Diet = Die or Eat As Biological definition, food is defined as; any substance consumed to provide nutritional support for the body. It is usually of plant or animal origin, and contains essential nutrients, such as carbohydrates, fats, proteins, vitamins, or minerals.

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

JavaScript is one of the main programming languages that the Web is built on. It talks directly to your browser and exchanges information with it in ways that HTML simply cannot. With JavaScript, you are able to access browser cookies, website preferences, real-time actions, slideshows, popup dialogs and calculators, or you create entire web-based apps. The list goes on nearly forever.

With FarmVille being one of the hottest Facebook games on the market, it's no wonder it's the primary target for scams and virus downloads. Anyone playing FarmVille is at risk, but the primary targets are those looking to improve their gameplay and build their farms and neighbors up. These "farmers" are the ones seeking quick hacks and cheats.

Bamboo is easy to grow, but there are a few things you should know before starting. There are hundreds of species of bamboo and they can be roughly divided into either running or clumping bamboos. Almost all cold hardy bamboos are runners and almost all tropical bamboos are clumpers. Running bamboos send out root like rhizomes underground and can spread many feet each year. Clumping bamboos slowly expand and stay in a tight clump with canes close together. We grow dozens of cold hardy bamboo ...

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

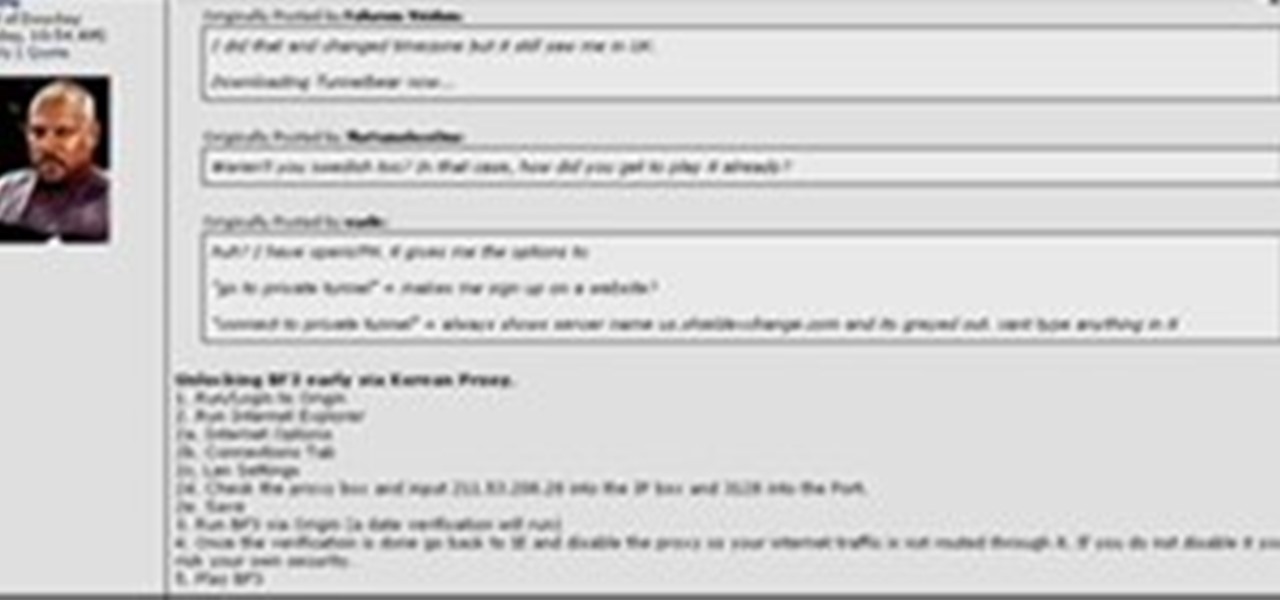
Battlefield 3 officially comes out tomorrow but people have figured out a way to play it today if you have it downloaded (digital pre-install). All you have to do is fake an ip to make it look like your timezone is ready to play. I'll try this when I get home, in the meantime:

Have an HTC smartphone? Chances are that some of your stored personal data has been hijacked by malicious apps on your device. Android apps that have permission to access the Internet, which is pretty much every ad-supported app out there, can snag valuable information such as email addresses, location history, phone logs, text messages, and more.

Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by amateur and wannabe hackers who want to have a little fun, but don't want to learn how to actually "hack" anything.

