Dips are great exercises, in or out of the gym, and are easily done. They're the perfect exercise for working out your triceps brachii and pectoralis muscles. This also works out a secondary muscle— the deltoids. THe beginner to intermediate exercise is a great way to work all three muscles. All you need to do this exercise is the vertical knee raise towers which most gyms have. For those who are new to this exercise and are unable to lift themselves, you can use the weight assistance to buil...

Angelina Jolie could probably style her locks into a day-glo orange fauxhawk on the red carpet and still be the most beautiful and fabulous woman there. In short, she's gorgeous enough that she can keep most of her makeup, hair, and dress choices simple.

This video demonstrates how to install additional memory into a Power Mac G5 system. It is G5,1.8 single processor machine.Start by lifting up the latch on the back for the front door. Remove the front door. Remove the plastic air blocker system and remove the main fan assembly just like is told. Going to install four 1GB memory, these are OWC 1GB chips. It's very simple to install. Have to install memory in matched pairs. There is existing 512MB memory in the form of two 256MB chips in this ...

Watch this video to learn how to cheat on a test with help from your iPod. Ask a trusted friend for their notes/answers the night before. Then at your computer, just type up their notes/answers, or the important parts, and then save it in your computer as "How to make Grandma's Secret Fudge Brownies.txt" . Now plug your iPod into your computer and click Start- My Computer- (someone's iPod- Notes. Now you will need a separate window. Click Start- My Computer. Now find "How to make Grandma's Se...

Barbabella shows how to make a modular origami hexagonal box lid with star design. Fold a two-sided square sheet of paper to form a triangle, unfold it and fold it in the opposite direction. Using the guidelines fold the paper on three sides forming a small triangle and leave one end as it is. Turn over the sheet and fold the opposite side of the unfolded one as shown. Now mark the points as shown and fold it on one side. Now fold it to mark point below and the crease ends at the point marked...

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to animate a 3D plane in Photoshop.

In this ten-step video tutorial, you'll learn how to quickly copy keys using a camera, printer and Dremel tool. With this ten-step process you'll learn the necessary steps to copy almost any key... even if you only have access to it for a brief period of time.

Pulling off the perfect ponytail is easy once you know a few tricks. You Will Need

Zacuto Universal Baseplate V3, includes 12-inch rods and works with all cameras. Zacuto's Universal Baseplate allows mounting accessories off the front and the back of the rods. Our new version 3 Universal Baseplate is 22% lighter then Version 1 or 2. The baseplate measurements (excluding rods) are 7 x 4 x 1 ½

Have you tried working out with advance triceps dips? Advance triceps dips are an essential part of body sculpting and strength training. This fitness how-to video demonstrates how to work out the triceps muscle with advanced triceps dips. Learn about arm exercises in this training video.

All of these four videos are excellent. You will notice that while all the videos and articles have slightly different design dimensions, they are fundamentally very similar. I urge you to view and read everything I am serving up. Then, my final words of advice are simply....choose between a barbeque switch and a taser gun. (Hint: there is a right choice, and there is a wrong choice.)

