JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

In late June, the biggest measles outbreak to strike Minnesota since 1990 seemed to be winding down. Today, public health officials announced a new confirmed measles case in the area.

Rabbits have been a persistent problem in Australia for over 150 years. Now the Peel Harvey Catchment Council (PHCC) and Peel-Harvey Biosecurity Group have released a strain of the rabbit haemorrhagic disease virus (RHDV), called RHDV1 K5, to reduce the number of pests in the Murray region of New South Wales.

Antibiotic-resistant infections that usually occur only in hospital settings are spreading in communities, increasing hospital stays—and danger—for young children.

Step aside, Heinz: there's a new ketchup in town. Beetroot ketchup is the rising star of condiments. It's a vibrant, earthy, and sweet topping for summer BBQ burgers and grilled hot dogs, as well as a pretty un-beet-able dip for French fries. There's no corn syrup, it's paleo-friendly, and the beets give it a bright, bold flavor like no other sauce you have ever tasted.

Mochi seems to be everywhere these days: as a topping at your local frozen yogurt shop, in ice cream balls (the green tea ones are heaven), and as colorful treats all over Instagram. It seems like mocha mania is in full force!

You can now access Google's slick Weather app without having to first open the Google or News & Weather apps. However, you will have to use Google to access the weather the old-fashioned way one more time, but you'll have the option to place a shortcut on your home screen to access the weather directly going forth.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Cooking on a budget isn't always easy, but there's a silver lining: it can be really fun. Ever since I started supporting myself I've enjoyed going shopping, finding the most affordable items, and learning how to make the most of them. Sure, sometimes I wish I could afford to buy a filet mignon and some morel mushrooms every night, but there's a different kind of enjoyment that comes from being able to turn a few dollars into a gourmet meal. For me, that means starting with cheap meat, and af...

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

Like most people who spend a good deal of time in front of their computer—whether for work, school, or play—I jump back and forth from window to window, working and playing with different things at the same time to get my work done faster or procrastinate harder.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

While CNN, FOX News, and MSNBC are valuable sources of information for what's going on in the world today, they may not be the best news stations to watch if you actually want to learn something. They, along with local news stations, are great at grabbing your attention, but if you truly want to learn something about recent events, you're tuning into the wrong channel.

Mirror, mirror on the wall, who is the fairest of them all? Besides being one of the most notorious misquotes of all time (the line is "Magic Mirror on the wall, who is the fairest of them all"), it's a question that men and women probably have asked themselves more than once.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

Once you unlock your bootloader and root, you're left with one more hurdle to overcome, and that's getting S-Off.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

The mother of all games is almost here. Super Bowl XLVIII pits the Seattle Seahawks (or Seachickens, if you're from the Bay Area) against the Denver Broncos and regent exemplar of neck surgeries, Peyton Manning.

It's no surprise that Costco has great deals, and that's why millions pay annual fees for the privilege to shop in their wholesale outlets. Just take their hotdog and soda combo for $1.50—it's the same price now as it was 27 years ago.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Everyone listens to music. I've got over 3,000 songs in my iTunes library, but am always looking for more, and I'm sure you are too. You can never have enough tunes to rock out to, right? If you're using Windows 8 like I currently am, these are some of the best apps in the Windows Store right now that will help you find new jams for your collection.

Autodesk Maya, affectionately known as just Maya to its users, is a 3D computer graphics software that makes it easy to create impressive, realistic models of real-life - or imagined - objects. Super useful for graphic designers, film makers and web designers, the program is one that you should study if you're looking to go into one of the fields above.

For most of us, putting on makeup is a real drag in the mornings. Don't get us wrong: We love looking not fatally ill when we head into the office, but when your eyes can barely stay open and it's still dark outside, applying foundation is the last thing we want to do.

Warwick is one of the champions your summoner can bring onto the Fields of Justice, whose speciality is jungling. This tutorial lays out the best items, glyphs and masteries to take advantage of his innate talents so you can ensure victory in your next League of Legends game.

