If you have a Mac, you've probably been anticipating the release of OS X Mountain Lion. If you have multiple Macs, you've probably been dreading the long process of downloading and installing it on all of them. Here's how to create a bootable backup disk and save yourself some time. Before You Start

Most of the time, asking to borrow someone's car will elicit a really long string of excuses. But unlike letting your buddy use your car, which usually gets you nothing more than an empty tank, GM has found a way to make car sharing beneficial for everyone involved. If you're one of the 6 million people who have a GM vehicle that's connected to OnStar, you're in luck: according to an OnStar employee, you can make up to $1,000 a month just by letting other people rent out your car when you're ...

Custom ring and text tones are great for knowing who's attempting to contact you without having to actually look at your iPhone. However, this feature is useless when your device is in silent/vibrate-only mode.

Paper towels are really cool. I like having them around for quickly cleaning up messes and what not. However, I do not have a stand or something similar for my paper towels, so it can sometimes get a bit taxing to pick up the roll and unravel it every time I need a towel.

Poor alignment of cabinet doors will cause a kitchen to look run-down and may be embarrassing to the homeowner. Luckily, with a single screw driver and a little ambition, the door alignment can look brand new.

In the following video, I demonstrate how to create a device capable of charging the body of anyone who wears it with static electricity, allowing a powerful shock to be discharged into anything that is touched. This grants the wearer the ability to do some pretty amazing things, some of which are shown in the first segment of the video.

Everyone loves using their cell phones for everything except actually making phone calls. Whether it's watching streaming video, listening to music or playing video games, it would seem that calling people is almost an afterthought to cell manufacturers in this day and age.

Watching videos on an Amiga computer without a web browser is really easy. Actually, you do need an internet browser to grab the links and the FFmpeg package. Once you have the links and have FFmpeg installed, then you can watch any videos streamed by YouTube without any browser.

In this Autos, Motorcycles & Planes video tutorial you will learn how to check and inspect the radiator hose damage and installation condition on your motorcycle. Make sure that the bike is cold and then locate the coolant system. Check the hoses by pressing them with your fingers. They should not be too hard, or soft or brittle. Check the clamps are in place and properly torqued. Visually inspect all the pipes and see that there are no dents. Repeat the same steps on the other side of the bi...

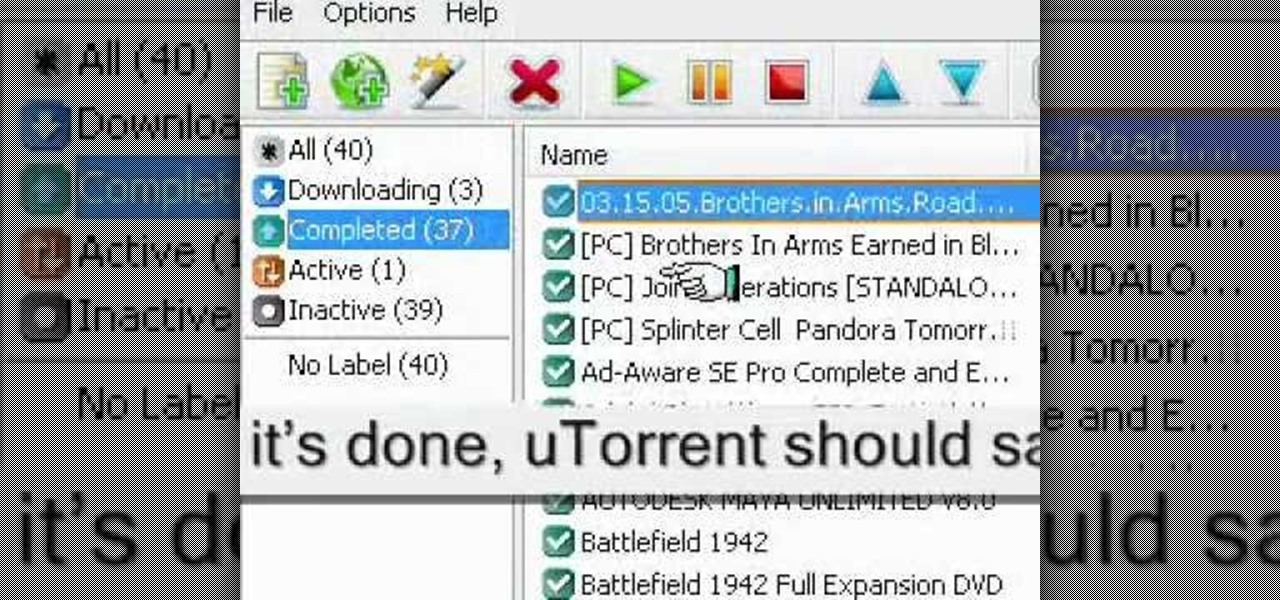
In this video tutorial, viewers learn how to seed a torrent in the u-Torrent client. Begin by downloading and saving your torrent file. Make sure that you uncheck Start Torrent when it opens. In u-Torrent, right-click on the file, go to Advanced and select Set Download Location. Now locate the torrent file and click OK. Then right-click the torrent again and select Force Re-Check. When it's done, u-Torrent should say that the torrent is 100% finished. Right-click the torrent and click on Star...

