Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

Learn in this video how to use XMLSpy to create and edit XQuery documents, debug them and profile execution speed and bottlenecks, and execute them against local XML data or XML stored on a database server. XML editing can't get easier then this.

The no scalpel vasectomy has been reported to reduce the risk of pain, bleeding and infection. It can be performed under local anesthesia. Dr. Bird demonstrates his standard technique for a how to perform no scalpel vascetomy: lidocaine infiltration, skin penetration, vas isolation, electrocautery dissection, partial fixation, luminal cuaterization, clip application, and closure.

Create your own virtual hard disk and local folders to store information in.

Bourbon is America's contribution to the whiskey family, and this isn't so much a drink as it is a tradition. Take bourbon, and ideally, dilute it with water from whatever branch of the local tributary was used to make the bourbon. If you don't have access to that, then use whatever filtered water you can get from the store, and be sure to use it for the ice cubes too.
Are you getting that nasty "Application access set to not allowed" error on your Nokia 5300 cell phone? Unfortunately, it's a problem for most Nokia 5300 owners, ones who wish to use 3rd party applications on certain carriers, like T-Mobile, who restricts the uses for branding.

Fish & chips is the most popular fish meal in the country, & you can make it yourself instead of paying a fortune at your local fish eatery. The special ingredient for these fish and chips… beer.

Imagine a game almost anyone can play that combines the best of skee-ball, bowling, and shuffleboard. Welcome to the ancient sport of bocce.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Make sure the bike is properly fit to the child. She should just be able to stand over the top bar of the frame without touching.

Elvira, Mistress of the Dark, was created in 1981 by Cassandra Peterson. She was the hostess of a local Hollywood horror movie show that became nationally syndicated. Elvira was the first horror host to be nationally syndicated, first person to be broadcast in 3-D on TV, and first female celebrity to do a national beer campaign and market her own beer.

Would you know what to do if someone ingested poison? Equally important, would you know what not to do?

You already know the mechanics of DJing, but you want to be an international celebrity -- or at least drink for free while showing off your music collection. Here's how to spin your hobby into a career. Watch this video to learn how to become a professional club DJ.

Learn how to choose an indoor plant. You don’t need a green thumb to have houseplants that flourish; you just need to know which ones will thrive in your home.

Download the P2 Step-by-Step Reference Guide. With Avid, editing footage captured with the Panasonic HVX200 camera is fast and easy. Avids system uses the same native file format as Panasonic P2 memory cards, so theres no need for any transcode, capture or file conversion process at all. You can edit directly and immediately from the P2 cards if you like or have Avid Media Composer create a rapid backup of your files. Nothing could be simpler or more immediate.

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

Apple finally unveiled the iPhone 14, 14 Plus, 14 Pro, and 14 Pro Max, and there are a lot of improvements that'll make you want to trade in your current iPhone stat. But I wouldn't be so quick to upgrade because there's one "feature" that will make many of you rethink getting a new iPhone 14 series model.

Navigating a pandemic is new for everybody, which makes staying on top of your finances more important than ever. Fortunately, financial freedom is possible when you focus on budgeting and investing wisely.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