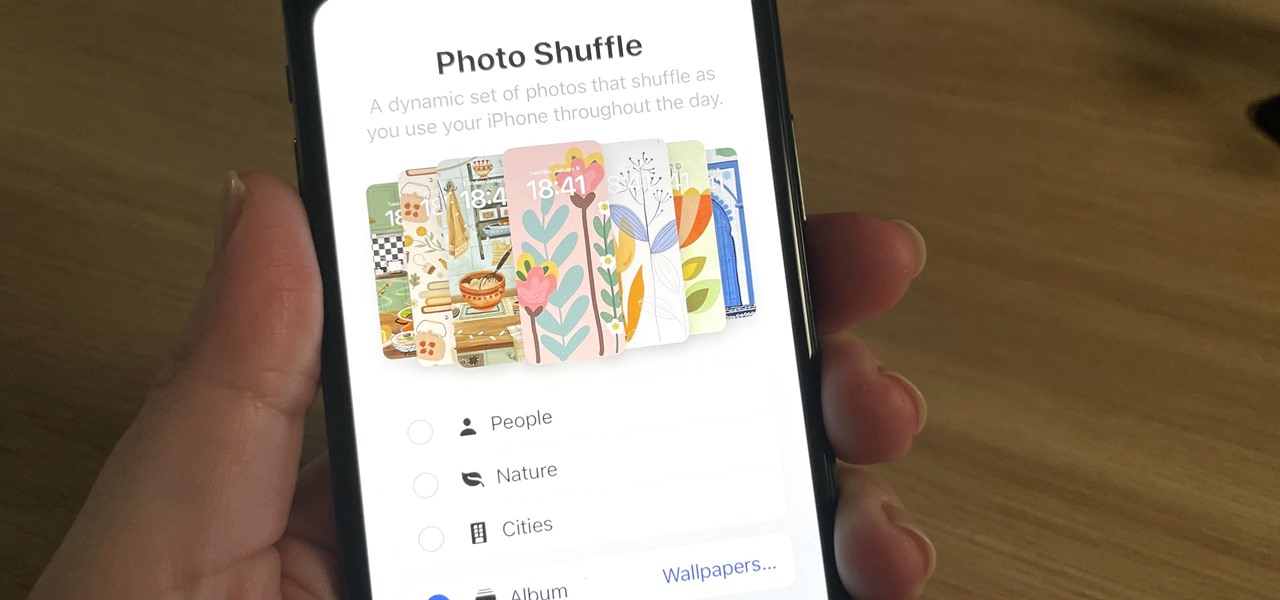
Your iPhone has plenty of already-created Apple wallpapers just waiting for you to set as your Lock Screen and Home Screen backgrounds. But using a photo from your own library can provide a more emotional connection, help you express yourself better, and give your phone a more unique look. To maximize these effects, auto-rotate your personal images daily, hourly, when locked, or when tapped.

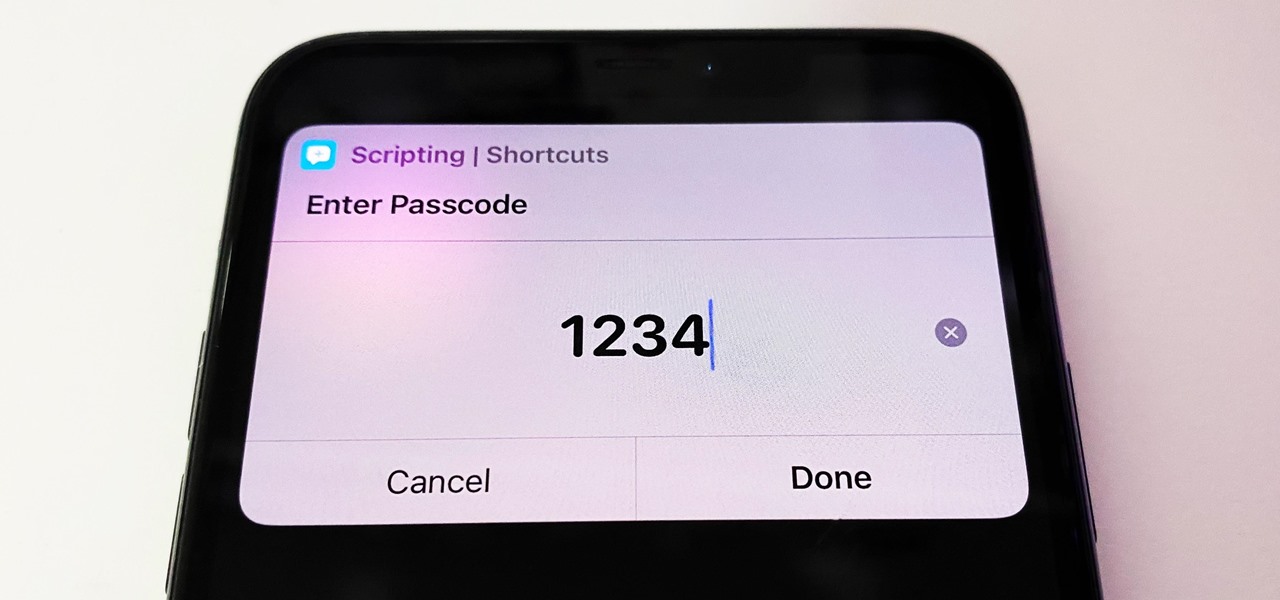
Some iOS and iPadOS apps give you an option to lock them behind Face ID, Touch ID, or a passcode, but there aren't many.

