Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

February may be the shortest month of the year, but for iOS softModders, there were plenty of apps and tweaks to fill up those days. Whether patching major security holes or just a tweak to make speed dialing more efficient, there was a plethora of great mods for our jailbroken iOS 7 devices. These are our favorites from the month.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

I'm one of those types of people who waits until the very last minute to find a Halloween costume, and thanks to last year's attempt at buying one at a local costume shop the day before Halloween, I will just settle for the things I have lying around in my house from now until eternity. It's like Black Friday chaos, only with more gropers.

No matter what the clean freaks out there try to tell me, I still drink my Los Angeles tap water without a care in the world. I figure that I've already consumed much more heinous things in my lifetime. Street vendor "steak" burritos comes to mind.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

The big fireworks day is almost here, but most of you are limited in what you can do when it comes to celebrating the Fourth of July with a bang. Unless you live in a dry area prone to wildfires, one type of fireworks you can probably still legally buy are sparklers.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

A deck of cards may be a magician's best way to demonstrate his or her's sleight of hand, but for the prankster, it's the perfect way to deliver a shocking 300 volts of electricity! And that's exactly what I'm going to show you how to do today. Stuart Edge used it in his "Electric Shock Kissing Prank" to show the ladies how a man can really put the sparks in a kiss.

McDonald's is probably the most recognizable fast food chain in the entire world, with over 34,000 restaurants in more than 100 countries. In may not be the healthiest place to get a meal, but like millions of kids in America, I grew up on McDonald's unquestionably delicious products—and I'm still alive.

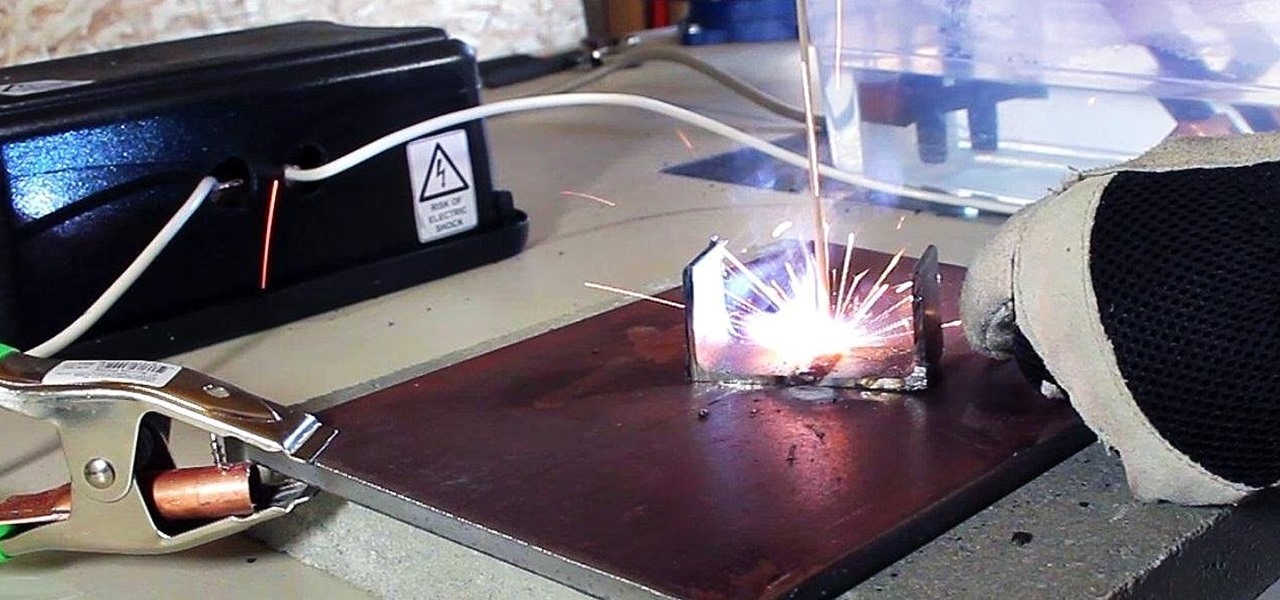
In a previous article, I demonstrated an Arc Welder made using parts from old microwave ovens. Video: .

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

It might be time to move those Instagram photos to another service. It seems that Instagram has never heard of the phrase, "If it ain't broke, don't fix it." In a very big WTF moment, the extremely popular photo sharing and editing app decided that it has the right to sell its users photos to third parties without pay or notice. Yep, you heard that right. That photo you took of your girlfriend laying out on the beach could be in the next stupid Corona commercial without your consent and witho...