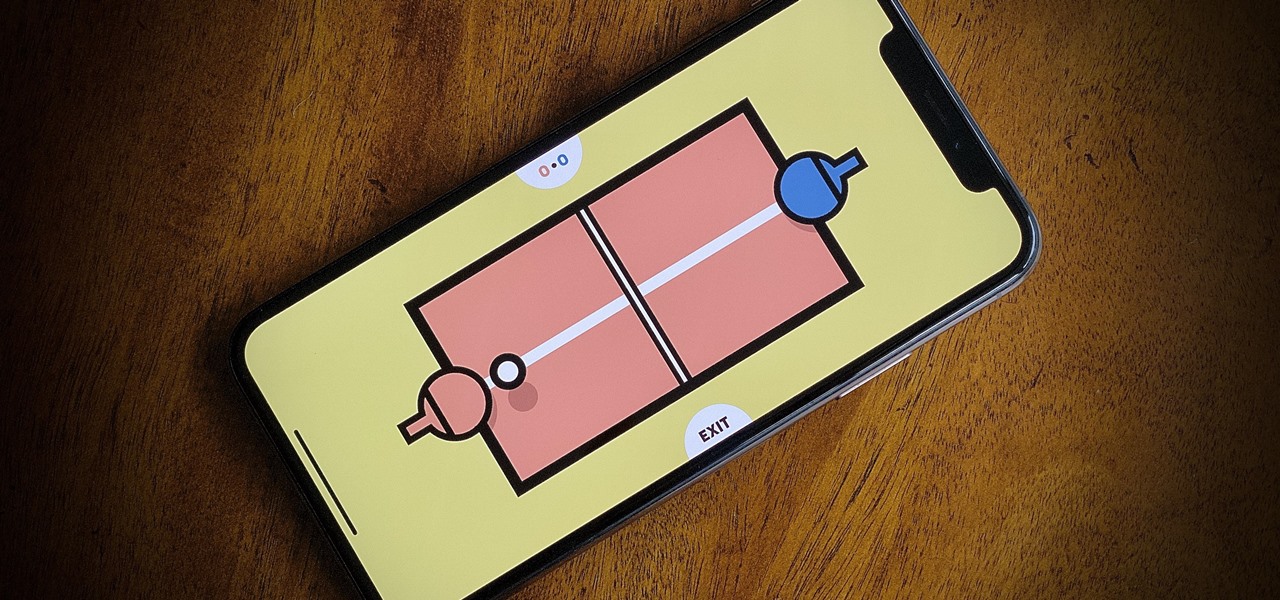
If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.

Whether you were exposed to the COVID-19 virus or just taking precautionary measures, self-quarantining is a tremendous disruption for anyone. Still, we all have to eat, pandemic or not. But unless you like eating canned food for two weeks, you're going to want to explore other options. That's why food delivery apps are going to be so necessary during such a hectic and uncertain time.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

I've just recently hopped on the AirPods bandwagon, and I can't see myself ever going back to the wired EarPods that Apple includes with every iPhone. The only issue is that I paid full price, but you don't have to with 2019's Black Friday deals, some of which are happening right now.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

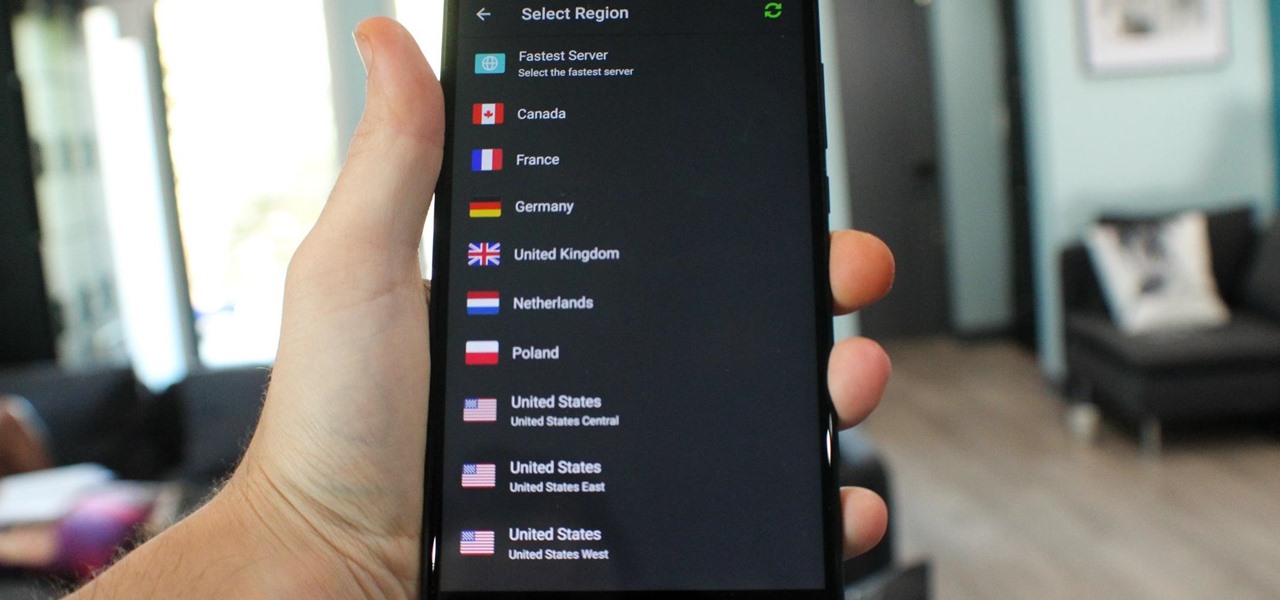
What you see when you open the Play Store is completely dependent on your country settings. Search results and top charts are specific to each region and there are lots of popular apps and games that simply won't show up unless your Play Store country matches up.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

