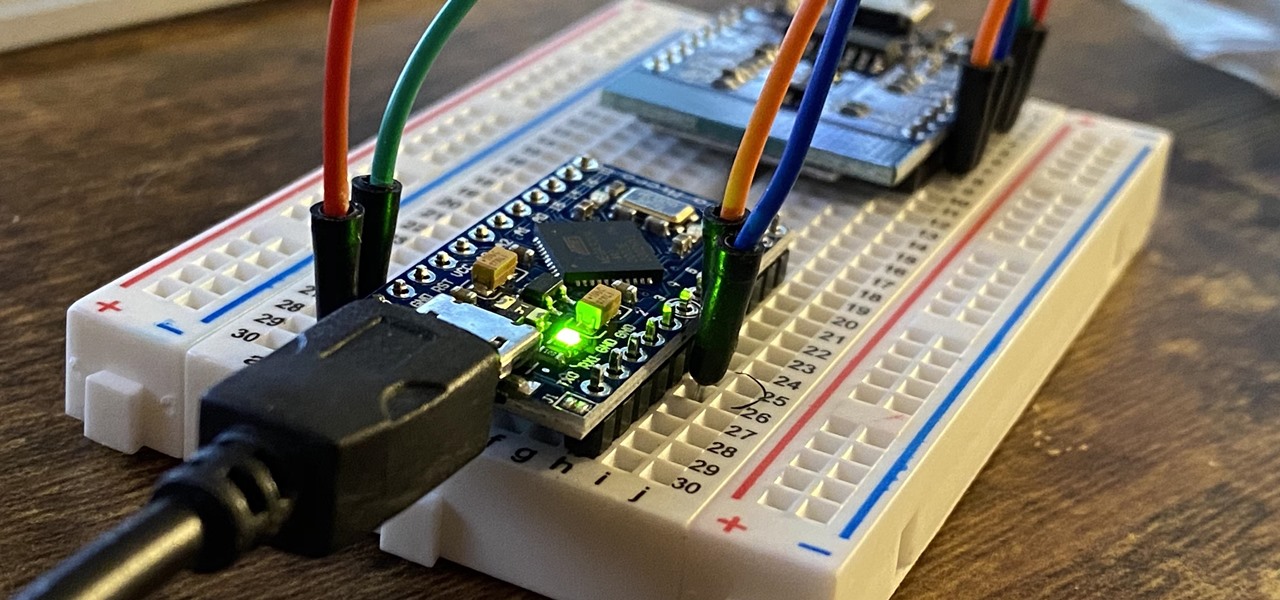
In the music world, it's safe to say electric instruments are more versatile, but they lack the portability of their acoustic counterparts. However, with the aid of your smartphone plus an audio interface, you can play your electric instrument anywhere — with all the pedal effects you please — and even record your efforts.

Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Skulls. What spooky Halloween décor or staging of Hamlet is complete without a skull or two popping up? For ghoulish special effect and/or setting a dramatic scene, skulls are absolutely integral. Well, with some artistry, hardware supplies, and a good dose of patience, you can create your own inexpensive prop skulls for use however you please.

Growing up, I was told that hard work could get me anything I wanted. But with Apple's Image Playground, I can create almost any illustration or drawing imaginable just by typing or selecting a suggestion. This groundbreaking feature in Apple Intelligence lets you generate images from simple prompts, opening up exciting possibilities for creativity.

Using different sounds on your iPhone for different notifications can help you determine — just by listening — alerts you may want to look at immediately versus untimely alerts or even ones you typically ignore. But Apple has never given us complete control over notification sound customization on iOS, though the latest iOS update is a step in the right direction.

