Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Previously, losing an AirTag or Find My network accessory meant relying on tech-savvy strangers to contact you via phone or email if they found it. With a new Find My update, you can ditch the passive approach and be more proactive about recovering your tracker by sharing its information with trusted contacts and even airlines, allowing them to track your tracker for you.

If you need to share something online but don't want your personal information attached to the file, use an anonymous file hosting site. By uploading files anonymously, you keep your IP address safe and won't need to create any kind of account that could provide further logging. You can do this in a web browser, but it's much easier to do using a shortcut on your iPhone.

You're in a Zoom meeting, and you're click-clacking away at your keyboard, typing important notes from the call. More realistically, you're doing something unrelated to the meeting, such as browsing the web, playing a game, or messaging friends. Whatever it is you're typing, if your microphone is on, everyone on the Zoom call will be able to hear the sound of you typing.

Google Maps tracks everywhere you go with your smartphone, even when you're not using the app. Even if it's as mundane as your weekly grocery trip, Google Maps has it saved for you to see in its Android and iOS apps. And while it's mostly used for recommendations and your reference — you may not want Google Maps to keep such a rich location history.

You don't need to take screenshots or make screen recordings to save photos and videos from other users on Instagram. While Instagram doesn't offer an official way to download others' posted content, dozens of shortcuts are available for iPhone that can do just that. But which one should you pick?

Apple just released the public GM (golden master) for iOS 13.6 today, Thursday, July 9. The update comes three hours after Apple released the 13.6 GM for developers, and the same day as the release of iOS 14 public beta 2.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

When you think about it, isn't life just one big open-world RPG just begging to be conquered? We all have a set number of specific tasks or chores we must complete every single day like clockwork. Sometimes, these items on our to-do list can become tedious and cause us to lose motivation. What if you could take those tasks and turn them into something awesome instead? Now you can.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

Apple's Wallet app lets you store boarding passes, concert tickets, gym memberships, vaccination cards, movie stubs, rewards cards, insurance info, student IDs, and more in one place on your iPhone, and you just double-click the Home or Side button to access them. Unfortunately, many cards and passes are not officially supported — but that doesn't mean you can't add them.

Since iOS 13, your iPhone's come equipped with a fonts manager that lets you install custom fonts for use in Apple apps and supported third-party apps. To add fonts, you need to use a font provider app that'll load them on your device and register them system-wide, and one of these apps shines above all else.

Your iPhone keeps track of every single place you go, especially those you frequent most often, and syncs those locations across all your iCloud-connected devices. People who gain access or already have access to your iPhone, iPad, iPod touch, or Mac may be able to view all of these locations to see where you've been and where you might be. If this worries you, there are things you can do.

Every year, Apple adds some old technology to the iPhone and gives it a catchy marketing name, then like clockwork, it becomes the next big thing. Google, on the other hand, creates some truly innovative features, doesn't really bother naming them, then lets them languish in obscurity until Apple reinvents them at a later date.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

With iOS 17 on your iPhone, you have access to new health- and fitness-related features that can help you improve your mental well-being, reach your fitness goals, take your medication on time, avoid eye strain, and more.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

Samsung has a cool security feature built into One UI that has an interesting side effect, one that lets you have two separate copies of any Android app on your Galaxy phone. And that's not the only integrated Samsung tool for cloning apps.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

You may use Safari on your iPhone or iPad to open links and browse the web, but there's so much more it can do for you. On updated software, you can implement third-party Safari extensions in your browser that go above and beyond content blocking, sharing, and performing basic actions.