Yes, you read that right—you can now get Google Maps back on your iPhone again. It may not be officially replacing Apple's notorious Maps app, but it sure is a sight for sore eyes.

Once you have the skills to bring your ideas to life, the hardest part is coming up with ideas. What do you do when you can't think of something to make? What happens when your well of inspiration runs dry?

With the recent announcement of our server shutting down, it's time to get in and save the things you've made. However, this will work on any CraftBukkit server as well, and gives no extra strain to the server as the work is all done on your local computer.

When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll.

Since it's October and Halloween is fast approaching, it's time for a series of articles on how to make the coolest Steampunk Halloween decorations for your home! In this installment, we'll look at some jack-o'-lanterns, skulls, and a few other things that are easy to Steampunk, but will still keep that "spooky" Halloween feeling.

There's only three weeks left until the spookiest holiday of the year, which means stores and costume shops everywhere are bringing out their Halloween inventory full force. So now's a good time to start prepping your Halloween costume—because you really don't want to do it last-minute again, do you?

There's nothing like buying an awesome new gadget, but it leaves you with one problem (besides an empty wallet)—what do you do with the ones you already have? There are plenty of ways to put your old gadgets to use, but if you'd rather get rid of them, you may as well get something out of it, right? Here are five places where you can recycle your electronics and replenish your cash stash.

I know, "Steamdown" conjures images of a hoedown, but "Steampunk prop breakdown" is a bit of a mouthful, I thought.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

Summer is in full swing! Everywhere you look, plants are in full bloom and green is a way of life. Gardeners are clearly living up to their full potential. I cannot think of anything else that personifies summer better than gardening.

United Arab Emirates is the cosmopolitan country that offers various attractions for tourists across the world. This country has buildup its image as one the fastest growing country of this region. Besides visiting worth seeing places, travelers can also enjoy tasty traditional food of UAE across the country. Whether you have chosen Dubai, Abu Dhabi, Ajman or Ras Al Khaimah, you will get the chance to enjoy best traditional food everywhere.

Computer Science Professor Francesco De Comité has a fantastic gallery of mathematical images on Flickr. As part of this collection, he has a few hundred images of real or rendered polyhedra made out of paper or playing cards which he calls "slide togethers." These are constructed by making cuts and then sliding one component into the other, creating a shape without using any glue. He constructed the entire set of the platonic solids—the cards form their edges—which can be seen in the image b...

SCRABBLE was invented by Alfred Mosher Butts, an architect in New York, in an attempt to make a word game that combined anagrams and crosswords, which involved chance, luck and a great degree of skill. Together, Butts and game-loving entrepreneur James Brunot, refined the game and made the games by hand, stamping letters on wooden tiles on at a time. They eventually came up with the name SCRABBLE, which means "to grope frantically."

Flank steak is an increasingly popular cut of meat in restaurants and on dinner tables. In this tutorial, the guys from Straight From the Block bring you a unique way of cooking this delicate cut of meat. This recipe is for pancetta stuffed flank steak, and it is easy to prepare and sure to impress.

Skulls. What spooky Halloween décor or staging of Hamlet is complete without a skull or two popping up? For ghoulish special effect and/or setting a dramatic scene, skulls are absolutely integral. Well, with some artistry, hardware supplies, and a good dose of patience, you can create your own inexpensive prop skulls for use however you please.

If you work for a company you are probably entitled to maternity leave. Gather as much info as possible and then have an honest conversation with your employers. With tact and civility should be able to have time to recover with your baby and keep your job too.

Using different sounds on your iPhone for different notifications can help you determine — just by listening — alerts you may want to look at immediately versus untimely alerts or even ones you typically ignore. But Apple has never given us complete control over notification sound customization on iOS, though the latest iOS update is a step in the right direction.

Wireless emergency alerts help warn mobile phone users of imminent threats to life or property, such as extreme weather and natural disasters. These alerts target affected geographic areas and come with a loud sound scary enough to make you want to turn off emergency alerts altogether on your iPhone, but there's a way to keep emergency alerts without the ear-splitting, intrusive sound.

You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.

The Apple Watch is rapidly becoming a standalone device that you can use without an iPhone or internet connection, and Deezer and Spotify have just helped make that even more true by adding support for offline playback on the watch.