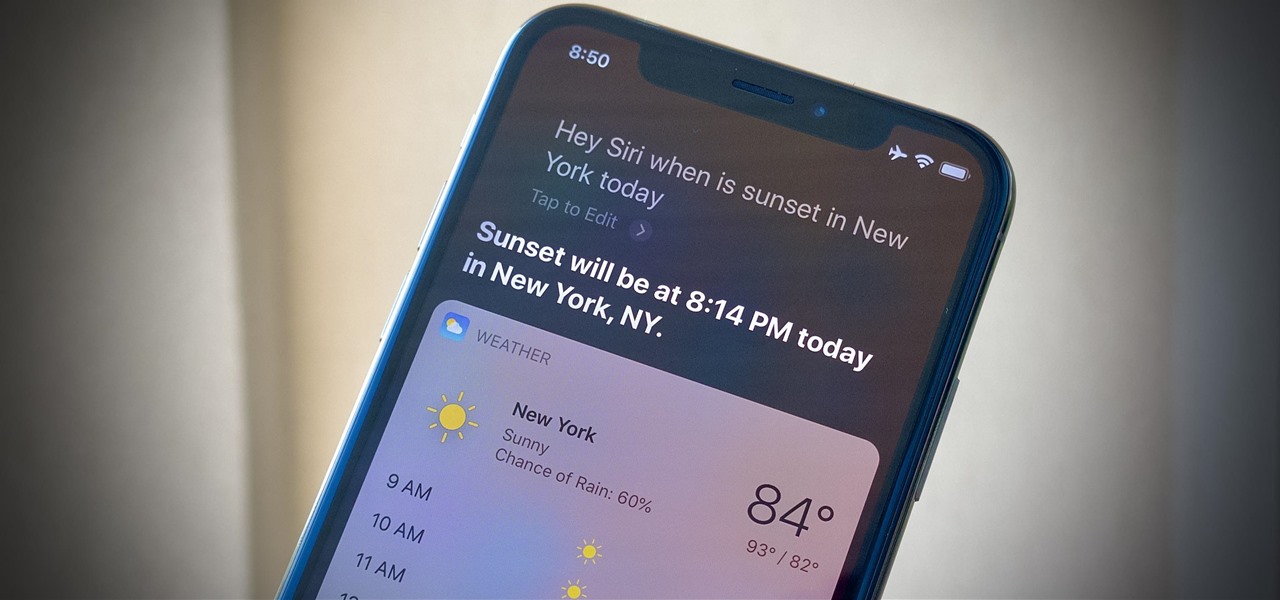
Wireless emergency alerts help warn mobile phone users of imminent threats to life or property, such as extreme weather and natural disasters. These alerts target affected geographic areas and come with a loud sound scary enough to make you want to turn off emergency alerts altogether on your iPhone, but there's a way to keep emergency alerts without the ear-splitting, intrusive sound.

If you're not planning to upgrade to a new iPhone 13, the new version of the iPhone operating system will breathe some new life into your iOS device.

Google and Snap held their annual conferences this week, and both companies managed to upstage their new AR software features with fantastic new AR hardware.

