As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

I remember a time when I had to rent a VHS from the local video rental store. It wasn't all that bad, with the only real annoyances being the trip to and fro, having to rewind the movie and the possible malfunction of my VHS player, which liked to eat tape from time to time.

It's that time of year again when pizza boxes line the room and buffalo wings stain the couch. When cases of beer sit in the cooler and the big screen TVs are fired up and properly calibrated. When two of the best football teams vie for the championship title and the Vince Lombardi trophy.

So many of you like to save up your gold coins to buy things like castles, treasure cards and clothing. But sometimes when you buy something, an error message pops up. One of them is this extremely annoying one: "Transaction was not successful."This error happens mostly when buying clothes. Let's say you want to buy a robe, but it is too expensive. You change the color of the robe to brown, yellow or white and try to buy it. When you click Buy, the error pops up. You switch realms. No differe...

In this video tutorial, viewers learn how to make their information more private on My-Space. Users will need to begin by logging into their account. On your homepage, click in Account Settings and click on the Privacy tab. Under General Privacy, users are able control who sees their online status, birthday and photos. To only allow friends to view your profile, select "my friends only" from Profile Viewable by. Users are also able to block other users by age and to block specific users from ...

I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned how stalkers work.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

But it seems like all of the major social networks are determined to send you one anyway: Pinterest:

Announcement #1:Felix Navidad is back fr another great December season! Come join him to celebrate another yuletide here in Wizard City. To buy items from him, go to the Shopping District near the fountain, where all the season sellers sell their merchandise. Just note these items cost crowns!

When I tried to send a free gift back to my friend, I got this popup I clicked skip the first time, and it came up twice more. So I logged in, it imported my contacts...

I can't say it's absolutely true, but when it comes to mobile word gaming, there's Scrabble people and then there's Words with Friends people. It feels segregational. Rarely does one play both. At least, that's what I see when it comes to my family and friends.

The purpose of this article is to discuss how you can change your Windows 7 logon screen. This post will explain how to require a user to enter a username and password by default like the classic version of Windows.

WANIGAN 61 points (11 points without the bingo) Definition: a supply chest used in a logging camp [n]

You're in a new city and you want to explore—what mobile app is best? If you want to know what club is hopping that night, use SceneTap. If you want to know if any friends are at a nearby get-together, use Foursquare. If you want to know what restaurant is best, try Yelp. But if you're looking to get a real feel for the city, skip the more touristy destinations and take to the streets—discover where some great graffiti is located or where the best view of the city is with the Trover iPhone ap...

Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia:

Do you have AMNESIA? How about SYPHILIS? Or have you gotten SODOMIZED? Well, the people pictured below do, and I don't feel sorry for them, not at all——those words would kill on the SCRABBLE board!

Tuesday update June 8th. Upon logging in you see this:

Hey Everyone! Welcome to my post. We have seen a numerous GUI Tool in kali linux. Armitage, wireshark, Burpsuite etc,. Lets see an another GUI tool.

This is a working solution for those using an external monitor on their MacBook Pro's running Yosemite. The previous terminal commands for Mavericks no longer works on Yosemite, so this how to do it.

Google is great. They provide us with tons of free services and open source APIs that we can code fun tools for, one of which I don't think gets enough credit: Google Voice.

The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor.

Check out MY quick intro and some tips for the Crafting building then watch my video for more in depth, live action information! This post is NOT copied from the Zynga boards, so it's unlike any you have seen yet!

I recently posted a link to what seemed to be a very useful guide on Lifehacker for creating a TOR button in Chrome. However, when I tried it myself, it did not work. Also, it lacked a warning on the limits of Tor, which I think are important. Therefore, I decided to create an updated and more comprehensive tutorial.

