Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.
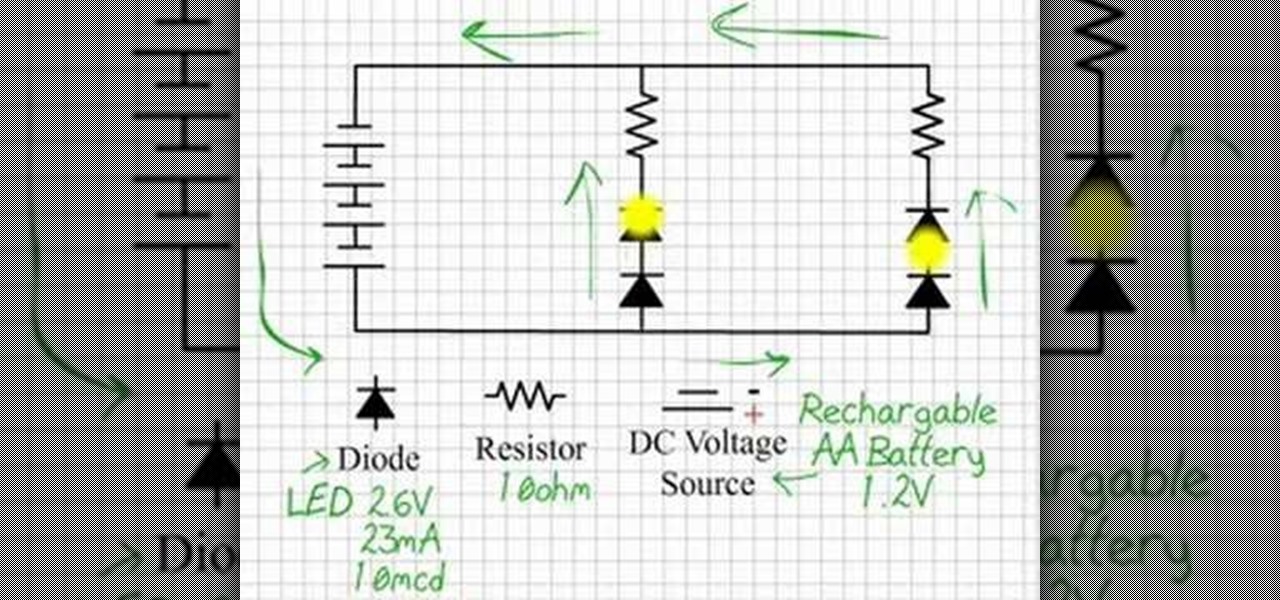
By using LEDs that only put out a little light the eyes can be lit in dim room light but still appear white, the moment the eyes are in shadow they glow bright red. Watch this video tutorial to see how to make glowing LED creature costume eyes for your film or costume project.
Watching videos on an Amiga computer without a web browser is really easy. Actually, you do need an internet browser to grab the links and the FFmpeg package. Once you have the links and have FFmpeg installed, then you can watch any videos streamed by YouTube without any browser.

