This workout video gives an exercise for you butt or gluteus muscles to tone and strengthen them. Most weight-bearing leg exercises will work out your gluteus muscles to a degree. The same is true with various gym classes, running, rollerblading and ice skating. You can decide to omit targeted exercises for your gluteus muscles from your regular workouts entirely, but it’s good to stretch (particularly if you have a day job which requires sitting on a chair), to strengthen and to tone this mu...

This video is on how to install a Revo forward only (or FOC) for your radio controlled vehicle. For this, you will need to remove your 2.5 or 3.3 Revo transmission from the kit and then I will walk you through the rest. You will basically be removing the front gears and then replacing another gear towards the back. Also, I am using the center differential kit which is easier as you do not have to worry about the gearing on the center differential shaft. If you do not purchase the center diffe...

Watch this instructional video to learn how to balance on a rolla bolla. A rolla bolla has two parts, the roller and the board. To begin with place the roller on the ground, it helps if you use some kind of carpeted surface or something like that when you're beginning, that will help slow down the rolling and make it easier to balance. Next take the board and place it on top of the roller, with the roller about two-thirds of the way up the board. Place your left foot on the lower end of the r...

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

Lose weight, watch what you eat, connect with others; learn to use the Daily Website in this free video and find out how to be healthy and lose weight while sharing your ideas on diet and nutrition.

Every day we pass bridges, whether it's a foot bridge, a highway overpass, a span over water, or a viaduct over a valley. We pass on these structures without even thinking of the engineering genius that went into their design and construction, let alone the science behind their strength.

To become a Victoria's Secret model, use the Internet to locate agency Web sites and register photos on-line to be viewed by modeling agencies. Build a portfolio and gather head shots for becoming a Victoria's Secret model with tips from a modeling instructor in this free how to video on modeling.

In this tutorial, we learn how to keep yarn from tangling when using many colors. A great way to do this is to start the crochet then place your color aside. So even though the colors are crossing each other they are not tangling up. Make sure to keep rotating your project and pay attention to where your yarn strings are located at. This will keep all your things in order so you don't have to deal with large knots and messed up projects. Just make sure to set up properly and you will have a g...

In this Autos, Motorcycles & Planes video tutorial you will learn how to drift in your car easily. In this video Bryan Norris tells you about basic drift techniques and counter steering. While at high speed when you turn a corner, the car will start to spin. What you do now is to counter steer. That is you turn the steering wheel in the opposite direction. As you come down the hill, step on the brakes. What this does is it transfers the weight of the vehicle from the rear of the car to the fr...

Access your computer's BIOS settings

Nursing a baby in the bloom ring ring sling is very simple and comfortable. While the baby is sitting in the sling their bottom will be at stomach level for you with the fabric stopping around the baby's knees. Support the babies weight with your hand and gently slide the top ring to lower the sling so your baby will be sitting at your hip. with the baby in place you can lower your shirt so the baby can latch on and nurse. The sling is high enough for you to be able to nurse hands free and no...

This video describes how to install the day viewer plug-in on a PSP. This plug-in is used to add features of Battery Percent, Month Name, Day of the Month, Day Name next to the battery. Firstly, download the Day viewer v5 zip file from the website link, now connect the "PSP" with the computer and the root of the memory stick will show up. Open the "Seplugins" folder located on the "Memory stick" and then extract the zip file of "Day viewer v5" and extract the "Dayviewer.prx" and "Dayviewer.tx...

The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.

Expert massage therapist Jinilee Reavis offers an introduction to hot stone massage therapy in this video series. She offers information about heating the stones, how the combination of heat and weight is therapeutic for relaxing muscles, and when to apply lotion to maximize the benefits of hot stone therapy.

You might want to take apart your Xbox for a variety of reasons. This video will walk you through the process of opening up your controller from unscrewing to the trick of lifting of the cover. You can see the different part where you might need to replace or upgrade things. Step 1: Start out by making sure that the XBox 360 controller is not turned on. The green lights around the XBox button should not be lit. Take off the battery pack located on the back of the XBox 360 controller. Step 2: ...

One thing about the small round little Pixel Buds — they might get lost easily if you have a terrible habit of misplacing stuff. Or worse, imagine someone taking a liking to them a little too much and stealing them when you aren't looking. Google thought ahead about these issues, so just like your smartphone, you can track your wireless earbuds from anywhere with ease.

