I actually have a lot of shoes, and putting them on the floor in my closet just makes for a very large mess, and makes it harder to find a matching pair. So, this simple yet cool DIY shoe storage is actually something I could benefit from doing. This project shouldn't be too difficult to complete. You can get PVC pipe from your local hardware store and either have them cut it, or you can do it at home if you have a table saw. You can also opt to buy concrete forming tubes, which may be a litt...

With all of the advancements in the smartphone world, we can virtually use them for anything. You can use your smartphone as a mobile hotspot, an Xbox controller, a car locator, and a security camera. Heck, you can even turn it into a Swiss Army knife. And now you can even use it as a wireless mouse for your computer!

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.

Fluorescent dye can be a great addition for decorating around the house for Halloween, especially for a haunted one. Creating your own fluorescent dye is a simple experiment, as long as you've got the proper chemicals and safety gear. Nurd Rage details the chemical process of creating your own fluorescein below.
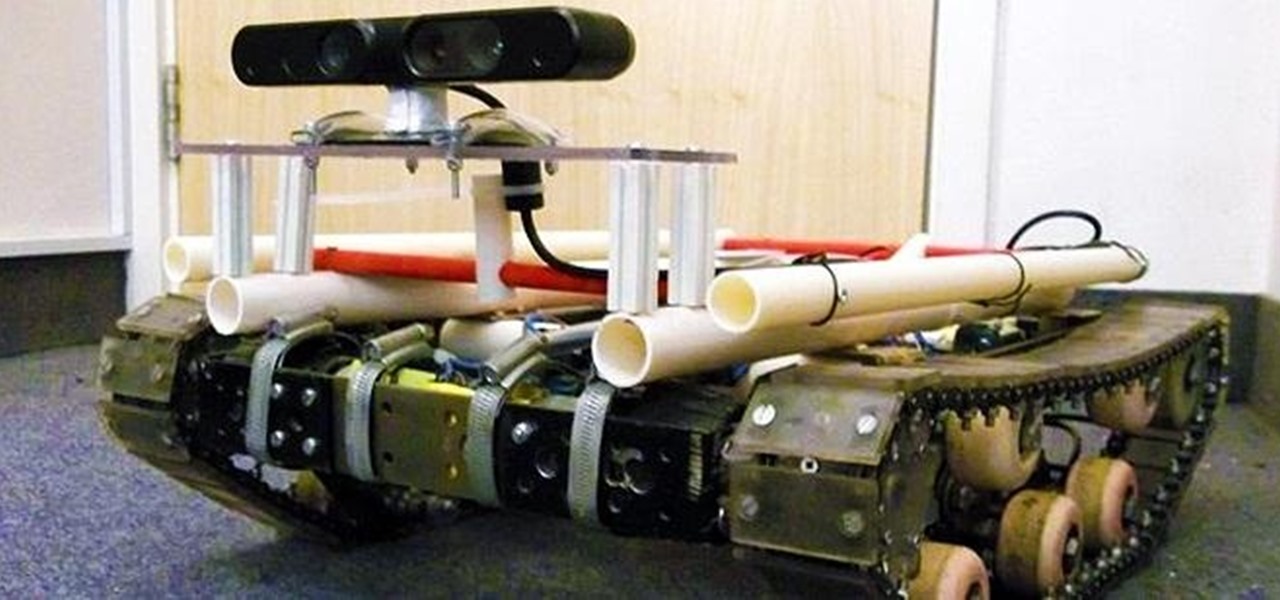
There are plenty of tank robots out there, but how many of them can recognize 3D objects and map their environment? Tanky, the tracked mobile robot, can do all that and more while rolling around on his bicycle chain treads. Created as a Master's thesis project, Tanky is made almost entirely of parts you can find at your local hardware store. It was built in two "layers" with the motors, electronics, and batteries on bottom and the processing unit, a laptop, on top. The motors came from cordle...

Wall Anchors. Drywall Wall Anchors. Plasterboard Wall Anchors. I discovered these plasterboard (drywall) anchors / plugs a few years ago and think they are fantastic. They are ridiculously easy to use and are extremely effective in attaching fixtures to walls. One of the main things to be aware of (as with all things that have fixtures hanging from them) is the recommended maximum weight loading of each size of anchor. What ever the packet says, adhere to it.