Since its introduction in iOS 11, the Screen Recording tool has been a great way to show less tech-savvy users how to use their iPhones better. It's never been easier to show your grandmother how to disable Live Photos or lower screen brightness. However, banner notifications can appear during a recording, forcing you to start over. They can even interrupt a screen share during a Zoom or Skype meeting.

In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

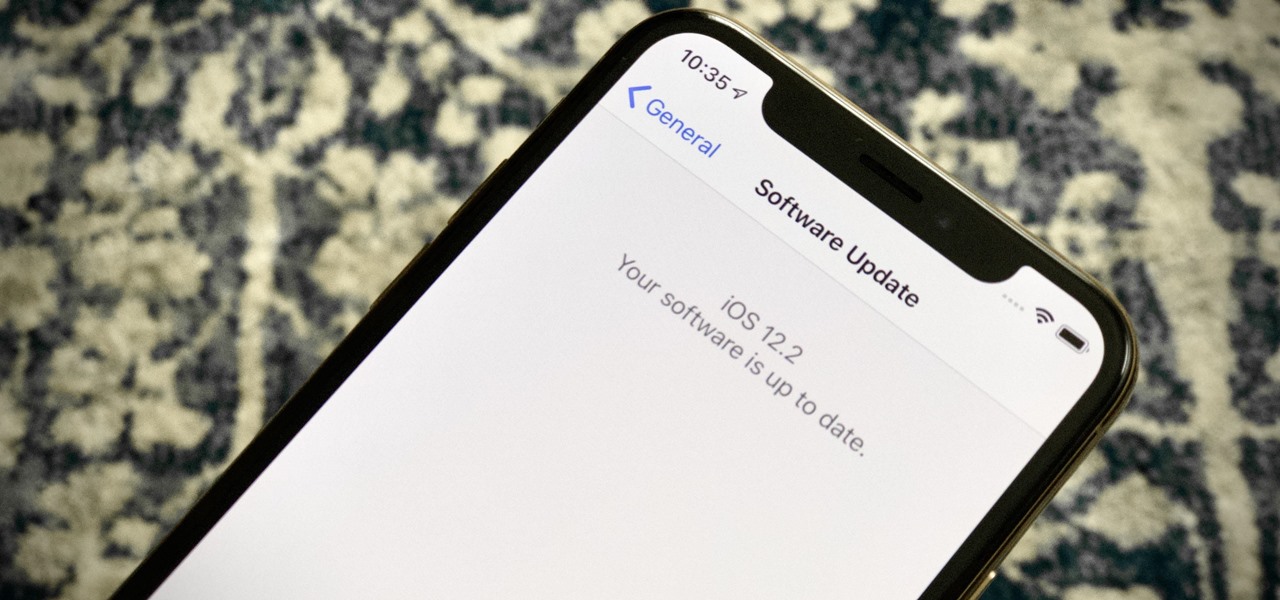
Public beta testers are in for a treat today. While Apple is extremely inconsistent with the release schedules for the developer and public betas, the company has once again released both versions of iOS 12.2 beta 5 today, March 11. If you're a public tester, you now get to experience all of iOS 12.2's new additions for yourself, instead of needing to read about them for up to 24 hours in advance.