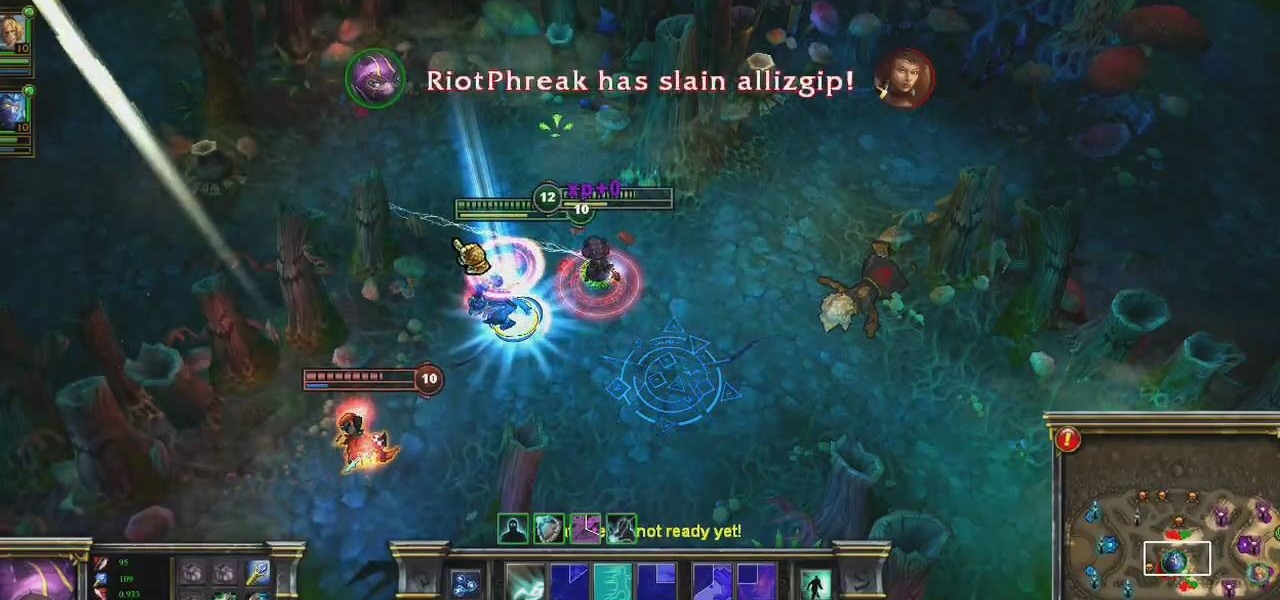
Time to get started playing League of Legends! This recently released game is a completely free to play multiplayer online battle area game. Play a powerful summoner and pit your chosen champion against your oppnents and defend your tower! Here's an easy guide to getting started playing League of Legends.

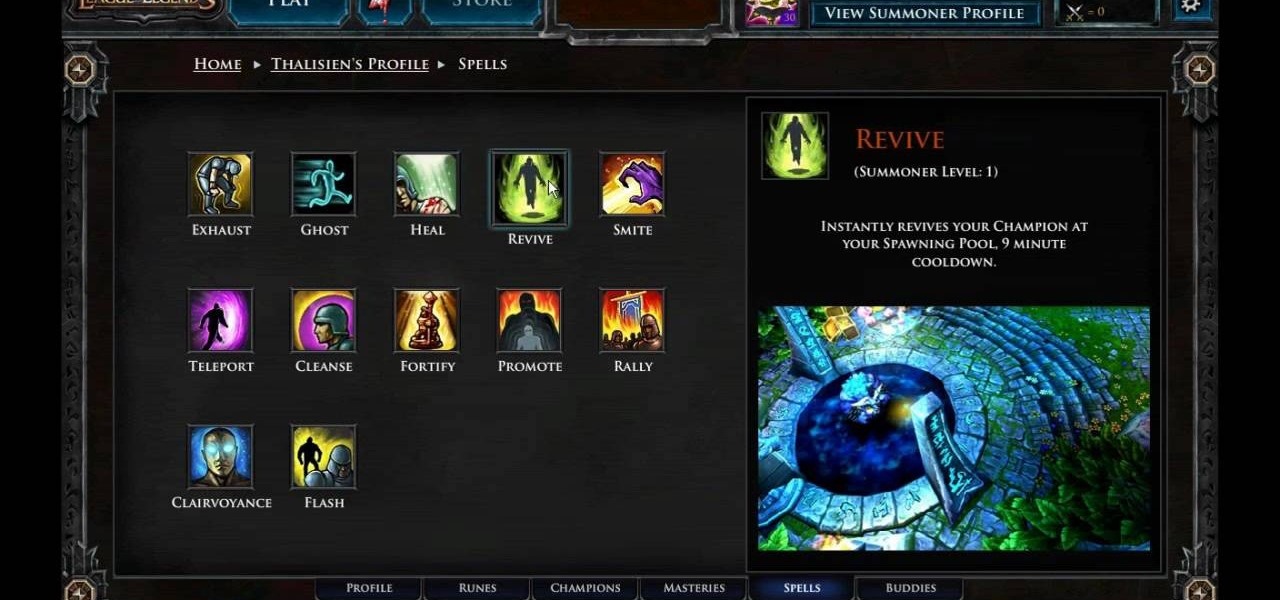
Your summoner is the core character in your League of Legends game, the one who summons the champions to fight on your behalf on the Fields of Justice. Going screenshot by screenshot, the summoner aspect of the game is explained. Stay up to date on your score, monitor your champions and keep track of your points!

