Performance and stability improvements, as well as new features, are just some reasons to install iOS 12, but new changes mean new battery health challenges. It can be difficult to boost battery life while taking advantage of everything this update has to offer. Luckily, there are plenty of ways to avoid unnecessary battery drain when using iOS 12 on your iPhone.

If you want the ability to play YouTube videos in the background as you multitask on your iPhone, you'll have to shell out $11.99 a month for the privilege of doing so with YouTube Premium. Not all of us can afford nor justify such an expense, but if your iPhone is jailbroken, you can get your hands on this sought-after feature — and much more — without spending a dime.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.
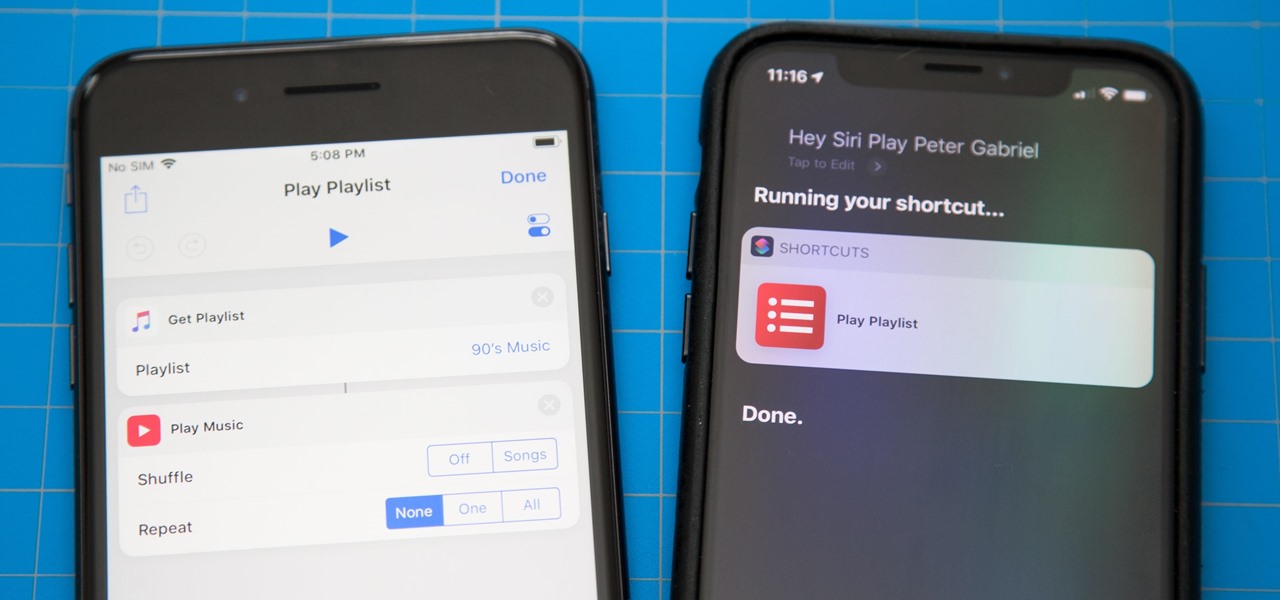
One of the most exciting additions to iOS 12 for iPhones is called Shortcuts, a tool integrated with Siri to help you get things done faster. While there are a few recommended shortcuts available to you in Siri's settings in iOS 12, the Shortcuts app brings the functionality of Workflow to Siri so you can build your own custom actions or select from the gallery of available shortcuts.

Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

There are a lot of Android phones out there, and chances are that someone in your life is looking for one this holiday season. Well, there also happens to be a lot of Black Friday deals on Android phones this year. So we've rounded up the best deals taking place on Black Friday weekend to help you save big.

If you've never used the Home button shortcuts on your iPhone before, you've been missing out. And no, I'm not talking about opening up Siri. By clicking the Home button three times, you could quickly pull up tools such as Magnifier, VoiceOver, Zoom, and Assistive Touch, but that's all changed on the iPhone X, XS, XS Max, and XR, which don't have Home buttons to click.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device.

When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side.

