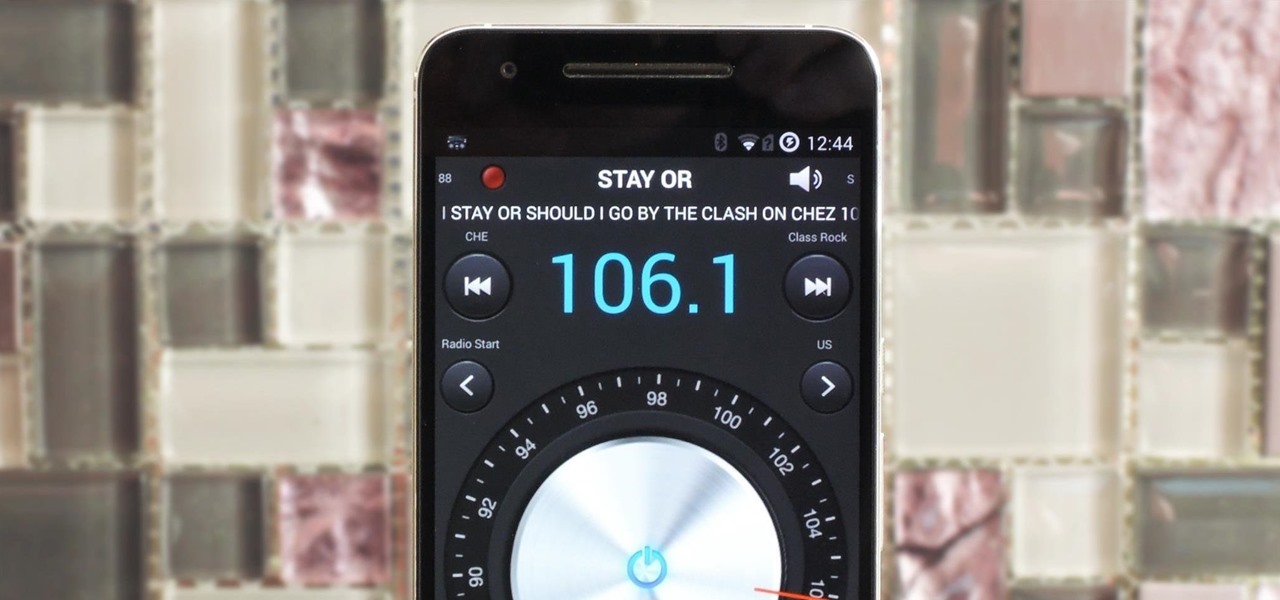
Android smartphones have all sorts of connectivity chips built in, including Bluetooth, Wi-Fi, GPS, NFC, and mobile data. But what about AM or FM radio, two of the most common methods of wireless communication?

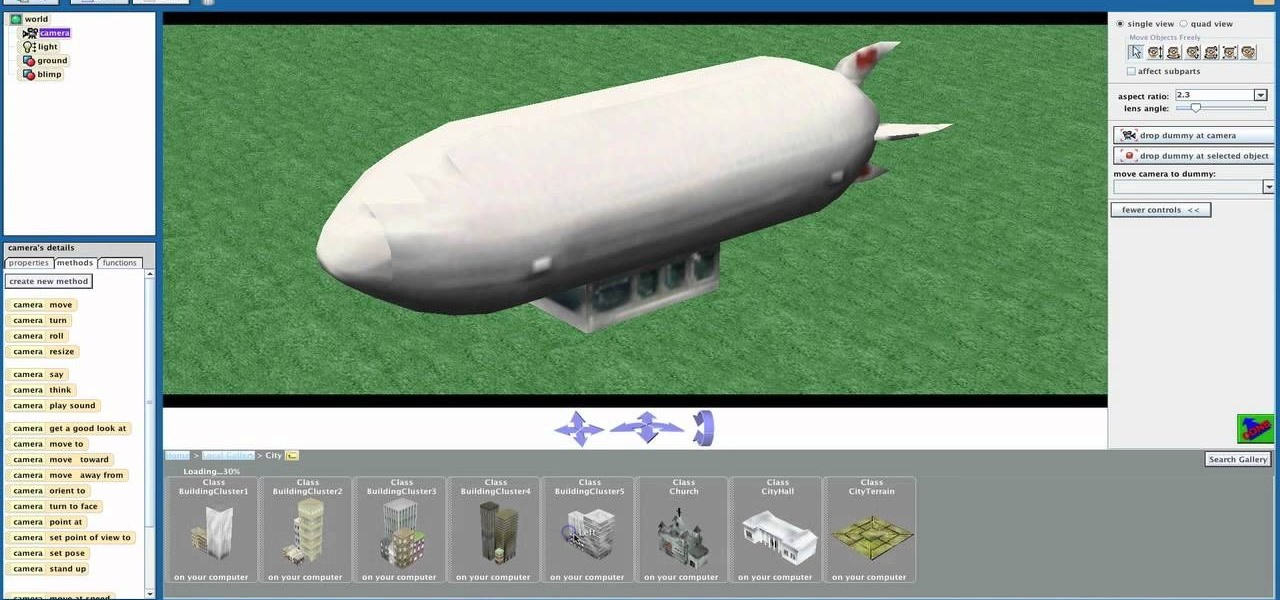
Shaun will teach us how to create a 3D video game compatible with MAC or PC with no prior programming knowledge. First download Alice, a 3D World program that can be turned into a video game. Open Alice, click on "add objects", click on "more controls" and select your choice of aspect ratio such wide screen. Now you can import your own 3D models that Shaun will show you at the end of the tutorial or choose from a wide selection that comes with Alice. In addition, if you click on "home," "web ...