Folders are a neat way to keep your home screen apps organized in your own specific categories, but what about your personal contacts? You can actually populate a folder with all of your favorite contacts for one-tap instant access.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

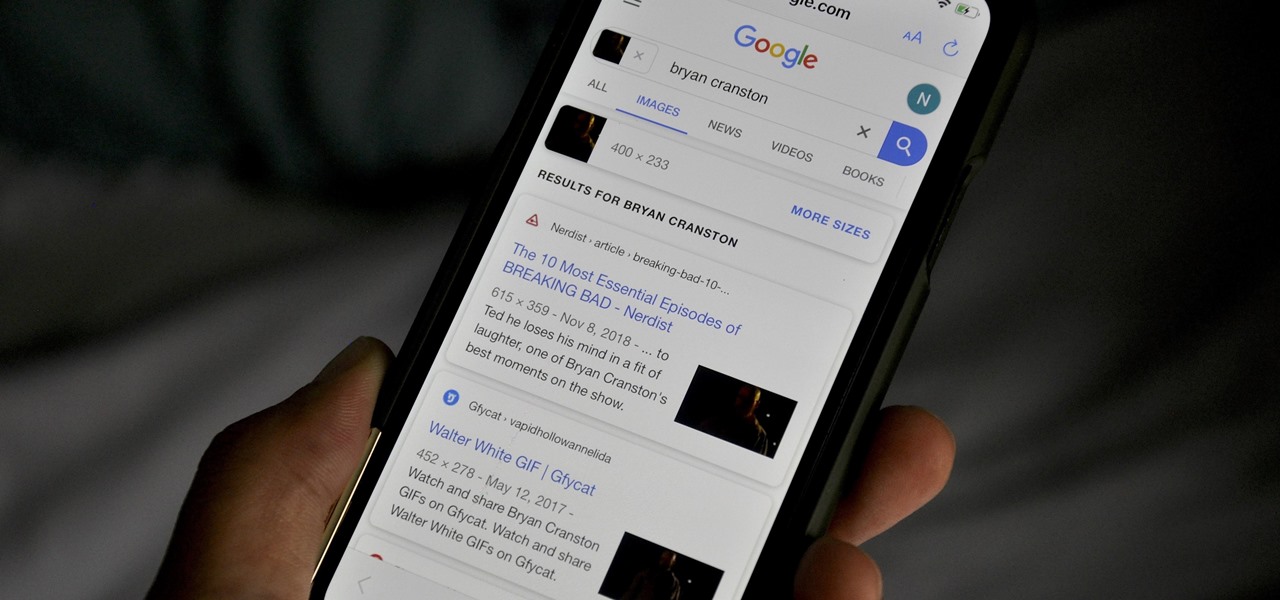
Google Images, TinEye, and other reverse image search engines can help you find where images appear on the internet. You can discover what TV show or movie an image comes from, who took a photo, and if the profile picture of someone you're talking to online is really them, among many other uses. And there's a shortcut for iOS that makes running a reverse image search easy.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