If you're lucky, your digital camera has a built-in intervalometer that lets you operate the shutter regularly at set intervals over a period of time. Why would you be lucky? Because you can create some very awesome time-lapse videos, like the horribly beautiful eruption of a volcano or vivid star trails in the night sky. You can capture the stunning display of the northern lights or even document the rotting of your favorite fruit.

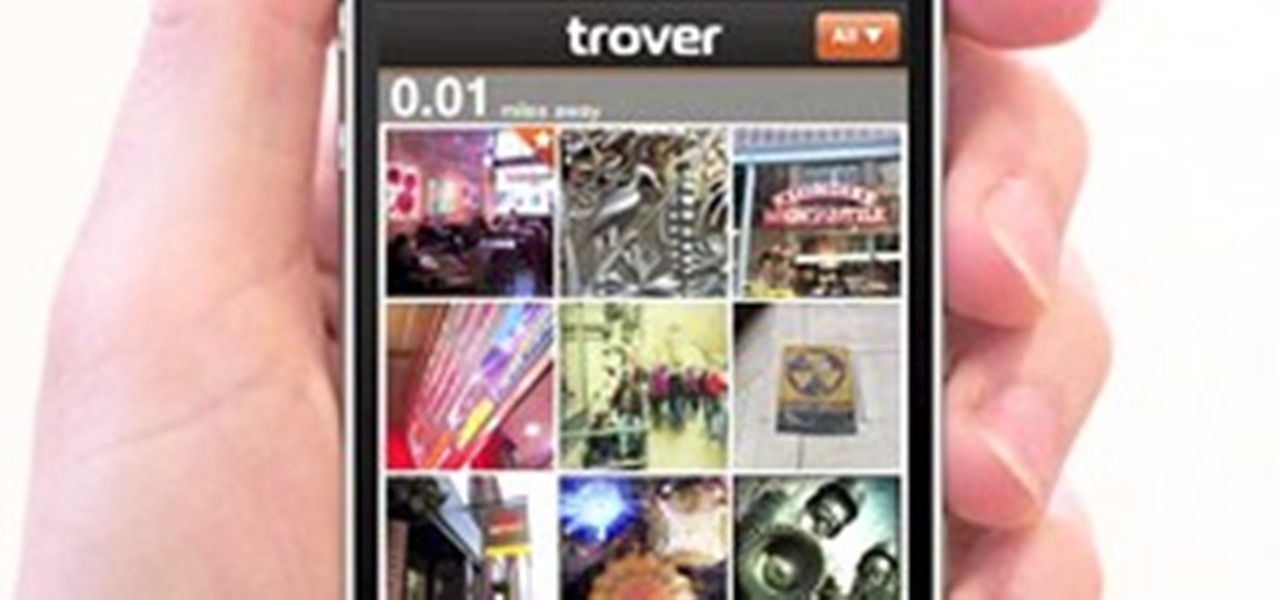
You're in a new city and you want to explore—what mobile app is best? If you want to know what club is hopping that night, use SceneTap. If you want to know if any friends are at a nearby get-together, use Foursquare. If you want to know what restaurant is best, try Yelp. But if you're looking to get a real feel for the city, skip the more touristy destinations and take to the streets—discover where some great graffiti is located or where the best view of the city is with the Trover iPhone ap...

Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giving them access to the cookies that keep you logged in. This is called session hijacking, and grants them easy access to your accounts, like Facebook, Flickr and Twitter. Now, there's an even easier way to do this—a mobi...
I remember once listening to a Christian comedian making fun of the way some Christians pride themselves on all the "evil" things they don't do.

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:

This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188,279 of them were decoded and made public. The biggest takeaway? Many Gawker denizens use downright dumb passwords. (Guess they didn't see their own Lifehacker's story on avoiding such a thing.)
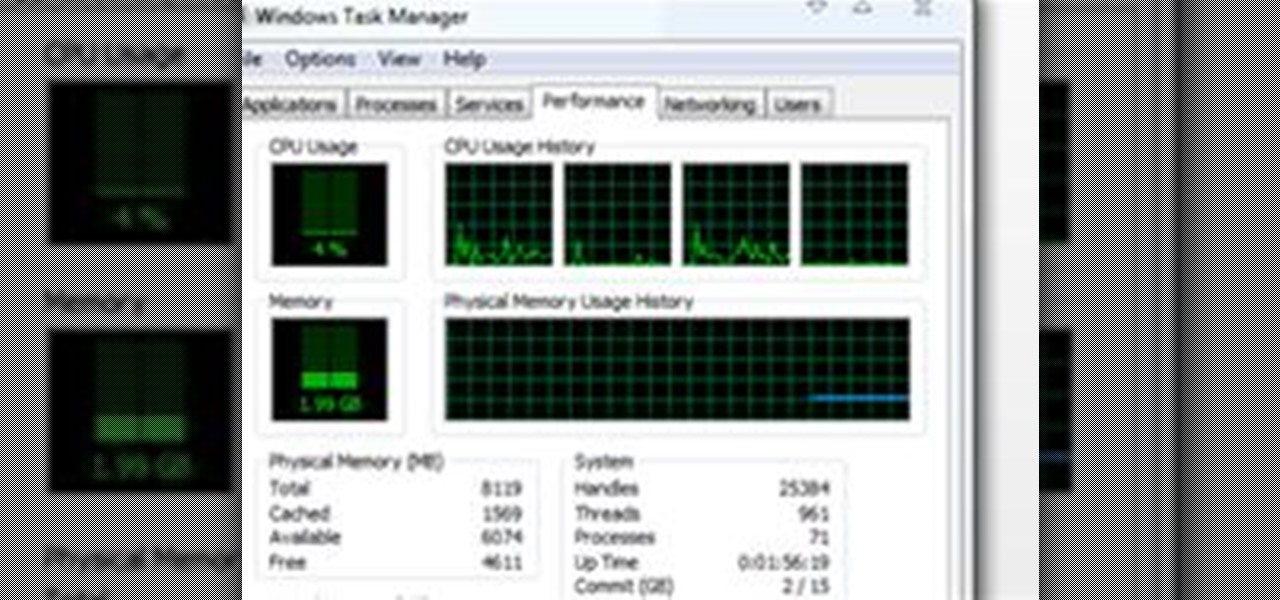
How to Fix Windows 7 Slow Start Up Is your Windows 7 slower on start up? Wondering how to make Windows 7 super fast? There are various reasons why this operating system performs slower but one common reason is that mostly it happens because of too many start up programs and services running in the background.

So, you've made your first zine. Now what? That depends on a couple things:

This is a followup from my recent series on XSS exploitation, giving a few extra attacks/tricks to try.

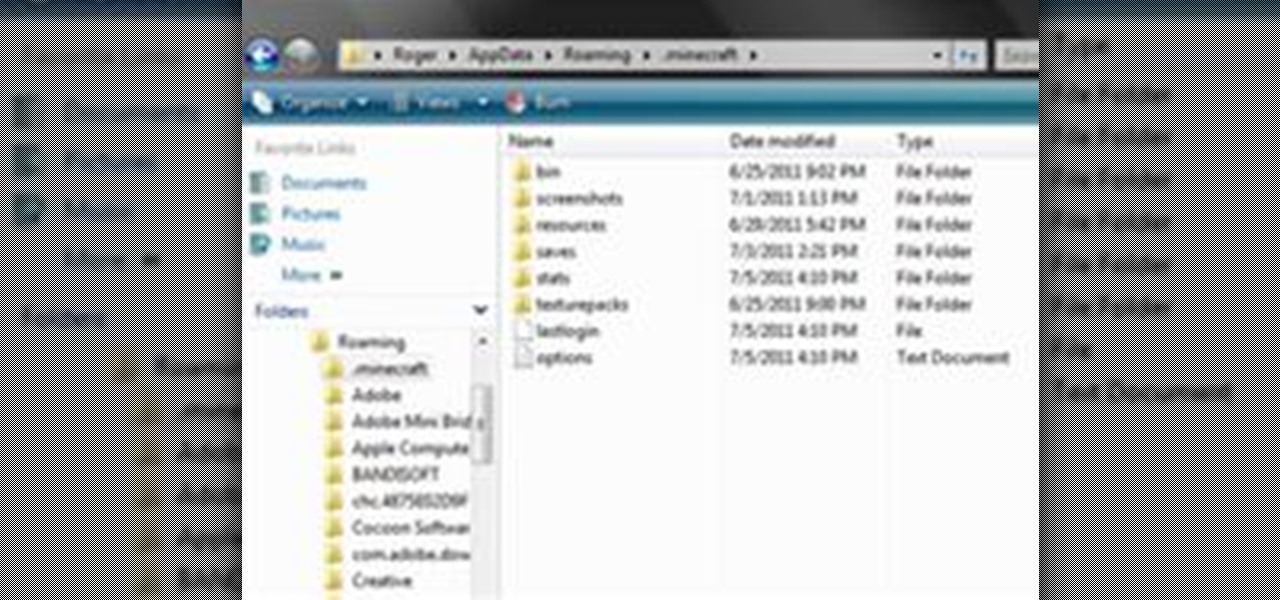
In this article, you will learn how to move your Minecraft save files. This knowledge is very useful if you want to give your friends a copy of your offline world, or play on one of theirs. You can also make backups, or move your offline world to your server folder to play online.