If you're an iOS app developer, your Monday just got better; Apple just released iOS 12.2 developer beta 5 to your Software Updates today, March 11. This fifth beta includes a number of small UI changes and tweaks, and likely some degree of under-the-hood improvements and bug fixes.

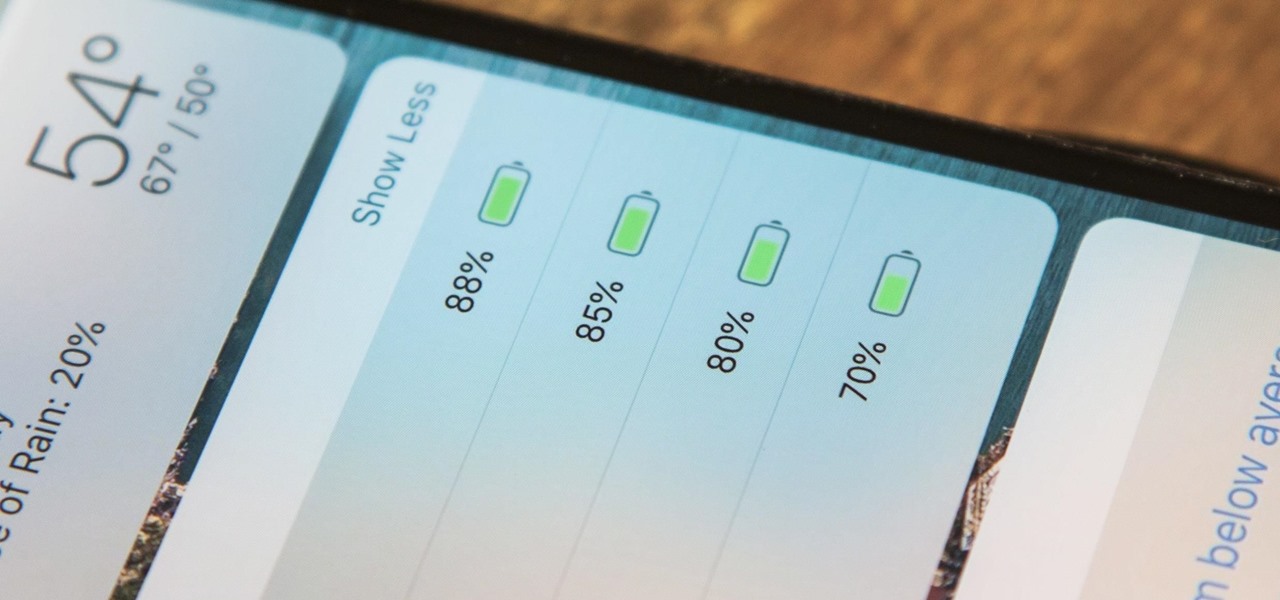
The battery icon in your iPhone's status bar gives you a visual idea of how much power is left, and there's a battery percentage option you can switch to or view in the Control Center, depending on your model. But what you may not know is that there's a way to view the battery percentage of every device connected to your iPhone, from AirPods to Bluetooth speakers and your Apple Watch.