In this Autos, Motorcycles & Planes video tutorial you will learn how to check and inspect the radiator hose damage and installation condition on your motorcycle. Make sure that the bike is cold and then locate the coolant system. Check the hoses by pressing them with your fingers. They should not be too hard, or soft or brittle. Check the clamps are in place and properly torqued. Visually inspect all the pipes and see that there are no dents. Repeat the same steps on the other side of the bi...
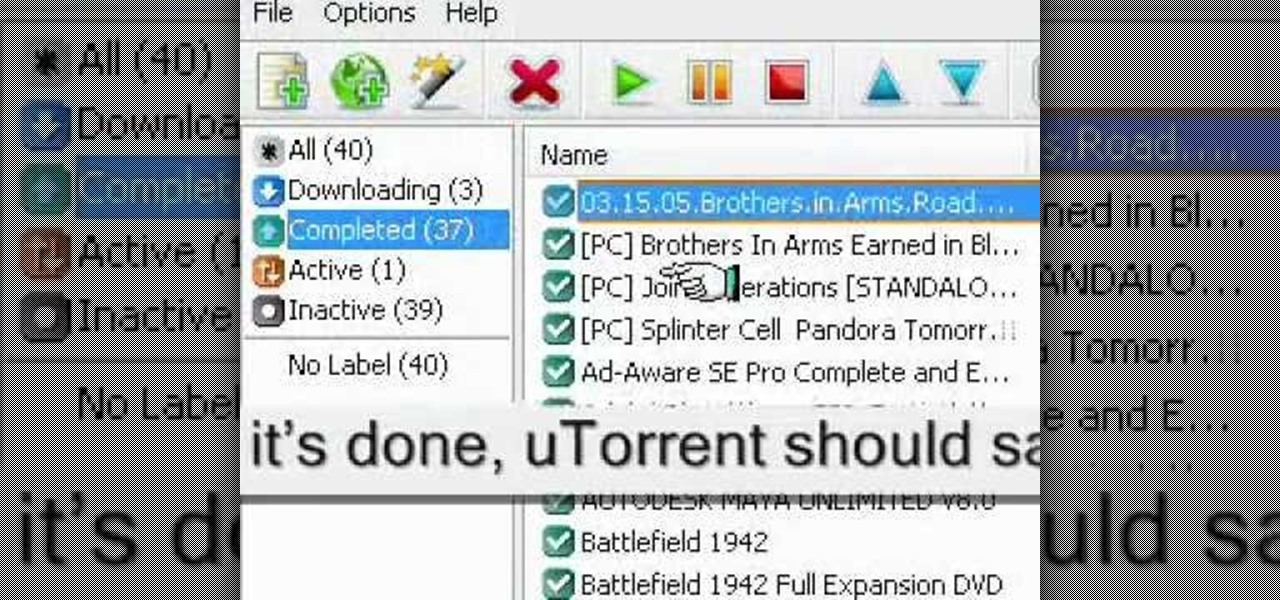
In this video tutorial, viewers learn how to seed a torrent in the u-Torrent client. Begin by downloading and saving your torrent file. Make sure that you uncheck Start Torrent when it opens. In u-Torrent, right-click on the file, go to Advanced and select Set Download Location. Now locate the torrent file and click OK. Then right-click the torrent again and select Force Re-Check. When it's done, u-Torrent should say that the torrent is 100% finished. Right-click the torrent and click on Star...

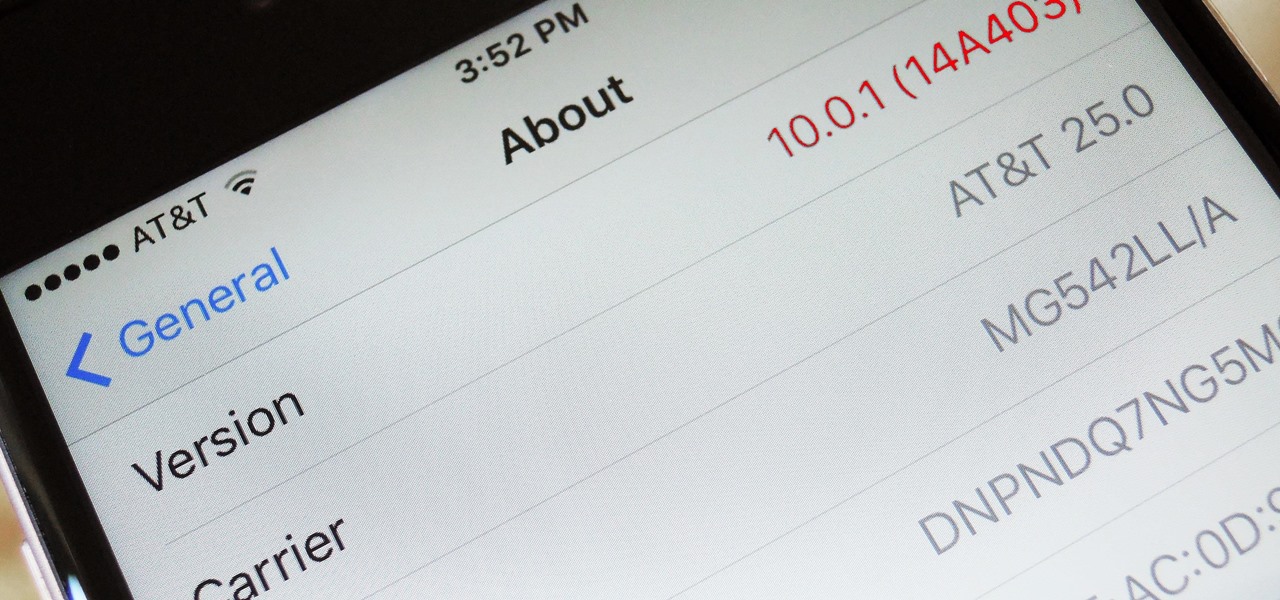
In this tutorial, we learn how to force an iPhone or iPod touch to turn off. First, hold the power button ( at the top of the device) and home button (one the bottom middle) at the same time and wait until the screen turns completely off. To turn back on, press the power button that is located at the top of the device. You will see an Apple logo pop up and it will stay on the screen for several seconds. After it's loaded, it will re-boot as normal and your regular home page will show up as it...

