This instructional gardening video demonstrates how to build three tiered walls into a slope to create a flowing curved garden. If you are gardening on a slope, you may want to build small walls to create level gardening areas. Use local stones to provide a rustic, natural look to your terraced garden.

This instructional video provides examples various supplies for war game terrain and diorama making. Most of these supplies for miniatures can be found at a local dollar store. Look for cardboard tubes, plastic sheeting, high density foam, metal foils and wires, plaster, sand twigs and other found materials.

Do you have wallpaper in you'd like to remove but aren't sure how to go about stripping it? In this tutorial, you'll learn in a few easy steps how to remove it using a wallpaper steamer (available at your local DIY or tool library), a six-inch drywall knife, a scoring tool and a sponge. Watch this video to learn how you, too, can easily strip wallpaper.

This video tutorial may be incredibly boring for individuals who dislike the daily challenge of the local newspaper's crossword puzzle, but for those who rack their brains wishing they were cryptically minded need not worry, because this instructional video will help you get started in decoding the world of cryptic crossword puzzles.

The hardest part about going to Rio, Brazil is leaving it at the end of your trip. In this South American travel video, Toby Amies soaks it up in a Rio beach, before visiting a favela, tries out at Samba School and samples one of the local Brazilian delicacies - a caipirinha!

A journey to Africa requires a certain amount of open-mindedness and flexibility to interact with people of a culture vastly different from anything in the West. This video travel-tutorial offers advice for how to relate and get along with the local hosts during a trip to Africa, what to expect, and how to behave when encountering people from a different area of the world.

Checkout this how-to video to make a simple focusing mask that works great. When not helping you to focus your camera, it also extends your dew shield to keep dew off of your lens.

Check out this instructional video on how to properly clip your pet guinea pig's nails. If nail trimming is too difficult for you, local pet groomers and veterinarians can clip your guinea pig's nails for you.

Want to stick a load of blood and guts in your film? Don't have a lot of money? No problem! Just go to your local butcher shop.

Shopping is very important even in Japan. Watch this video and learn basic Japanese phrases you can use while in Japan or in your local Japanese community.

Improvised igloo building on the Vermillion Lakes outside Banff, Alberta, Canada, using a recycling bin, a toboggan and tools from the local hardware store.

In this episode, Brandon Jackson joins D.Lee Beard to present an in-depth review of the Slingbox A/V, explore where to find free downloadable audiobooks online, and to answer viewer questions on using an iMac as a display and how to share files over a local network between a Mac and a Windows PC . Be sure to check out our next video to learn how you can win the Techies' Slingbox and begin watching your home TV from all over the world via the internet.

This is how to fill a paintball tank using a scuba tank. You will need- $150 Scuba Tank

