Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

Students have been passing notes in class for decades, so what's the big deal about sending a quick text message? Everybody does it, even your teacher was surely guilty of covertly communicating with his or her peers back when they were in high school.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

The right music can spur you to pick up the pace during an intense workout, pep you up before you hit the treadmill or walking path, and even encourage you to lift for just a few extra reps. Although we all have our favorite workout playlists, scientists have discovered what it is, exactly, that makes you workout harder when certain songs begin.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

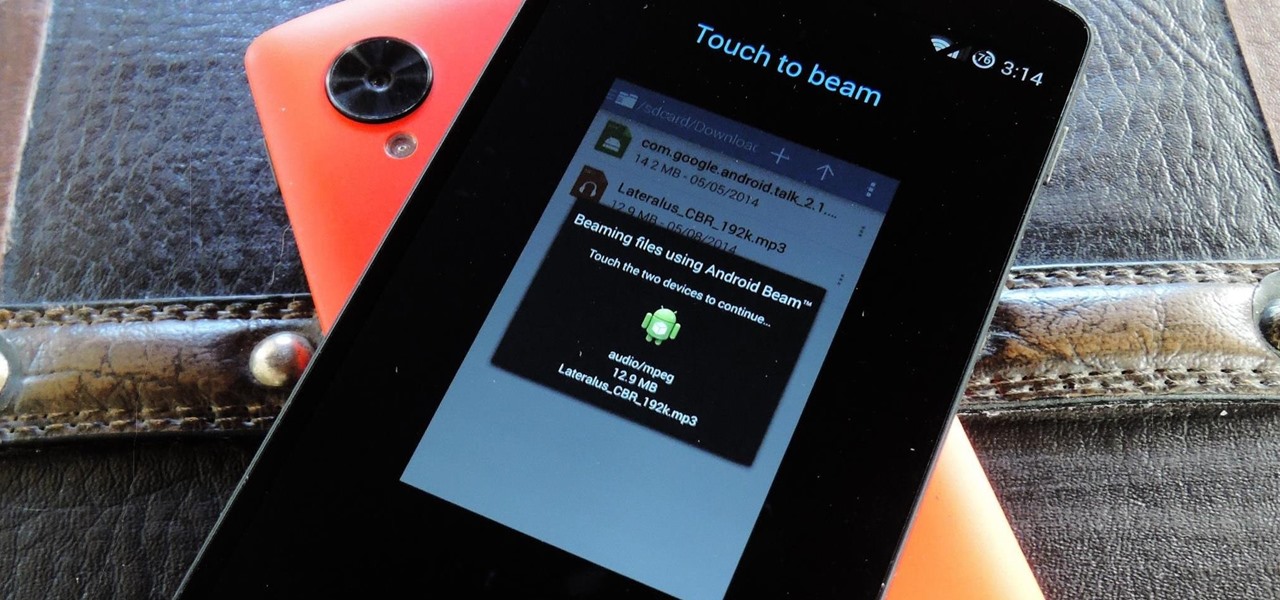
NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receiver, be it tap-and-pay with Google Wallet, a file transfer via Android Beam, or a Tasker profile triggered by a specific NFC tag.

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

Your Nexus 5 comes with a pretty cool feature baked in called Android Beam. Using NFC, or Near Field Communication, this functionality allows you to send information to another compatible device by simply touching the two together. Most flagship devices have NFC built into them these days, so there is a broad range of devices that your Nexus 5 is capable of sharing information with wirelessly.

There are much better things that can go in your iPhone's status bar besides an always-on indicator displaying what carrier you're shelling out money to every month. While it would be nice to get rid of the carrier name altogether at the top of the screen, an even better option is switching it out with something else to better personalize your iPhone.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet.

Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario

While it's not a highlight of the PlayStation 3, you can actually control the video game console with your smartphone. However, only certain aspects of the PS3 can be controlled from your iPhone, and it's not very obvious what you can and can't do — but that's where we come in.

Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time!

Mens jeans come in a ridiculously broad range of styles and sizes, from form-fitting to huge and baggy. Different body types look better in different types of jeans, and this video will teach you how to determine what types of jeans are best for you body type.

Everyone loves Scrabble, but not everyone knows how to play the game properly. Yes, there is a set up rules that come with each game, but who actually wants to read them? Isn't it better to learn from a more visual approach? This video will teach you the basics of gameplay.

This photoshop tutorial demonstrated by Howard from tutcast.com, teaches you how to do amazing glow effects for your work and projects. Everything you need to know from the background you choose to use to editing out the leftovers. You can use any image that you choose to. Start out with the pen tool located on the toolbar on the most left of the screen. Create the initial layer for the glow by clicking now on the new layer icon located on the bottom right. Next, define brush by pressing the ...

You're a committed environmentalist but you love your candles. What are you to do? Did you know that you can recycle your candles? There's bound to be stuff left over. Just watch this video and learn!

Identify the proper time to throw a knee kick. If you are grappling with an opponent, look for an opening where you can knee-kick him in the ribs or side of the thigh. If an opponent is trying to tackle you around the waist or take you down by grabbing your legs, introduce his face to your knee. If the opponent is standing in front of you and there is not enough room to throw a fully extended kick, grab him and try a knee.

This video shows how to fix an iPod which is stuck in a loop between battery warning to the apple logo. You will learn how to fix your iPod by watching this video. The procedure used in this video is to sync the iPod to the computer. Lock the iPod in disconnect mode so you can let it charge. You then wait for it to charge. You then tell I-tunes to restore the iPod to factory settings. If these steps don't work you need to replace the battery.

Is your waffle iron collecting dust? Plug it back in and use it like never before by whipping up a batch of brownies.

If your old clothes are of high quality and in good shape, selling them on consignment is an easy way to make cash quickly.

A good party guest should live by this motto: Ask not what the party can do for you, but what can you do for the party!

Check out this woodworking video from Eagle Lake Woodworking. Learn how to build a table saw crosscut and miter sled by watching this five-part series.

Increase your odds of meeting Mr. Right with these tips. Learn how to meet men if you are single. You Will Need

Watch this how to video and discover why induction cooktops are the hottest trend in the kitchen. These Home & Garden tips will help you decide on an induction stove that is right for you kitchen.

The Paslode Framing Gun is operated by a gas cartridge and battery so an air compressor is not needed. The tool also has a large range of nails available for different job requirements from 50mm To 75mm. Watch this video tutorial for a demonstration on how to use a Paslode impulse framing nail gun.

Do it yourself: extend your WIFI signal. This is a quick and easy way to get more range for pennies.

In this lesson we will learn how to solve probability problems involving a spinner. A probability measures the likelihood of a certain event. It always ranges between 0 and 1. The following formula can be used to find the probability of a particular event:

Learn how to perform this lateral crossover skip drill in order to maintain a full range of motion.