In this tutorial, we learn how to force an iPhone or iPod touch to turn off. First, hold the power button ( at the top of the device) and home button (one the bottom middle) at the same time and wait until the screen turns completely off. To turn back on, press the power button that is located at the top of the device. You will see an Apple logo pop up and it will stay on the screen for several seconds. After it's loaded, it will re-boot as normal and your regular home page will show up as it...

In this video tutorial, viewers learn how to recover lost data using R-Studio. Begin by running R-Studio. Locate the drive that you want to recover. Right click it and select scan. The scan can take up to 45 minutes depending on the size of the drive. Once its finished, there will be a list of hard drives in which data is stored. Green, black, and orange will recover with no problems. Red is not recoverable. Double click on the wanted drive and wait for it to load. You can now see all the dat...

All of us guitar players love to play our favorite songs on our own guitars. Sometimes it is hard to learn how to play specific songs. It can also be difficult to locate a tutorial on how to play these songs! Old Crow Medicine Show's "Wagon Wheel" is a great song that is fun to play, especially for fans of Bob Dylan. By viewing this 5 minute video and with practice, you'll learn how to play "Wagon Wheel" like a professional! If it is hard for you to bar your frets, be sure to use a capo and l...

To become a Victoria's Secret model, use the Internet to locate agency Web sites and register photos on-line to be viewed by modeling agencies. Build a portfolio and gather head shots for becoming a Victoria's Secret model with tips from a modeling instructor in this free how to video on modeling.

One thing about the small round little Pixel Buds — they might get lost easily if you have a terrible habit of misplacing stuff. Or worse, imagine someone taking a liking to them a little too much and stealing them when you aren't looking. Google thought ahead about these issues, so just like your smartphone, you can track your wireless earbuds from anywhere with ease.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Smartphones have put an end to camcorders. If you want to capture memorable moments in high quality, look no further than that technological marvel in your pocket. Recent Galaxy phones are shining examples of how far we've come — but the more capable a camera gets, the more complicated things can be.

The greatest pain in owning a high-powered gaming PC is the simple fact that you can't play it all the time. Sometimes you have work or school, and other times, you may just want to go mobile. When something like this impedes your ability to play PC games, you may end up settling for mobile games. What if, instead of doing that, you were able to play your PC games from your iPhone?

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

In this tutorial, we learn how to keep yarn from tangling when using many colors. A great way to do this is to start the crochet then place your color aside. So even though the colors are crossing each other they are not tangling up. Make sure to keep rotating your project and pay attention to where your yarn strings are located at. This will keep all your things in order so you don't have to deal with large knots and messed up projects. Just make sure to set up properly and you will have a g...

Access your computer's BIOS settings

This video describes how to install the day viewer plug-in on a PSP. This plug-in is used to add features of Battery Percent, Month Name, Day of the Month, Day Name next to the battery. Firstly, download the Day viewer v5 zip file from the website link, now connect the "PSP" with the computer and the root of the memory stick will show up. Open the "Seplugins" folder located on the "Memory stick" and then extract the zip file of "Day viewer v5" and extract the "Dayviewer.prx" and "Dayviewer.tx...

The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.

You might want to take apart your Xbox for a variety of reasons. This video will walk you through the process of opening up your controller from unscrewing to the trick of lifting of the cover. You can see the different part where you might need to replace or upgrade things. Step 1: Start out by making sure that the XBox 360 controller is not turned on. The green lights around the XBox button should not be lit. Take off the battery pack located on the back of the XBox 360 controller. Step 2: ...

Folders are a neat way to keep your home screen apps organized in your own specific categories, but what about your personal contacts? You can actually populate a folder with all of your favorite contacts for one-tap instant access.