In this video tutorial, viewers learn how to recover lost data using R-Studio. Begin by running R-Studio. Locate the drive that you want to recover. Right click it and select scan. The scan can take up to 45 minutes depending on the size of the drive. Once its finished, there will be a list of hard drives in which data is stored. Green, black, and orange will recover with no problems. Red is not recoverable. Double click on the wanted drive and wait for it to load. You can now see all the dat...

All of us guitar players love to play our favorite songs on our own guitars. Sometimes it is hard to learn how to play specific songs. It can also be difficult to locate a tutorial on how to play these songs! Old Crow Medicine Show's "Wagon Wheel" is a great song that is fun to play, especially for fans of Bob Dylan. By viewing this 5 minute video and with practice, you'll learn how to play "Wagon Wheel" like a professional! If it is hard for you to bar your frets, be sure to use a capo and l...

To become a Victoria's Secret model, use the Internet to locate agency Web sites and register photos on-line to be viewed by modeling agencies. Build a portfolio and gather head shots for becoming a Victoria's Secret model with tips from a modeling instructor in this free how to video on modeling.

Eve reveals the tricks of the trade and shows how to hide that double chin and manage a blotchy face.

There are more than a few exciting new Home Screen customization options available in the iOS 18 and iPadOS 18 software updates, including some we've been waiting years for. Apple never mentioned a few of these new features and changes in the release notes, but you can see them all right here.

There's a world of hidden features on your iPhone just waiting to be explored, and one of them is hiding in plain sight right in front of you. You likely see it multiple times a day after performing a routine action without ever thinking twice about what else it can do, and you're not the only one.

There's a feature hiding in your iPhone's Mail app you may have missed but should definitely know about. It gives you quick access to something you'd typically have to dig around in folders to find.

There are many things your iPhone or iPad can do, and Apple does an excellent job of documenting everything on its website. But there are some features that won't show up in any Apple manuals or help pages.

One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. It's like having a safe built right into your smartphone, and it couldn't be easier to set up.

