In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a friend pointed out to me, Ubuntu is currently the only distro implementing SHA-2 as the default. With SHA-2, your passwords take an unreasonably larger amount of time to calculate. This will greatly decrease how many password...

Getting your own blog is easier than what you can imagine. Thanks to WordPress. One need not be a techie to follow the steps mentioned below (though certain stages might require third-party advice).
Hello fellow Null-Byters today I will be showing you how to change from the simple but powerful BASH system to a more powerful and faster Z - Shell system. This change can be permanent if you want but doesn't have to be, and it is an extremely simple one to perform.

Remember last month when we introduced you to Trover? Well, now this great little discovery app for iPhone has completed its beta mode and has officially launched in wide release.
I assume you are on the same network with your router 1 - open a terminal window
Welcome, The Geeks!! This is my first article on email spoofing and hope everyone likes it.

WonderHowTo is a great place to find advice and learn things that you want to know, but can't find anywhere else. On this website, there are tons of people who make articles and videos to show you how to do stuff. In this tutorial, you will learn how to make your own WonderHowTo account and join this amazing place.

This tutorial shows us how to change the default password on a d-link router. First, go to your web browser and type in "http://192.168.0.1". A pop up box will now appear, in the user name section write "admin" and in the password section, leave it blank. On the new page, click on the "tools" section, then type in a new login name under the administrator section. After this, enter a new password and confirm it. Now delete all the information under the "user" section. Save these settings, clic...

In this video tutorial, viewers learn how to change the default password on a NET-GEAR router. Begin by opening your web browser and go to this site: Router Login. When the Prompt window opens, type in your router's user name and password, and click OK. In the sidebar, under Maintenance, click on Set Password. Now type in the old password, new password and re-type the new password once again to confirm. Finish by clicking Apply. This video will benefit those viewers who use a NET-Gear router,...

In this video tutorial, viewers learn how to disable SSID broadcast on a NETGEAR router. Begin by opening your browser and go to the site: Router Login. Then type in your user name and password. Click OK. In the sidebar under Setup, click on Wireless Settings. In Name (SSID), type in a new network name and click on Apply. In the sidebar under the Advanced, click on Wireless Settings. Type in your user name and password once again, and click OK. Under Wireless Router Settings, uncheck Enable S...

In this video tutorial, viewers learn how to set and encrypt a NET-Gear router with WEP password protection. Begin by opening your web browser and go to the router website: Router Login.. When the Prompt window appears, type in your router user name and password, and click OK. In the sidebar, under Setup, click on Wireless Settings. Once again, type in your user name and password, and click OK. In the Security Options, check WEP (Wired Equivalent Privacy). Then select the Pass-phrase box, typ...

Composting is said to be every gardener’s gold, but making compost and getting it ready could take up to a year. Professional growers have discovered that compost activators can help speed up composting quickly…sometimes to as little as 30 days!

Papaya trees are very vulnerable to transplantation shock. Seedlings tend to recover slowly and poorly after replanting in a new location under a sunny sky. Many internet articles advise that papaya trees should be transplanted without injury to their root systems. Keeping the root systems intact is next to impossible if the papaya seedlings are too close to each other. However, you would be surprised to learn how a papaya tree with serverely broken root systems can survive a transplantation ...
Just a quick post. Xorg is the graphical server that handles the desktop environment you choose for your Linux box. A pretty big flaw was found in Xorg versions 1.11 and later that allows anyone to bypass the screen lock mechanism on xscreensaver, gscreensaver, and many others.

Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will make the effort to learn even when I am not present. So, a tip of my hat to Mr. Sol Gates and the rest of you fine people.

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.
Social networks play an important role in the life of a blogger, they can deliver, what he writes about what he publishes ... Here are the steps to bind a Twitter account to their Facebook account.

These days I found a very beautifull python script that just prints the google chrome usernames and passwords that are stored on your machine.

Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group website.

Welcome to another Community Byte announcement! In the past two sessions, we have coded an IRC bot in Python capable of issuing commands. Since it can issue commands and most of you are new to programming, that project will stay idle for a while. Other commands such as voice and half-op can be easily hacked in via common sense, even if you weren't there for that session.

These days, I keep multiple browsers open so I can keep track of all my work and personal items. As a staff member of WonderHowTo, a lot of my work is done through our Google Account, which is separate from my personal Google Account.

Before you begin to make your skillet grilled chicken fajitas, place a skillet in your oven at about 350 degrees. You will also need flour tortillas. Heat up another pan and drizzle some olive oil into the pan. Slice up an onion and place in pan to brown. Add a pinch of sugar and a sprinkling of red wine vinegar to bring out the sweetness in the onions. Make sure you stir regularly so the onions don't burn. Choose either a red, yellow, or green pepper and wash it. Cut out the stem/top, pull o...

Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to hack into accounts, but rather to protect you from using weak passwords).

Wade Bourne of MyOutdoorTV.com shows you how important it is to take care of leather hiking boots. Leather boots are expensive, and they should be treated like an investment. This means giving them proper care to extend their life and receive the greatest use and value for your dollars spent. Here are tips on how to care for leather boots to extend their useful service.

Scientific studies have shown that species with large swimbladders, especially bottom dwelling fish such as grouper and snapper, derive an immediate benefit from venting.

Front crawl is the fastest stroke and gives you the feeling of being powerful in the water. It is often hard to get the hang of at first because fitting in the breathing can be difficult. Follow along in this swimming how-to video to learn the basics of the front crawl.

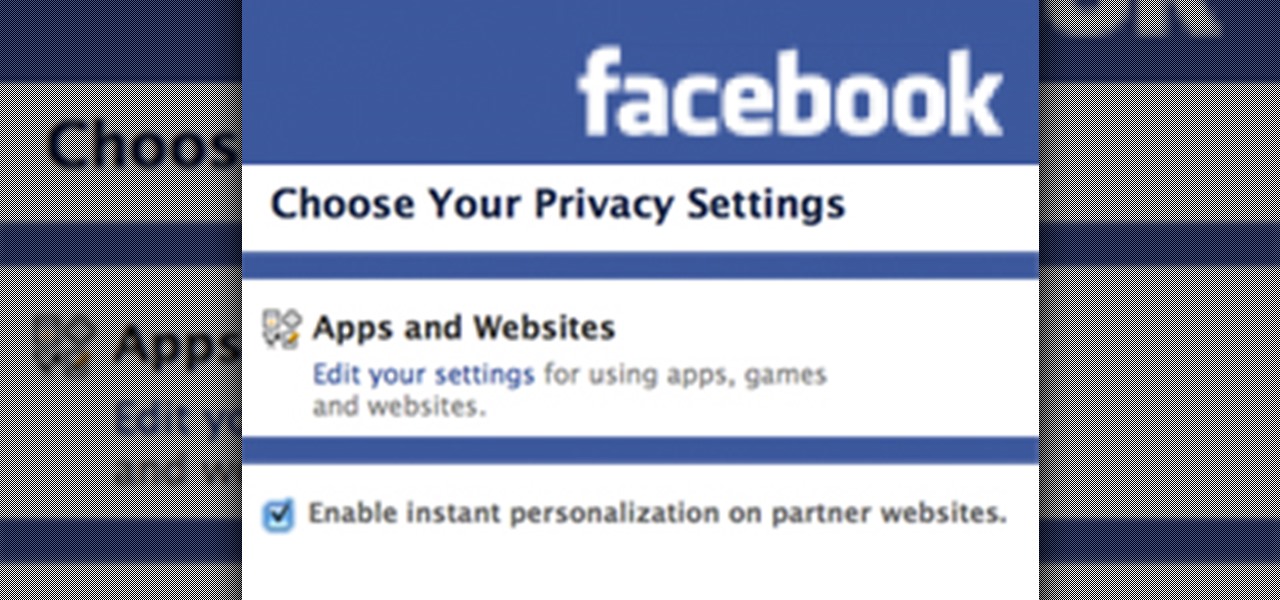
Instant Personalization. If you have a Facebook account, you've probably heard of it by now. If not, you need to educate yourself— and fast. Because they recently made some changes, affecting your privacy settings.

Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide below, we'll show you how to secure your wireless connection in three easy steps.

If you have made the switch from Windows to Linux, I want to congratulate you in advance. I'm sure you have noticed a huge performance increase when using Linux over other operating systems. This is only half the battle, though! Most users who are new to Linux end up using Ubuntu. I have no gripes with Ubuntu, but I do not agree with their philosophy. It almost mimics Windows. Ubuntu favors ease of use, and despite valiant efforts by the development team thus far (Ubuntu is crazy fast), all o...

How to change the login password on Windows XP without having to know the existing password. Change the Windows XP login password.

A seasonal tradition brought over from Japan to America by Japanese-American farmers, making hoshigaki (as they're called in Japanese) is a fun outdoor autumn project you can do before the winter season really kicks in. Hang a bunch of peeled persimmons on a string outside, wait for three to five weeks, and harvest yourself some naturally dried persimmons during the winter months. Though peeling the fruit and then regularly massaging the fruit every few days after hanging may be more labor in...

