Snapchat just fast-tracked the majority of its app user base into the world of augmented reality production by making its Lens and Filter tools available to anyone with a web browser.

Exposed to hormones, pharmaceuticals, and other chemicals, the beautiful wild fish in Canada's Grand River have taken on some pretty odd characteristics—they're turning into females. A long-term study suggests using bacteria to manage polluted water could turn the tide for feminized fish.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.
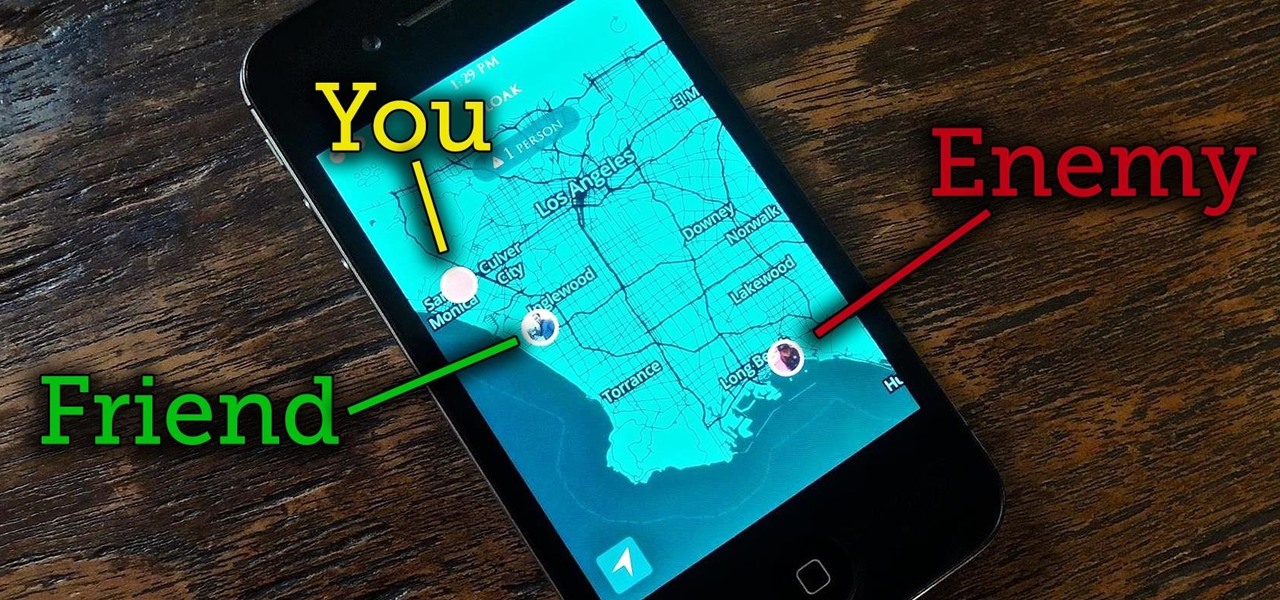
I never want to bump into my ex-girlfriend while out in the city (talk about a buzz kill), so if I could get an alert telling me that she's at Shortstops down the street, I'll avoid that area completely. This is where the new, interesting app Cloak - Incognito Mode for Real Life from dev Brian Moore comes in.

Take a walk on the wild side at La Pointe de La Torche, France, where powerful winds and waves draw surfers from all over the world. The rugged beach is located on the edge of northwestern France, in Brittany, where the Bay of Audierne opens to the Atlantic.

Good for fantasy art, and anyone learning fantasy illustration. I go over how I draw a swamp monster. If you want the step by step, it is located at:

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Smartphones have put an end to camcorders. If you want to capture memorable moments in high quality, look no further than that technological marvel in your pocket. Recent Galaxy phones are shining examples of how far we've come — but the more capable a camera gets, the more complicated things can be.

The greatest pain in owning a high-powered gaming PC is the simple fact that you can't play it all the time. Sometimes you have work or school, and other times, you may just want to go mobile. When something like this impedes your ability to play PC games, you may end up settling for mobile games. What if, instead of doing that, you were able to play your PC games from your iPhone?

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

After debuting its virtual Pocket Gallery last year with the works of Johannes Vermeer, Google Arts & Culture has released a sequel that brings even more artists into your home via augmented reality.

