Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

Experts from the World Health Organization just expressed concern for the rising number of measles outbreaks across Europe. Despite a perfectly capable existing vaccine, "immunization coverage has dropped below the necessary threshold of 95%," causing the measles to spread throughout the European region.

The Weather Channel, by virtue of its name, has always been tasked with the difficult problem of making the weather interesting. As Mashable notes, they've turned to augmented reality for a solution and can now render a 3D storm in their studio, as well as help us understand how bad a storm might be with 3D forecasts.

Many websites are crowded with ads, pictures, and other irrelevant content that make it harder than necessary to read a simple article on your iPhone. In many cases, you have to zoom in just to get a better view of the text you're attempting to read—unless the webpage blocks zooming.

Although I am a loyal premium Spotify subscriber, I still regularly use Pandora in hopes of stumbling across new artists and songs. If I'm fortunate enough to come across something I enjoy, it's easy to use the Like feature in Pandora to locate the song later.

Apple's iPhone is one of the most popular, most expensive smartphones in the world, yet with a broken Home or Sleep/Wake button, it might as well be a doorstop. There are many different DIY ways to fixing a busted Home button, but the Sleep/Wake button (aka Power button) is a little more averse to DIY trickery.

With over 500 million downloads on Android alone, I find it safe to assume that most of us use the Chrome Browser on our mobile devices; it's great for reading articles with Reader mode enabled, syncs open tabs and bookmarks across all your devices (as long as you're signed in to your Google account), and is regularly updated with new features and optimizations.

Aside from identifying songs with Shazam and using the "Hey Siri" feature while driving, Apple's personal assistant isn't something I regularly use on my iPhone.

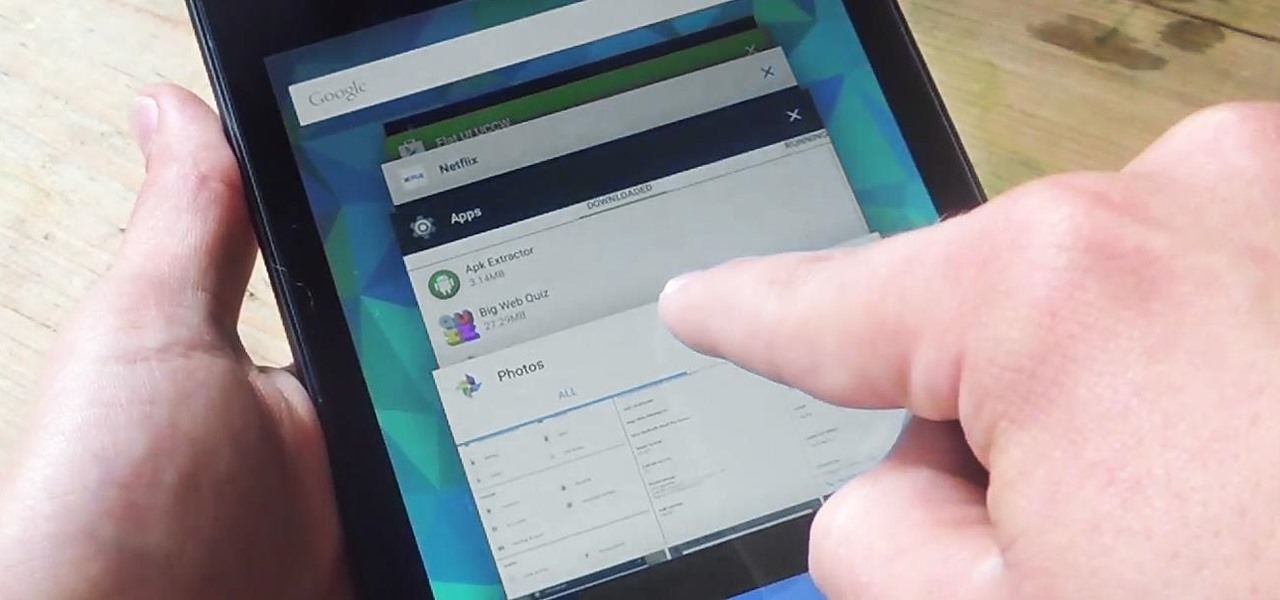
On earlier Android versions, you were able to hold down on an app's icon in the recent apps menu (aka app switcher) and jump straight to the app's info page. From there, you could easily uninstall the app, force-stop its activity, or clear its cache and data.

To say that there are a lot of app switchers and launchers available is an understatement. We've covered a few ourselves, including Loopr and Switchr. But why not check out one more?