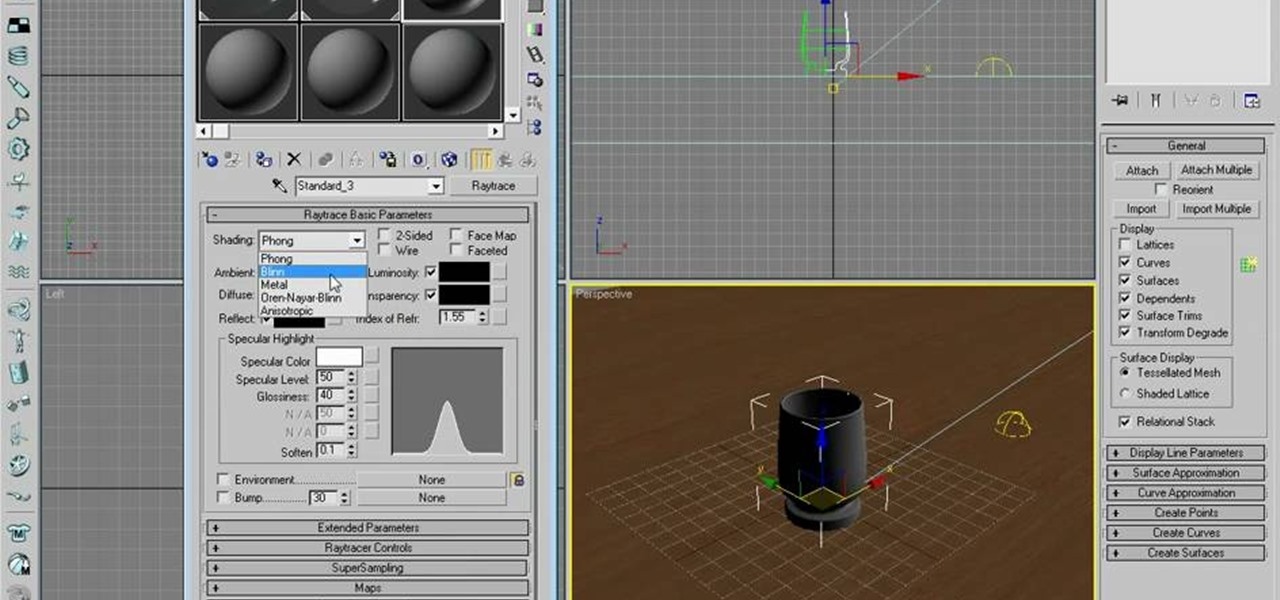
Dave shows you how to produce a glass three different ways in 3ds Max in the video tutorial. Put two panels away, then concentrating on sensor one press m on the keyboard to bring up the materials editor. On the material editor go to the first sphere, choosing a slight blue color, bring up the specter level, bring up the glossy level, click on two sided and bring down the last two to about four. Look to see it is fairly transparent, in a test window. This is glass one, put on hide. Go to glas...

