If you have an iPhone or iPad, but use a Google account for most of your communication, syncing your contacts just got a lot easier. Google recently announced that they added CardDAV support, an open protocol that lets you seamlessly integrate Google Contacts into other services. Google states that "Syncing via CardDAV is only available over SSL for Apple devices on iOS version 5.0 and above." So, if you're running an older iOS version, you'll have to use Google Sync instead.

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.
The Internet has had a huge influence on many areas of our lives, but, in particular, has resulted in nothing short of a revolution in the way we work. The web has offered the sort of flexibility to the individual that few people would have dreamed of just a couple of decades ago. And where once a global marketplace was available only to a handful of multinational corporations, today thanks to the Internet, we can all access it.

Do you want to change the login wallpaper on your Mac OS X? It is as simple as replacing an image in the file system.

Too many people just drive their cars for a few years and then replace them. When treated right, cars can keep on running for decades. You may not be able to keep your car running forever, but you can definitely extend its life.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

It's March once again, and while that might signify the beginning of spring for some, basketball fans have this month marked on their calendars for one good reason: NCAA March Madness. Though the tournament is already underway, the Sweet Sixteen leg begins Thursday, March 23, 2017. If you fear you may miss the upcoming games, worry not, as free apps for smartphones and tablets are available to help you watch all the action.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

GetYourSkinBack discusses the various causes of black circles under the eyes and how to get rid of them. Skin discoloration under the eyes affects almost everyone at one time or another. It can add many years to your appearance, so getting rid of it is extremely important. The main causes are heredity, stress and fatigue, age, allergies, and medical conditions.

Watch to learn how to replace the HEPA filter on a Dyson DC04 upright cleaner. You'll remove and replace the Pre Motor Filter and the Post Motor HEPA Filter on a Dyson DC04 vacuum cleaner. It is important to change the filter regularly as part of regular vacuum maintenance and to prevent loss of suction.

For top performance, clean your musical wind instruments regularly. Learn how to clean wind instruments, from woodwinds to brass, in this free video.

A side effect of the COVID-19 pandemic is that small businesses are suffering from forced closures and social distancing, but game developer Niantic has a solution.

Google's G Suite collection of premium cloud services and apps have become popular with business customers, with more than six million subscribers now.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Friends and family receiving new Portal devices for Christmas will have some extra stocking stuffers in the form of new AR features.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

To make its services more accessible to regions with limited bandwidth, Spotify has rolled out with a leaner, stripped down version of its music streaming app. The aptly named Spotify Lite has been released for Android devices in 36 countries in Africa, Asia, and Latin America, but you can try out the app right now thanks to a simple workaround.

Talking Tom has long been mesmerizing children of all ages with his ability to repeat words and phrases and encourage touch interactions. Now, the lovable cat and his band of cuddly friends have ventured into the endless runner genre as heroes bent on saving Angela and their city from a band of mischievous raccoons.