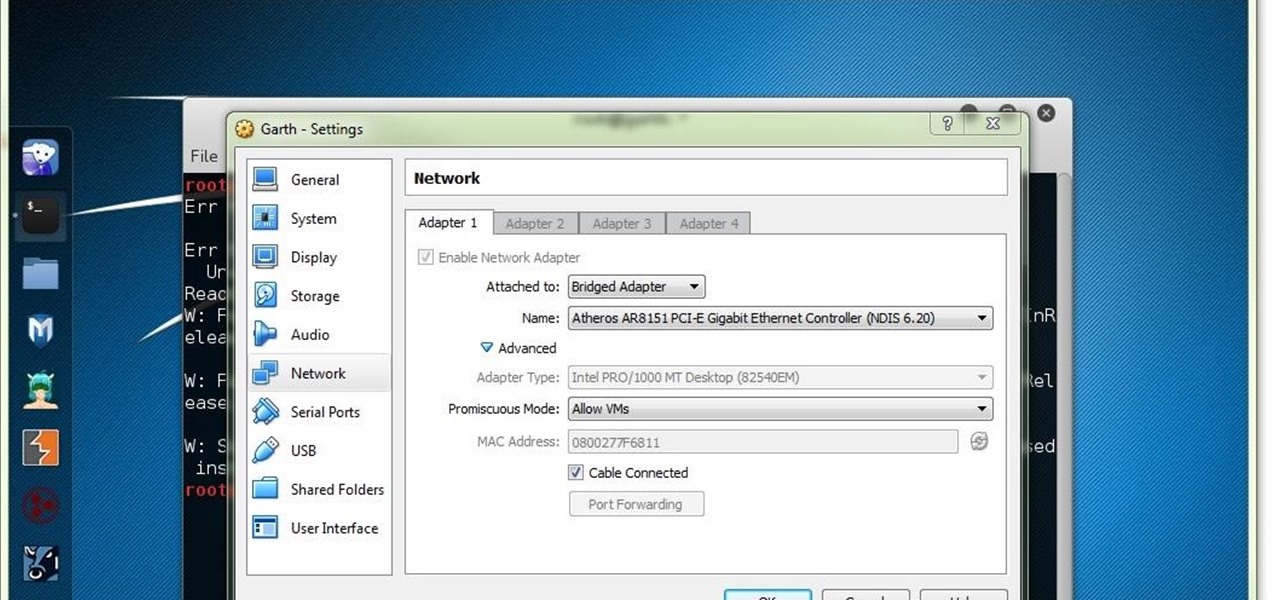
Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

It's live! Google has finally unveiled the much-hyped makeover of their Gmail email service. As of yesterday, anyone who wants to update to the new Gmail look can, but in the coming days it will be forcefully pushed to Gmail users everywhere. If you enjoyed the look of the old Gmail, you've only got a few more days to bask in the design before it becomes a mere memory.

Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

If you own an Android device and a Windows computer, there is absolutely no reason you shouldn't have Pushbullet installed. With the Android app and a companion Chrome plugin, you can easily send files between all of your supported devices, and there's even a notification mirroring function so that you never miss an important update.

We all know the dangers of logging on to our personal accounts on public networks, but we pretty much all do it anyway—especially when it comes to Facebook. But the next time you're in a public place and can't wait to check out your Facebook news feed, use this simple trick to make sure that no one gets a hold of your password. In order for this to work, your mobile phone needs to be linked to your Facebook account. All you have to do is text "otp" (for one time password) to the number 32665.

Hello everyone and welcome to Part II - The Ultimate Guide: Diagnosing & Fixing Connection Issues. In this tutorial we will discuss more advanced methods that I took in order to fix our home network. I have also attached a link to download the FREE eBook - so feel free to download it to you can refer to this manual when you are experiencing connection issues. I would also like to note that the manual has been loaded onto a free server - it will remain on the server until people stop downloadi...

Facebook's new Timeline feature has been rolling out gradually since its unveiling in September, but yesterday it finally became available to Facebookers everywhere. It's even available on your mobile device, too. Those who want to upgrade to the radical new profile design can do so by simple logging into their Facebook account and visiting the About Timeline page on Facebook.

The dreaded moment you hope never happens—someone has stolen your laptop. You could have private information, pictures, or even private information belonging to the company you work for, all lost forever. It can cause you pain, money, or even a job.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

Okay, stop me if you've heard this one. You have a document that you want your co-workers' advice on. You attach said document onto a mass email. The first reply comes back with an edited version of the document. You begin to make changes, but another email comes in, with yet another edited version. Soon you're drowning in a desktop folder full of mismatched documents, all with the same name.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

I'm not sure exactly when it happened, but it's awesome that you can now download music from the iTunes Store that's free of DRM (digital rights management) limitations. That was always my biggest problem with buying music from iTunes. Paying a buck for a song that I can only play on Apple devices? Really? That's what finally led me away to other legal music downloading services like eMusic and Amazon.