In this video you will learn how to check your internet speed without using any software. In order to do that just follow these simple and quick steps and instructions: The first thing that you need to do is to double-click on your Local Area Connection icon. A window will appear and you will see what your speed is on the right of it. The speed of your internet will be in Mbps. If you follow these easy and quick steps you will now how to check your internet speed without using any software or...

A cold frame is a great way to extend the growing season in your garden. When you set up a cold frame, you can keep your plants healthy and growing, even when it's cold outside. In this video tutorial, you'll learn how to set up and use a cold frame.

Aerating your soil is an essential part of gardening, but it can be long and back-breaking work. In this episode of Growing Wisdom, Dave Epstein will teach you how to use a broadfork to aerate your soil. Using a broadfork, you can aerate the soil without damaging the soil's ecology.

With the growing popularity of buying local, many people are rediscovering the benefits of preserving fruit at home. Concerns over food origin, additives and preservatives are driving this trend and in just 20 minutes you can enjoy fresh produce all year long. Watch this how to video to learn more about picking fresh food and the preservation process.

Looking for a great idea for a science project? In this video series you'll learn how to build a battery-run light board which can test the electrical conductivity of various objects. You can find these supplies easily at your local hardware store.

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

When you start to play golf, you will need to know certain things like how to keep score and follow the game. When looking at a golf scorecard, there is typically a list of local rules listed, and these rules should be taken into account in addition to USGA rules. Find out how handicaps indicate the difficulty of a hole in golf in this helpful tutorial. So, if you are ready to start playing, follow along with this video and start taking proper score.

It can be a real challenge to plant your seeds in evenly-spaced lines. In this episode of Growing Wisdom, Dave Epstein will show you how to use a four-row pinpoint seeder to plenty your seeds. Using devices like this, planting seeds in even lines will be a whole lot easier.

Breathing is a skill to master before trying advanced swimming strokes. Learning to breathe while swimming will enable rapid progress. Get expert tips and advice in this swimming video tutorial.

It may not seem like a big deal, but sometimes when your filenames are being saved in the incorrect case, it is. If you save a file with uppercase letters in the name, your computer may change them to all lowercase. This occurs when downloading files form a host server to a local hard drive. But what if you want them back how you had them? Well, there's a small Windows tweak you can use to stop it from happening. Learn how!

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

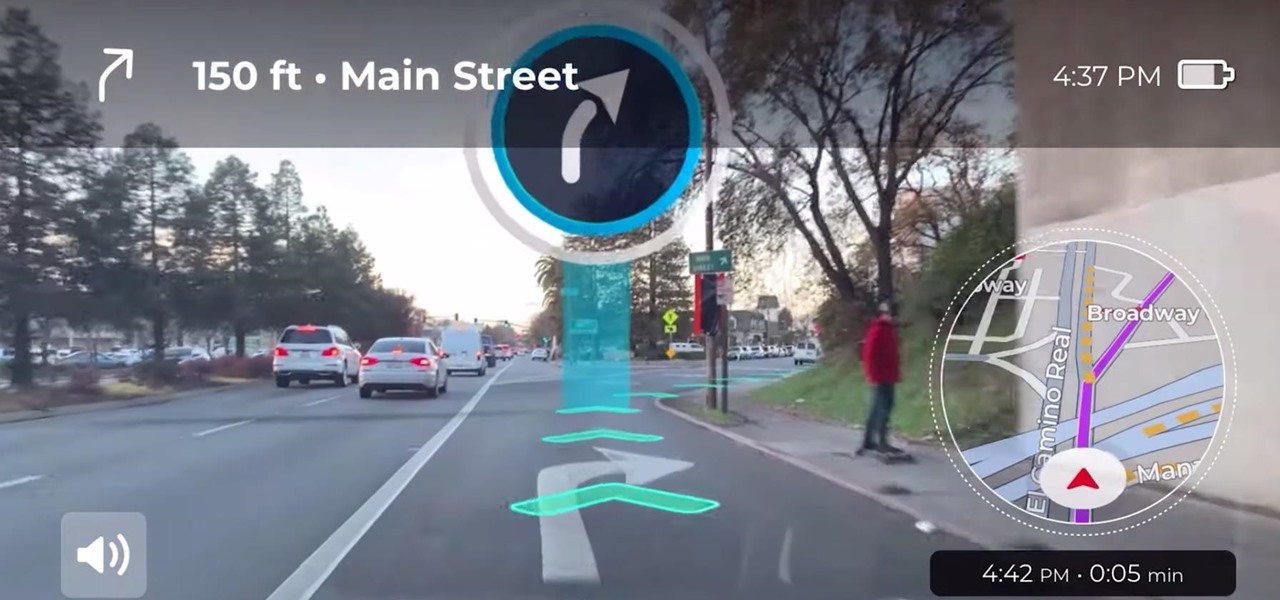
Google pushed a new kind of augmented reality walking navigation to the mainstream last year, and now startup Phiar is hoping users will use its AR app in the same way for driving navigation.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