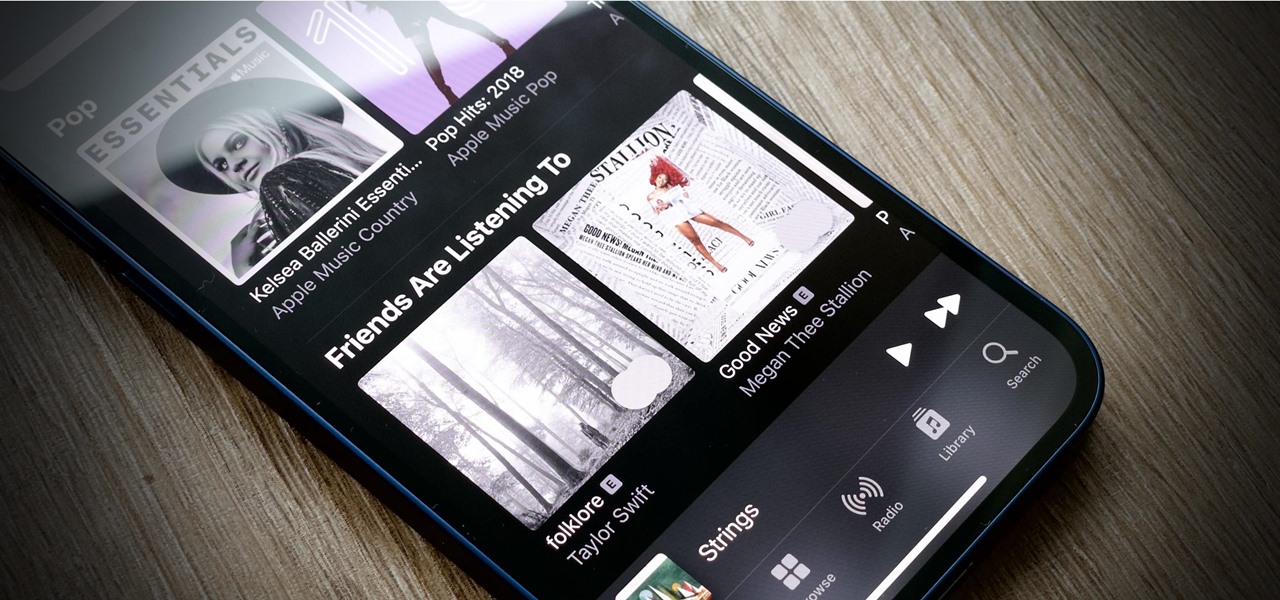
You shouldn't care what other people think, but sometimes, it's unavoidable. Take your music tastes, for instance. Sure, you might want your friends to think you only listen to the coolest songs, but we all have our guilty pleasures. If you're uncomfortable with your peers seeing your listening history in Apple Music, know there's something you can do about it — on iOS or Android.

One thing about the small round little Pixel Buds — they might get lost easily if you have a terrible habit of misplacing stuff. Or worse, imagine someone taking a liking to them a little too much and stealing them when you aren't looking. Google thought ahead about these issues, so just like your smartphone, you can track your wireless earbuds from anywhere with ease.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

