Mochi seems to be everywhere these days: as a topping at your local frozen yogurt shop, in ice cream balls (the green tea ones are heaven), and as colorful treats all over Instagram. It seems like mocha mania is in full force!

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Mirror, mirror on the wall, who is the fairest of them all? Besides being one of the most notorious misquotes of all time (the line is "Magic Mirror on the wall, who is the fairest of them all"), it's a question that men and women probably have asked themselves more than once.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

Once you unlock your bootloader and root, you're left with one more hurdle to overcome, and that's getting S-Off.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

The mother of all games is almost here. Super Bowl XLVIII pits the Seattle Seahawks (or Seachickens, if you're from the Bay Area) against the Denver Broncos and regent exemplar of neck surgeries, Peyton Manning.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

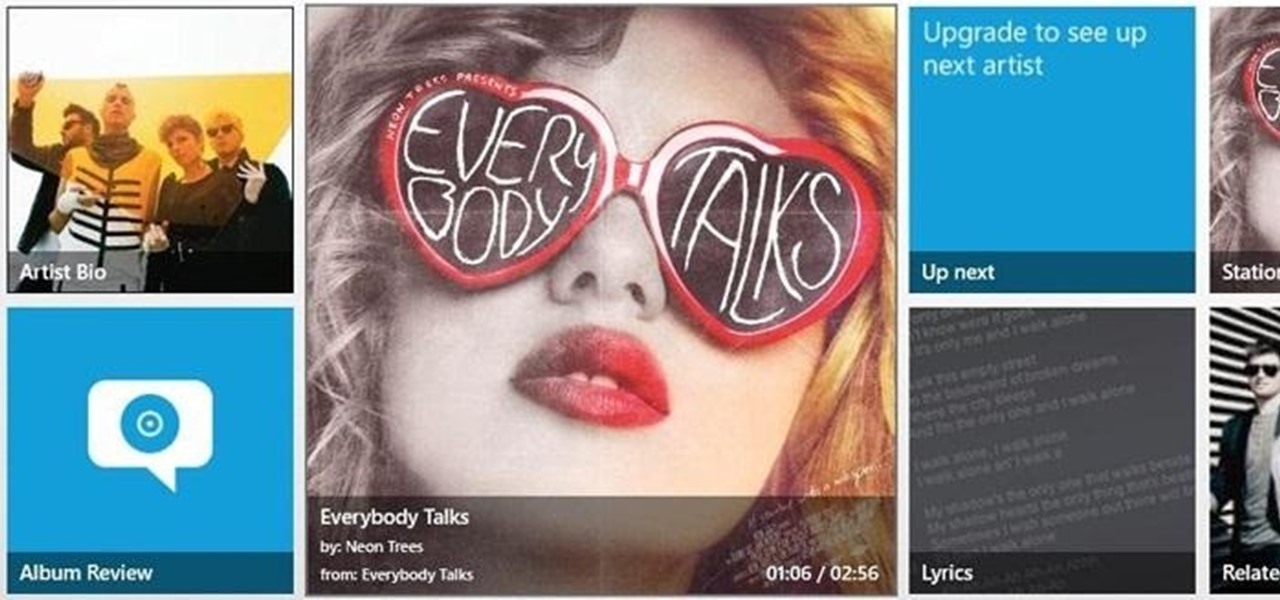
Everyone listens to music. I've got over 3,000 songs in my iTunes library, but am always looking for more, and I'm sure you are too. You can never have enough tunes to rock out to, right? If you're using Windows 8 like I currently am, these are some of the best apps in the Windows Store right now that will help you find new jams for your collection.

If you've accidentally jiggled your Xbox while a game was playing (or maybe your pet did), you might experience the Perfect ring scratches - or a laser burn. Ignore all the advice that tells you to use toothpaste, an eraser, or even crazier substances. All you need to do is go down to your local video game store or rental store (like Vintage Stock, GameStop, EB Games, or a similar place) and ask for a disk resurfacing. It's usually either cheap or free, and definitely worth it!

Zabernism. What exactly is it? It's a term that originated in 1912, during an incident involving an overzealous soldier who killed a cobbler for smiling at him is Saverne, a small town in Alsace in north-eastern France. The said event ultimately triggered an intervention from the army who took over the power from local authorities.