Miss Fortune excels at ranged DPS combat on the Fields of Justice. Here's a good overview of this champion for League of Legends, which gives some useful tips and strategy ideas for building her and bringing her into battle.

Play an ice phoenix as your League of Legends champion! Here's a tutorial that shows you how to build Anivia the Cryophoenix to maximize her damage capability. She's not fast, but she can hit hard and ensure victory for your team on the Fields of Justice.

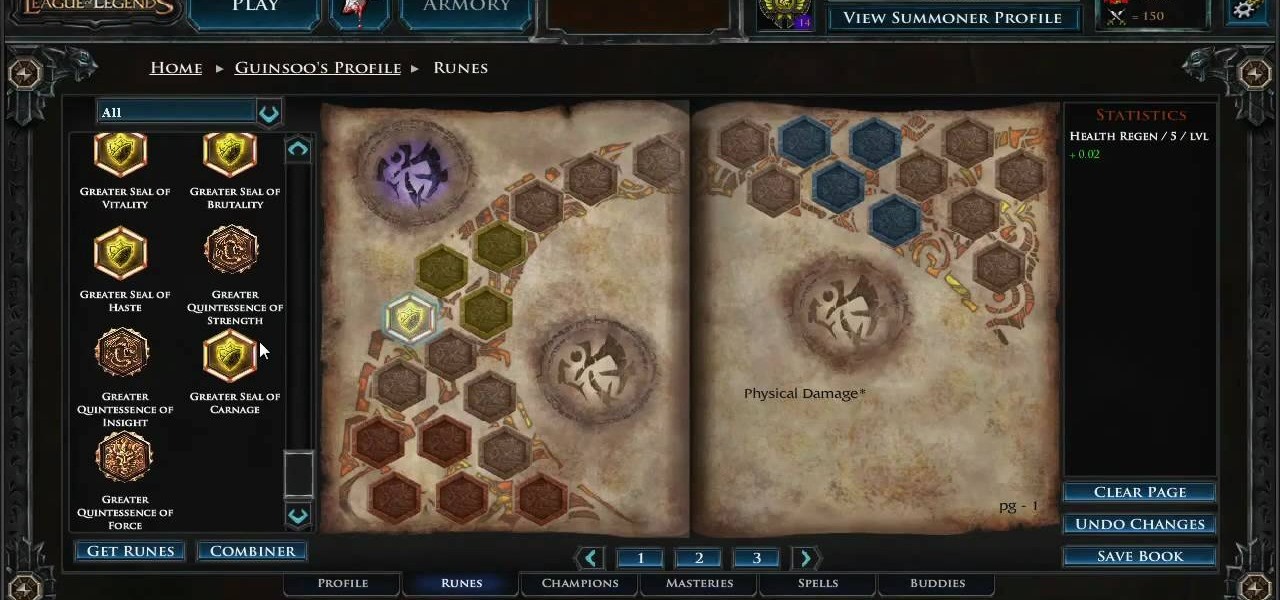
Runes are special abilities in the game which allow you customize your summoner in League of Legends. Here's how to equip runes and unlock the abilities to accumulate more runes. You can even save rune configurations in your tome and combine them to create special runes!

This spotlight focuses on Garen, the Might of Demacia, a melee champion who can be brutal with a sword. This video goes over how his abilities let him deal a great deal of damage to others while taking very little himself. Here are also some useful strategies when it comes to playing Garen in a battle.

Heimerdinger is one of the weakest champions in League of Legends, but that doesn't mean you can't still win with him! This video shows you useful strategy tips when you play the Revered Inventor based on his unique abilities and the optimized build to ensure victory for your side.

Is Kennen one of your favorite champions to play for League of Legends? This strategy guide goes over how to best use the unique abilities, masteries and optimal items to make sure this tiny ninja fights his best for your summoner!

You wanna play too? It'll be fun! This is a video which explains the best way to play the rather creepy nuker Annie, the Dark Child. Achieve victory for your team by making sure you've optimized her abilities, spells and items!