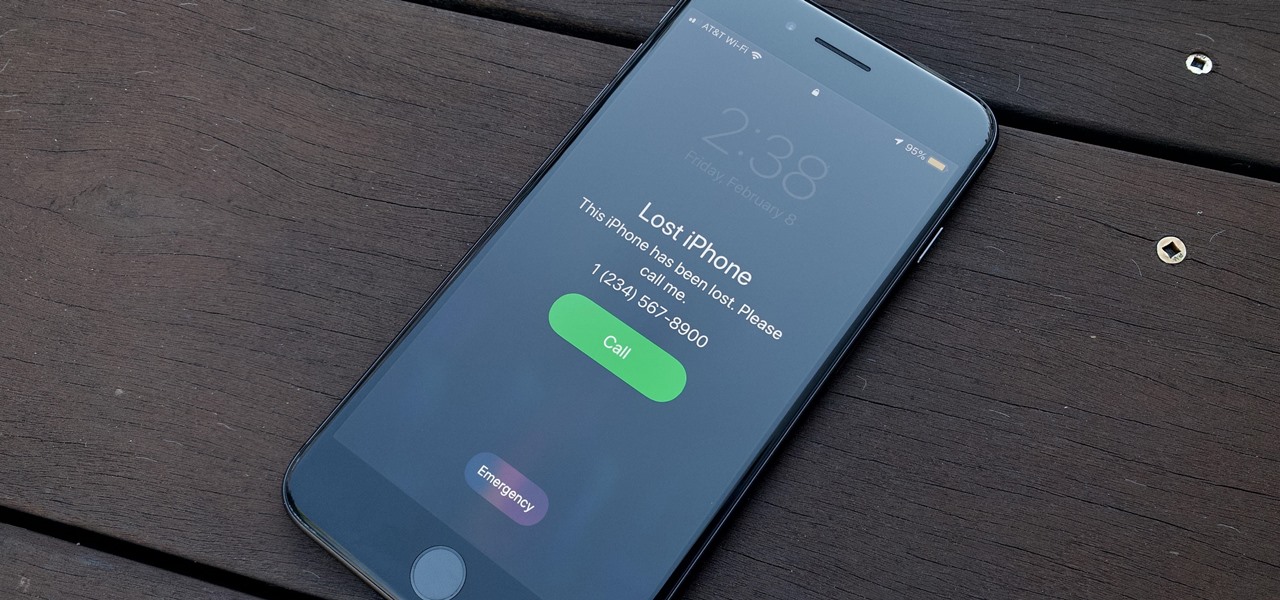
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

While iPhones may be more expensive than ever, it won't stop us from losing them or having them stolen. Whether you have an iPhone 5S or an iPhone XS Max, there's a good chance it'll go missing at some time during your ownership. It could end up in a couch cushion or in the hands of a pickpocket, but no matter what happens to it, you need to prepare it beforehand for the inevitable.

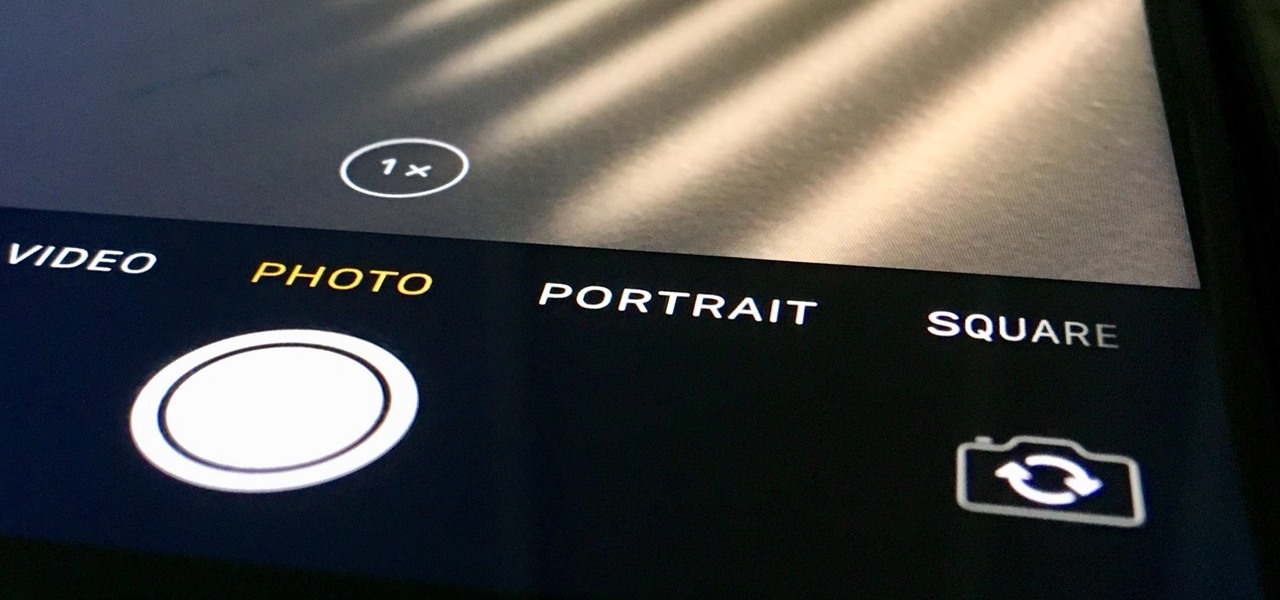
Even though your iPhone's Camera app is fast and easy to use, its default settings prevent you from immediately accessing any other shooting mode aside from "Photo" with "Live Photo" on and no filter applied. But there is a way to make the Camera app remember what you prefer the next time you open it up.