With Nokia's relaunch, the iconic company attempted to reimagine the budget phone market. The series of phones they introduced last year challenged the idea that good phones can't be cheap. This year, Nokia introduced the Nokia 7 Plus, a phone which offers perhaps the best balance of specs, software, and price.

Super Bowl LII will bring millions of football and non-football fans together to watch the big game on the big screen. But without a cable subscription, this process can be a little daunting. Luckily, the Google Play Store and the iOS App Store offer a few ways to accomplish this — no cable contract required.

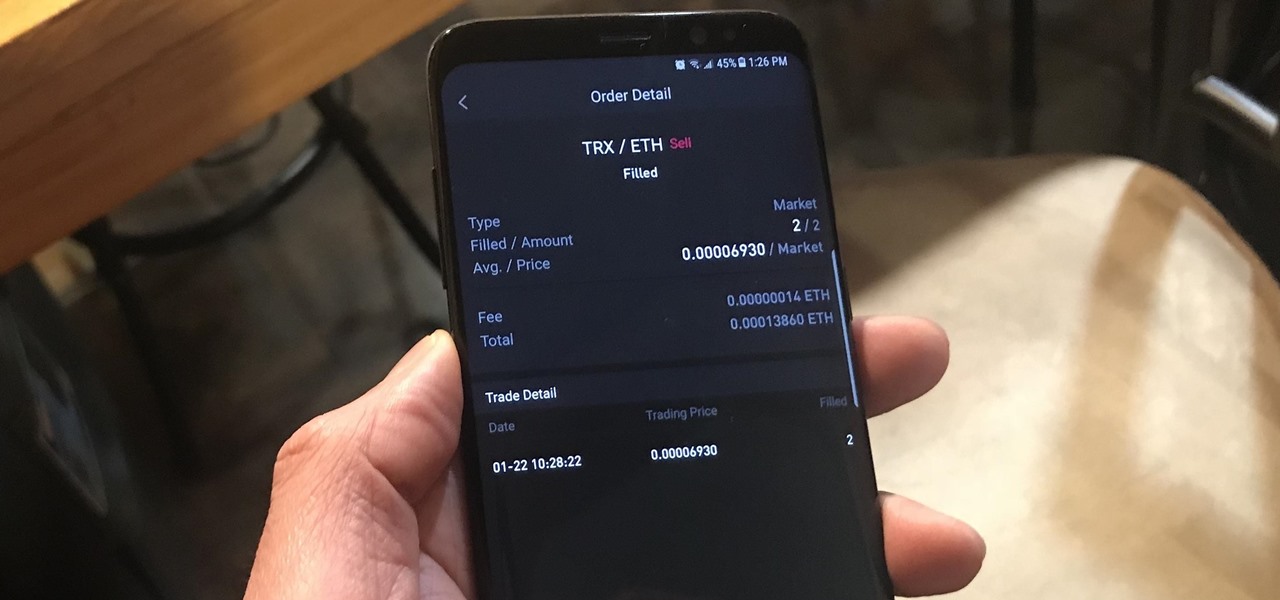
Selling alt-coins like Stellar (XLM) or Ripple (XRP) in exchange for more widespread coins like Ethereum (ETH) or Bitcoin (BTC) can be a daunting task if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.