If somebody really wants to gain access to your iPhone, they'll get in. Phone thieves (and mischievous friends) can easily figure out your passcode just from looking over your shoulder or tracing over the oily smudges on the screen. And if you're using popular passcodes, birthdays, and addresses on your iPhone, you might as well disable lock screen security entirely.
It's been a great week for Chromecast owners. First, Google released the development kit, allowing devs to install the casting code into their apps. Then, CyanogenMod dev Koush updated his AllCast app to support the Chromecast. That means you can shoot personal movies, music, and photos directly from your Android device over to a Chromecast-connected display.

The @DesignGears guys have been busy today, leaking an unofficial KitKat build (Android version 4.4.2) for the AT&T Samsung Galaxy Note 3. The latest is a peek into what the international variants are beginning to see, although this build is far from official. Still, if you want to give it a shot, I'll show you how to install it, but make sure to check out the details below the how-to to see what you can expect, good or bad.

The Chromecast may be slowly weaving its way into the smartphone ecosystem, but the amount of supported Android apps that are available for the streaming media player are still severely limited.

What you watch in the privacy of your own home should be no one's business but yours. That was the case until Prime Minister David Cameron decided that there was too much porn available to minors in the United Kingdom.

Let's get one thing straight: CyanogenMod is one hell of a ROM. They've got a great community, a great product, and getting it on your HTC One couldn't be easier with their CyanogenMod installer, which does all the hard rooting and bootloader unlocking for you.

Voodoo you want the best costume this year? You're probably laughing so hard right now that you need to hold yourself together with pins and needles, right?

Over time, the dryer belt can become hard and brittle when the drum is turning loud noises such as squeaking, squealing or thumping noises can occur. Replacing the belt is an easy task for the do-it-yourselfer. All that’s required is a few simple tools. Here’s a step-by-step guide to help you install a new belt in your dryer.

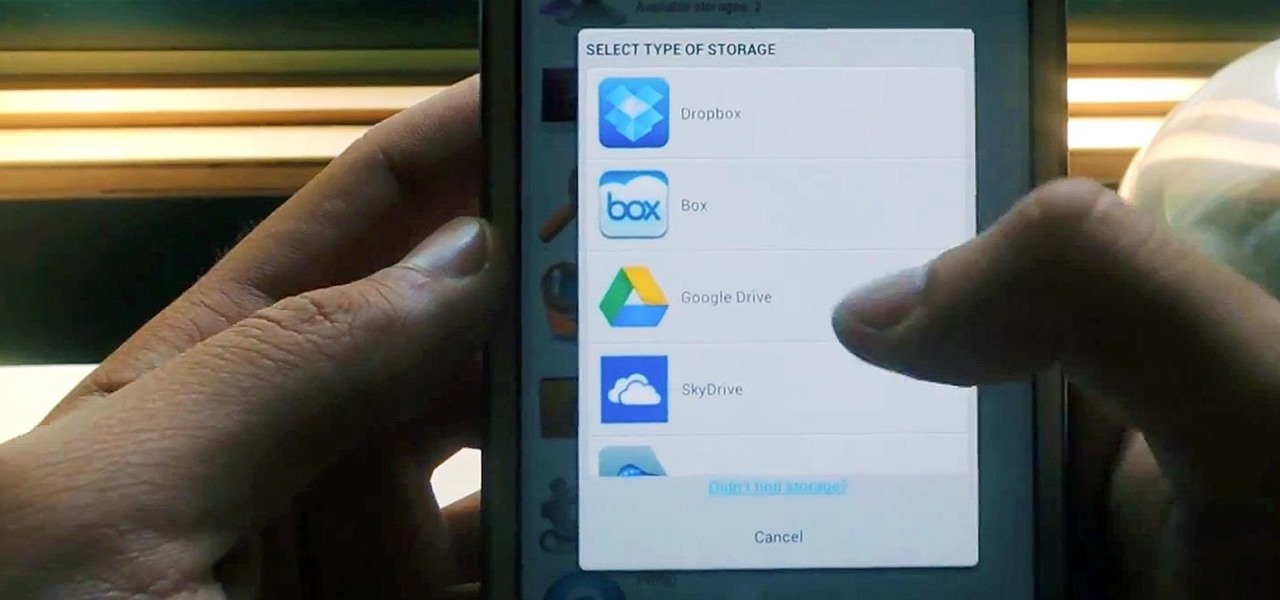
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work computer, personal laptop, tablet, and more. While accessing a specific cloud storage system like Dropbox or Google Drive may be easy on your Samsung Galaxy Note 2, managing all of them individually can not only get confusing, ...

