Frozen fruit is always in season at your local grocery store, so you don't have to wait until the farmers market starts again to enjoy delicious baked fruit desserts. Peach pie, blueberry muffins, raspberry scones... all of these delicious baked goods can be just as delectable when using frozen fruit, too.

So you dropped your smartphone and the screen cracked. Again. Just the thought of sending it out for repair or buying a new phone is driving you mad.

The big day is nearly here... Super Bowl 50 kicks off this Sunday, February 7, at 3:30 p.m. PST (6:30 p.m. EST). And whether you're having a giant party or watching the game on your big-screen TV by yourself, there's one thing you probably won't be doing: cooking food in your kitchen.

Every phone has its issues and quirks, and the Nexus 5 is no exception to this rule. One of the most common troubleshooting questions asked by its owners is "Why does my Nexus 5 keep shutting off or restarting?" where the device suddenly decides to reboot or power off randomly on its own.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Nowadays, it feels like you can't talk about eating healthy without bringing up quinoa. Quinoa (KEEN-wah) has been the "superstar" of the health movement for a while; 2013 was declared the International Year of Quinoa by the United Nations, and has only continued to grow in popularity with both health nuts and culinary experts alike through the past few years. The true testament to quinoa's success has been its eventual integration into our everyday lives. Quinoa is now very accessible to fol...

Smelly foods are what make my culinary world "go 'round," so to speak. I grew up with fish sauce, learned to cook with and love fermented beans and veggies, and am one of the biggest garlic advocates I know... other than my husband, who thankfully shares the same smelly food sensibilities. (Let's put it this way: anyone that can stomach stinky tofu can handle anything I could possibly cook up.)

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

When your cat goes missing, chances are it's just chilling in a cozy spot under the couch, or maybe even hiding from you. So it's okay to not freak out just yet. Cats love to hide as if they're spiders, and even their hiding spots are similar. You can find them in corners, on the refrigerator, and according to my roommate, even the dryer hose is fair game.

Whether you choose the sassy face of someone like your inner Disgust from Inside Out, or you're the happy-go-lucky Joy, chances are you're well-versed in expressing your inner "ew." So for this Halloween, take pride in your judgmental self by donning a DIY Disgust mask.

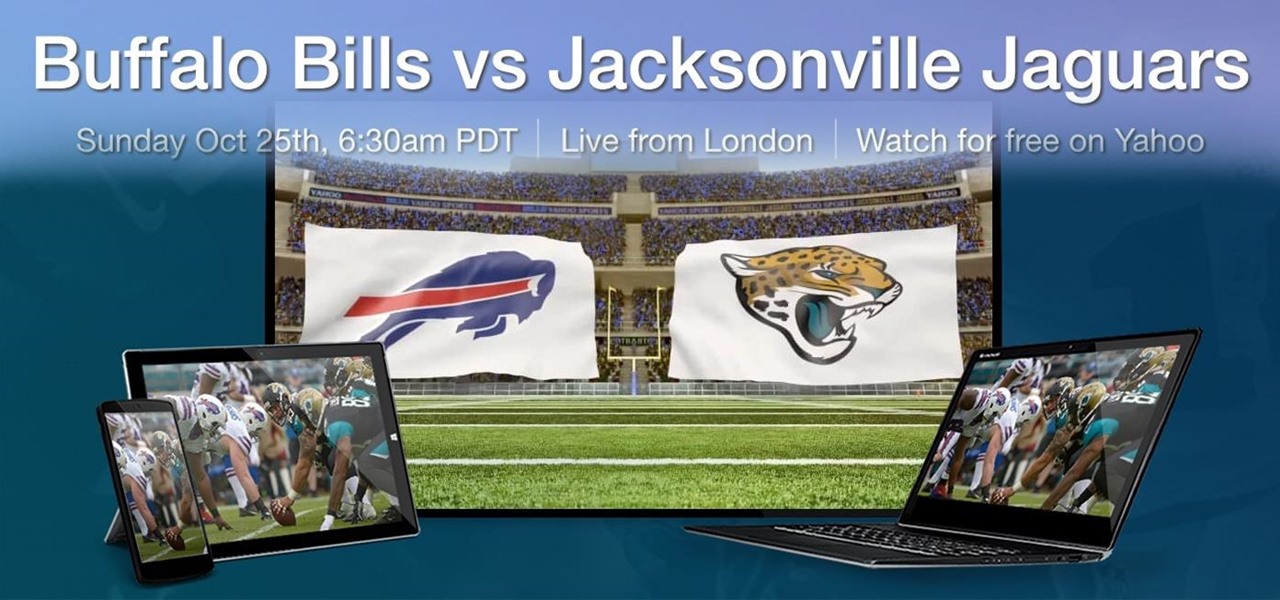
For a lot of would-be cord cutters, the lack of streaming local sports is the only hurdle that needs to be cleared before they can sever all ties with big cable. This is why it was a huge victory for us anti-cable folks when Yahoo announced that they would be hosting the first ever live-streaming NFL game this Sunday at 9:30 AM Eastern.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Editor's Note: The research described in the article below has been criticized and any conclusions based off this research should be examined with a skeptical eye. The article has been edited to reflect these issues.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in an effort to make utilizing OneDrive easier for you.

Star Trek Communicator badges rule. If you're a Trekkie, you know they are iconic to the TV series. The Next Generation, Voyager, and Deep Space Nine all had these awesome communicator badges.