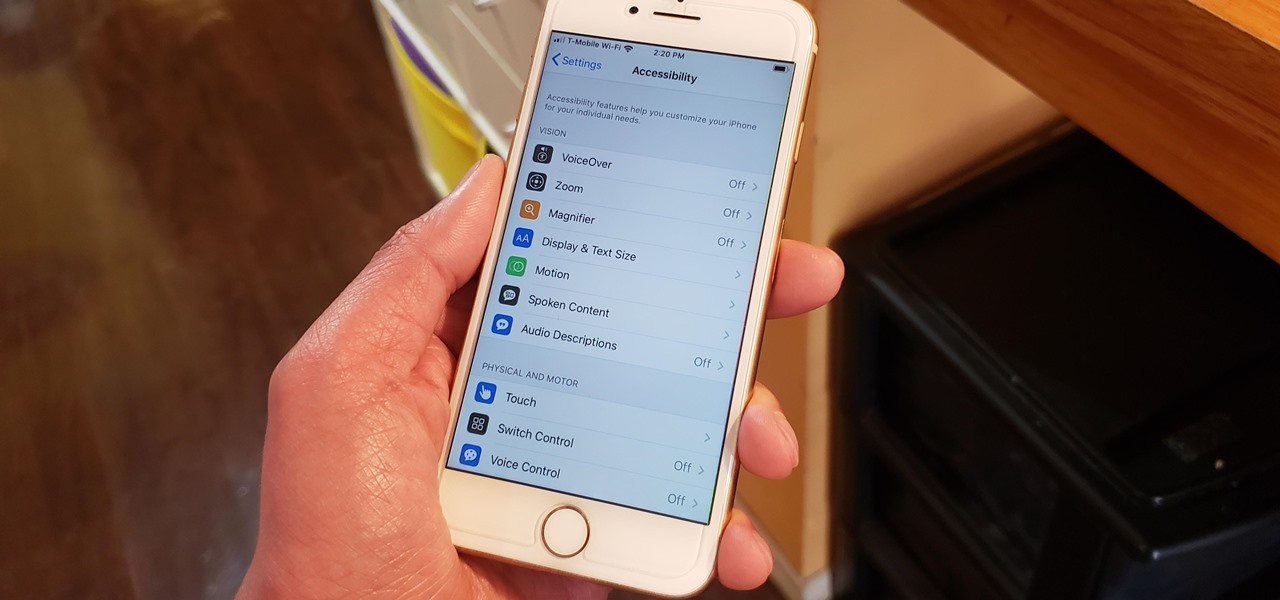
The iPhone's "Accessibility" menu is one of those options that's very easy to overlook but incredibly handy in certain situations. You can set AssistiveTouch to help navigate your device, use a Bluetooth mouse when your screen is acting up, and enable the red screen filter for nighttime escapades. For as long as the menu has been available, it's been in the "General" settings, but not in iOS 13.

As highlighted in our article on how to enable Google Now in Action Launcher, doing so takes away the Quickdrawer. This effectively ruins one of the more beneficial features of Action Launcher, making it a tough choice between the two options. So I looked for a solution and found one that works.

For those times when we need music grouped together for a specific task, we have playlists. Playlists are the next natural step after mastering your library and radio stations. While you've probably been an All-Star of curating playlists since your mid-90s mixtapes, Google Play Music has some pretty neat features that are going to really Smash your Mouth.