What can you do if you're about to leave for a big trip and can't find a plant-sitter to regularly water your indoor plants? Just like pets, your indoor ferns and marigolds need attention, too!
to be honest with everyone, this is probably the first thing ive written about magic the gathering, but i figured i might as well start somewhere. in the game of magic the gathering there are countless different keywords, some being common, like trample, or rarely used or seen, like splice. what i wanted to do was take a closer look at some of the different keywords out there, and see just how they change the average game.

You can see why Ralph's daughter Dylan may have conceived of the $15 grand gingerbread house. Below, images of the fashion King's exotic car garage, via Vanity Fair.

If you don't watch Argentine soccer regularly, it's possible that you don't know who Martin Palermo is. He scored Argentina's second goal against Greece yesterday and wrote another page in a story that's bound to be made a movie someday. He's won about 14 titles, scored over 222 goals in Boca Juniors and is their record striker.

With film being such a vital outlet and marketing tool for fashion, movie stars are either wearing the coolest and latest threads, or retro looks that are sure to make a comeback. I regularly see a cool jacket or pair of sneakers being worn by an actor in a movie I'm watching, and I just know those items would look great on me.

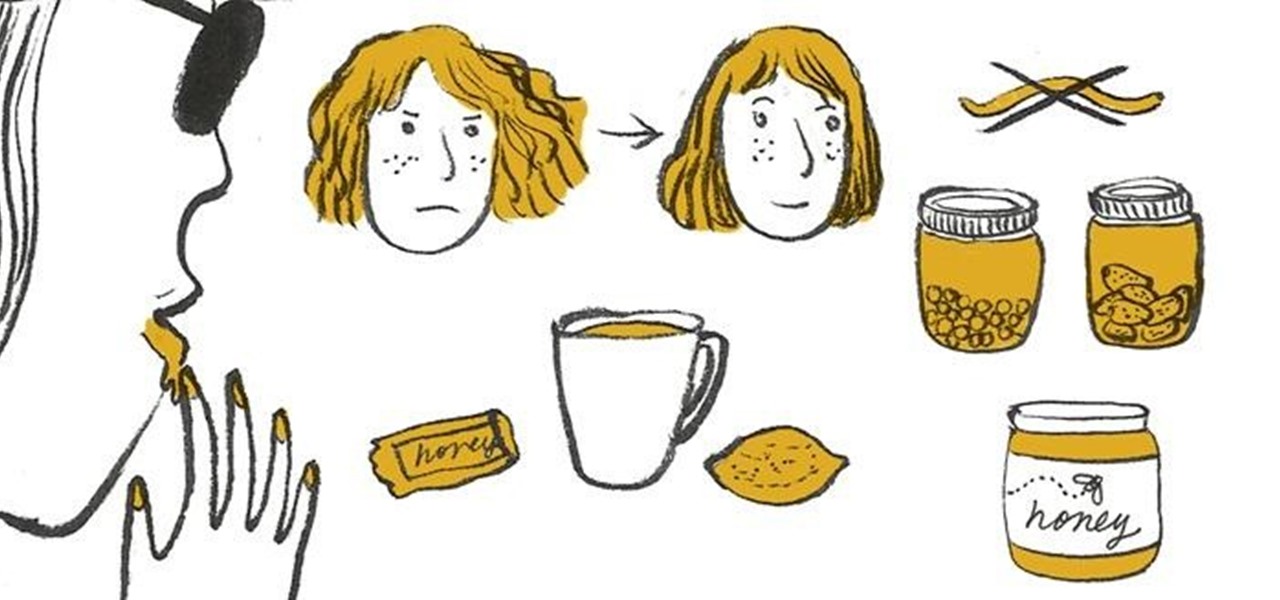
Got a minor cut, but no Neosporin? Rather than running to the nearest drug store, simply grab a jar of honey from your pantry and apply directly to the wound before wrapping with a band-aid.