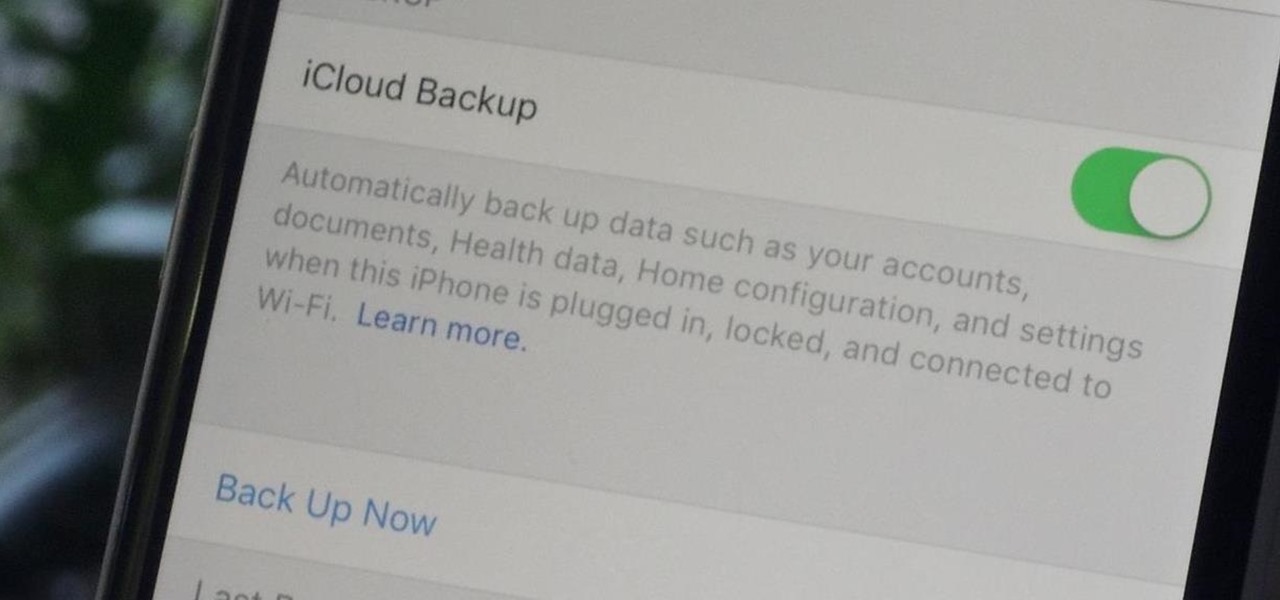
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

There are three huge benefits to microwave popcorn: it's quick, it's delicious, and it's cheap. But there's a way to make popcorn that's better, more delicious, and cheaper than the microwave variety. And oh yeah, quite a bit healthier.

I have a thing for citrus in any form. If I can't get a hold of oranges or clementines, I've been known to slice up lemons and limes and eat them straight with a little bit of salt—terrible for the tooth enamel, but amazing for the tongue.

Here at Food Hacks, we're very fond of finding ways to regrow food. That means taking things like carrot tops and leftover bits from garlic, onions, chives, and other herbs and aromatics to create mini reusable herb gardens.

I have a thing for black foods, whether it's mysterious, lovely black garlic (the secret to its color: fermentation) or adding charcoal powder with its reputed health benefits to cookies, cakes, and breads.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

There are a lot of frustrations when you're dealing with cramped living quarters, but you can do a lot of good cooking in your tiny kitchen if you make the most of your space. These storage hacks will make it easy to cook delicious meals, no matter how limited your square footage.

Hops have always been known as the driving force behind beer, but now they're starting to grow their own culinary wings. Slowly but surely, this bizarre and bitter plant is showing up on more and more menus across the country as it catches on as a trendy and up-and-coming ingredient. What Are Hops?

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

There are lots of great reasons for going out to a fantastic coffee shop for a cuppa. Coffee shops have a lovely ambiance, are a perfect place to meet with friends or do some work, and are a great excuse to get out of the house. Seeking out a perfect cup of coffee, however, shouldn't be one of the reasons that you hit up your local café.

If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.

Those ordinary green zucchini you see in the market are hiding a lovely, delicious secret: Actually, all summer squashes produce these delightful blooms, but the zucchini's are most frequently used for eating since they taste the best: fresh, clean, and zucchini-like, but with a little something extra. They used to be a rarity at supermarkets, so you had to have a garden or a gardener friend who would generously share the bounty with you.

Using breadcrumbs in the kitchen is the perfect way to add crisp and crunch to the usual salad, entrée, or dessert. As chef and media personality Mario Batali once said, "There's almost nothing I wouldn't put homemade breadcrumbs on."

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

One of the most mind-blowing meals I ever ate occurred when I was 12 years old. The main course and sides were good, if unmemorable, but my jaw dropped during dessert when my friend's mother whipped out a blowtorch—as in a bona fide welding torch from the hardware store—to finish off the crème brûlée.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

Roasting turkey is a topic that inspires endless debate among cooks. How do you get the perfect mixture of juicy meat, crispy skin, and flavor? Everyone has a favorite technique, whether it's brining the bird or spatchcocking it. However, if you're ready to move onto Ph.D. levels of turkey cooking, you might just want to look beyond these methods and get genuinely wild.

The Snapdragon 801 processor inside the OnePlus One puts the device on par with other phones like the HTC One M8 and LG G3 in terms of power and speed. While the OPO is just as fast and responsive as many of the flagships currently available, there's no reason why we can't try to squeeze every last bit of speed and performance out of it.

It's pretty logical for your MacBook to sleep when you close its lid, but under certain circumstances, you may not necessarily want this feature to kick in.

It wasn't too long ago that I showed you how to unlock the LG G3 bootloader and install TWRP, and while the process was extremely easy, the custom recovery can look a little intimidating to new users. Even long-time users who know how to navigate it find it boring to look at, as TWRP has had the same basic aesthetics since its creation.