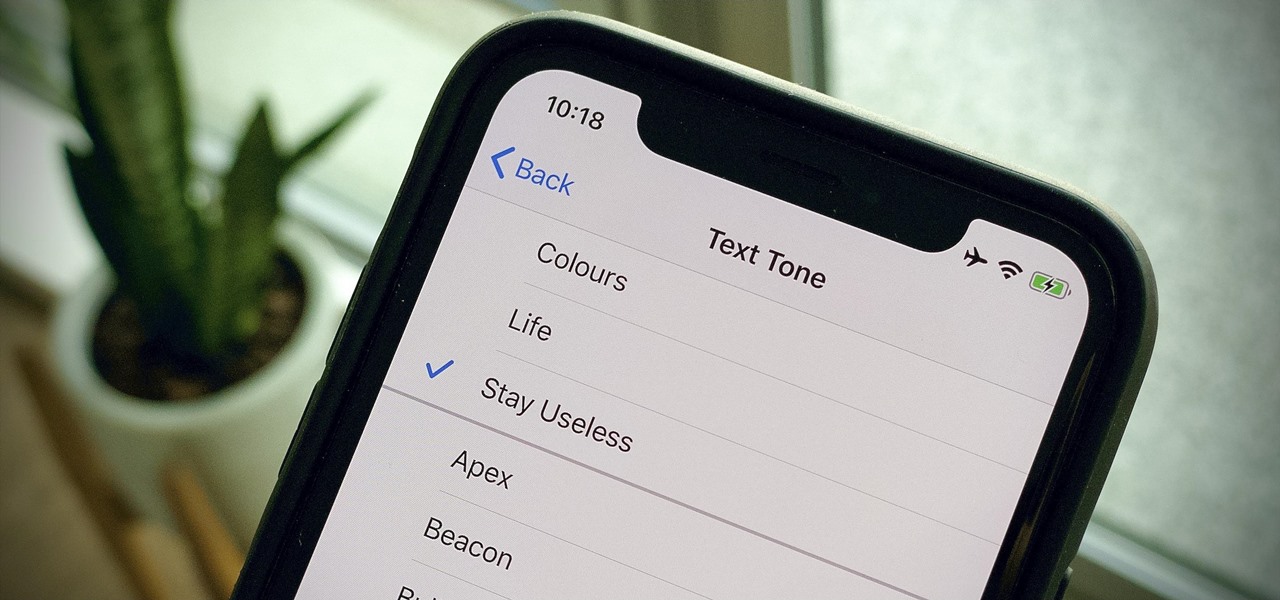
Apple hasn't refreshed its text tones on iPhones since iOS 7. That's six years of the same sounds. And while text tones like Bamboo and Hello have undoubtedly aged like fine wine, that's still too long to live with the same old sounds day after day. Let's take matters into our own hands — let's make our own text tones, right in Music on macOS 10.15 Catalina.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

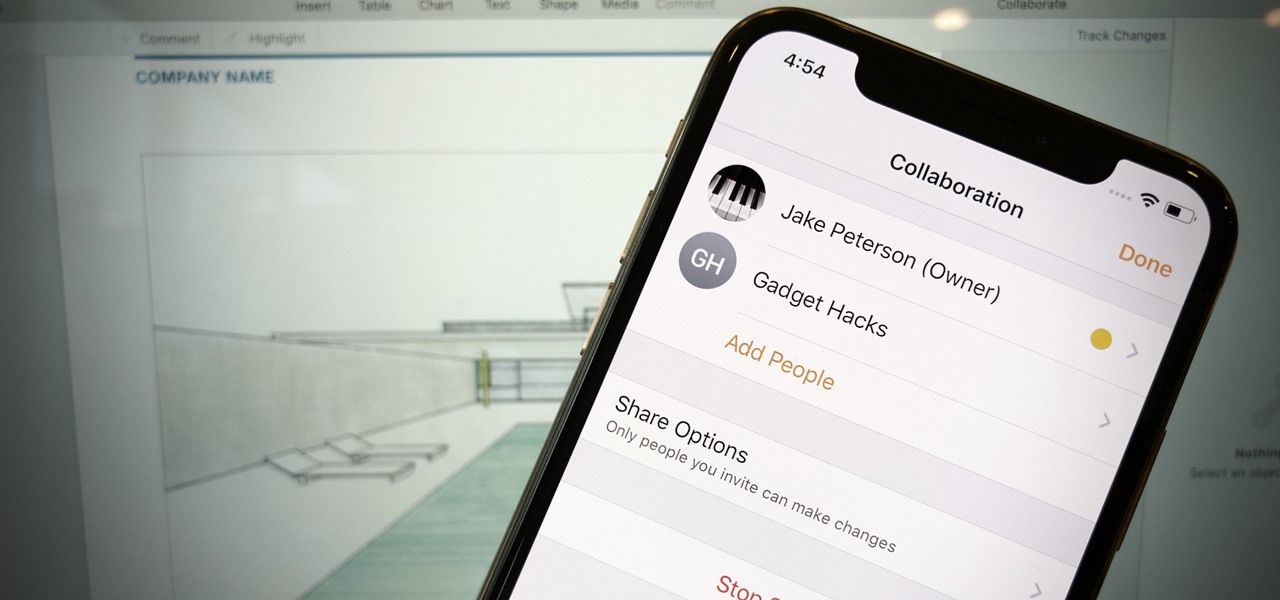
Google Docs is made for teamwork and collaboration, but Apple's iWork suite also comes with the same functionality. If you're working on a Pages document on your iPhone, and you want input from other members of your team, you can easily invite them to view, comment, edit, and more right alongside you.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