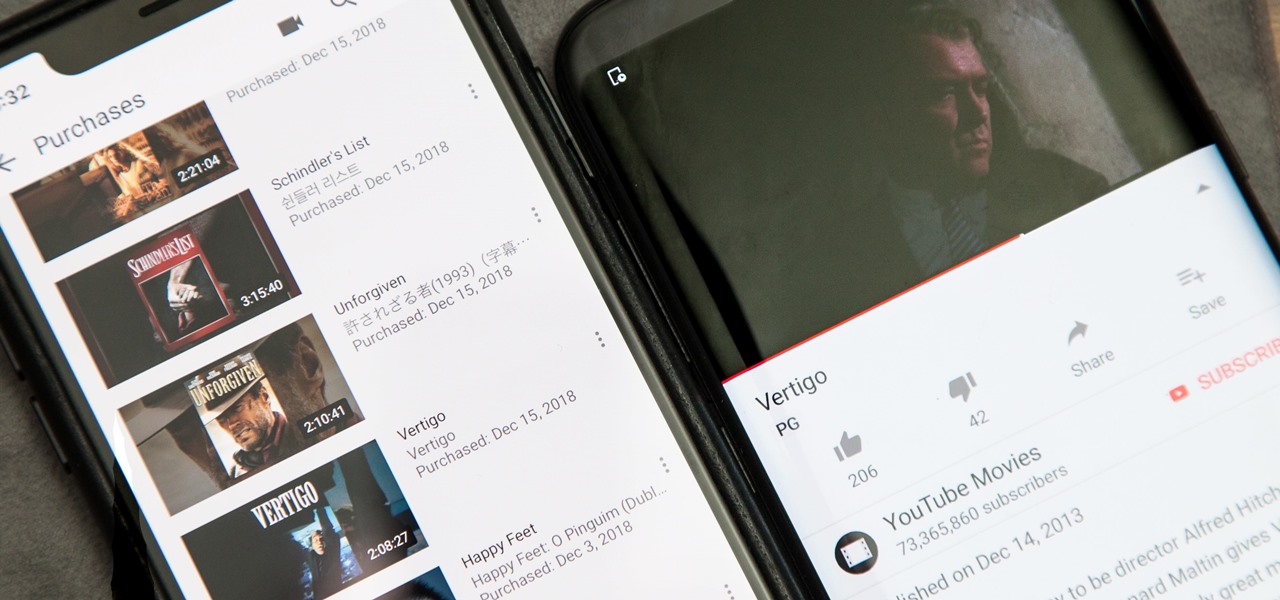
Owning digital movies has many advantages over physical discs, such as easy access and a variety of online stores you can turn to for good deals. There's Prime Video, iTunes, Vudu, and the list goes on. However, this leads to fragmented video libraries, unlike DVDs and Blu-rays which can be stored together. Surprisingly, YouTube is one app that can help consolidate your collection online.

In an ongoing effort to improve its services and become more accessible to users from all regions, Facebook has released a streamlined version of its social media app. Though the leaner Facebook Lite is only officially available in Turkey for now, there's a simple workaround you can use to get the app in any country.

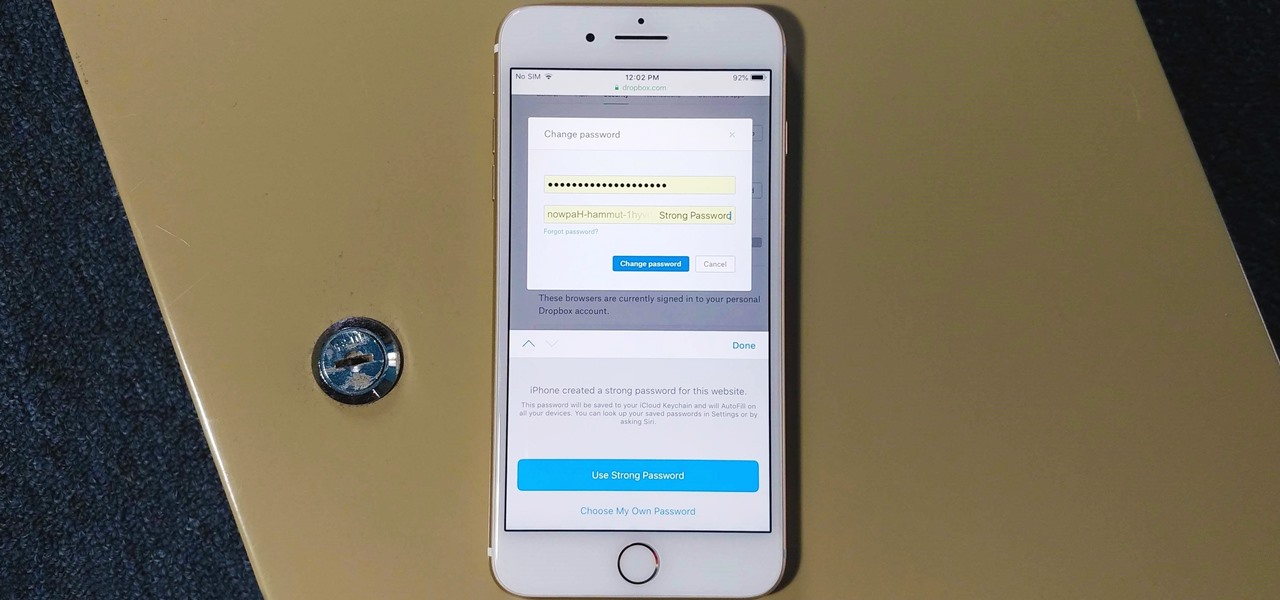
With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.