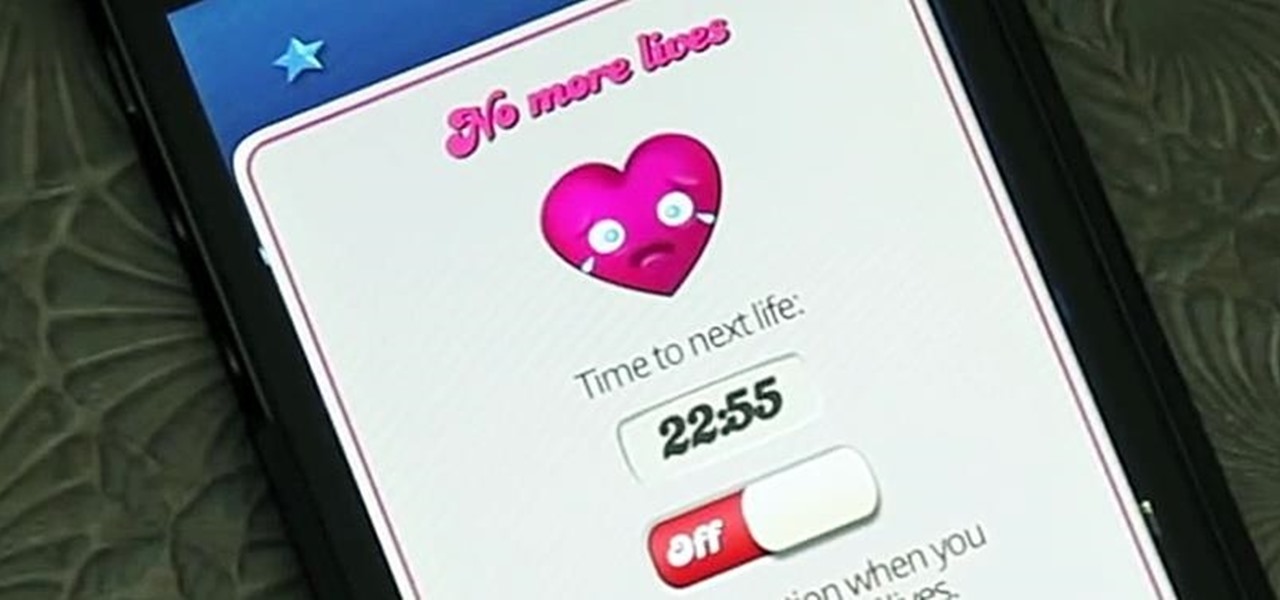
I hate waiting to play, and I hate bugging my Facebook friends even more. But that's what Candy Crush Saga makes you do if you want to get new lives and levels faster.

We've gathered some of our favorite pranks with the seasonally appropriate for all you college kids out there. You're more than likely cohabitating with a complete stranger, and what better way to make a good first impression and develop a strong personal relationship than subject them to a hilarious prank?

With the Kodak Zi8, the power to capture razor-sharp, full 1080p HD video fits in the palm of your hand. Its easy, one-touch operation and incredible versatility make it the perfect camera for beginners, experts, and everyone in between.

