When your cat goes missing, chances are it's just chilling in a cozy spot under the couch, or maybe even hiding from you. So it's okay to not freak out just yet. Cats love to hide as if they're spiders, and even their hiding spots are similar. You can find them in corners, on the refrigerator, and according to my roommate, even the dryer hose is fair game.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

While most of your iPhone's features are intuitive or well-covered across the web, there are some features hidden deep within iOS that you probably never even knew about. (These could also apply to an iPad or iPod touch.)

Downloading YouTube videos for offline use to watch later has always been a problematic endeavor. Dedicated third-party apps don't last long in the App Store, web-based converters aren't very functional on mobile, and rogue apps outside the App Store are tricky to sideload and open up the possibility of vulnerabilities. But that doesn't mean you still don't have a few good options.

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

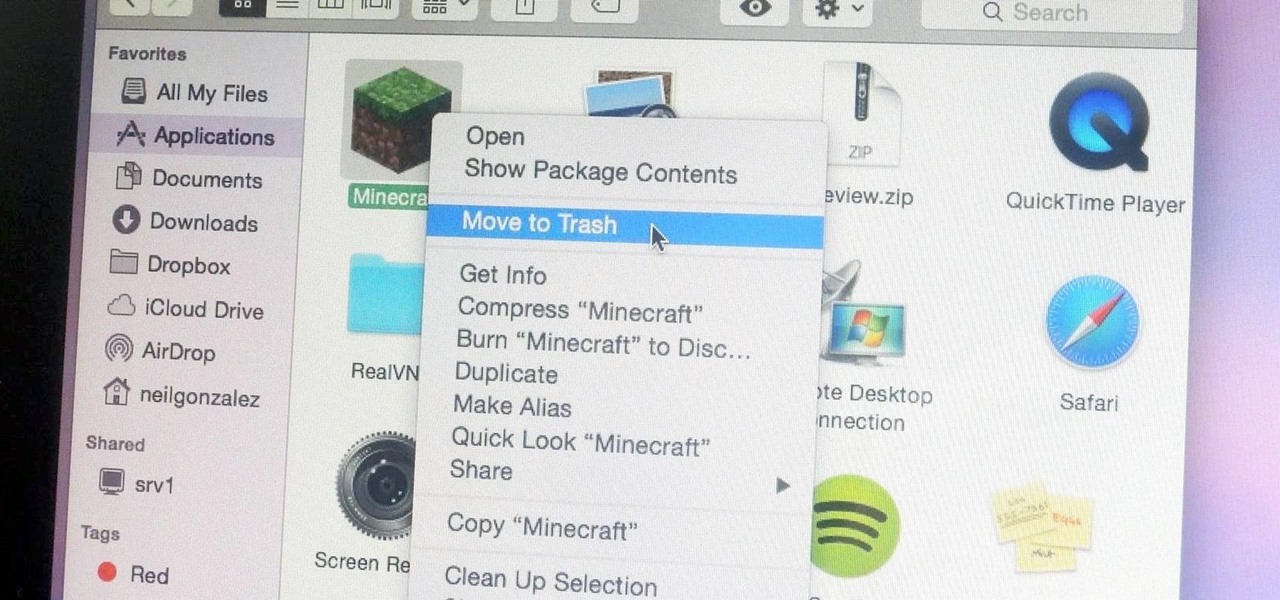
Uninstalling an app on your Mac isn't as straightforward as you would think. When you drag and drop an app into the Trash, then empty it, the main app itself may be gone, but many associated files and folders are left behind. So how do you get rid of them? There are a couple of ways.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

As someone with a pretty nice TV, I've never found the allure in purchasing a projector. While they're certainly smaller and sleeker than a television, and more portable, they can be pricey and produce a less than stellar image. And who really buys a projector anyways? They're for school, they're for work, they're for theaters, but they're not really for my apartment, right?

Part 1: What is Popcorn Time? Part 2: What is a torrent?

When a stuffy nose hits, it feels like breathing clearly and easily may never come again. Allergies, colds, and even changes in weather can leave our sinuses blocked, with medicine seeming like the only option. But don't break out the medication just yet — relieving the pressure of a stuffy nose, a stuffy head, and stuffy ears can be as easy as touching a pressure point.

With the brand new SMS-based ordering service called Magic, anyone with a mobile phone can order whatever they want—really, anything—by sending causal text messages. Who says magic isn't real?

When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

As I've explained before, black app backgrounds save you a bit of battery life on your Samsung Galaxy S5. This is because the AMOLED display on your S5 does not have to power pixels or a backlight for portions of the screen that are black.

Fifty-four percent of Americans 18 and older drink coffee every day, and why not? With 100 milligrams of caffeine per six ounces of drip coffee, it's just the morning beverage to wake you up and kickstart your day. You can feel the caffeine surge through your body like the Holy Ghost, making you aware, focused, and ready for action.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

It was the star of the show, but now that Android L has been released for preview to Nexus 5 and Nexus 7 owners, there's a lot that Google didn't tell us about their latest mobile operating system, rumored to be called Lollipop.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

If you've ever seen one of those Samsung commercials from about a year back, you know that the Galaxy S series of phones come with a feature that allows you to do certain things by making gestures in front of your screen. They call this feature Air Gesture, and it enables you to perform certain functions without even touching your phone.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

A picture is worth a thousand words, and depending on what you're taking a picture of, it could be worth a lot more. Our phone's camera can easily capture high quality photos, scan barcodes, and make us Instagram famous. You can compare prices of items and download applications just by scanning a QR code. Of course, we can always do this stuff a little bit better on our iPhones.

The advent of a new Nexus phone begins with the bigwigs at Google partnering with a manufacturer, then selecting that manufacturer's flagship as the model for the new Nexus hardware.

Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC.

It's rare that a developer listens to the wishes of the masses, but that's exactly what CyanogenMod has done with their new CyanogenMod Installer, which automates the entire ROM installation process on your HTC One or other Android device. Previously, upgrading from the stock HTC One ROM to CyanogenMod required an unlocked bootloader, a custom recovery, the latest CM version, and Gapps. Let's be honest—unlocking the bootloader is a pain the ass, and probably the only reason stopping most peop...

Attention all veterans and active-duty military personnel—this coming Tuesday, November 11th, is Veterans Day, that time of year where the whole country thanks us for our service. For the most part, a simple thanks will do, but some folks like to go above and beyond and give us veterans free or discounted meals and discounts on merchandise in stores.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

You probably know Lenovo from their low-cost Windows PCs here in the states, but something you may not be aware of is that they also make smartphones. Right now, their biggest market is in China, but a rumored merger with BlackBerry could make Lenovo a contender in North America, not to mention one of the biggest smartphone manufacturers in the world.

Why can't I see who is stalking my Facebook profile?

The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history!

The most viral internet cat of the moment is a virtual kitty trapped in a billboard in the Shinjuku district of Tokyo, Japan.

QR codes are so handy. Nowadays, all you have to do to scan one is open your phone's camera app and tap a button. But creating one is a different story — online QR code generators aren't always trustworthy, and most phones don't have a built-in feature for it. Thankfully, Google Chrome now does.

The Galaxy Note 20 series has one of the largest screens on any smartphone. Such a massive display not only makes it easy to enjoy videos, but it also makes split-screen mode more viable, as each half of the screen is large enough to enjoy the content — including two different videos.