Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

In today's world of ordering food from your PC or hailing a cab with an app, it almost seems archaic when we have to actually use our vocal cords to contact a local business. It sure would be nice if we didn't have to use our smartphones as, well, you know...phones.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

If you've seen ParaNorman or Fantastic Mr. Fox, then you have some kind of idea of what stop-motion animation is. Basically, these artists make objects, or small figures, appear to be moving on their own by manipulating and repositioning them in the smallest increments, then capturing each frame after doing so. When all the frames are compiled together, the final product is something spectacular like The Nightmare Before Christmas, which took roughly 109,440 frames in all.

Assuming that you're not going to knit a sweater and celebrate New Year's Eve with Ryan Seacrest and Jenny McCarthy on ABC's “New Year's Rockin' Eve," it's a pretty safe bet to say that you're probably going to consume alcohol—a considerable amount of alcohol.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

If you haven't walked into a department store or seen one of those millions of jewelry commercials airing over the last month, you might not know that February 14th is Valentine's Day.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

How to inflate a flat tire...if you're a pyromaniac. This creative solution to a flat tire uses fire to swell the rubber and get you back on the road.

Safety is important. If you are going to be riding a bike at night, make sure you are wearing light colored clothing and that you have lights. Lights help cars and other cyclists see you in the dark so you stay safe.

To change your tire on your dodge charger you need your jack, your spare, and your lug tool. To change the tire you will take the jack and place it under the proper spot underneath the car. You will find that the lug tool from your American car to look a bit different than a lug tool from a foreign automobile. A foreign tool will not be as bendable. Engage your emergency brake while changing your tire to prevent the car from moving especially if you have a flat by the side of the road. By rot...

Play "Scream" from High School Musical 3, an acoustic guitar tutorial. Follow along with this demonstration, tabs & lyrics here:

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Your best chance of getting to a destination on time during rush hour is to drive through relatively empty HOV lanes. Thankfully, if you're using Waze to navigate through traffic, you can easily locate HOV or HOT routes to optimize travel times by adding your toll passes in the app's settings.

Say you're on a train to work, but you forgot your headphones. You'd normally listen to music to pass the time, but given the circumstances, your choices are to sit silently like a considerate adult, or to blare songs out of your phone's main speaker like a jerk. Thankfully, there's now a third option.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

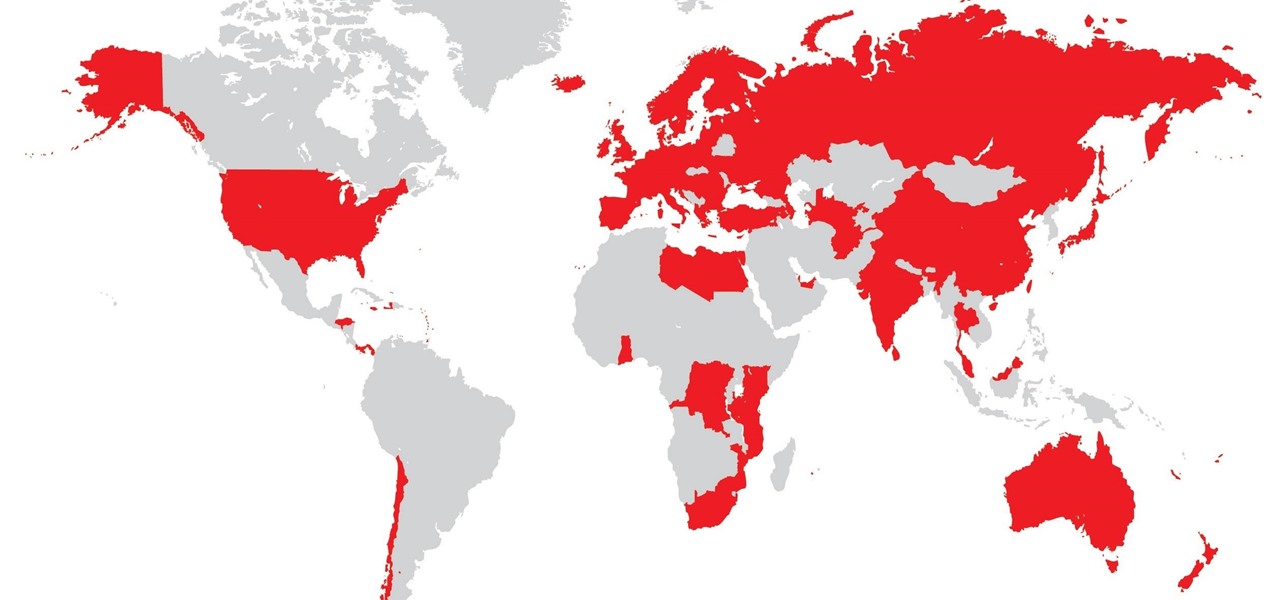
Vodafone India has merged with telecom company Idea Cellular to become India's largest mobile player this week.

