Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

In today's world of ordering food from your PC or hailing a cab with an app, it almost seems archaic when we have to actually use our vocal cords to contact a local business. It sure would be nice if we didn't have to use our smartphones as, well, you know...phones.

Video: . How to Make My Famous Spaghetti.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

If you've seen ParaNorman or Fantastic Mr. Fox, then you have some kind of idea of what stop-motion animation is. Basically, these artists make objects, or small figures, appear to be moving on their own by manipulating and repositioning them in the smallest increments, then capturing each frame after doing so. When all the frames are compiled together, the final product is something spectacular like The Nightmare Before Christmas, which took roughly 109,440 frames in all.

Assuming that you're not going to knit a sweater and celebrate New Year's Eve with Ryan Seacrest and Jenny McCarthy on ABC's “New Year's Rockin' Eve," it's a pretty safe bet to say that you're probably going to consume alcohol—a considerable amount of alcohol.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

If you haven't walked into a department store or seen one of those millions of jewelry commercials airing over the last month, you might not know that February 14th is Valentine's Day.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Did you know that the average cost to make a penny is about 2.4 cents?!? That's why the Obama administration asked Congress earlier this year for permission to change the metals in the penny, hoping to get the cost back down where it makes sense.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

This video teaches the method to find the area of triangle using law of cosines and law of sines together with the area formula. Law of cosines is used when you have the length of three sides. It states that the square of side 'a' is equal to addition of the squares of sides 'b' and 'c' minus the product of 2, b, c and cosA. The values of sides are substituted and angle A is found. This is substituted in the area formula which states that the area of a triangle is equal to the half of the pro...

If you work for a company you are probably entitled to maternity leave. Gather as much info as possible and then have an honest conversation with your employers. With tact and civility should be able to have time to recover with your baby and keep your job too.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Thirteen isn't an unlucky number for this Limbo walkthrough; it's the number of videos in this series, a series which shows you the complete process, through trial and error, life and death, and as least amount of edits as possible.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Your best chance of getting to a destination on time during rush hour is to drive through relatively empty HOV lanes. Thankfully, if you're using Waze to navigate through traffic, you can easily locate HOV or HOT routes to optimize travel times by adding your toll passes in the app's settings.

Say you're on a train to work, but you forgot your headphones. You'd normally listen to music to pass the time, but given the circumstances, your choices are to sit silently like a considerate adult, or to blare songs out of your phone's main speaker like a jerk. Thankfully, there's now a third option.

Vodafone India has merged with telecom company Idea Cellular to become India's largest mobile player this week.

Sky Zhou, also know as Matrix Inception on YouTube, is no stranger here on NextReality. We loved his Pokémon concept game for HoloLens, as well as his D3D Keyboard that lets HoloLens users leave notes around the house. He just can't seem to stop creating cool mixed reality apps, and he's already got another one in the works.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Five Phases of Hacking:- The five phases of Hacking are as follow:

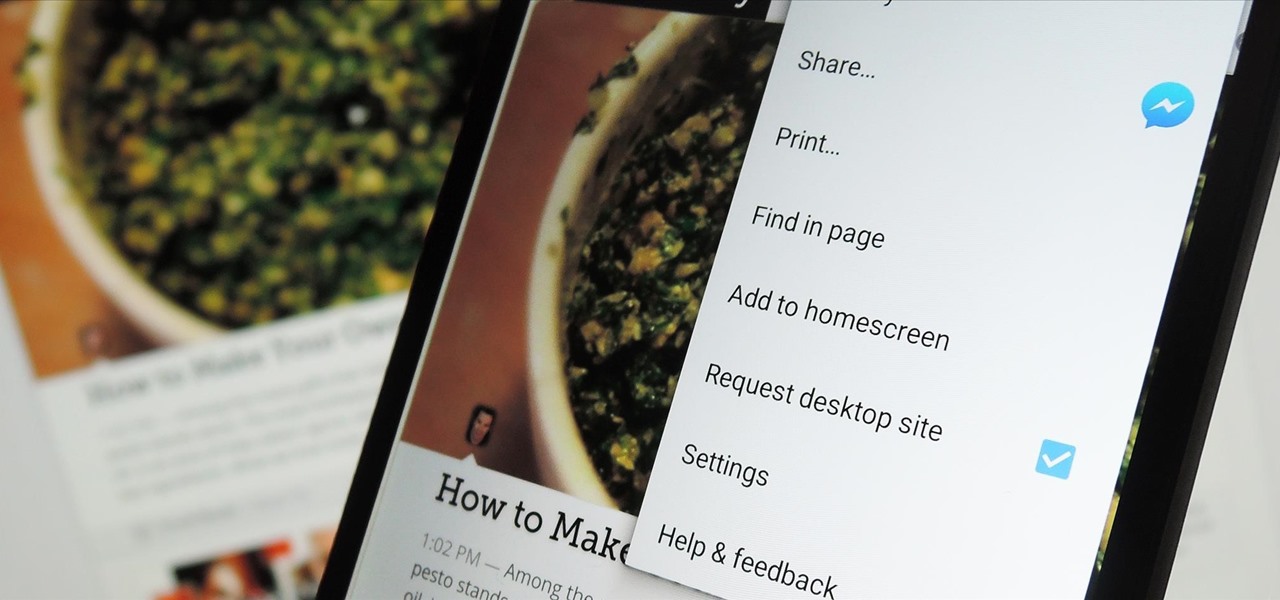
The majority of Android web browsers carry a "desktop mode" feature that makes mobile websites look like normal computer versions. Mobile versions are designed to work faster and more efficiently on smartphones, but sometimes the desktop version looks better on large displays or has additional features not included in the mobile one.