The pen doesn't have to stop on the paper. Your art masterpiece doesn't have to stay on the canvas. You can share your favorite drawings with everyone, right on your own chest. Wear your art designs with pride by using a scanner/printer, a photo editing application, an iron, and Avery iron-on Dark Fabric Transfer paper. And don't forget your tee shirt.

There comes a time in many tattooed individuals when they want to remove their tattoos. There are a lot of different ways to remove tattoo but they all cause scar. Dr. Neal Schultz explains only laser tattoo removal will not leave a scar and give a cosmetically-superior result. Laser energy is specifically targets the colored pigment of the tattoo so it only damages the colored pigment. It does not damage any of the surrounding skin. When people are treated for tattoos, it can take 8-12 treat...

It can be hard finding fellow singles in the suburbs but it can be done! Keep your eyes peeled and make sure you are out and about meeting new people in public settings. Don’t forget about your online or in print options.

Two ladies are discussing how to prepare to decoupage a wooden bangle bracelet. They are using a broad wooden bangle crafted from birch wood that can be purchased at a local craft store and printed tissue paper, for example, one in an animal print. This is part one of a three part series.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to apply localized correction in Lightroom 2.

Check out this DIY video tutorial from Curbly, the best place to share pictures of your home, find design ideas, and get expert home-improvement advice.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

This four-part video tutorial will show you how to make a basic boffer sword for full contact padded weapons fighting and live action role-playing.

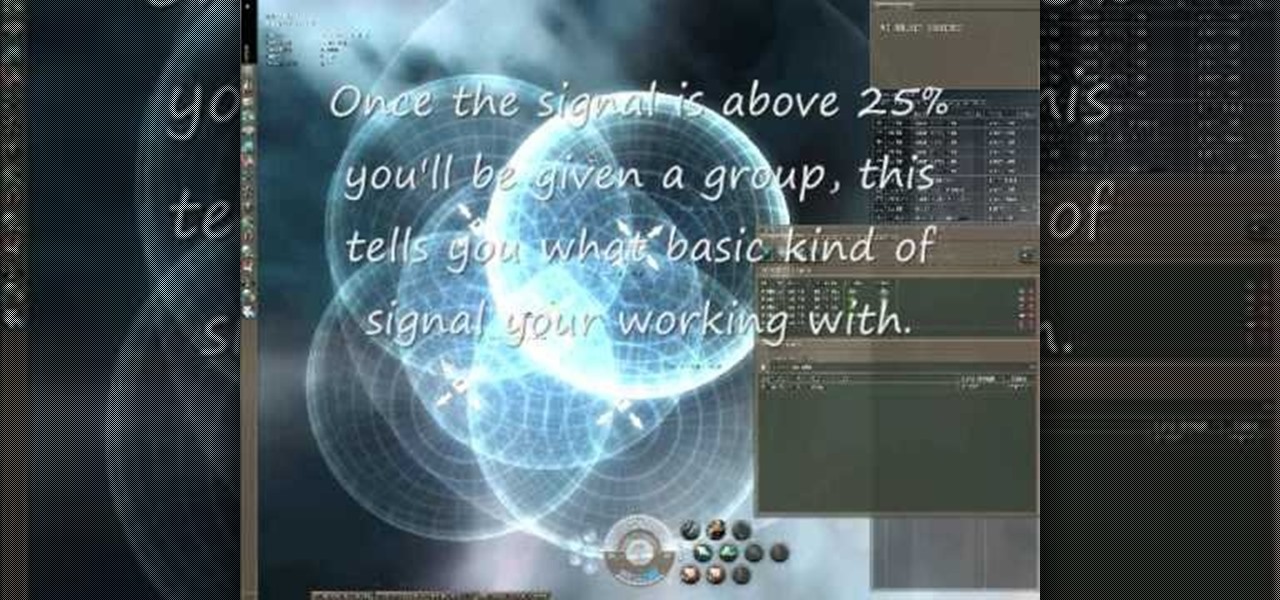
Know what's out there! You can send out probes to explore the area surrounding your ship. This tutorial shows you how to send out five probes and manipulate them in order to quickly and easily scan the local territory.

If you're the designated cook, outdoor BBQs should be fun, not time consuming and tedious. But this is what often happens when you're trying to barbacue beef, pork, or chicken and need to make sure each gets its marinade, the right coal or wood chips, and gets cooked long enough.

Learning the blues isn't an easy task, but this video helps make it a little easier. The song you'll be learning is "Coffee Blues" by Mississippi John Hurt. It's in the key of A and is a typical blues progression, in an alternating bass. It's the chords A, D, and E. If you're yearning to learn the delta blues, this is a great first step.