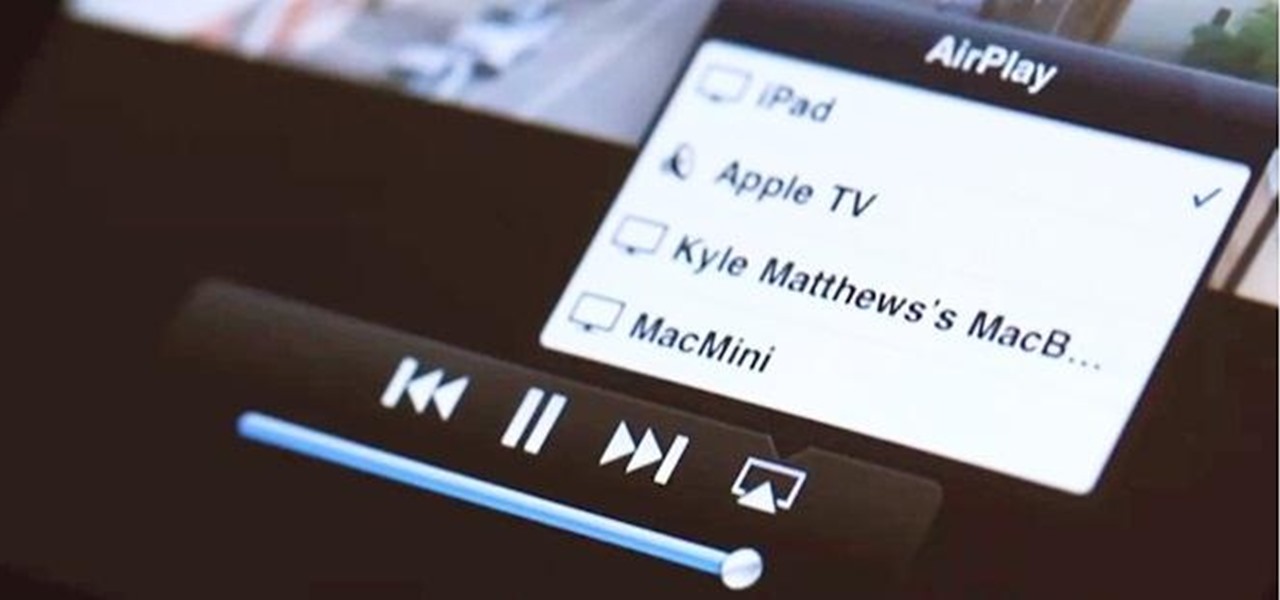
AirPlay is probably one of the most underutilized features in Apple products. It allows users to wirelessly stream photos, music, or video directly from their iPad, iPhone, iPod touch or Mac to their Apple TV or AirPlay-supported speakers. The Apple support page has a complete list of all the supported and needed devices. Mirroring is also available, but only for the iPhone 4S, iPhone 5, and iPad 2, all of which need to be running iOS 5 or later.

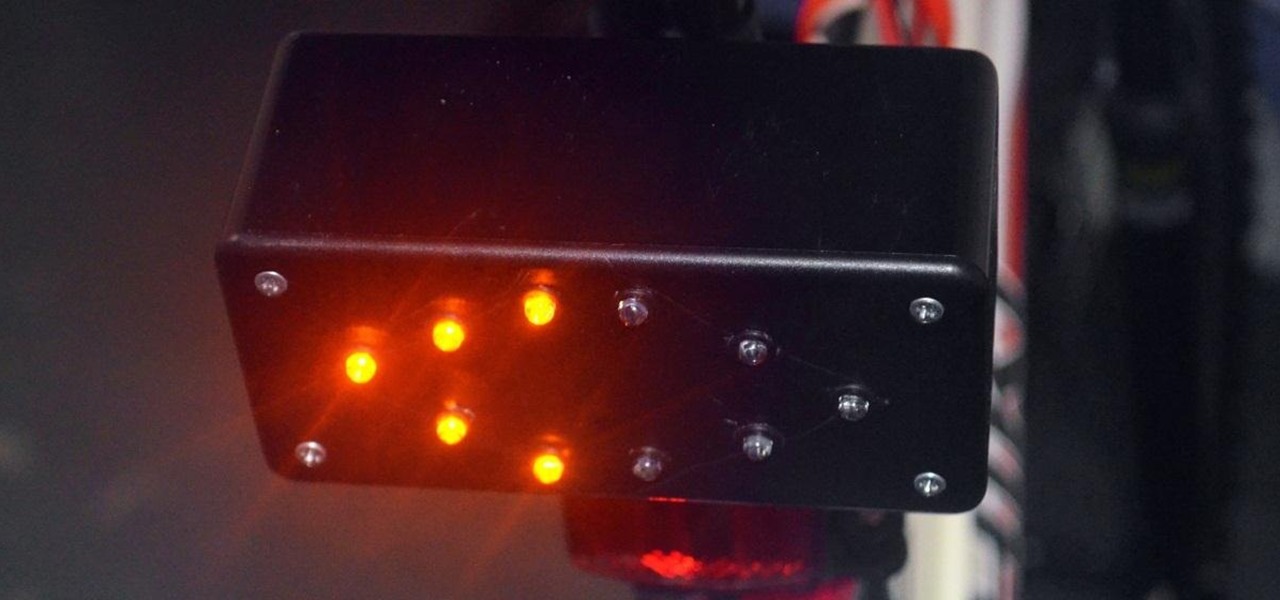
In the past few weeks, you've already learned how to make your bike light up at night with some DIY rim lights and handlebar lights. But how about something a little more functional? Instead of using those tedious hand signals (which drivers don't even understand), spruce up your ride with some do-it-yourself LED turn signals.