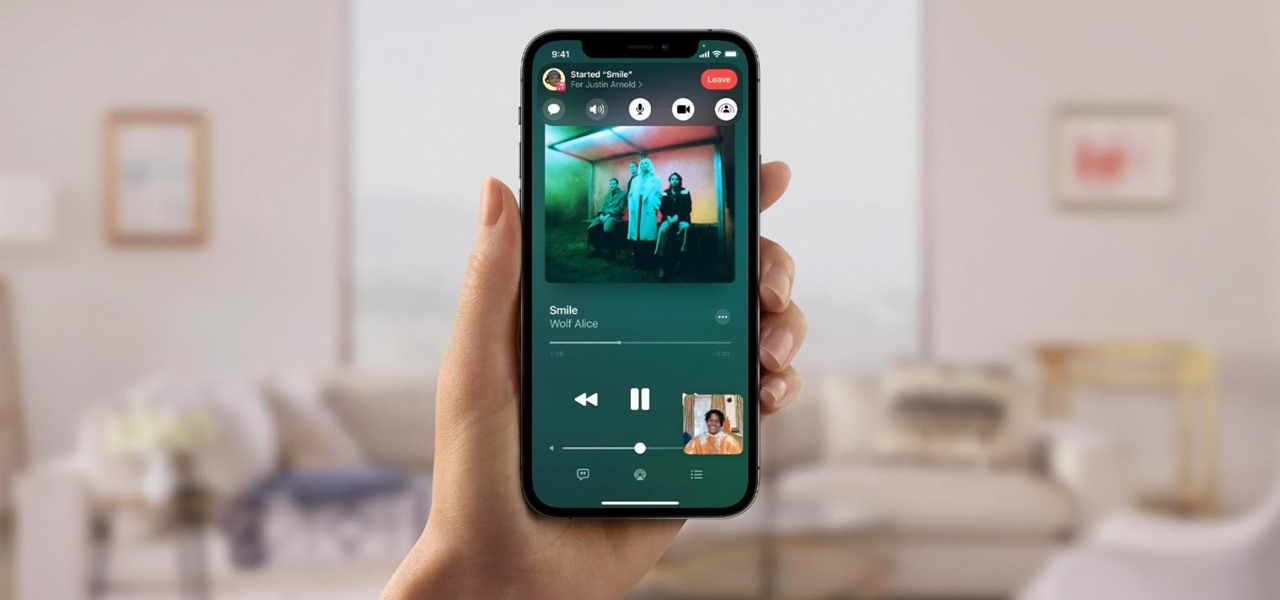
The Apple Watch is rapidly becoming a standalone device that you can use without an iPhone or internet connection, and Deezer and Spotify have just helped make that even more true by adding support for offline playback on the watch.