Sky Zhou, also know as Matrix Inception on YouTube, is no stranger here on NextReality. We loved his Pokémon concept game for HoloLens, as well as his D3D Keyboard that lets HoloLens users leave notes around the house. He just can't seem to stop creating cool mixed reality apps, and he's already got another one in the works.

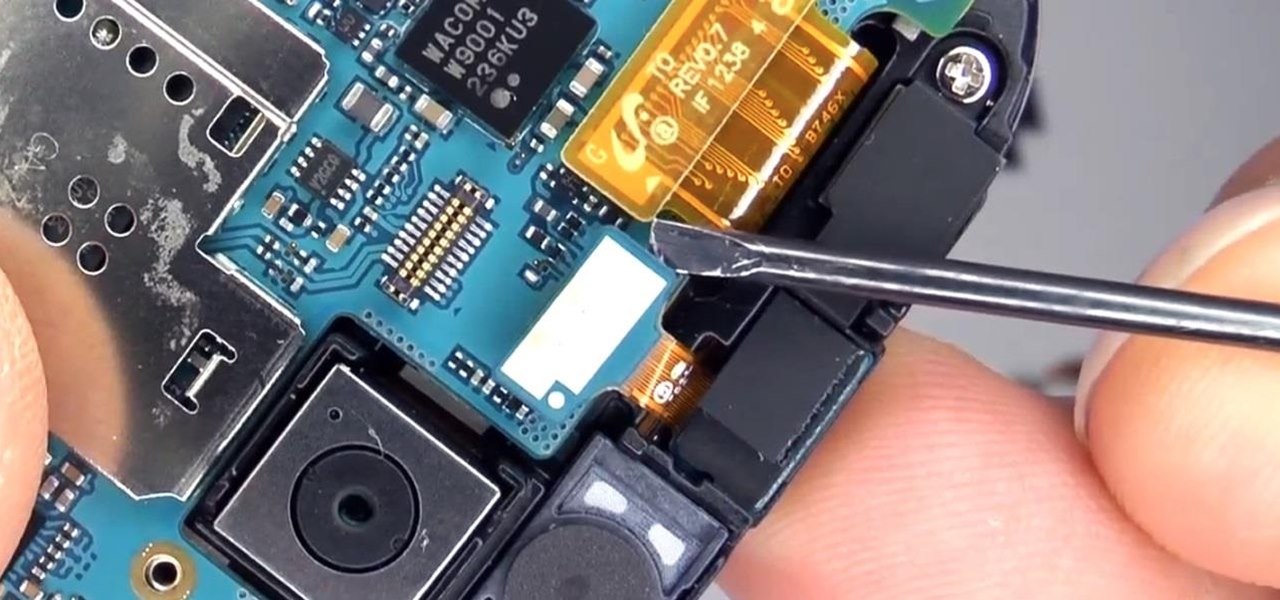
In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Five Phases of Hacking:- The five phases of Hacking are as follow:

The majority of Android web browsers carry a "desktop mode" feature that makes mobile websites look like normal computer versions. Mobile versions are designed to work faster and more efficiently on smartphones, but sometimes the desktop version looks better on large displays or has additional features not included in the mobile one.

I wonder if Best Buy has any Note 3's for sale?? When trying to figure out when something is in stock, we usually either check online or call the store to talk to someone. If certain products are out of stock the process might be tedious, with having to find phone numbers and calling several stores.

The new Samsung Galaxy S4 may be the only phone to include temperature and humidity sensors, but your Galaxy Note 2 has a few weather-detecting features of its own.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Here's a technique I used to whip up a batch of super cheap and easy to make smoke flares! WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

Even if you're not a hipster with your own self-sufficient garden, making your own edibles at home can be pretty cool. And while it's obviously easier to pick up a bottle of 7-Up at the store, there's something undoubtedly fun about making your own. For those addicted to their fizzy drinks, DIY soda is a great way to save some cash and make their drinks healthier with natural flavors and sweeteners, instead of something like corn syrup or aspartame.