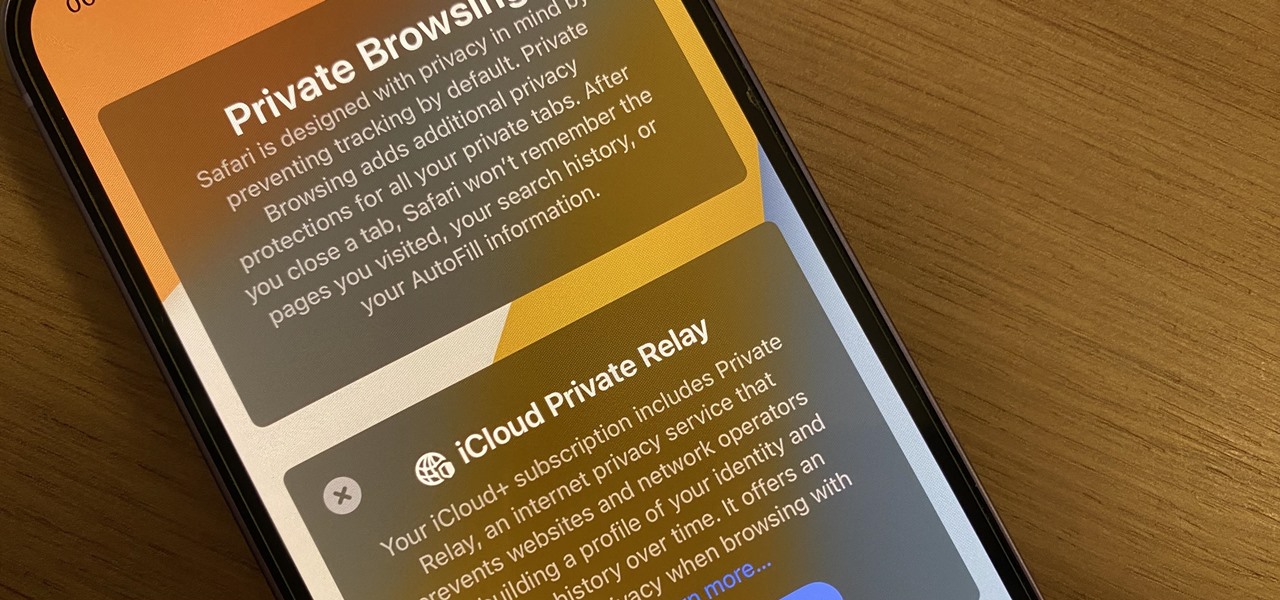
In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

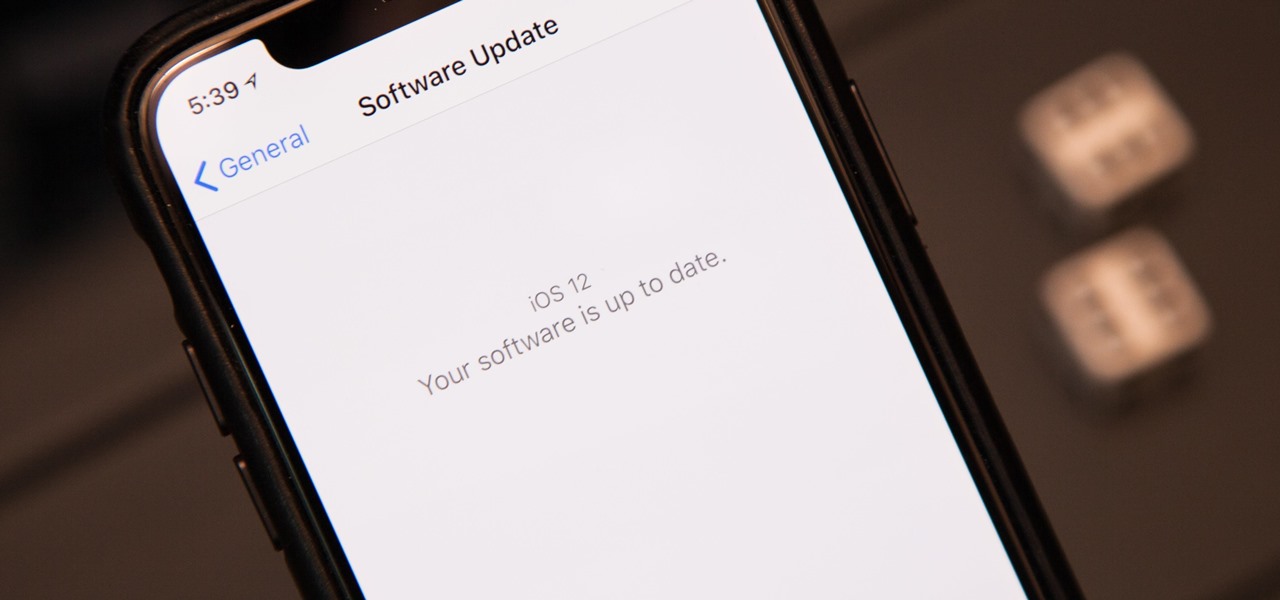
The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

