EVENT: A Night of Music and Poetry with Street Poets
STREET POETS INC INVITES YOU TO AN EVENING OF SACRED MUSIC & ILLUMINATING POETRY:

STREET POETS INC INVITES YOU TO AN EVENING OF SACRED MUSIC & ILLUMINATING POETRY:

Do you write left-handed or throw a dart left-handed but play golf right-handed? If you answered yes, then the chances are you may be trapped trying to make the wrong golf swing. The more logical, natural swing for you is left-handed. Coach to lefties, Jeremy Dale, shows you how to make the change by reversing your swing. Switch to left-handed golf.

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.

My mind is playing tricks on me! Discover Magazine systematically dissects five fantastic optical illusions. The scientific explanations are logical:

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

We're a sucker for the cute ones. This mini-magician might not have much up his sleeve as far as slight of hand, but he's got energy.

Lucy once ranted to Ricky, "How can I look up a word in the dictionary if I don't know how to spell it?" A very logical conundrum that exists in the world of video search as well.

Introduction In this post we will look at how to access a PosgreSQL database in your C/C++ application. It's not as hard as you might think, but you need to understand the procedure and the functions used.
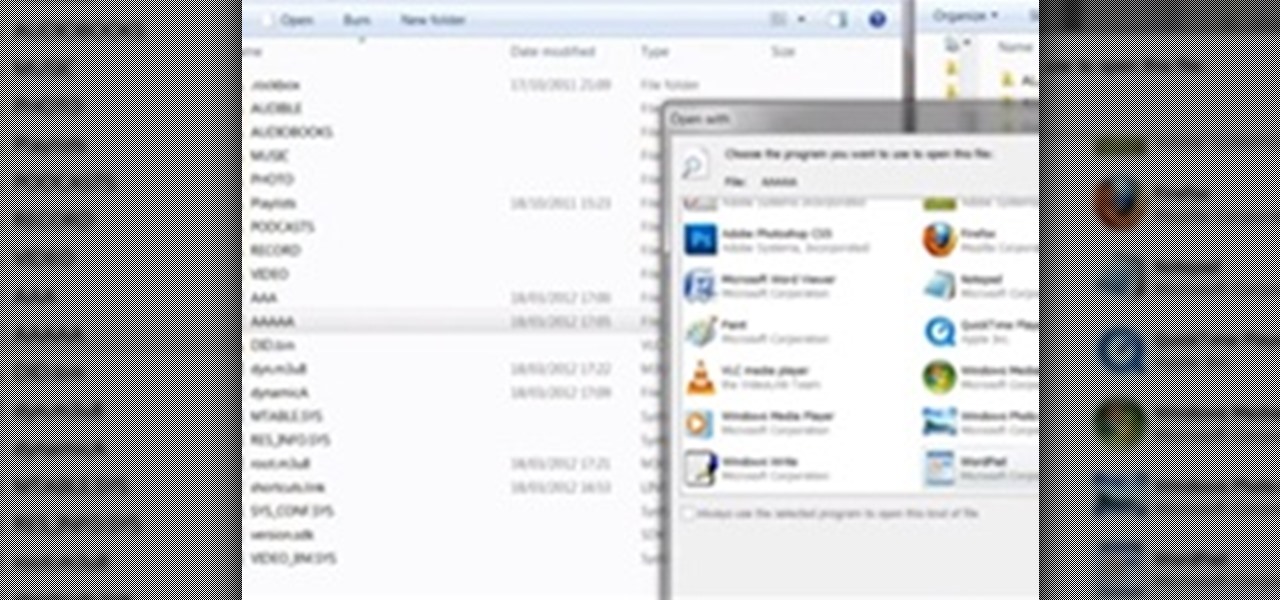
A playlist is simply a list of songs which can be played in sequential or shuffled/random order. Many people tailor-make playlists to suit a particular style of music or atmosphere, so being able to share these between people is great.

There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer security, networking, software development, testing, and so on...It's probably a bit premature to decide what you want your speciality to be, but keeping the question in the back of your mind will help give you direction in ...

Note: Little Brother is available as a free ebook download. Warnings

Google has produced millions of low-end Cardboard VR headsets, but now it's upping its game with virtual reality phone packaging. Yep, you heard that right. A patent application published in February would suggest that the tech giant has developed phone packaging that doubles as a VR headset.

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

Many folks seem to treat their computers as a sort of mysterious alien technology that only the shamans of the IT Department can comprehend. You might have gotten it into your head that you're just not good at computers and will never understand them. On the contrary, getting a basic grasp on all the amazing stuff inside your computer doesn't require you to be a technological genius. Most people will never have a need or desire to open up their computer and poke around. But it's your machine....

I've been curious to watch one of these famed '3D' games for a while now. Last April at NAB, I attended several 3D panels and folks from ESPN suggested that one of the strongest experiences that would bring 3D into the home would be live sports. I've missed opportunities to watch the PGA Masters broacasts, and NCAA games, but being a hardcore Soccer (Futbol) fan, I've been most excited about this possibility. It did not disappoint, but not without some concessions. I will be as detailed as po...

Duhhhh. How to disguise that Spitzer face. Hell. Spitzer used an alias of a hedge fund buddy George Fox. Eliot should have gone one logical step further. Make a compelling disguise.

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.
(This is a manifesto I wrote 2 years ago. I have never published it. It was a reaction to the ignorance I faced in graduate school from the modernist sculpture

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.
Sergio Peralta Advisor: Jessica Davis

I've been dealing with emotional difficulty for many years. It started when I had surgery for the epilepsy I was dealing, and quite literally, dying with. Since the surgery on March 28, 1990 I have had no seizures, but I have had plenty of emotional difficulty. Along with that, surviving some traumatic events has added some emotional baggage...in other words struggling...along the way.

I'll give you some hints... 1. Women have less than men.