This video illustrates the quick and easy method to Buy fresh ginger and brew a pot of ginger tea . The process is comprised of the following steps:Step 1: Visit a local store or a vegetable shop and buy some ginger. Identifying whether the ginger is fresh or not is a easy job. Just smell it and judge if the odor is strong. A strong odor indicates that the ginger is fresh.Step 2: Mesh the ginger pieces and peel off it's skin.Step 3: Take small pieces of ginger and add them to boiling tea.Step...

Beets are good source of folacin, vitamin C, and potassium. They also taste super delicious when you roast them in the oven. This video tutorial demonstrates a simple way to roast beets in your oven and shows a tasty vinaigrette serving method.

Purchase a silver XBox 360 faceplate from your local gaming retailer. You can also remove the faceplate currently on your XBox 360.

Transform a piquant herb into a creamy, sweet paste by oven-roasting garlic with the help of these tips.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

You Will Need * A fire extinguisher

Systm presents this detailed tutorial on how to make a custom Star Wars style light saber. Luke, Darth and Obi-Wan's Lightsabers were pieced out of junk piles. David shows you how to build exact replicas and an original design from The Custom Saber Shop. Then he picks a fight with Patrick.

Learn to make your own super effective bass traps and acoustic panels with materials from your local hardware store, just by watching this home audio video tutorial.

American economy is based on credit in the form of credit cards, loans and debt management. Learn about credit and credit cards from a credit counselor in this free personal finance video series.

Location-based gaming company Niantic knows its business model is inextricably tied to the outdoors, so it is in its best interest to help preserve that environment to give players a place to play.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

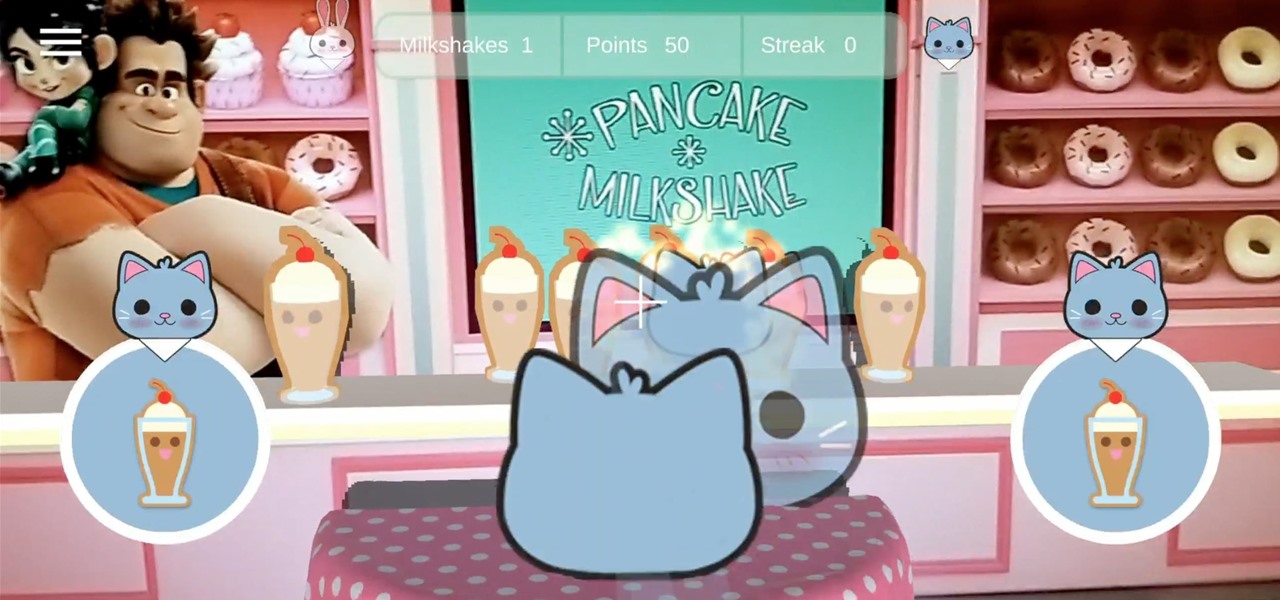
One of the funniest scenes from the teaser trailer for the Wreck-It Ralph sequel is the basis for the new pre-show augmented reality experience via the Noovie ARCade app.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.