For the most part, Xbox Live is amazing, but there is one thing that has been annoying for pretty much everyone, to say the least. Microsoft Points.

Facebook knows who all of your closest friends and family are. When you backpacked across Europe last summer, they went along on the trip. Remember that break up two years ago? Yeah, they were there. The breakfast you ate this morning? They probably have a picture of it. They're even right under your own feet.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....

Plastic red cups are synonymous with college parties, beer pong, and generally a good time. The reason these cups are so rampant in the party scene is because they're cheap, easily disposable, and, well... who wants to drink out of a blue cup?!? Oh, to be young and in debt.

During the colder months, it seems like almost everyone wears boots. Even when it's hot out, people can be spotted with knee-highs and westerns. Whether it's for fashion or because you live in a place where 3 feet of snow is common, a good pair of boots (or five) is nice to have.

Parking. Ugh. Parking is about as fun as running through a swarm of bees while being chased by a pack of wolves from The Grey.

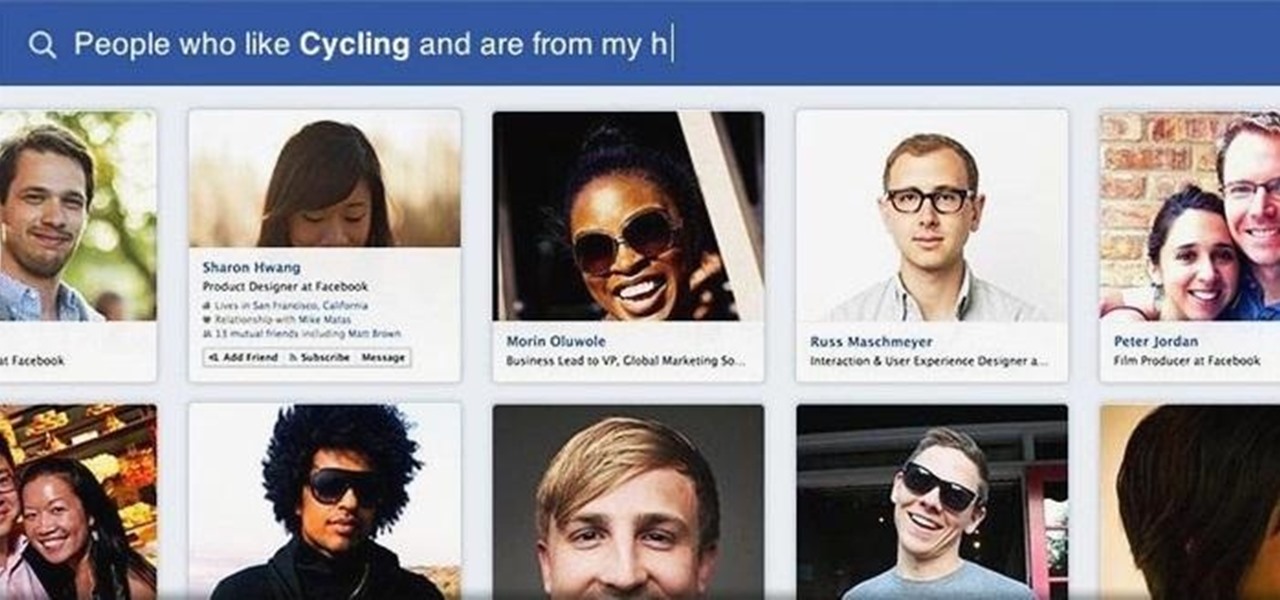
Facebook has been looking to launch a new product for a while now, and it seems they've finally realized what they're best at—being as creepy as possible. If you thought your boss checking out your girlfriend's beach photos was weird, Facebook's new Graph Search has only upped the ante. Now, I don't want to be an alarmist, because I'm sure there are a bunch of great things a Facebook search would find. If you're single, perhaps you could search "Girls that are single that like Goodfellas." Th...