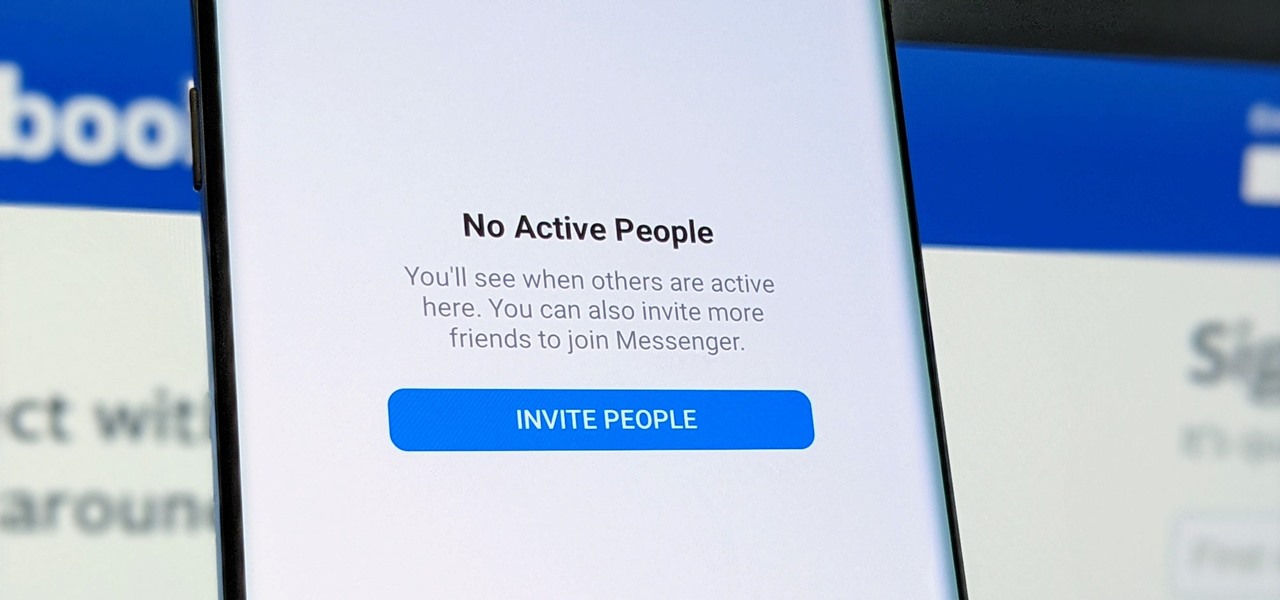
Facebook Messenger's user base has grown so much that it has taken over text messaging as the primary contact method for many people. However, sometimes you might want to hide your online status from specific contacts and appear offline to others. There's a neat little trick you should know that can help you achieve this.

There's a whole world of hidden iPhone features you might be missing out on, but this little-known tool for iOS is something you should definitely enable so that it's ready when you need it.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

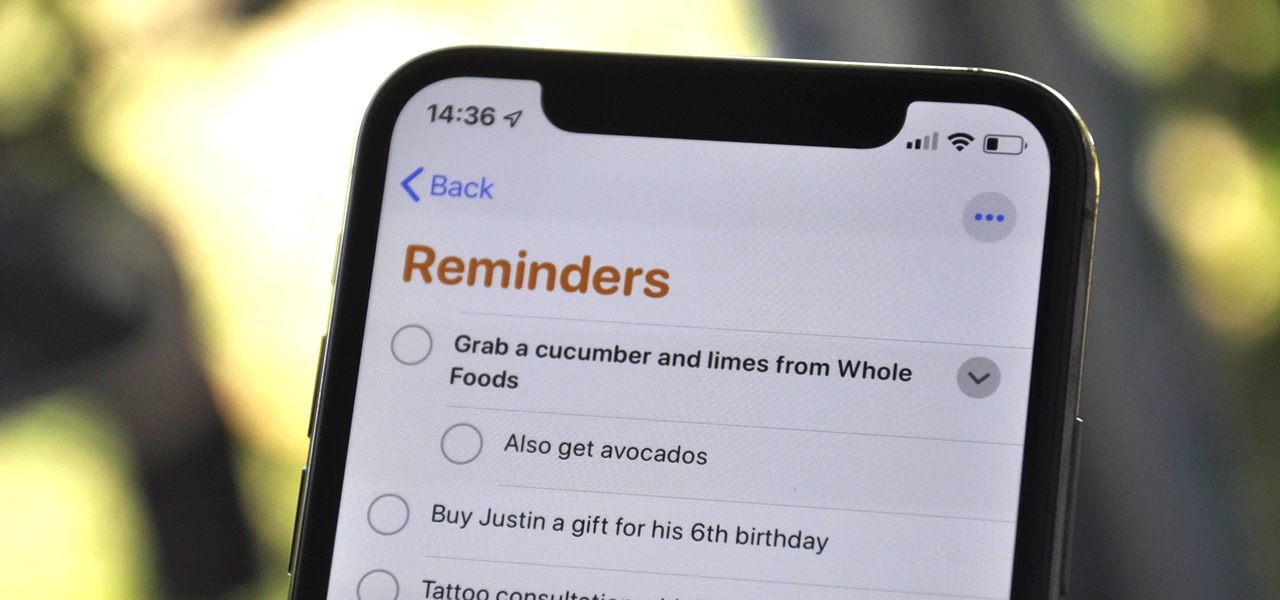
Things are a bit more organized in Apple Reminders, so the cluttered mess that it once was is no more in iOS 13. The slapped-together feel in older iOS versions was the main reason I never used it that much, but the updated version for iPhone has finally got me hooked.