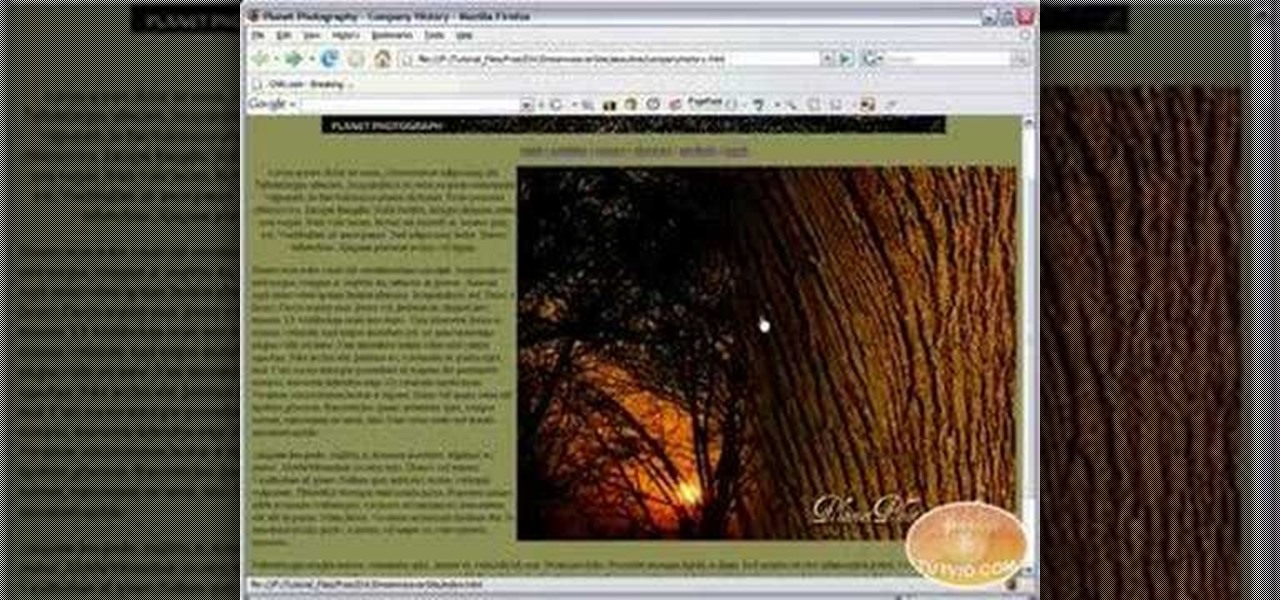
This is a video tutorial on creating Hyperlinks to your local site or other websites with Dreamweaver as well how to create email links.

From the dark depths of your local swamp, and by swamp I mean Indy Mogul, comes the SWAMP MONSTER!!!! For under $35, you can make your lead actor so ugly that you'll be able to steal his girlfriend.

Learn and understand hand match ups and the percentages of winning those hands in a Texas Hold'em game. Become the local guru and know pot odds and percentages of winning.

Want to show off some talent at your local bar? Learn to break a bottle with your bare hands and impress the crowd. Take your bare hand and break a bottle and make everyone believer.

Don't buy those expensive allready made tombstones at your local party store. We will help you with tips on where to buy your supplies and make your own tombstones for your holiday decorating. Its easy and a lot of fun.

Stuttering is a communication disorder affecting over 3 million Americans. Stuttering can make school and other social interactions difficult. Although there are no instant cures, these tips will help your progression toward speech fluency.

A side effect of the COVID-19 pandemic is that small businesses are suffering from forced closures and social distancing, but game developer Niantic has a solution.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Hi , Today i will show you how to do HID Keyboard Attacks With Android BUT without using Kali NetHunter BUT You will need to install custom kernel to your Android device, that will add keyboard+mouse functions to it's USB port,So Lets Get Started