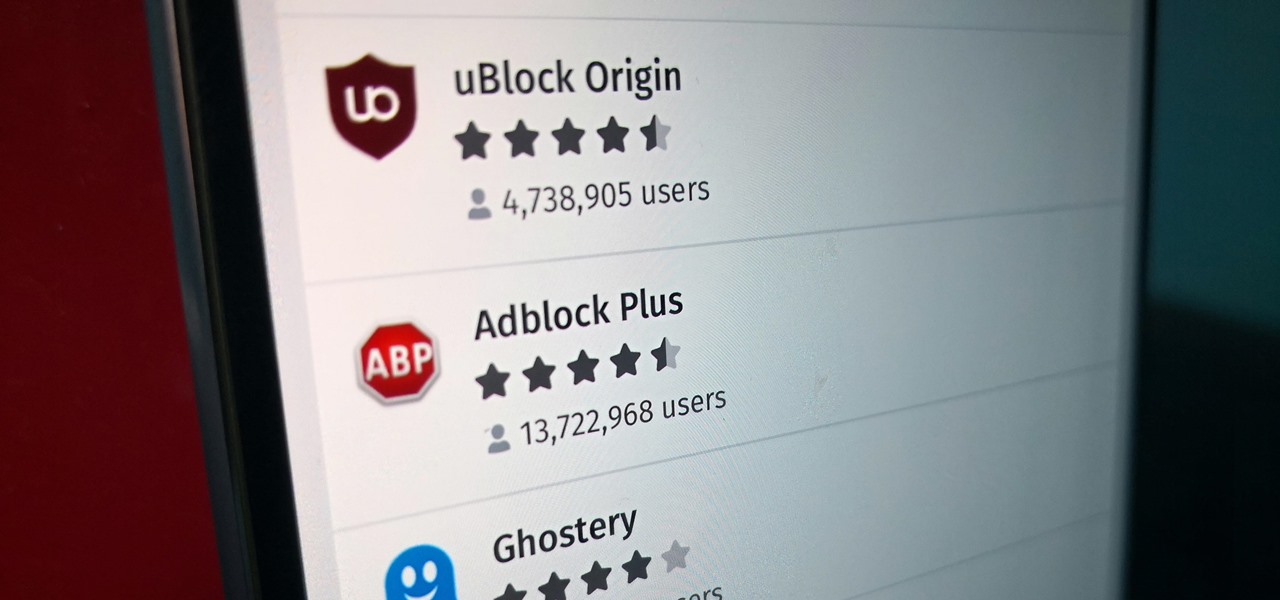
Features like themes and a tab queue make Firefox an extremely versatile mobile browser. Mozilla is constantly adding bonus functionality like this to Firefox, but a long-time staple is perhaps the most powerful feature: Extensions. This system gives you the ability to add features without having to upgrade the entire app.

More often than not, road trips will include unforeseen pit stops that have to be made, no matter how well prepared you are. In the past, making an unscheduled stop may have led to headaches and delays when your navigation app got off track, but thanks to a feature in Google Maps, this is no longer an issue.

Aspiring engineers, your challenge, should you choose to accept it, has been issued by Jaguar Land Rover.

Stratford may soon become Canada's answer to Silicon Valley as the driverless car industry arrives. Potentially changing the character of the Ontario town known for hosting the Stratford Festival, a celebration of all things Shakespearean and stage-related.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

You know how annoyed you get when you put a quarter into the vending or washing machine and it gets stuck? There's a quiet rage that boils inside you. Now, imagine that quarter is a sixty dollar video game, and it's stuck inside your brand new, four hundred dollar PlayStation 4 system.

Windows 7 has a new feature called Device Stage. It's a powerful and handy hub for all of your electronic gadgets that connect to your PC. It's device management for the power user! Microsoft shows you the layout real quick, so watch and learn.

Libraries is a cool new feature in Windows 7 that helps you find and manage all of your documents, music, pictures and videos in one location, no matter what location there in. This video from Microsoft outlines the usage of this new feature.