I wonder if Best Buy has any Note 3's for sale?? When trying to figure out when something is in stock, we usually either check online or call the store to talk to someone. If certain products are out of stock the process might be tedious, with having to find phone numbers and calling several stores.

The new Samsung Galaxy S4 may be the only phone to include temperature and humidity sensors, but your Galaxy Note 2 has a few weather-detecting features of its own.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

Even if you're not a hipster with your own self-sufficient garden, making your own edibles at home can be pretty cool. And while it's obviously easier to pick up a bottle of 7-Up at the store, there's something undoubtedly fun about making your own. For those addicted to their fizzy drinks, DIY soda is a great way to save some cash and make their drinks healthier with natural flavors and sweeteners, instead of something like corn syrup or aspartame.

Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.

Looking at homes is the fun part. But before you go house hunting, make sure you have your financial ducks in a row.

Learn how to exercise your dog. Follow a regular exercise routine together with your pet. It will benefit you both!

Learn how to use more English phrasal verbs with this instructional English language lesson. get...over with

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

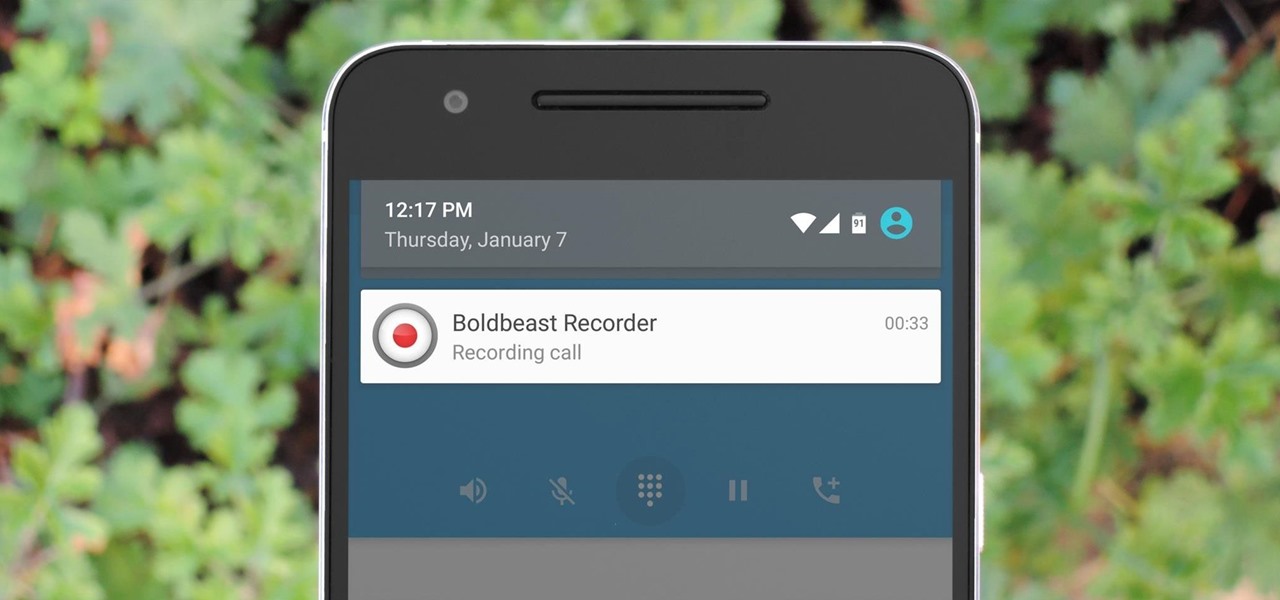
There are plenty of legitimate reasons that you might want to record a phone conversation. Let's say you operate a business and take orders over the phone, and you don't want to miss an item. Or perhaps you need to jot down some notes from a recent conference call, and things were just happening too quickly in real time.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

Fromage blanc cheese is something every cook should experience in the kitchen. To consider yourself a real chef, you need to grab the cheesecloth and dip your hands in the cow's milk, because making cheese is a culinary experience like no other.