The option to auto-fill passwords on your iPhone has been around a while now, but iOS 12 improves on it by suggesting strong passwords when first creating an account online in Safari or within apps. Apple has also added "password reuse auditing" for your iCloud Keychain, where all your logins are housed, which will find and change your weak passwords to strong ones.

Augmented reality experiences created in Lens Studio now have a permanent home in the Snapchat app. On Tuesday, Lens Explorer will begin giving users access to a scrollable screen full of a variety of new Lens Studio creations.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

After two dramatic Conference Finals, the dust has settled to reveal ... the Golden State Warriors and the Cleveland Cavaliers. Well, at least the Irving-less Celtics and Rockets (short of Chris Paul for Games 6 and 7) gave it their all. With these teams battling for the fourth straight time, people want to know if the Cavs can even up the score at 2-2.

Despite the abundance of sci-fi titles in the iOS App Store, very few of these mobile games ever have the staying power keep us glued for more than a few hours. Enter Space Pioneer, an awesome space exploration game that soft-launched in Canada ahead of a worldwide debut. With a little spoofing, you can experience the game yourself right now.

Taking a cue from the smash hit Super Mario Maker, Bandai Namco has soft launched PAC-MAN Maker in Canada ahead of a worldwide release. This is welcome news for mobile gamers, as you won't need a console to enjoy this classic arcade game when it finally touches down stateside. But if you want to give PAC-MAN Maker a shot right now, we've got you covered.

With tons of titles to choose from on the iOS App Store, you'll never be lacking when it comes zombie shooters. Unfortunately, the same can't be said if you're more interested in base-building and defending against the undead. PlayStack aims to change this, and they've soft-launched Survival City in the Philippines for further development. With a simple hack, you can try the game yourself right now.

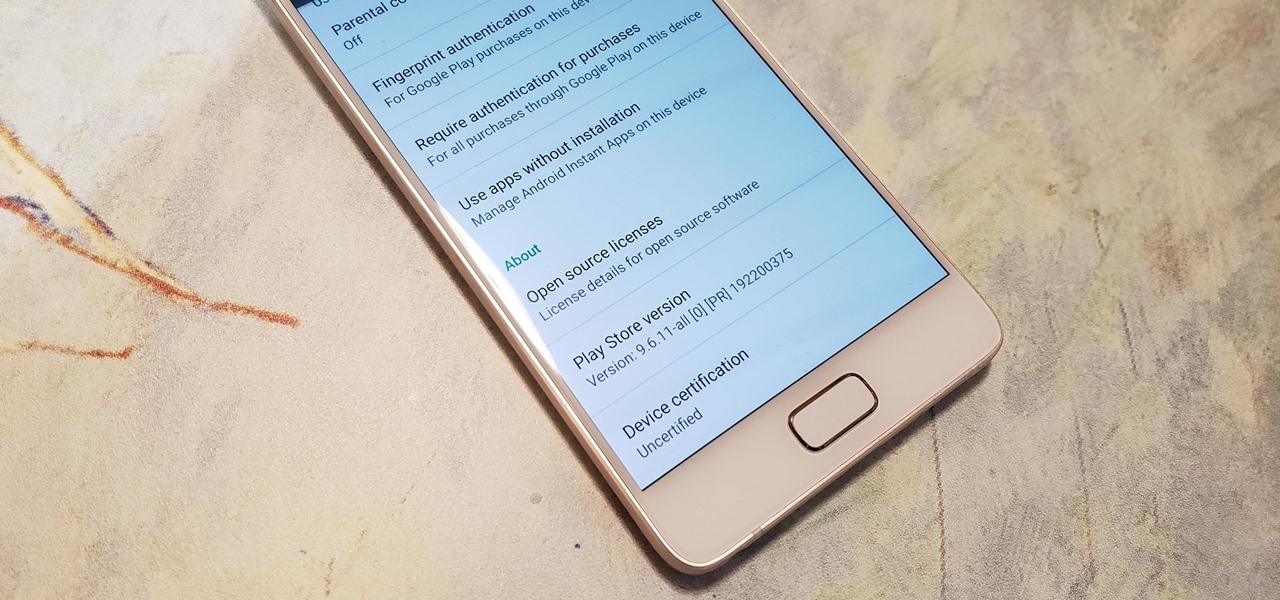
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