Less than a week after debuting its AR Cloud platform in public with a multi-user installation of more than 100 participants, Ubiquity6 announced on Tuesday that it has closed a Series B round of funding totaling $27 million.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

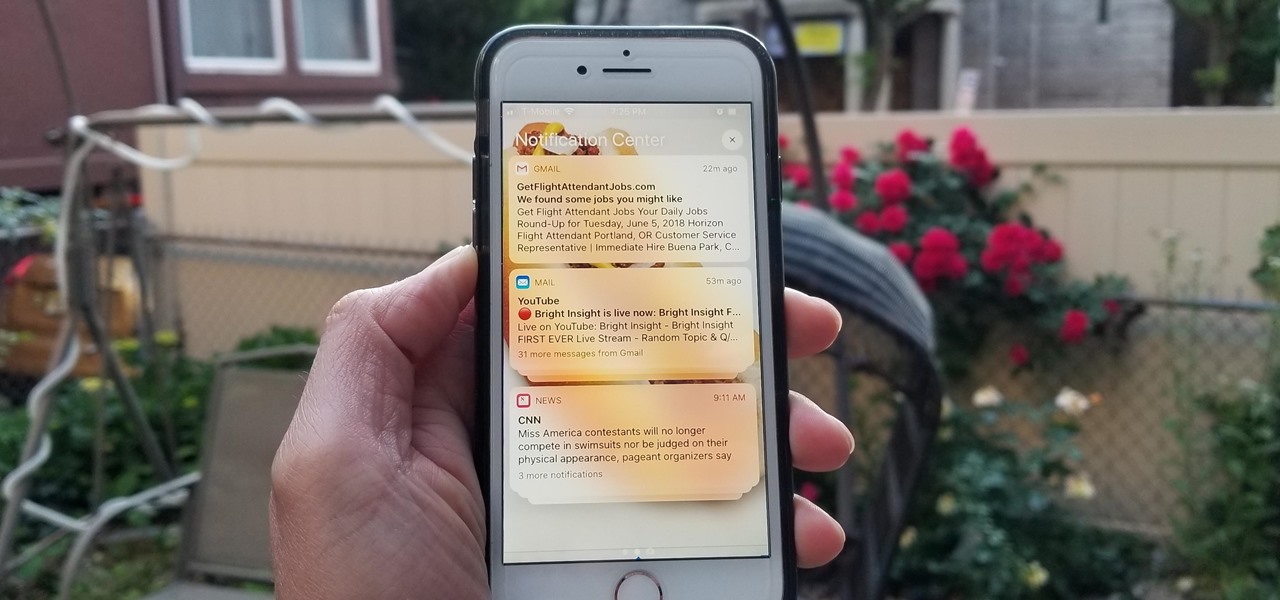
Apple's linear Notification Center has been scattershot at best since iOS 9 when we could group notifications by app. Without any type of grouping ability, the notification history becomes more of a nuisance of random alerts based on time alone, making it a treasure hunt to find the notification wanted. Now, iOS 12 has addressed this issue, bringing back groupings — with improvements.