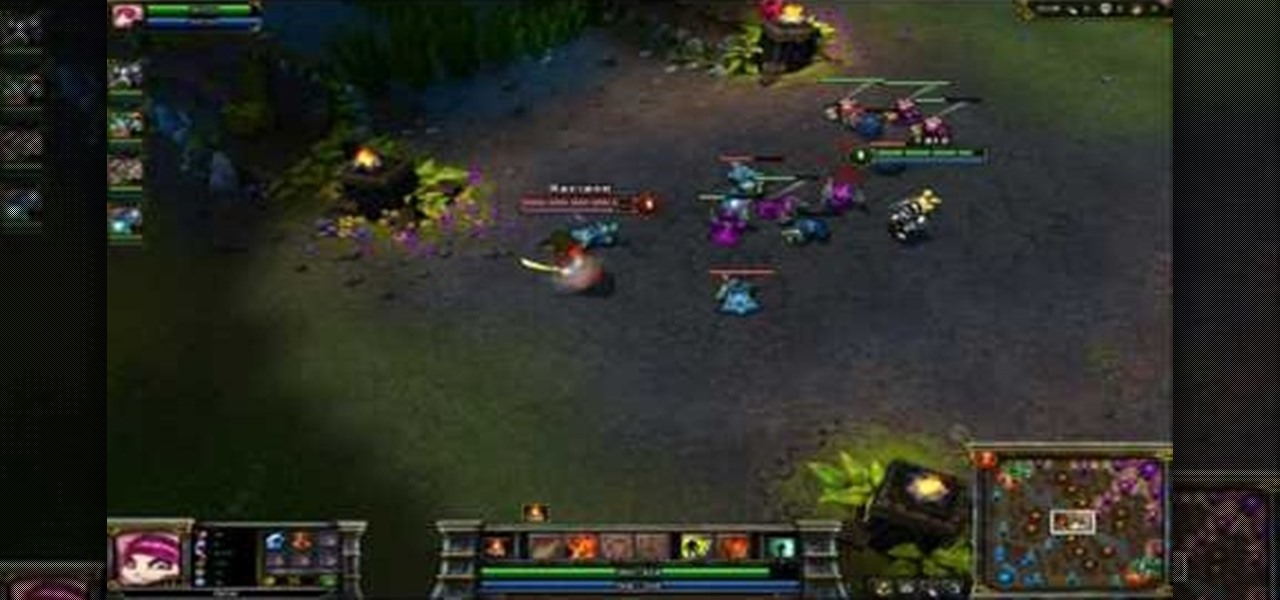
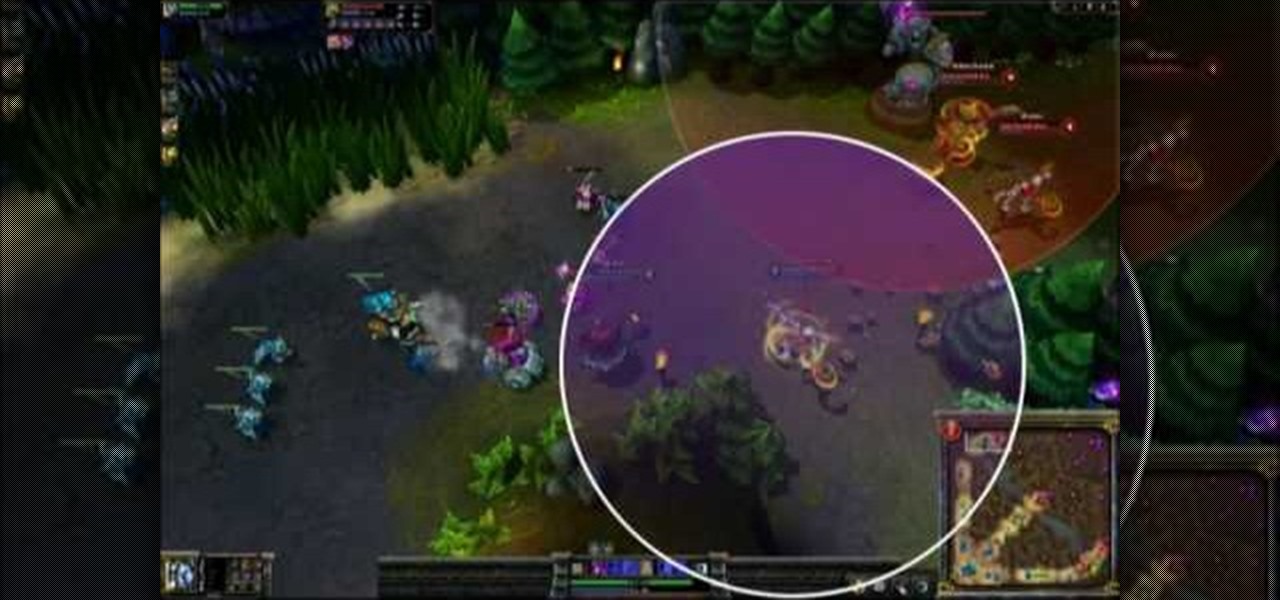
Keep your enemies at bay and control as much space on the map with your champion as possible. This tutorial shows you how to dominate the map for greater control during your League of Legends game. Be aware of your surroundings, and learn a few tricks to get out of a bad spot when you're trapped by enemies.