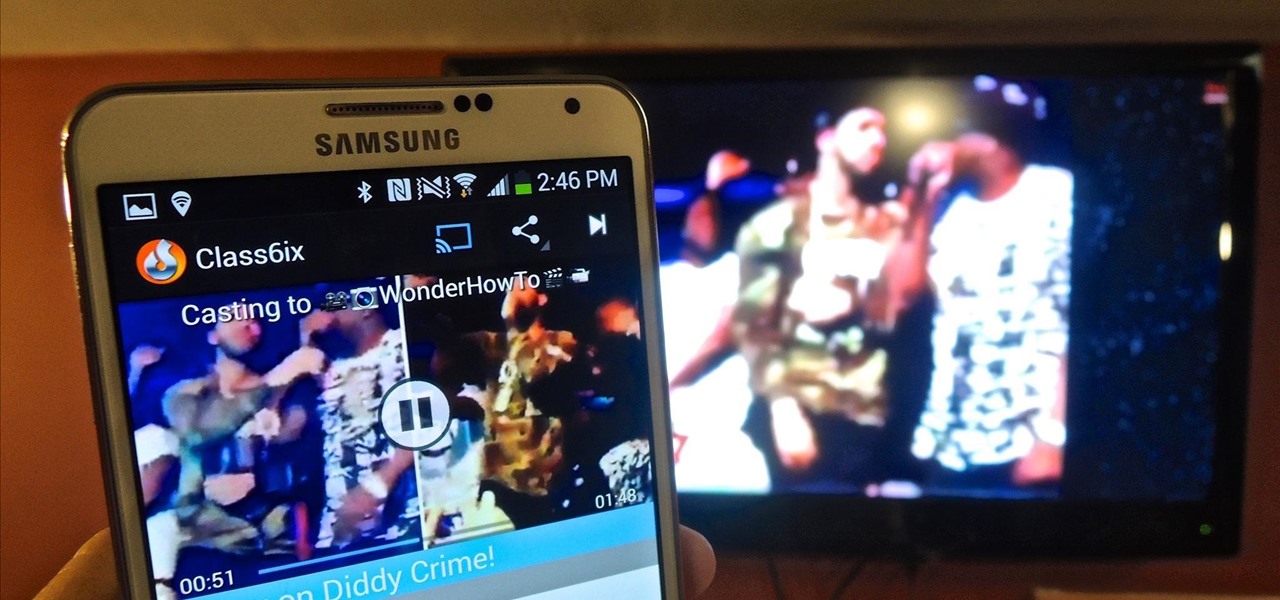
With Chromecast-capable applications slowly seeping into the market, it's difficult to find useful ones that we might use on a daily basis.

For many busy people, time is of the essence, and for others, it's simply just being impatient. But no matter what your vice, having your computer start up as quickly as possible is usually a plus for anyone.

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

It takes more than a kicky costume to become a professional wrestler. Start young to build up your basic wrestling skills and athleticism. To turn pro you’re going to need some acting flare, love for performing and a little luck.

Did you know that you can grow beans in your garden just by buying ordinary packs of soup beans at your local grocery? Once you start growing beans, you can keep growing them for a lifetime--just keep the seeds around. Soon beans will be sprouting in your garden every year!

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

Just because you are using Linux, doesn't mean you have to be cut off from file sharing with those using a regular Windows PC. In this tutorial, learn how to share files between Ubuntu and Windows using a Samba local network. Samba is simple to use and can be obtained through your Synaptic package manager.

This is a simple demonstration of how to design and paint your own skateboard, a great way of combining your art and your riding and bring more originality to your local skate park.

The Mighty Car Mod team will show you how you can make a homemade boost pressure tester for a turbo car, all with parts you can get from your local hardware store, just for about ten bucks. You can use this boost pressure tester to find pesky leaks in your custom intercooler piping on your vehicle.

Exterior lighting can add to the beauty of your home. Watch this how to video and wire exterior lighting yourself following these guidelines and safety tips. Before beginning any outdoor wiring project make sure to check with local utility companies and follow outdoor wiring codes for your area.

Tribune food and wine critic Bill Daley visits a local restaurant to get the scoop on Asian noodles. This tutorial video will show you a quick recipe for an Asian inspired bolognese.

Looking to create a great centerpiece that will dress up your table for all teh winter holidays? We have some tips for a local 'award winning' expert.

This is a simple recipe that just uses regular AP flour. You can, of course, use a mixture of semolina flour like many pasta recipes suggest. But, this recipe is very user friendly, and if you’ve never made your own pasta before, this would be a good place to start. By the way, those pasta machines are surprisingly affordable at your local mega-store

Choosing a paint color is a creative and fun way to begin any home decorating project. The right color can easily brighten up a dark room, or create the illusion of more space in smaller areas. For this project, you will need; foam brush,a handful of 6-inch by 4-inch pieces of white cardboard, various paint swatches and a small jar or two of paint samples, which can be picked up at your local home improvement store.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

Get ready to step up your game, explorers! Google Maps is releasing an update for its gamified program to encourage reviewing of businesses and other locations within the Google Maps app.