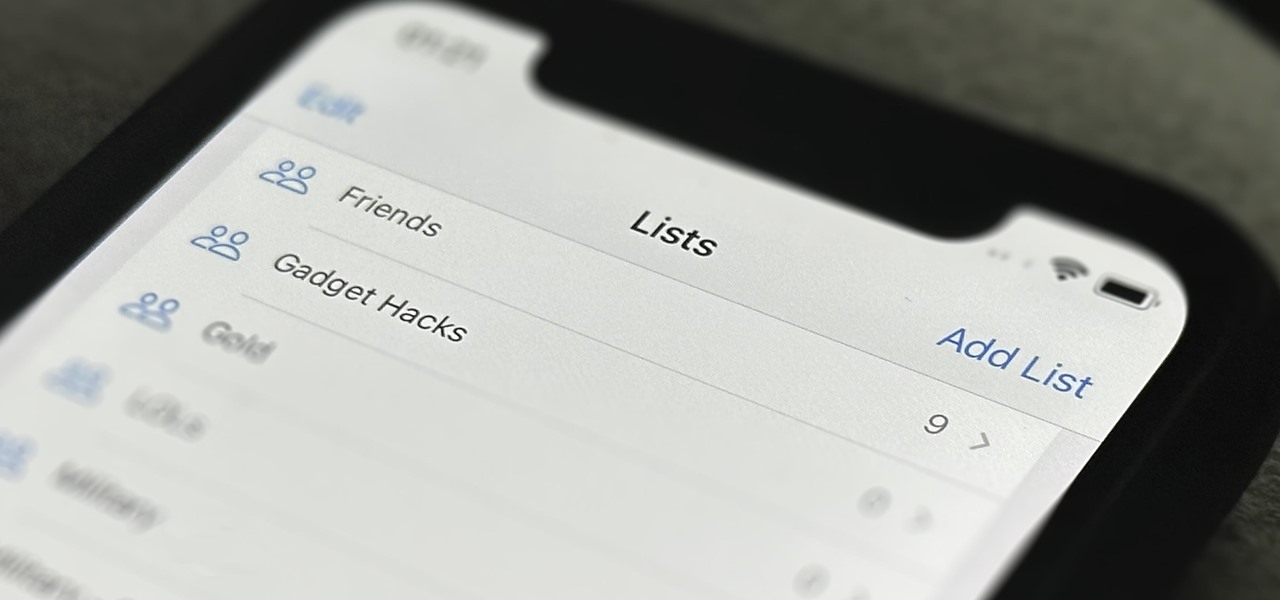
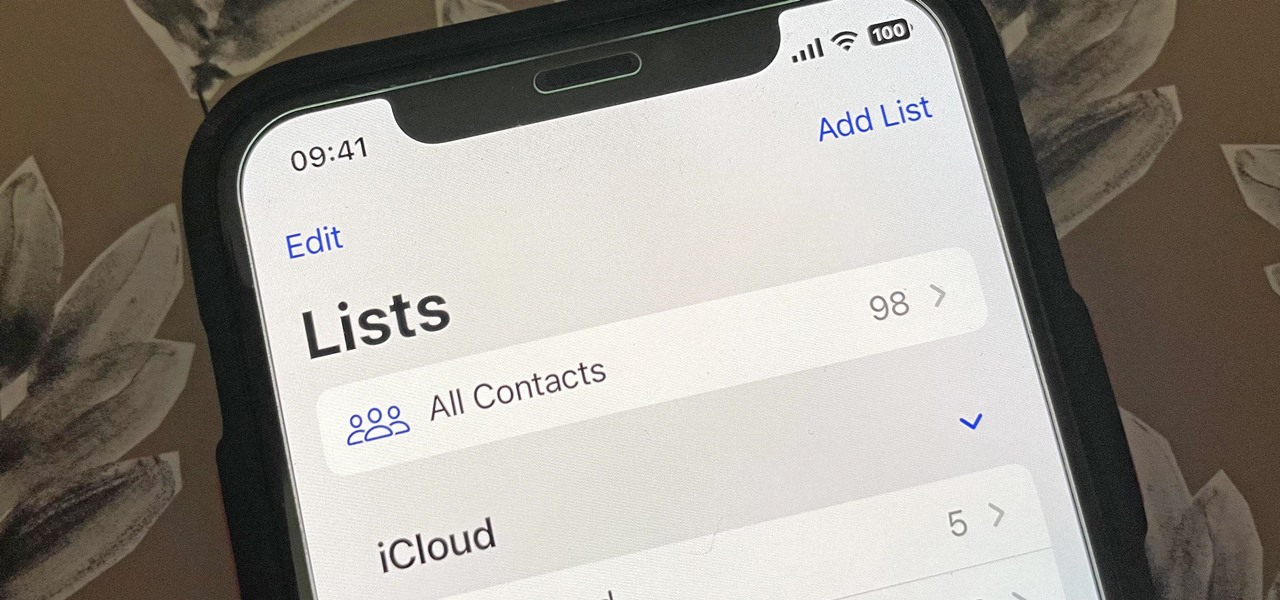
In the past, Apple never really put much work into its Contacts app for iPhone, making the tool much less useful than its Mac and iCloud counterparts. But now the Contacts app for iOS is a force to be reckoned with. Packed with new features (some hidden), it's finally good enough to beat all of the third-party contacts apps that previously reigned supreme.

Apple's Contacts app just got its biggest update ever. Since the first iPhone in 2008, there have only been minor upgrades here and there to how you manage and interact with contacts. That changes with iOS 16.