With all the time most of us spend on our phones each day, wouldn't it be great if we could get rewarded for our addiction? Well, we can, thanks to various iPhone apps out there that can help us make a quick buck, earn cash back, donate freebies to charity, get complimentary cryptocurrency or stock, and receive other types of rewards.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

This fast tutorial will show viewers the basics of how to use Facebook for those who are new to using the website. After creating an account and logging into Facebook, you will see your homepage, which has most of the new information regarding your friends and their recent activity. Clicking on the links at the top of the page will allow you to access pages such as your own profile, where you can display information about yourself, such as where you work or your date of birth. After watching ...

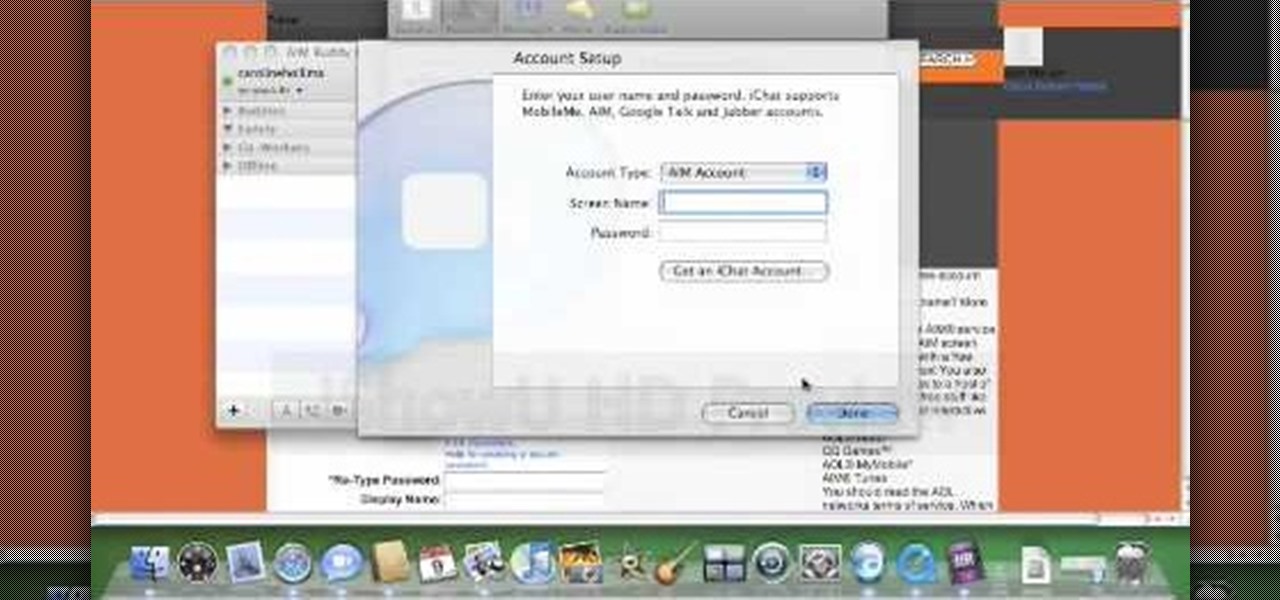
In this video, viewers are shown how to use the iChat feature on a Mac computer. To begin, the video creator instructs us to open Safari (or your preferred) browser and to navigate to www.aim.com. This is the AOL Instant Messenger site (AIM) and from here, you are able to create a screen name. This is important because you have to have a screen name with a instant messaging service to be able to chat using the iChat application.