The business of enabling the development of augmented reality experiences appears to be as lucrative as AR app development itself.

Google's AI investment arm, Gradient Ventures, has joined a $10.5 million round of funding for Ubiquity6 and its platform for shared augmented reality experiences, just weeks after Google's GV fund backed a competing AR cloud platform.

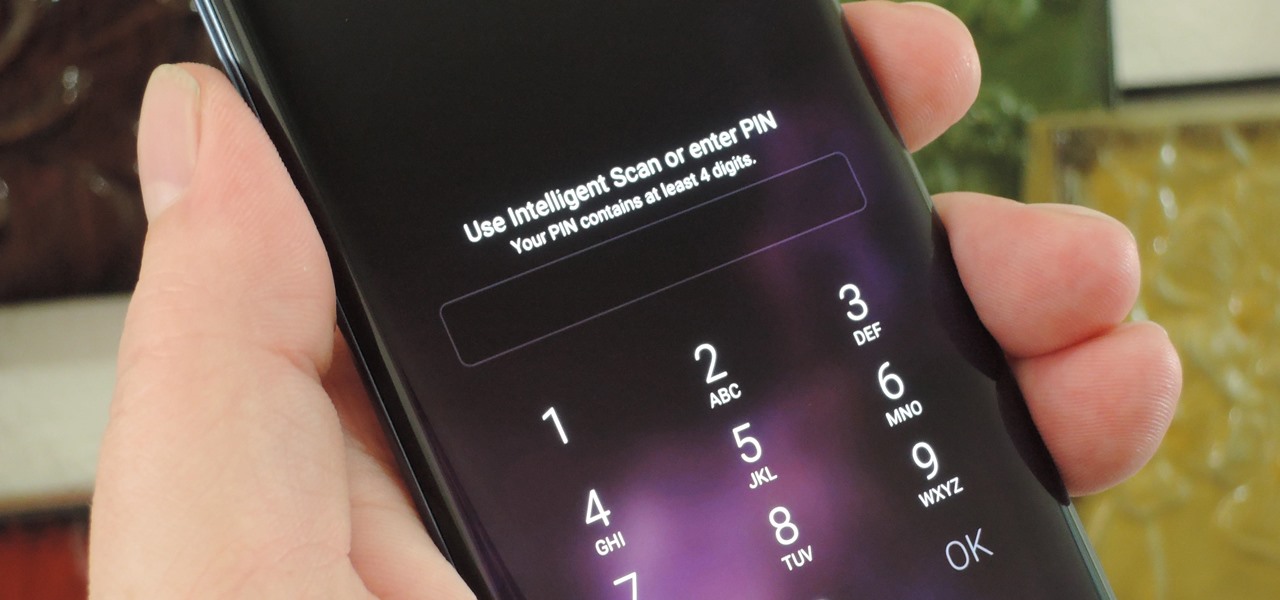
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these efforts is called Intelligent Scan.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

Android users have had access to live wallpapers since the Eclair days, but some newer apps have made this feature even more useful. Now, you have the ability to use GIFs as your wallpaper, and through the marvels of modern technology, you can even set a video as your home screen and lock screen background.

In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more controlled environment for developers to get feedback and zero-in on issues that may occur in a game's early development phases.

LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader is absolutely pointless, as having it locked will not hinder normal device usage, which is kinda true.

When you want to see something far away with a little more clarity or you're having a hard time reading small letters right in front of you, you can point your iPhone's camera at the subject and "pinch" to zoom for a better look. But there's actually something built into iOS for the exact purpose of magnifying objects, and it goes above and beyond the normal camera features.

We haven't had a working jailbreak method since October of last year, and that only worked for about a month until iOS 9.2 came out and shut down the loophole it was using. So all of those cool Cydia tweaks have been out of the question for quite a while now, unless you downgraded your firmware to keep jailbreak compatibility.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.