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Maybe not water per-se, but with this simple technique you can turn one of the most abundant materials on earth into a highly explosive gas.

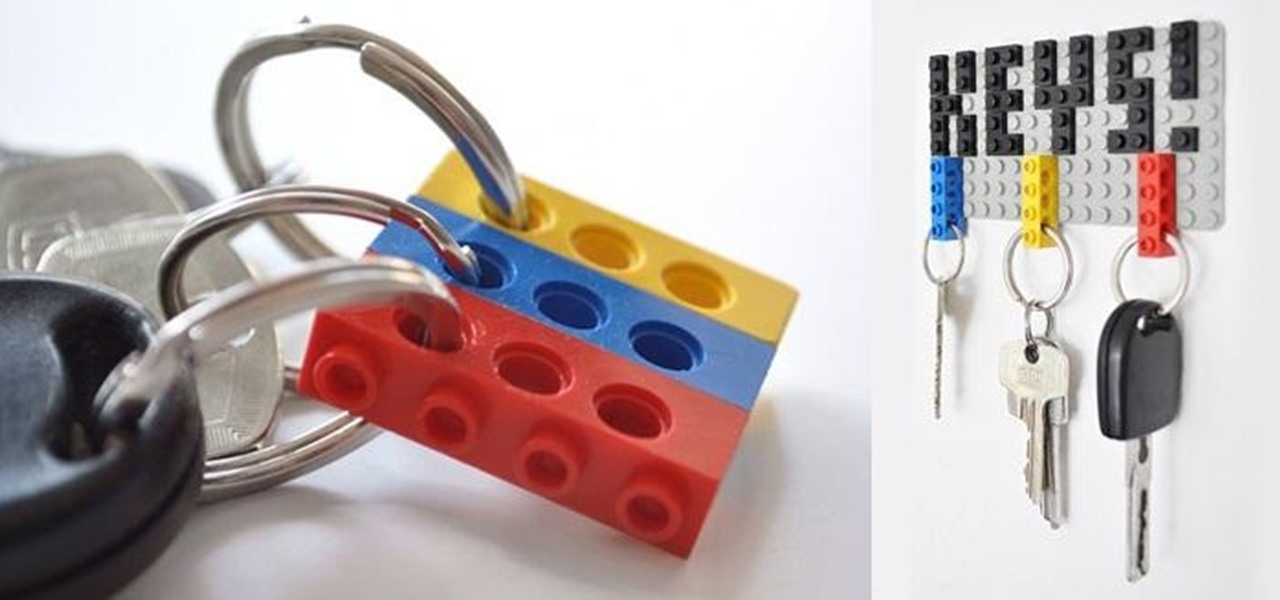
LEGO may no longer be in its heyday, but those colored building blocks of joy can still make some really cool and creative things. I mean, take a look at these pieces from LEGO artist Nathan Sawaya. While making something like that is undoubtedly impressive, it could be just a little too difficult for the common LEGO enthusiast—and expensive (LEGOs aren't cheap these days). So, for the regular LEGO-builders, usefulness is more important that extravagance.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks at Facebook are using this technology. Obviously, this brings up some pretty serious privacy concerns amongst most people, because honestly, who wants to be tracked? Right now, there's not a lot we can do about it being ...

Sometimes you just want to grill. It doesn't matter where you are, what you have, or whom you're with—you just want a delicious burger and you don't care what it takes.

If you've ever wondered what exactly goes into a McDonald's sandwich (or what the heck that secret sauce stuff is anyways), you might be a little surprised to learn that all of the ingredients are readily available at your local grocery store. In an interesting move, McDonald's has released a video featuring Executive Chef Dan Coudreaut showing, step by step, how to make your own Big Mac sandwich at home. Here is the video, and if you'd like to read along with Coudreaut's instructions, you ca...

Someday, maybe not today, maybe not tomorrow, but someday, you'll find yourself on the road in your car, maybe on the highway, and you'll hear something.

Get a crash course on HScript Expressions, Variables, and Attributes in Houdini 10. If you don't even know what this means, then you probably need to check this video tutorial series out. Understanding how to massage data in Houdini is key to giving yourself the creative edge and allowing you to unleash mind-blowing visual effects. This 18-part video series covers a variety of simple yet essential weapons in your arsenal including Global, Standard and Custom Variables to Math and String Modif...