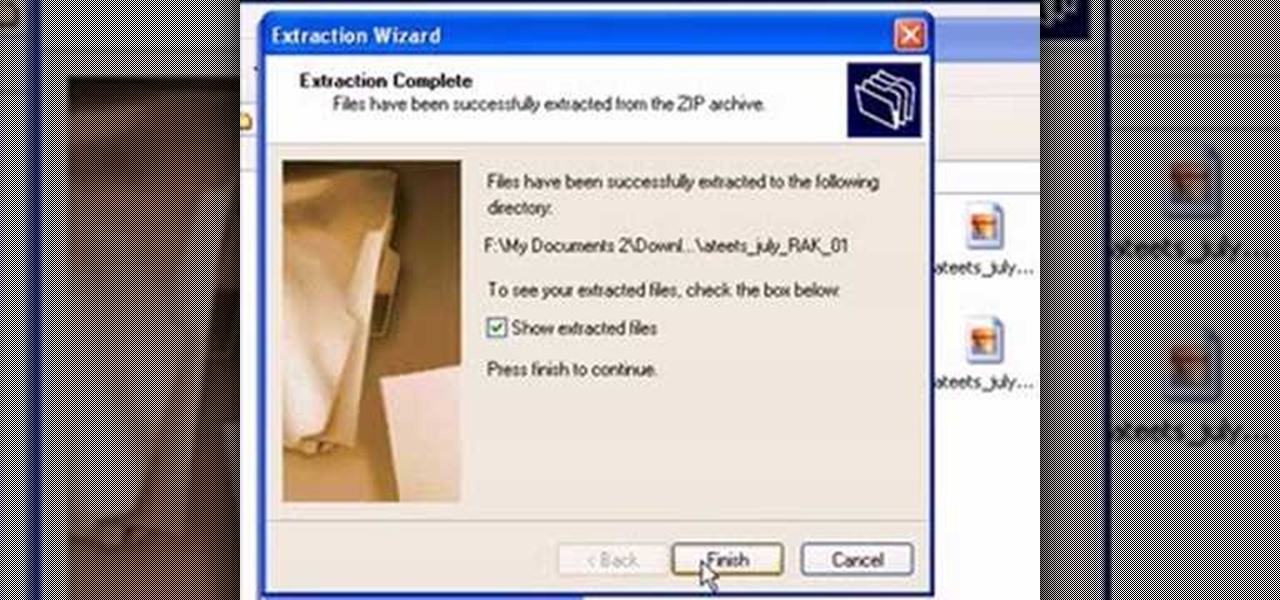
This video from scrapwow shows how to unzip a file in Microsoft Windows XP.Firstly, open Windows Explorer application and navigate the file you want to unzip. Once you've located the file, double click on it. A new window will open. Here you will have Extract all files option which you can choose from menu to the left.Clicking the button allows you to extract a single file or a zipped folder, containing a number of files. In this case Extraction Wizard will open, leading you through the extra...

Need to know what kind of oil your car needs? How about your vehicle load capacity? What about the standard maintenance procedures for you specific make and model? All of this and more can be located inside your owner's manual. If you don’t have an owner’s manual for your used car, you may still be able to find one even if your car is an antique.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

The North remembers...that smartglasses are the future! Game of Thrones jokes aside, the smartglasses startup opened its doors, and we visited its Brooklyn store to get our hands the consumer-focused Focals smartglasses.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

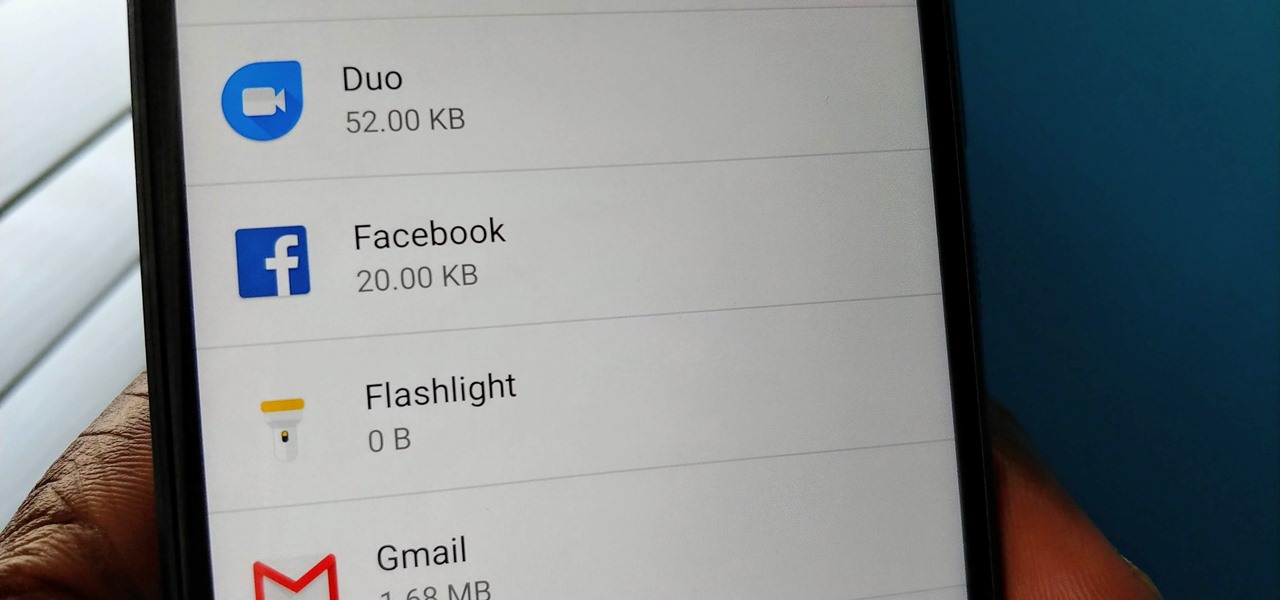
Despite years of user complaints, OEMs are still preinstalling third-party apps on brand new devices. Even in 2019, you'll still find plenty of phones with Facebook preinstalled. What's worse, it's installed as a system app, so it can't normally be uninstalled without root access. However, there are a few workarounds.