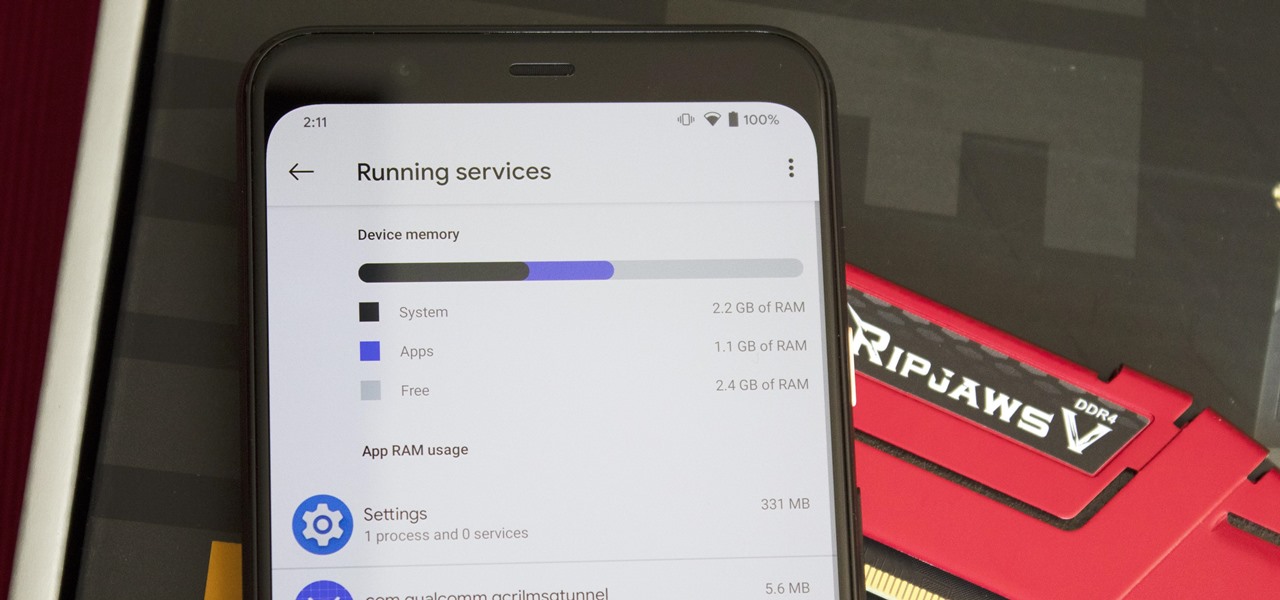
Not every app is designed well. With nearly 3 million apps on the Play Store and countless more that you can sideload from other sources, there are bound to be a few stinkers. And many of them do a terrible job using RAM.

As phones' screens get closer to seven inches, now is the perfect time to take advantage of Android's split-screen mode. This feature has available since Android 7.0 Nougat and allows you to divide the screen into two halves, with a different app on each side.

For Android smartphones, the latest craze is high refresh rate displays, and many popular flagships have them. But until now, there has been no way to confirm it is, in fact, running at higher hertz besides a menu option. Android 11 changes this.

OnePlus releases some unique and exciting features before they start catching on with everyone else. Their OxygenOS is often considered the cleanest and most useful variant of Android. However, there are still a few key features OnePlus has yet to bring to their devices. This includes a proper lift to wake option.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

Google's push for your safety gained some much-needed attention when it released the Pixel 4 smartphone. It has an app called "Personal Safety," which uses the array of built-in sensors on your phone to detect if you've been in a car crash. The futuristic safety feature was exclusive to the Pixel 4 initially but is now available to all Pixel owners as well.

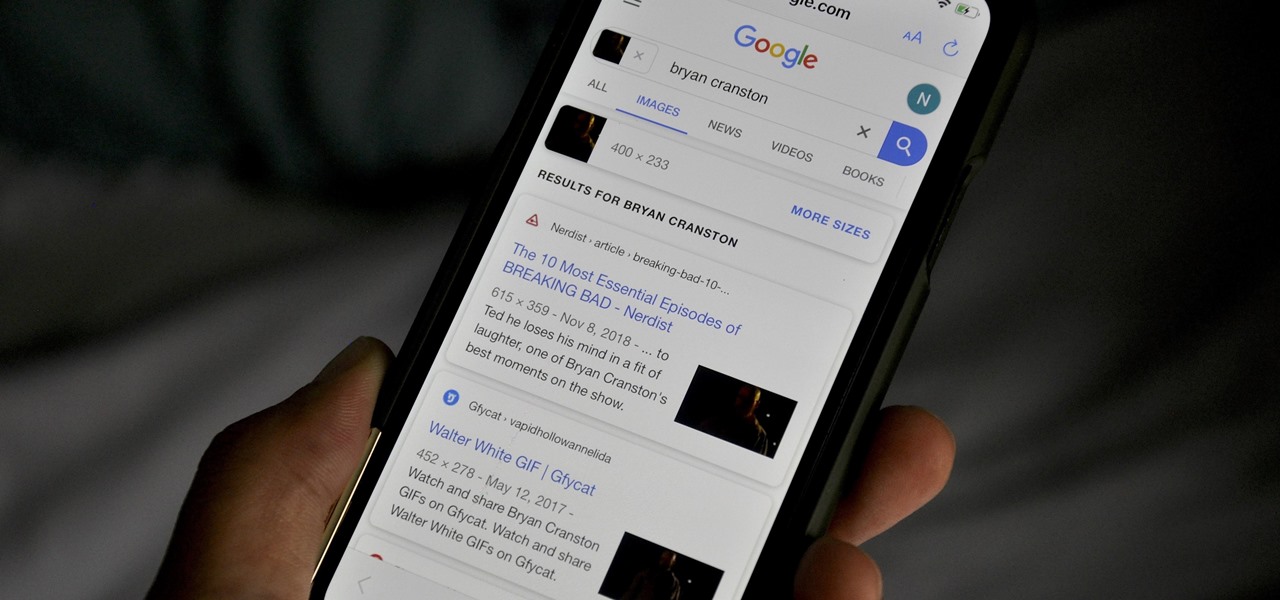
Google Images, TinEye, and other reverse image search engines can help you find where images appear on the internet. You can discover what TV show or movie an image comes from, who took a photo, and if the profile picture of someone you're talking to online is really them, among many other uses. And there's a shortcut for iOS that makes running a reverse image search easy.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.