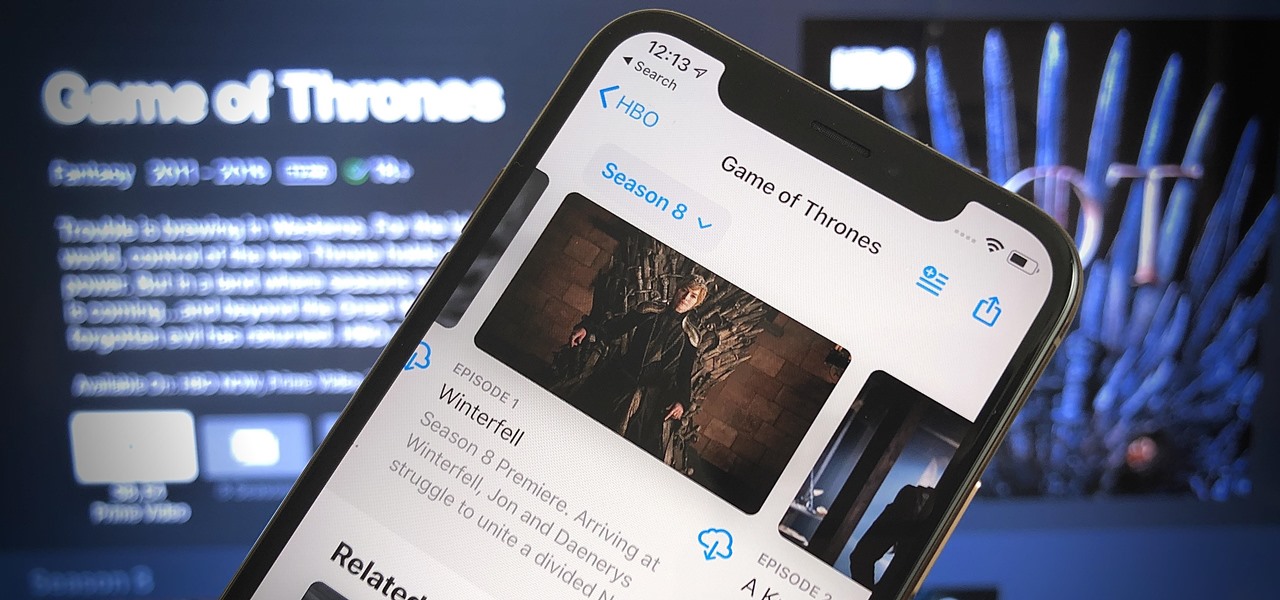
If you're a Game of Thrones fan and would like to watch the latest season offline on your iPhone, or if you need to catch up on previous seasons, there is no current support on HBO Go or HBO Now to download episodes for offline viewing. But that's only halfway true because there is a legal, official way to download HBO content on your iPhone, it's just not obvious at all.

Smartphones have put an end to camcorders. If you want to capture memorable moments in high quality, look no further than that technological marvel in your pocket. Recent Galaxy phones are shining examples of how far we've come — but the more capable a camera gets, the more complicated things can be.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

The OnePlus 6T is easily one of 2018's best value phones for many reasons, especially when it comes to rooting and modding. But like many new phones, it's plagued with the single bottom-firing speaker that left us wanting more in the sound department. The speaker is decent on its own, but it appears to have some hidden potential at the same time.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

On Tuesday, the smartglasses startup known as North finally took the wraps off its Focals product, but in a very unique way: The team simply opened a couple of stores and invited the public in.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

One of the primary marketing tactics used by Magic Leap in promoting the Magic Leap One was selling early adopters on the "magic" contained within the device. On Thursday, some of that magic was uncovered as the Magic Leap One was completely disassembled by repair engineers, revealing the delicate innards of the device and detailing how it delivers its augmented reality experiences.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

The share menu is a vital part of Android that lets you send data between between apps. Many of your favorite apps support the feature, including the new Direct Share sub-menu, which can lead to a messy share menu. However, there are a number of tools to clean up this clutter, three of which don't require root.