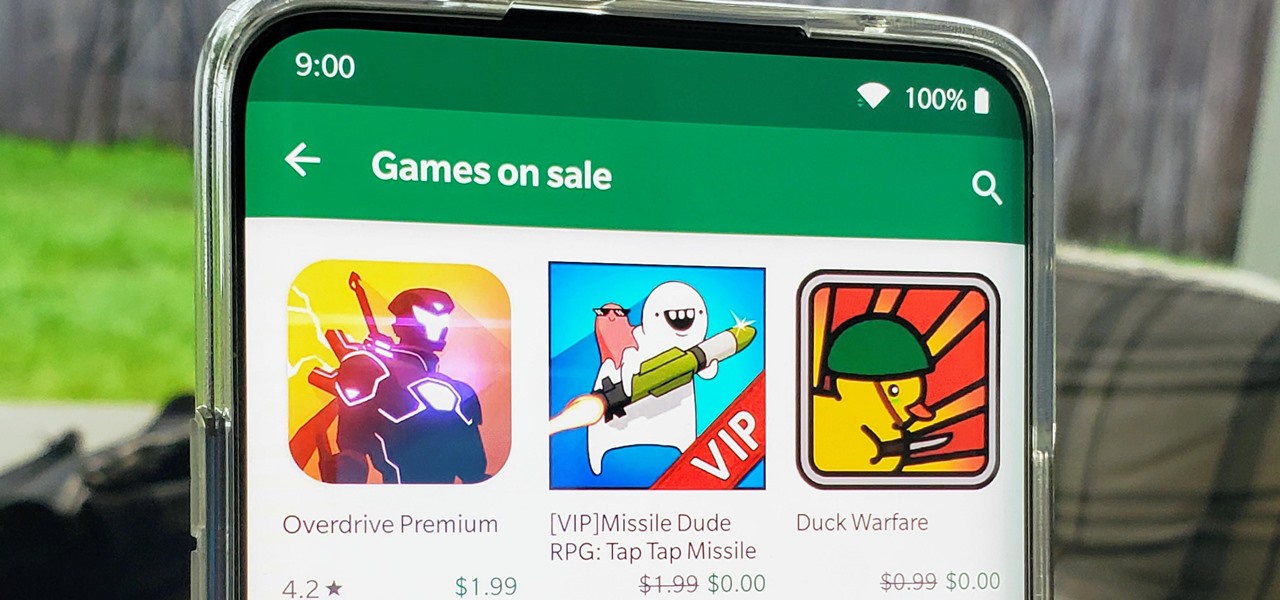
I think we all like the idea of getting paid games for free with minimal effort. Typically, though, anything claiming to help you do that is either illegal or a scam. But there are actually quite a few no-fuss methods that can get you paid games without going too far out of your way. From checking notifications to discovering hidden offers, you might have something waiting for you.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

The greatest pain in owning a high-powered gaming PC is the simple fact that you can't play it all the time. Sometimes you have work or school, and other times, you may just want to go mobile. When something like this impedes your ability to play PC games, you may end up settling for mobile games. What if, instead of doing that, you were able to play your PC games from your iPhone?

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

If you have encountered bed bugs lately, you are not alone. While the pesticides used to fight these pests are losing effectiveness, a fungus shows promise in knocking the bugs out of beds everywhere.

When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that users discover along the way.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

So you finally decided to make the switch from iOS to Android, huh? Well first off: welcome to the world of tomorrow. And secondly: good call, mate.