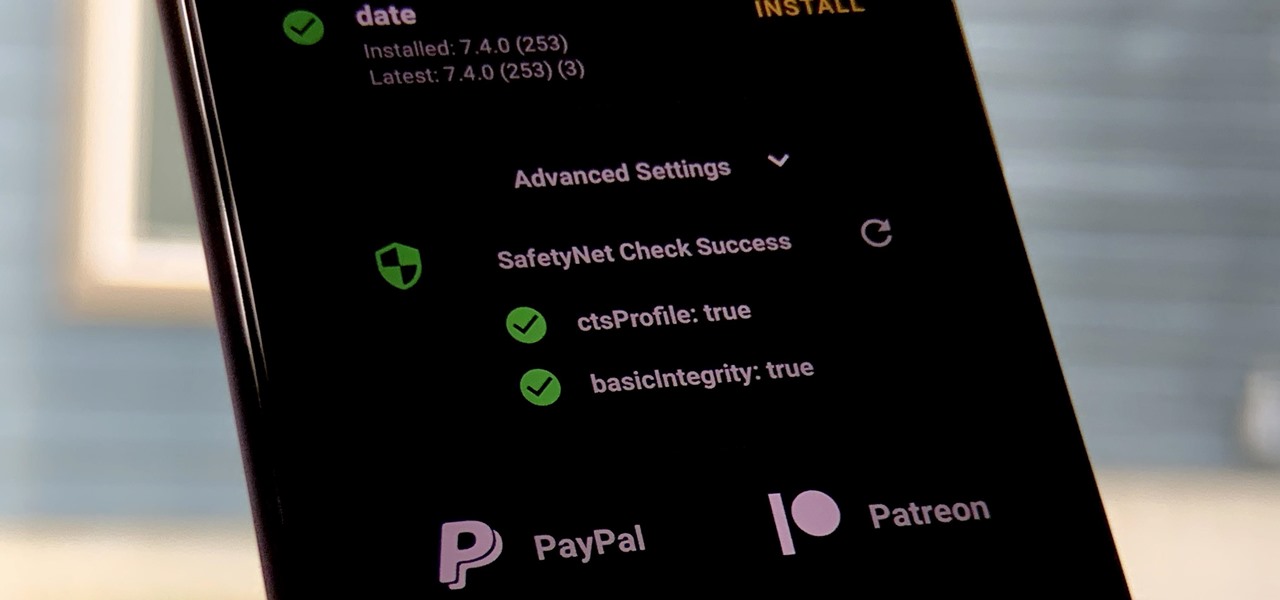
One of the longest-running cat and mouse games in Android has to be that of Google's SafetyNet feature and specific apps that can trip the flag. Many developers have resorted to using Magisk to create their modules since it can systemlessly pass SafetyNet in most cases. However, EdXposed is having some issues passing SafetyNet right now, which affects more than just your mods.

Best known for its mobile phones and television sets, South Korea's LG has had a quieter presence in the US compared to the country's homegrown efforts.

Apple revealed its newest line of iPhone models on Tuesday, Sept. 10, at its "by innovation only" event in Cupertino. While the release date for iOS 13 wasn't announced at the event, Apple issued a press release with the date. If you missed the event, you can still watch it from your computer, smartphone, Apple TV, and any other device that YouTube works on.

In recent years, augmented reality has increasingly helped to take art off museum walls and bring it (virtually) into people's homes and communities, offering new perspectives on classic pieces and modern creations alike.