Fromage blanc cheese is something every cook should experience in the kitchen. To consider yourself a real chef, you need to grab the cheesecloth and dip your hands in the cow's milk, because making cheese is a culinary experience like no other.

Facebook is an awesome free online resource that is connected to billions of people around the world. These days, you won't meet many people who do not have a Facebook account. As a real estate agent, you can take advantage of social networking to promote your business and share your listings. By posting on Facebook and creating a page for your business, you gain free advertising to thousands of local buyers. Check out this tutorial and learn how to start uploading videos to Facebook to promo...

Karen Solomon shows how to make bacon. You need 2 1/2 to 3 pounds of pork belly with no skin or bone. Rinse the belly with water and pat really dry. Mix ingredients for cure which includes 1/2 cup sugar, 1 tablespoon blackstrap molasses, 1 teaspoon freshly ground pepper, 2 tablespoons kosher salt and 1 teaspoon curing salt. Curing salt may be obtained at local butcher shop or online at Sausage Maker. Curing salt helps preserve the color of the bacon and ensures no spoilage. Mix ingredients un...

HippyUrban teaches viewers how to make inexpensive tortilla chips from scratch! First you will need to buy some MasaMix at your local Spanish market! It really is just corn flour. First, you need two cups of corn flour, 1 quarter teaspoon of salt and 1 quarter cup of water. Mix this up and add a tablespoon of water at a time to get it just right. Divide this in three and roll the dough on parchment paper. You want it to be thin and as thin as pie crust. With thicker chips, they can hold the s...

Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

If you're one of the many professionals transitioning to working from home amidst the current pandemic, there's a good chance you're now realizing how far behind your at-home setup is compared to what you had at the office.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

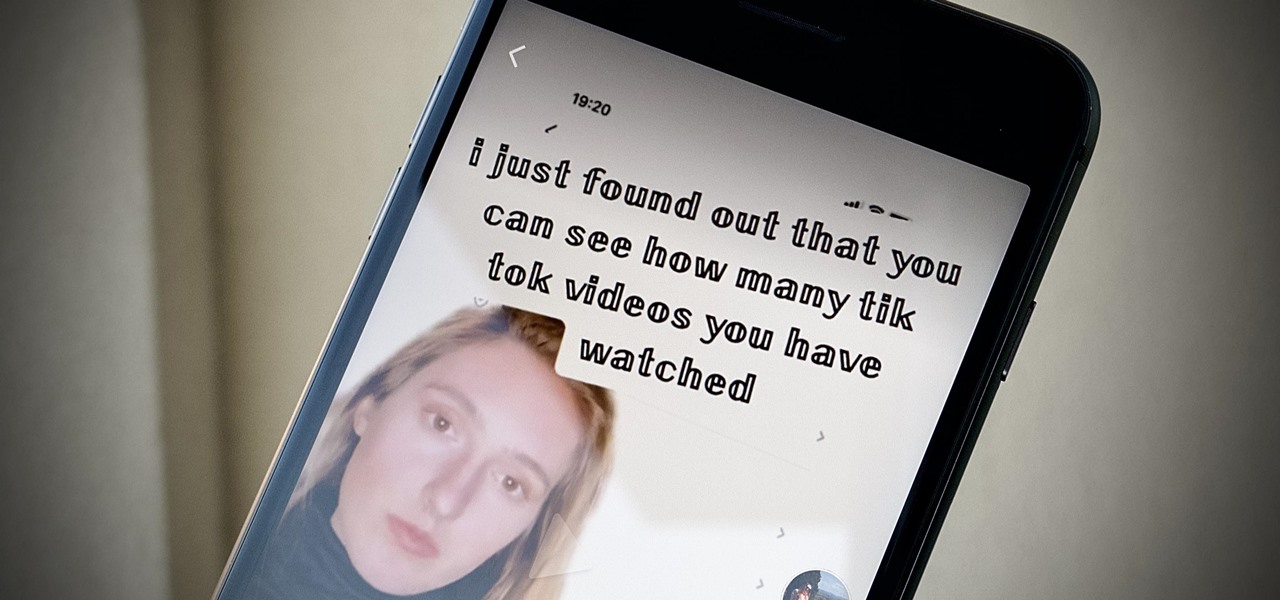
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

While holographic Whitney Houston is hitting the road, a new mobile app is bringing volumetric captures of up and coming performers directly to the iPhones and iPads of fans.