Apple's newest mobile operating system, iOS 8, is out for the general public, and we've got a rundown on the best new features you can use on your iPad, iPhone, and iPod touch. While there's not a huge visual change as there was from iOS 6 to iOS 7, there's still plenty of cool new features in iOS 8 to be excited about.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

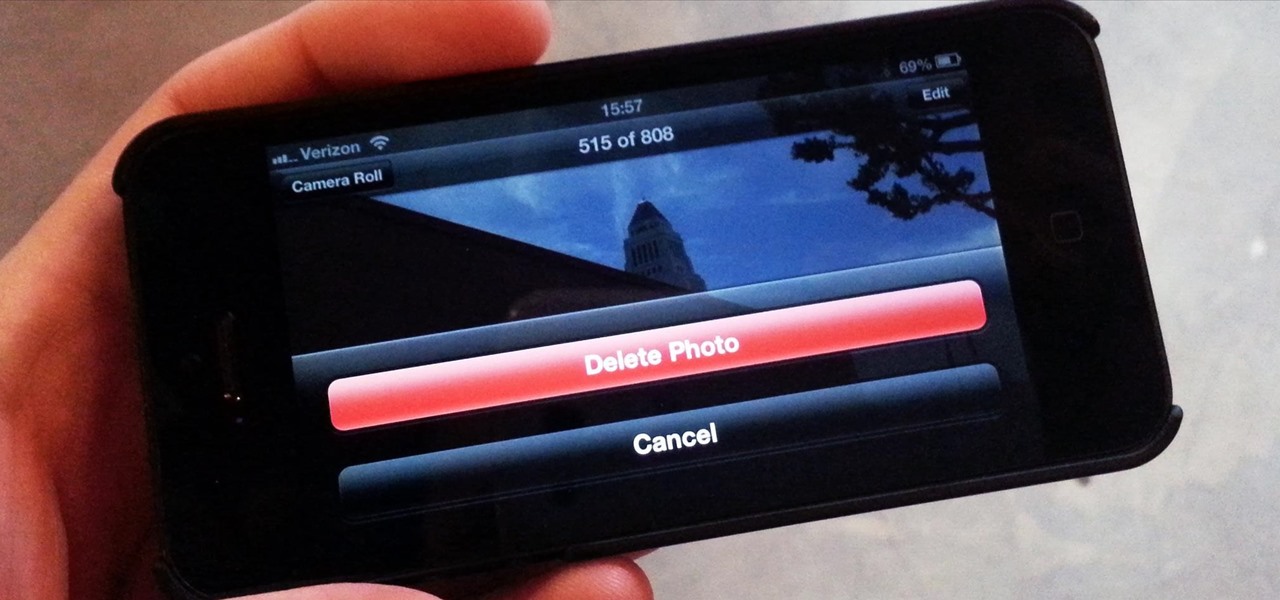
In one of Apple's newer ads, the company claims that "more photos are taken with the iPhone than any other camera." If this is in fact true, then it might also be appropriate to say that more photos are accidentally deleted on iPhones than any other camera.

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming, and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough; you'll always be looking for more...

Bikes are a great form of transportation. They use human energy more efficiently than any other machine. You can keep it in your closet or hallway. You can even take it on the train in a pinch. However, this portability is also the bike's biggest draw back. If you own a bike in the city, chances are it will be stolen. Locks barely deter thieves armed with bolt cutters and crowbars. Throw the bike thieves for a loop and make a tilt-sensitive alarm. It will hopefully startle your bike's assaila...

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Increasingly, I'm turning to Google+ as a source of news, and it looks like I'm not the only one. On Thursday, news of a small earthquake broke on both Twitter and Google+. One curious user, +Keith Barrett, decided to try and find out which social network was faster with the news. Turns out it was a tie. As Google integrates Google+ more closely with the rest of its services, and more users post relevant stories, I think we'll start to see Google+ as a place that can create and break stories,...

+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new Uncrunched blog, made a concise post revealing Facebook's dishonesty: Facebook submitted a patent application for "tracking information about the activities of users of a social networking system while on another domain...

This Null Byte is a doozey.

Even with Apple's forthcoming iOS 5 updates to its default camera application, those upcoming features can't match what already exists in Global Delight's Camera Plus Pro. For $1.99, Camera Plus Pro provides users with over 100 tools for every part of the picture taking process, including video recording. It works with all versions of the iPhone, iPod touch, and iPad 2 with iOS 4.1 or the later update. Let's examine what it can do, and why you will want to replace Apple's default camera with ...

Image via Tiger Mom Says.