Are you getting that nasty "Application access set to not allowed" error on your Nokia 5300 cell phone? Unfortunately, it's a problem for most Nokia 5300 owners, ones who wish to use 3rd party applications on certain carriers, like T-Mobile, who restricts the uses for branding.

In this tutorial, professional referee, James Armstrong teaches you all about two of the most commonly forgotten rules of basketball. In the NBA, you rarely, if ever, see violations for things like traveling and lane violations.

Fish & chips is the most popular fish meal in the country, & you can make it yourself instead of paying a fortune at your local fish eatery. The special ingredient for these fish and chips… beer.

Imagine a game almost anyone can play that combines the best of skee-ball, bowling, and shuffleboard. Welcome to the ancient sport of bocce.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Have you ever wanted to go into another user's account on your computer but had trouble finding the energy to log out, then log out, only to log back into your own account? Well, here's your solution: XNest will let you log in to another user's account from your account in a virtual way. It's very simple to set up and may just help you with your virtual account crisis!

Benny from askbenny.cn teaches you how to say some local proverbs and sayings in Mandarin Chinese. Part 1 of 2 - How to Say Chinese sayings and proverbs.

Make sure the bike is properly fit to the child. She should just be able to stand over the top bar of the frame without touching.

Elvira, Mistress of the Dark, was created in 1981 by Cassandra Peterson. She was the hostess of a local Hollywood horror movie show that became nationally syndicated. Elvira was the first horror host to be nationally syndicated, first person to be broadcast in 3-D on TV, and first female celebrity to do a national beer campaign and market her own beer.

Would you know what to do if someone ingested poison? Equally important, would you know what not to do?

You already know the mechanics of DJing, but you want to be an international celebrity -- or at least drink for free while showing off your music collection. Here's how to spin your hobby into a career. Watch this video to learn how to become a professional club DJ.

Learn how to choose an indoor plant. You don’t need a green thumb to have houseplants that flourish; you just need to know which ones will thrive in your home.

Download the P2 Step-by-Step Reference Guide. With Avid, editing footage captured with the Panasonic HVX200 camera is fast and easy. Avids system uses the same native file format as Panasonic P2 memory cards, so theres no need for any transcode, capture or file conversion process at all. You can edit directly and immediately from the P2 cards if you like or have Avid Media Composer create a rapid backup of your files. Nothing could be simpler or more immediate.

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

There are loads of reasons for somebody to want to recover a Windows password, and there are lots of different ways of doing it. My favorite of all of these ways is to use a piece of software called Ophcrack because:

I feel like doing a bit of chemistry today, how about you? To my knowledge, thermite is the hottest burning man-made substance. Thermite is a pyrotechnic composition of a metal powder and a metal oxide that produces an exothermic oxidation-reduction reaction known as a thermitereaction.

Apple finally unveiled the iPhone 14, 14 Plus, 14 Pro, and 14 Pro Max, and there are a lot of improvements that'll make you want to trade in your current iPhone stat. But I wouldn't be so quick to upgrade because there's one "feature" that will make many of you rethink getting a new iPhone 14 series model.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.

As government officials scramble to contain the new coronavirus outbreak with bans on large gatherings, travel restrictions, and school closures, the rest of us have to worry about how we're going to safely purchase water, toilet paper, groceries, and other household goods during the global COVID-19 pandemic.

Whether you were exposed to the COVID-19 virus or just taking precautionary measures, self-quarantining is a tremendous disruption for anyone. Still, we all have to eat, pandemic or not. But unless you like eating canned food for two weeks, you're going to want to explore other options. That's why food delivery apps are going to be so necessary during such a hectic and uncertain time.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

I've just recently hopped on the AirPods bandwagon, and I can't see myself ever going back to the wired EarPods that Apple includes with every iPhone. The only issue is that I paid full price, but you don't have to with 2019's Black Friday deals, some of which are happening right now.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.