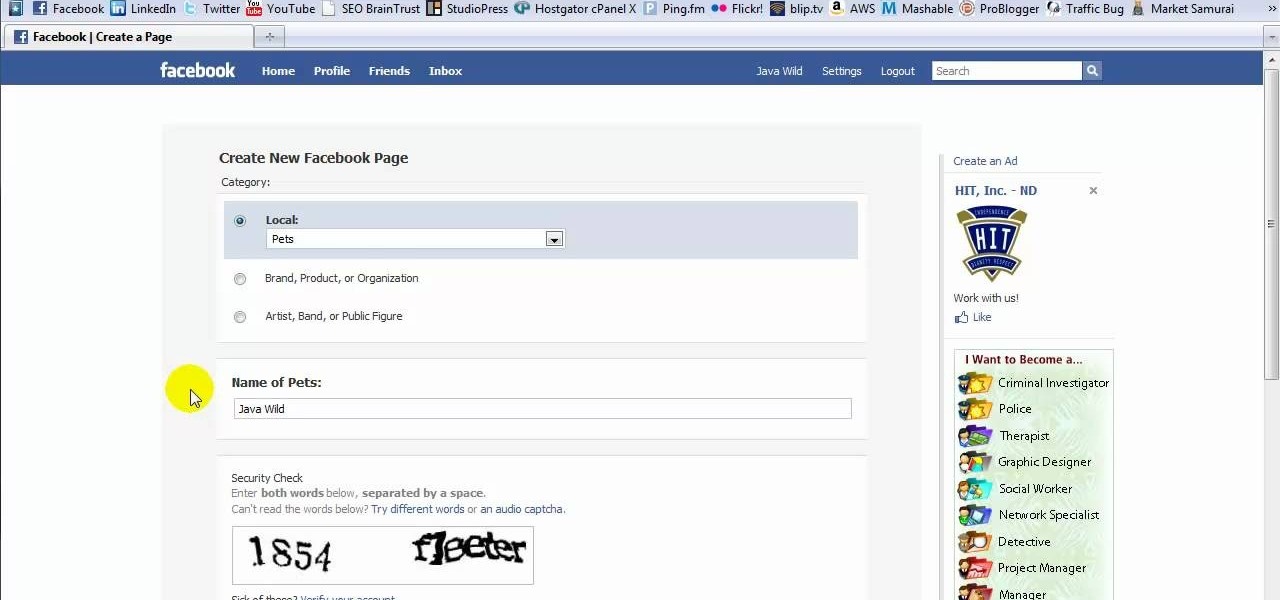
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

Purchase the necessary equipment for this project. Pumice stones can be purchased at any beauty supply store. Chlorine can be purchased from any household supply store. Sodium bisulfite can usually be found at hobby stores. Obtaining the industrial washing machines for personal use is the hardest step. Call local cleaners to see if they will allow you to use their machines. Soak the pumice stones in chlorine overnight. This will allow them to soak up the bleach and create a good absorbency fo...

It’s time to celebrate! What better way than with a bubbly brunch? You Will Need

It was bound to happen with all those numbers floating around in your brain – you've forgotten your Windows password. Here's how to recover it.

Why waste your vacation dollars on pricey hotel rooms when there are cheaper – and sometimes free – alternatives? Watch this video to learn how to find cheap (or free) places to crash on vacation.

If things are getting a bit stuffy at your desk, don’t fret. A cool breeze is just a USB slot away. Watch this video to learn how to make a USB fan.

Learn how to start seeds for planting. Start your own seeds to save money, grow different plant varieties, and extend your growing season.

Learn how to drop in on a quarter-pipe. Dropping in on a quarter-pipe or other vertical ramp is something to try after you have been skateboarding for at least a few months.

Grow some of your own food by starting a vegetable garden. You'll eat better and save money. You Will Need

It's the coolest pool party game ever named after a 13th-century explorer. Marco Polo is a perfect way to cool down and have fun.

Sound Like a Duck or a Fog Horn! All sounds are created by vibrations. You can discover this next time you're out at a fancy restaurant. All you need is that straw in your soda and a pair of scissors. Makes sure you flatten it out really good to make this work, then make sure you parent tip your server well.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Learn in this video how to use XMLSpy to create and edit XQuery documents, debug them and profile execution speed and bottlenecks, and execute them against local XML data or XML stored on a database server. XML editing can't get easier then this.

The no scalpel vasectomy has been reported to reduce the risk of pain, bleeding and infection. It can be performed under local anesthesia. Dr. Bird demonstrates his standard technique for a how to perform no scalpel vascetomy: lidocaine infiltration, skin penetration, vas isolation, electrocautery dissection, partial fixation, luminal cuaterization, clip application, and closure.

Create your own virtual hard disk and local folders to store information in.

Bourbon is America's contribution to the whiskey family, and this isn't so much a drink as it is a tradition. Take bourbon, and ideally, dilute it with water from whatever branch of the local tributary was used to make the bourbon. If you don't have access to that, then use whatever filtered water you can get from the store, and be sure to use it for the ice cubes too.

First measure the window to decide if you would like the blinds inside the frame or outside on the casing. In most cases inside looks the best plus it gives you the added feature of adding curtains.

If you're bound to a wheelchair and living in Orange County, California, then this video is a must-see if you use public transportation. It will show you the steps to boarding an Orange County Transit Authority (OCTA) bus the right way, when in your wheelchair.