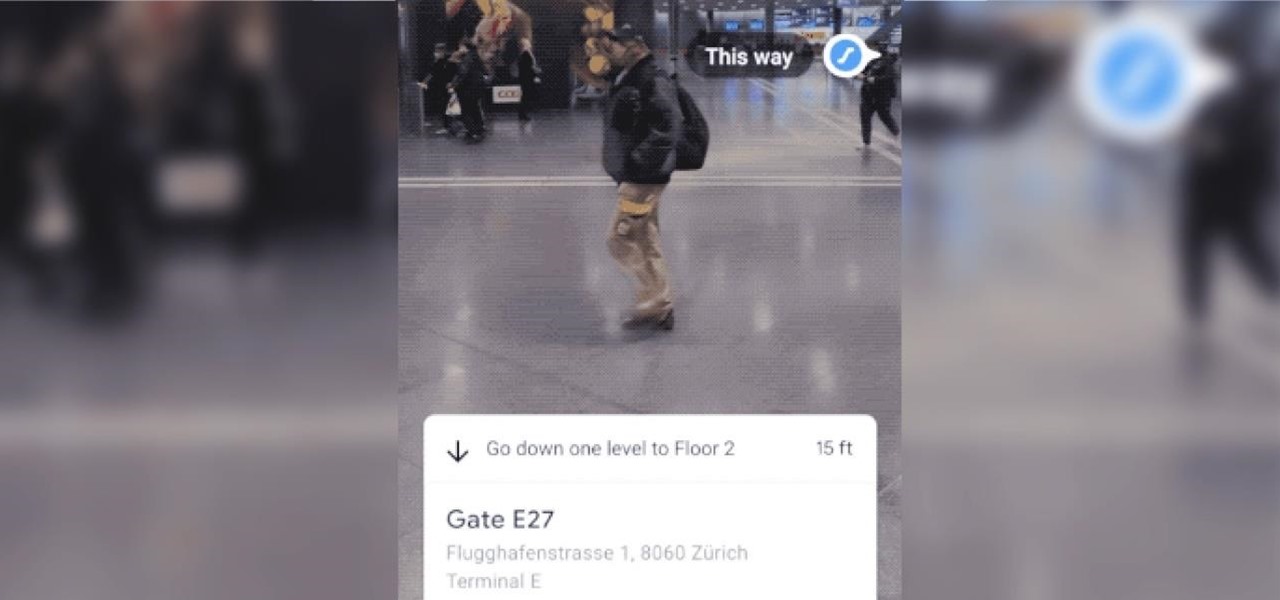
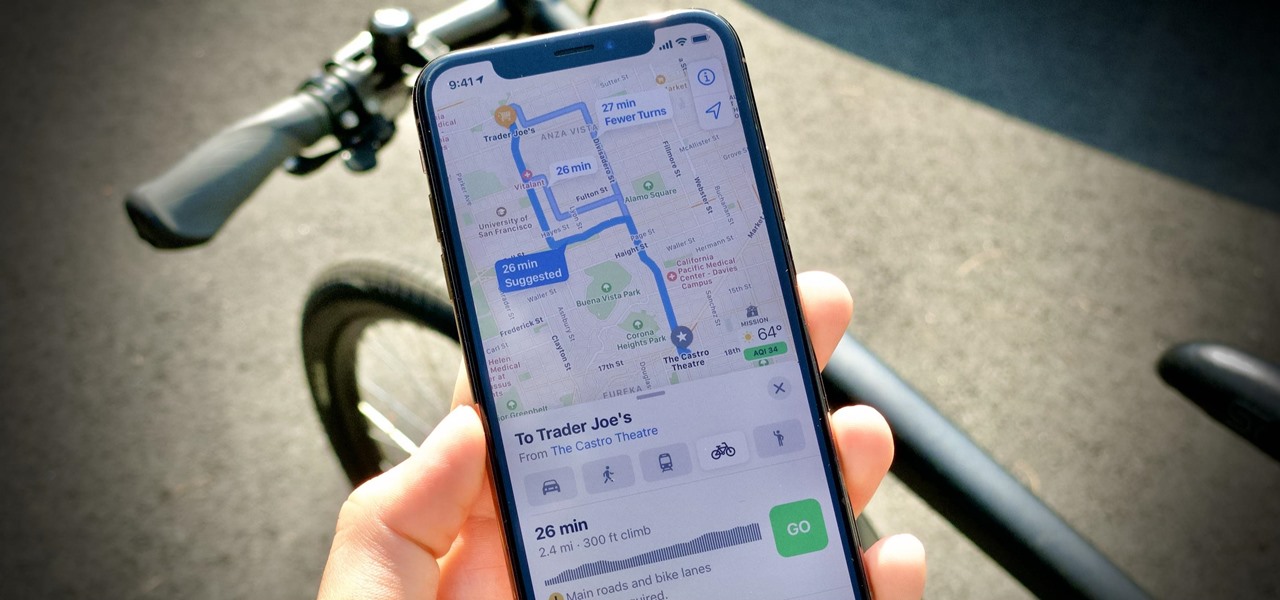
The AR walking navigation feature in Google Maps, which is arguably one of the most useful mobile augmented reality to available to consumers, is about to get even more indispensable for travelers.