Do you have an awesome rig that is able to run anything you throw at it at 60 fps with maximum settings? Prepare to be humbled. The Witcher 2 is the first game in quite some time to tax your system the same way Crysis did when it first came out.

Tera Online is a beautiful Korean MMO with real time combat. The game is coming to the states towards the end of the year. Unlike other MMOs were combat is target specific (lock on target) and dependant on skill timers and macros, Tera Online focuses on fast area of effect action. Your blade or spell will hit whatever is in front, or miss if it's not. The closest thing to the game play of Tera is Vindictus, a free to play MMO with the same concept of game play. If you've played Vindictus, the...

You've seen his explanation of a combination lock's inner workings. You'll never lose another game of Jenga, thanks to his winning wooden pistol. And nearly 4 million YouTube users have marveled at his wooden marble machine sculpture. He's Matthias Wandel, and he's accomplished what most only dream of—turning a hobby into a career. Matthias has been tinkering in woodworking since he was a child, with unrestricted access to his father's workshop, permitted to use power tools unsupervised from ...

WELCOME & THANKzZz For Your Contribution, Support And Time...! ...Hello, zZz~AKA~StanDP Here...;

Each aspirant nursing assistant is require to obtain CNA certification for their work employment. Thus, passing the CNA state exam is highly recommended. Usually the CNA testing process has two types of test - written and clinical exam. The most difficult yet challenging part of CNA test is the skill exam.

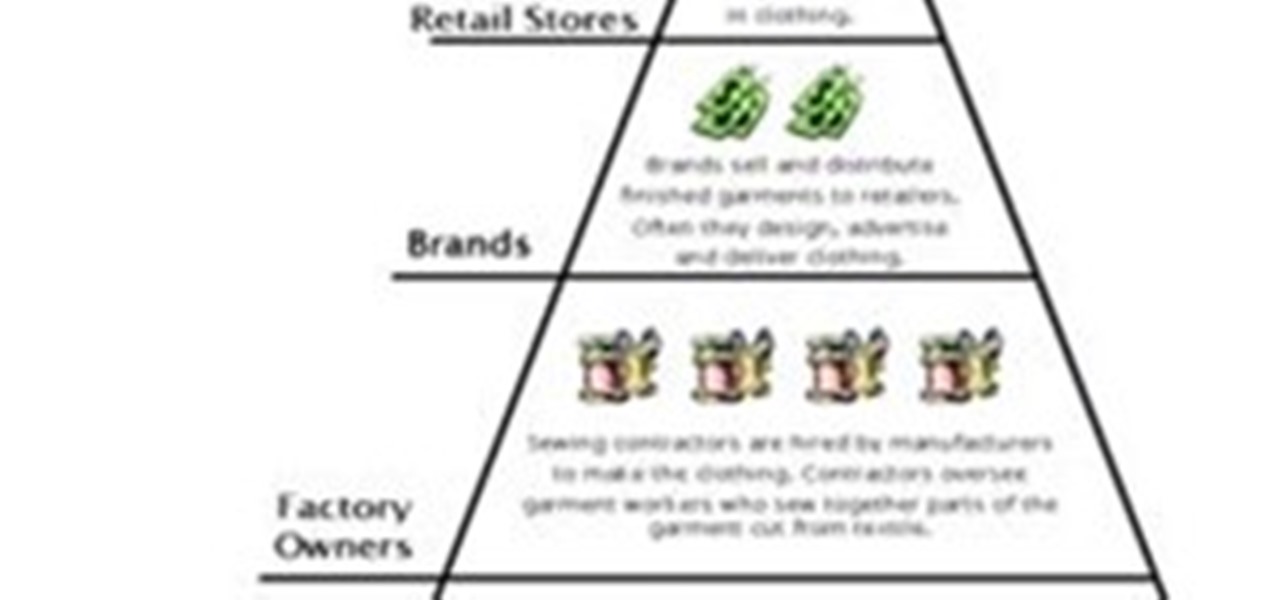
The United States is a hierarchical country where the weak ones are at the bottom and the powerful ones are at the top. Garment workers are at the bottom of the list although they are the most important. Without them there would be no fashion industry. They sew and cut the garments that people buy, the raiment that models wear on the runways. After the garments are sewn, factory owners send the garments to contractors to get make the clothing. Contractors make sure the garment workers sew the...