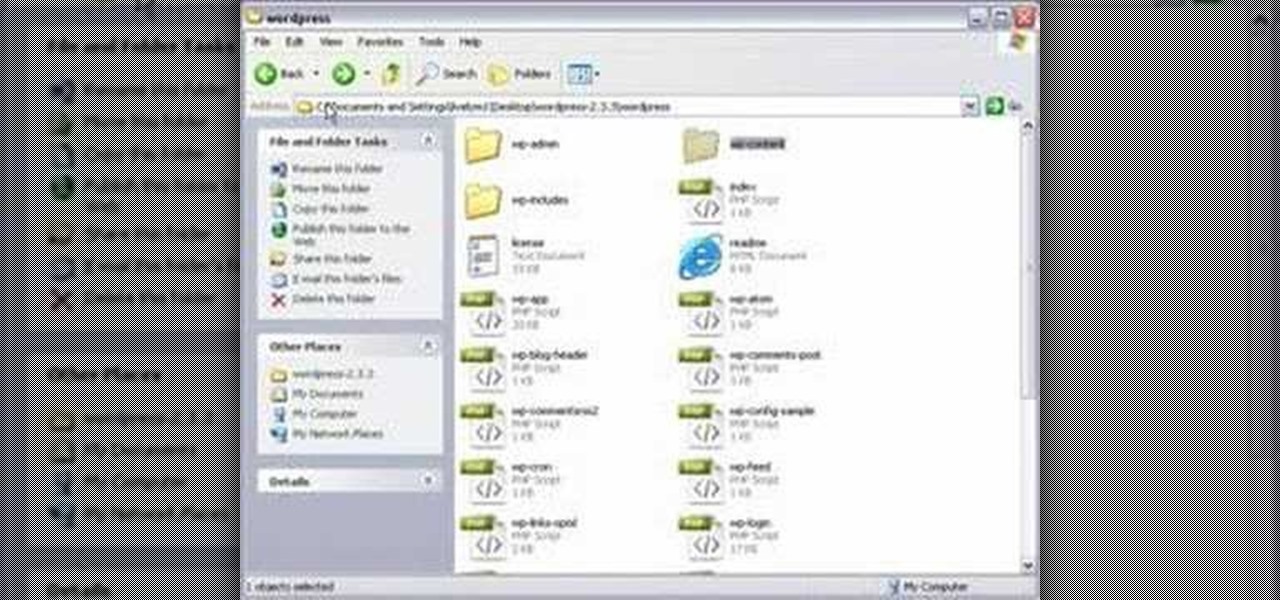
In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.

In this tutorial, we learn how to remove stains from your car seats and carpet. To start, you will need cheap orange cleaner that you can find from your local Dollar Store, as well as cheap carpet cleaner. When you find the stain that is on your carpet, you will first spray it with the orange spray, then go over it once more with the carpet spray. After this, use a scrubbing brush and wash cloth to scrub out the stain in the affected area. When finished, let dry or use a vacuum to soak up any...

In this video you will learn how to check your internet speed without using any software. In order to do that just follow these simple and quick steps and instructions: The first thing that you need to do is to double-click on your Local Area Connection icon. A window will appear and you will see what your speed is on the right of it. The speed of your internet will be in Mbps. If you follow these easy and quick steps you will now how to check your internet speed without using any software or...

A cold frame is a great way to extend the growing season in your garden. When you set up a cold frame, you can keep your plants healthy and growing, even when it's cold outside. In this video tutorial, you'll learn how to set up and use a cold frame.

Aerating your soil is an essential part of gardening, but it can be long and back-breaking work. In this episode of Growing Wisdom, Dave Epstein will teach you how to use a broadfork to aerate your soil. Using a broadfork, you can aerate the soil without damaging the soil's ecology.

Looking for a great idea for a science project? In this video series you'll learn how to build a battery-run light board which can test the electrical conductivity of various objects. You can find these supplies easily at your local hardware store.

With the growing popularity of buying local, many people are rediscovering the benefits of preserving fruit at home. Concerns over food origin, additives and preservatives are driving this trend and in just 20 minutes you can enjoy fresh produce all year long. Watch this how to video to learn more about picking fresh food and the preservation process.

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.