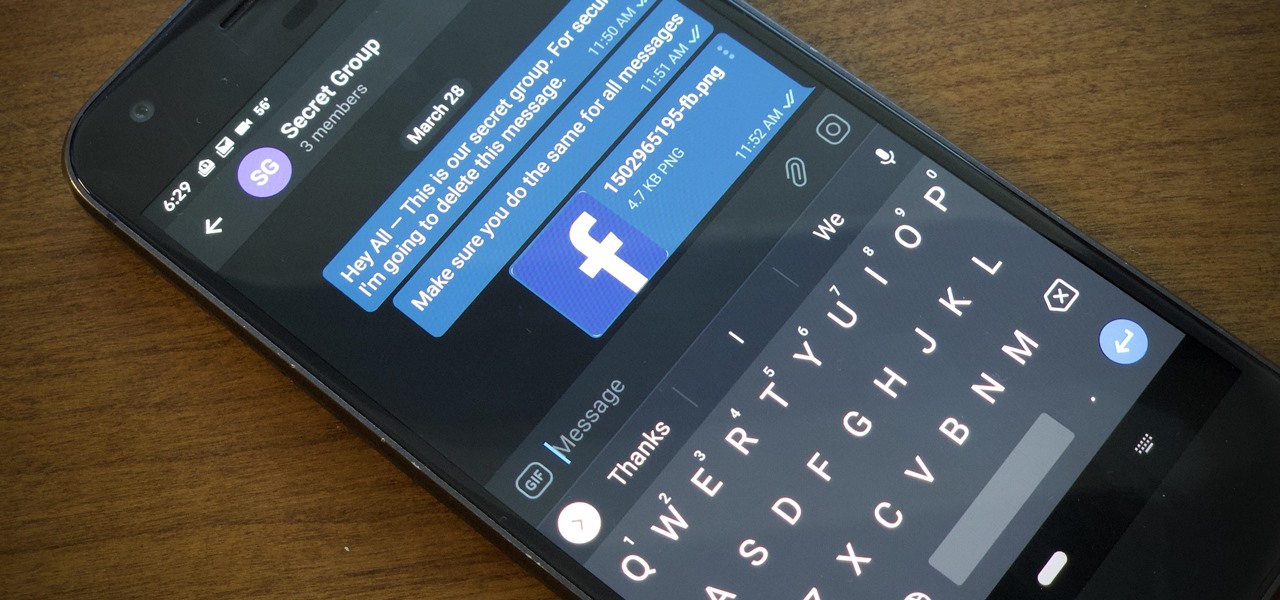
Your TikTok videos might be interesting, creative, fun, and appealing, but that doesn't necessarily mean you want the entire world to see them. While you're fine with strangers watching your videos, you may not want your close friends, family, and coworkers to see the kinds of mischief you're up to.

Pixels don't have a "Download Mode" like Samsung Galaxy phones, so there's not an easy, point-and-click way to send firmware files and low-level commands from your computer. What they do have is an even more powerful tool: Fastboot Mode.

The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if you don't know what the target computer is, you might come up empty. That's where the WiFi Duck comes in handy.

Wordpress is one of the world's most-loved content management systems (CMS). The user-friendly interface and ease of use have made this open-source system a no-brainer for millions of people. Over one-quarter of the top 10 million websites on the planet use Wordpress.

Apple's Dark Mode in iOS 13 and later offers a cool, comfortable viewing experience on your iPhone. You may prefer the dark theme all day long, but if you like to use it only at night, it's not very convenient to switch it on and off daily. But there's a setting that lets you set it and forget it, so you never have to do it manually again.

Once the laughing-stock of the navigation app market, Apple Maps is now a powerful, reliable travel companion. Apple rebuilt the platform from the ground up, placing the app in league with Google Maps. That said, there's always room for improvement, as demonstrated by its impressive new features set in iOS 14.

Apple just released iOS 13.6, and while there aren't a ton of new features here, there are some pretty amazing ones to be on the lookout for.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

It's finally here. After years of rumors and speculation, Apple unveiled the new iPhone SE on April 15. While it doesn't have a 4-inch display like the original SE, it's the smallest new iPhone you can buy today, with the chipset of the iPhone 11, 11 Pro, and 11 Pro Max. So, when can you get your hands on it?

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

Whether you've made a resolution to try and read more books this year or are just looking to set time aside to listen to an audiobook a little bit each day, building good reading habits can be tough with a busy life. However, with iOS 13, Apple Books includes reading goals, which might give you that little extra bit of encouragement and accountability to help you reach your goals.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Whether gabbing via cloud chat or Secret Chat, there's no denying that private messaging is one of Telegram's strengths. Communications can often occur at night, where Telegram's default bright white theme can be a bit uncomfortable to use, but Telegram supports dark mode on Android and iOS — with a few different themes to match any late-night chatting style.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

Planning a vacation overseas can sometimes feel overwhelming with the number of things you need to remember before heading out. Since smartphones keep us connected at all times, it's essential that you have everything you need here as well. Unexpected events can arise while on your trip, and you should be prepared for anything like a survival expert.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.