Introduction This is one of the things I am asked the most and there are so many different answers. It is hard to just tell you without know your computer's current speed or what type of hardware it has. So here I will talk about how to speed up a slow computer and how to keep your computer running fast.

Social Profile Change the privacy settings on your social profile (Facebook, MySpace, Friendster, Twitter, etc.) so that the following information can't be found by a random person who you didn't accept you as a friend:

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.

Watch out Instagram, there's a new free, sociable photography filter app that hit the iTunes App Store recently, and it just might be some good competition. It's called PicYou and might sound familiar to some of you photo sharing fiends out there. That's because it's been a successful web-based alternative to Instagram for about six months now.

Welcome to the closing of the second HackThisSite and programming Community Byte. First and foremost, I would like to ask that people start showing up on time to the Community Bytes. If you need help converting your time zone to PST, go to Time Zone Converter. When users do not show up on time, we have to go backwards and catch everybody up. This wastes time and will also make other users' experience less enjoyable when they have to watch and listen to the same thing 100 times. Punctuality as...

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

To the displeasure of many loyal Firefox users, Mozilla has been deploying what seems like a new marketing strategy to "catch up" to Google Chrome. I have no idea if this is because the version number is higher than theirs, but it is downright annoying. It's not all complaints, though. Firefox has done an amazing job at completely revamping its source code and redesigning all of its engines, making it a more than worthy competitor to Chrome. However, we are displeased with Firefox because eve...

As we all know, security is a big thing here in Null Byte. We've talked quite a bit about ways to encrypt traffic and become anonymous on the internet, some of which entail using proxies, VPNs, and SSH tunnels. We've also talked about preference using SSL pages in practice for safe logins. These are all great protocols and tools, but aren't without their flaws and inconveniences.

Welcome to another Community Byte announcement! For the past few Community Bytes, we coded an IRC bot, and hacked it. Then, we created a web-based login bruteforcer! This week we are going to start something a bit different. We are going to start going through the missions at HackThisSite one-by-one each week, starting with the basic missions.
On Thursday, March 9, there was a news story on the evening news about Khan Academy (NBC News). The story began when Sal Khan started tutoring his cousin in 2004. Since he was in Boston and she was in a different city, he decided to make and post videos on YouTube so anyone could watch the videos. Later he added videos for her brothers and for people that contacted him with requests for other videos. During this time Sal had a job that he later replaced with another job. Today Sal has 2010 vi...
Many people must be asking, how do you enter a coupon code on Wizard101? This is a follow-up of the "Promo Code: 1000 Gold Coins" post. So here's how you do it:

Hey wizards! As you have read in the gardening article I put up a few days ago, it requires the Test Realm! It's pretty easy to use the Test Realm, but there are a few very important limitations you have to pay attention to before using it. Many of you reading this may be pretty agravated. Here's how KingsIsle puts it:This Test Realm is available to Subscribers.

Normal body temperature, normothermia or euthermia; is a range of temperature rather than a fixed number. That Range represents the temperature that could be measure form the body under normal conditions.

The noble board game has stalwartly staved off elimination in the face of more technologically advanced video games for four decades. Try as they might, video games just can't seem to surpass them as an easy-to-use diversion for large groups of seated indoor people.

Scrabble has invaded just about every medium out there. It started as a mere board game, but has since spawned numerous board game spinoffs and variations, an electronic version, mobile apps for just about anything (Android, iPhone, iPhone, iPad and Kindle), games for both PC and Facebook, and video games for handheld consoles like the Nintendo DS and Sony PSP. Heck, it's even on the PlayStation and Xbox 360 gaming consoles. And it hasn't forgotten about film. You can see Scrabble featured in...

Blizzard Entertainment is considered one of the most successful game developers in the world. Ever since the release of Warcraft: Orcs & Humans (their debut Warcraft game) in 1994, they've set sales records and created genre-defining games with remarkable consistency. But the company wasn't founded in 1994—it all started back in 1991 when they were called Silicon & Synapse.

Every summer my husband and I plant a tomato plant. We do this to enjoy the plump red tomatoes right off of the vine.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

I can't say it's absolutely true, but when it comes to mobile word gaming, there's Scrabble people and then there's Words with Friends people. It feels segregational. Rarely does one play both. At least, that's what I see when it comes to my family and friends.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.