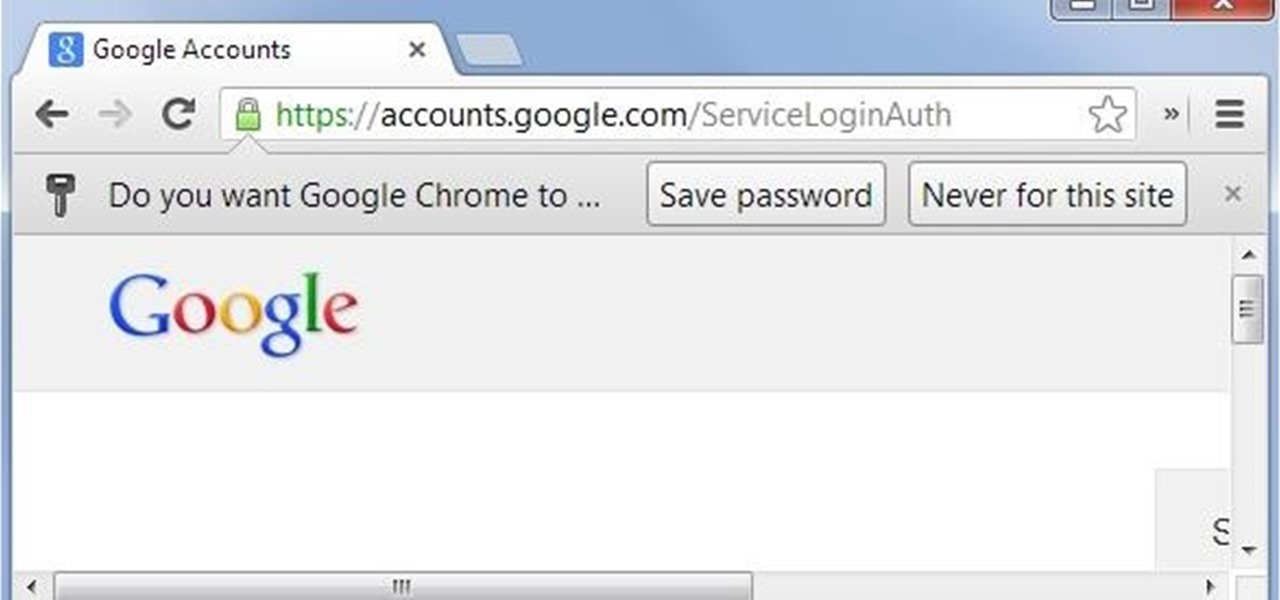
SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

Don't want one of your Facebook "friends" knowing your status updates? Prefer to keep a few of those "friends" out of your photo albums? Would you like to prevent a few "friends" from accessing your address?

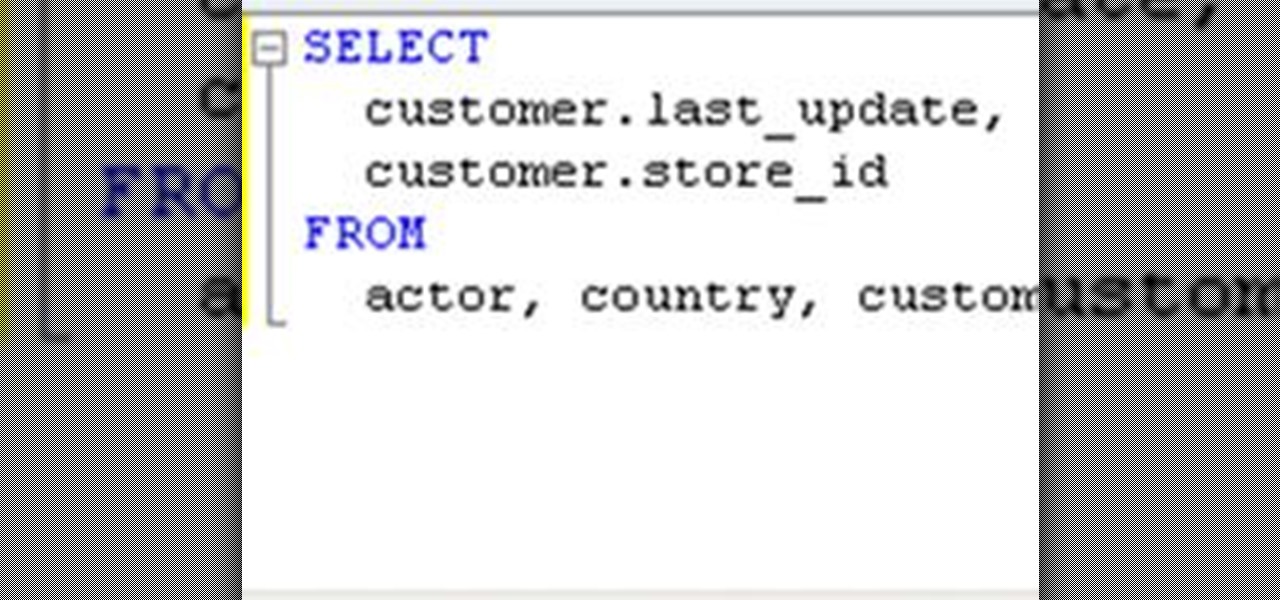
If you need to build a SQL query, you can choose one of two alternatives. The first and a rather old way is using a console. But if you build your queries in MySQL console, you have to remember all the commands and keys. This is not a convenient way, because query execution is a time-consuming process. Another way is to use some graphical interfaces for MySQL. It can fulfill many developers' requirements, including query execution.