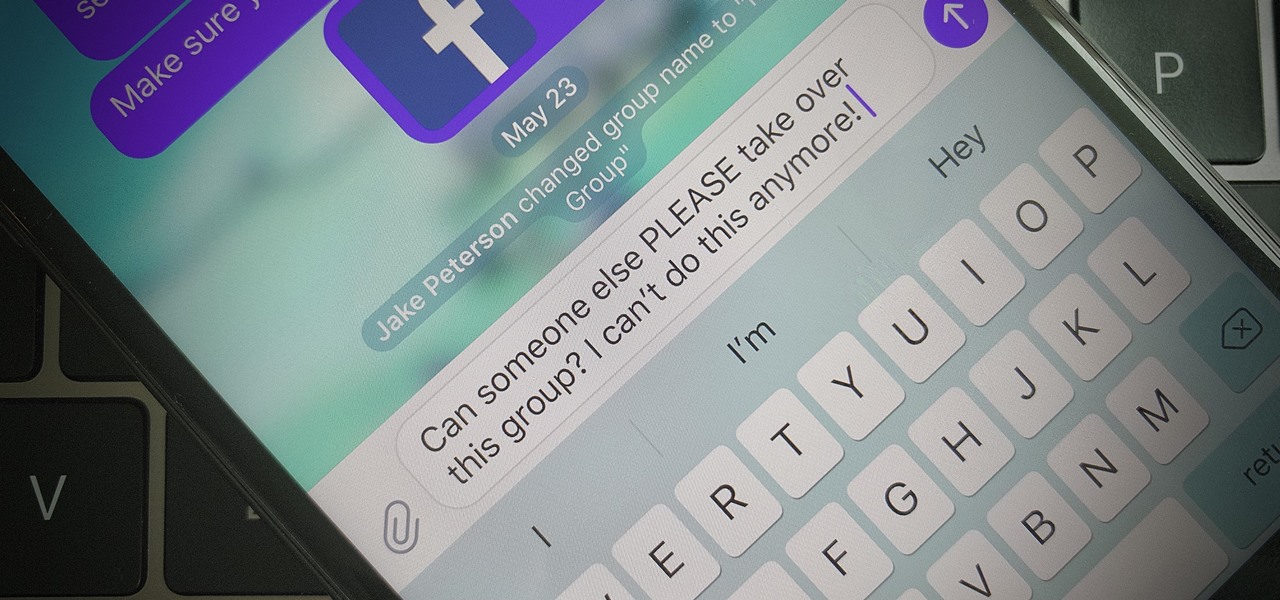
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling overwhelmed with administrative responsibilities, why not pass on that burden to another member of the Telegram group?

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

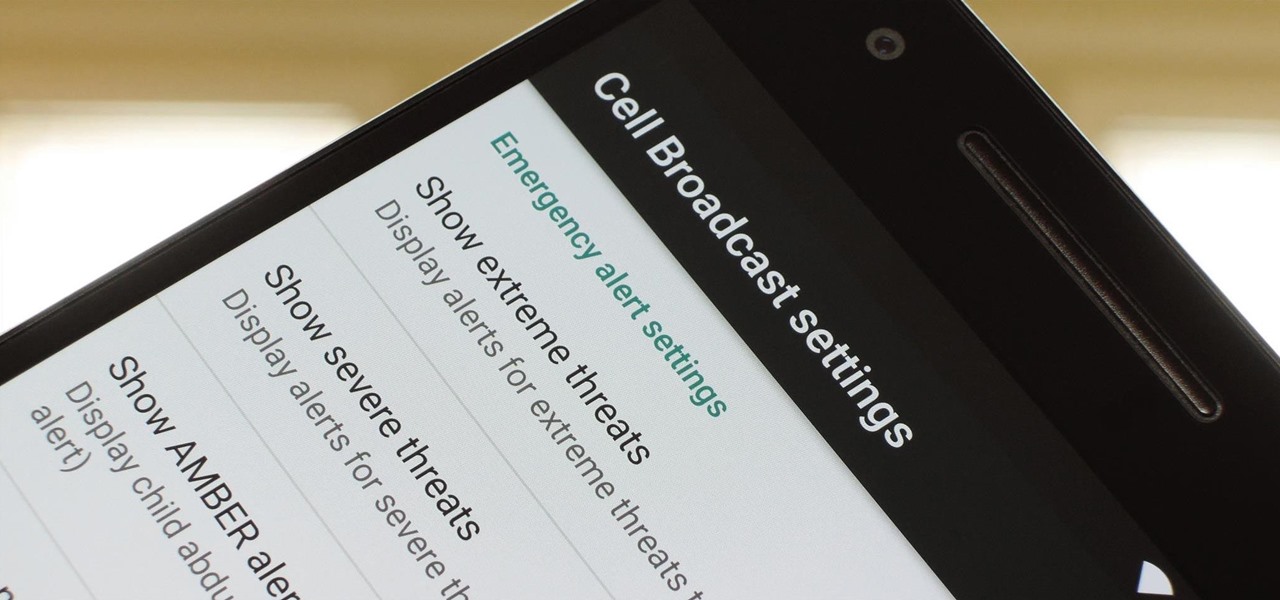
To bring things up to code with a new FCC standard, Android recently added an "Emergency broadcasts" feature that will make your smartphone notify you whenever a potential safety threat or Amber Alert is posted in your area. Even if you have your phone set to silent, these emergency alerts will cause your device to emit a loud, piercing sound when a potential threat is nearby.

The long guarded veil of mystery surrounding Magic Leap for years was finally lifted last year when the company revealed its Magic Leap One device.