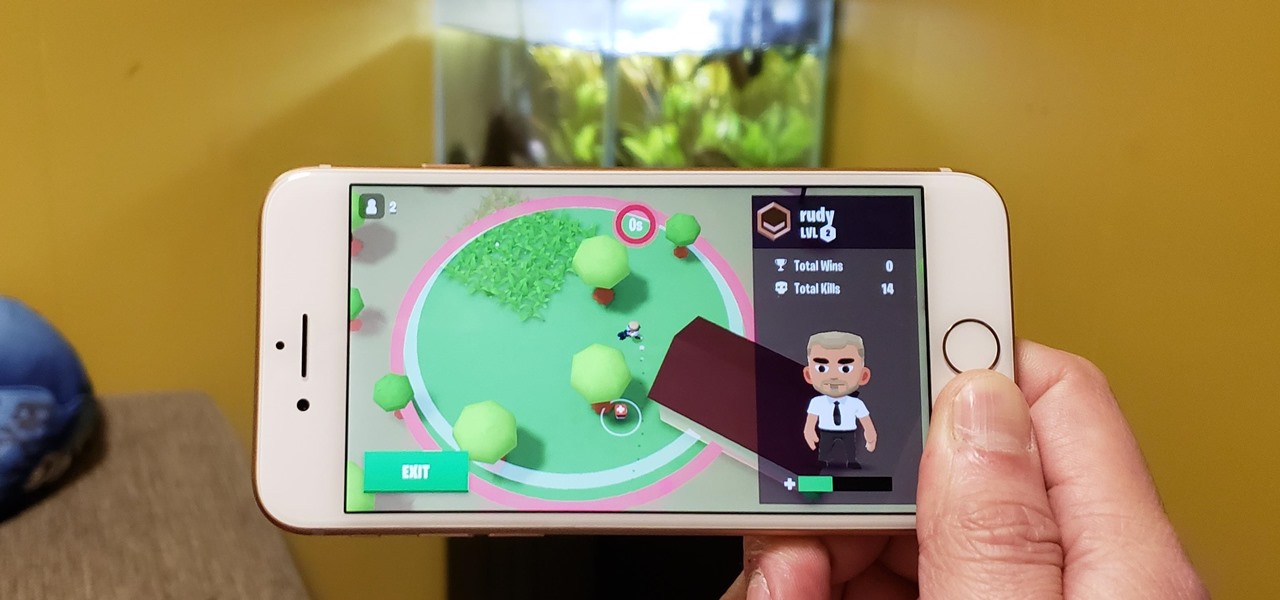
With PUBG and Fortnite dominating the gaming scene, other companies are making royale-themed games to get in on the trend. Futureplay is no different, as they've soft launched Battlelands Royale in Finland, Poland and Ukraine to iron out bugs before its worldwide debut. If you don't live in one of those countries, you can try this game right now with a quick workaround.