Getting new loot can be challenging in Fortnite Battle Royale. Whether you decide to pay for the Battle Pass or stick with the Free Pass, you still need to put in 50+ hours to unlock all the items. For those of us with Amazon Prime subscriptions, there's another way to unlock free items, and it won't cost you an extra dime.

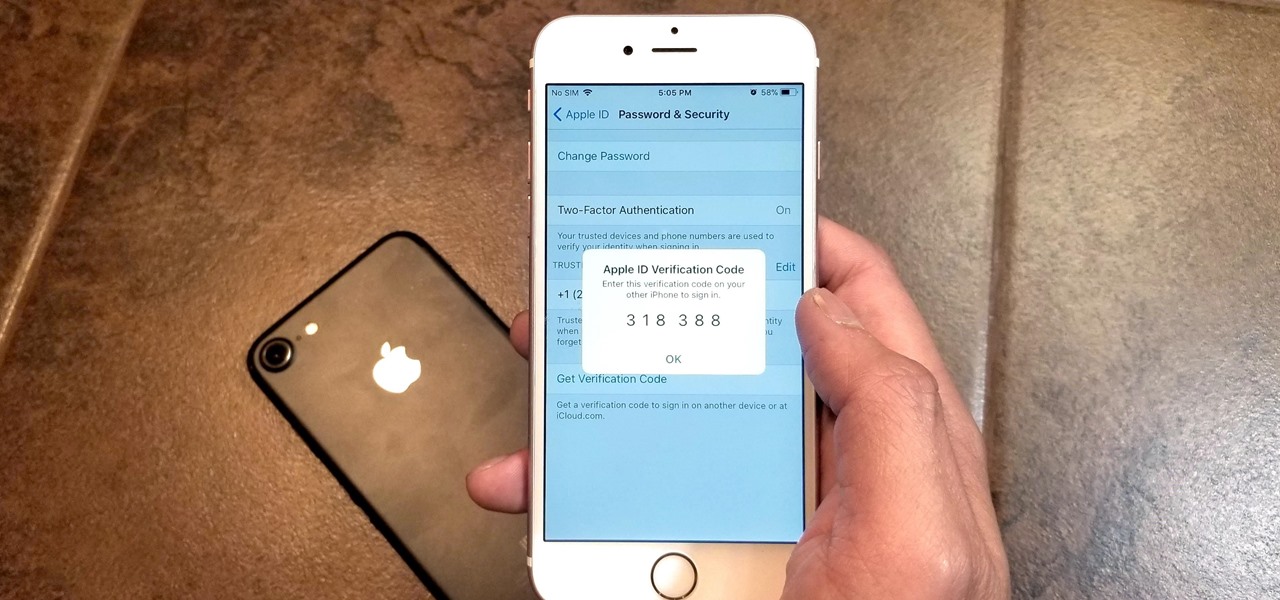
Two-factor authentication has been around since iOS 10. It's a handy option that adds an extra layer of security to your iPhone and makes its almost impenetrable security even stronger. This feature has remained intact in iOS 11 and iOS 12, and thanks to the straightforward nature of iOS, is relatively easy to enable.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.

When a new jailbreak method comes out, Apple is quick to patch the vulnerability it exploits by issuing a new iOS update. If you were to accept such an update, you'd no longer be able to jailbreak your iPad, iPhone, or iPod touch unless you could roll back your firmware to a version that could be jailbroken. But Apple even takes things a step further and stops signing older iOS firmware versions, which makes downgrading next to impossible. This is where your SHSH2 blobs come into play.