As you level up in online gameplay for Grand Theft Auto 5, certain vehicles become inaccessible—no longer spawning as they regularly would. One such vehicle is the Cargobob helicopter, otherwise known as the largest and heaviest helicopter in the game. If you're no longer able to spawn a Cargobob in GTA 5 and want one for your own, you can purchase one with a little help from YouTube user omgurheadsgone.

In this video I did a very simple nail design that can be worn by women and teens on valentines day or just regularly too ! It is a very easy to create design and looks not only pretty but also immensely elegant!

Starting your own seedlings is a great way to save money, have a wider selection of varieties and gain personal satisfaction. Here are easy to follow tips on getting your seeds off to a great start.

Not sold on Apple's iPhone claims of battery performance? I will show you some simple tweaks and tips to reduce that rapid battery drain and extend the use of your iphone between charges -free.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

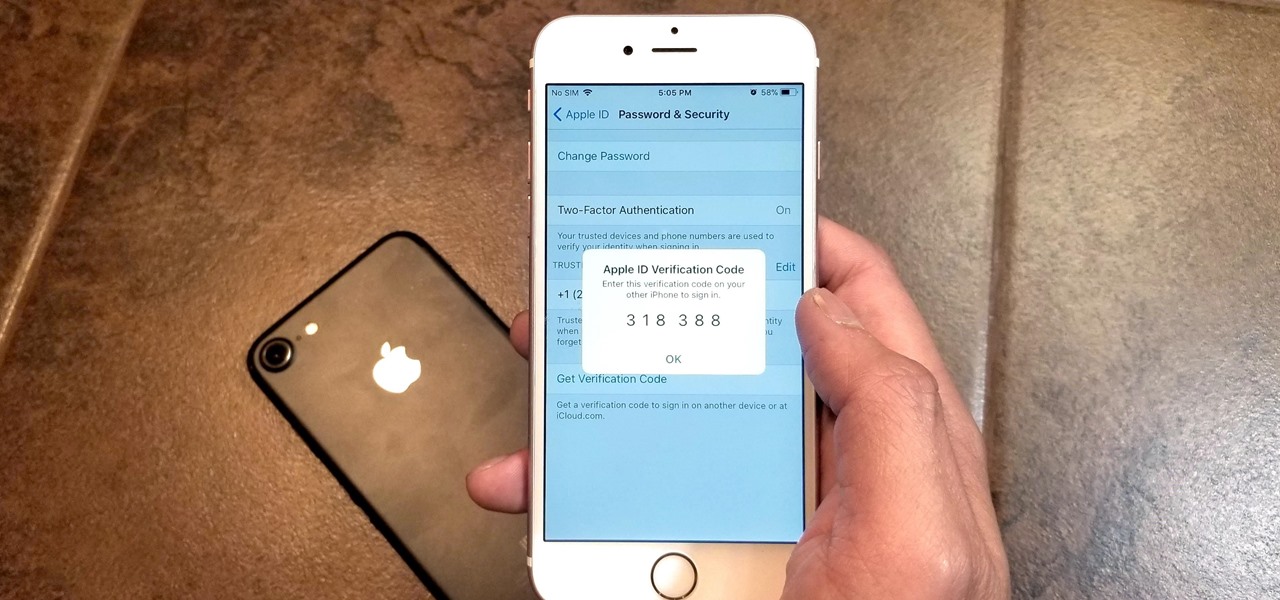
Two-factor authentication has been around since iOS 10. It's a handy option that adds an extra layer of security to your iPhone and makes its almost impenetrable security even stronger. This feature has remained intact in iOS 11 and iOS 12, and thanks to the straightforward nature of iOS, is relatively easy to enable.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

This video will show you how to record video on your Apple iPhone 3G for free! This is a complete guide to installing the iPhone Video Recorder on your iPhone 3G, which also works on the First Generation iPhone.

This video shows how to enable automatic login for Macintosh Operating System users: 1.Click on the Apple icon in the top-left corner and select System Preferences.

If you're the sort of person who regularly engages in DIY projects around your home, one imagines you'll need to take a shower every now and again. In this tutorial, Danny Lipford will guide you through the process installing a ceramic soap dish in a shower stall.

If the thought of drought resistant plants makes you picture only cactus and succulents, think again. There are many other beautiful plants that can help you conserve water. This gardening tutorial teaches you how to create a xeriscape or drought resistant landscape. These plants do need to be watered regularly at first but once they have developed their root system you can pretty much leave them to fend for themselves.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

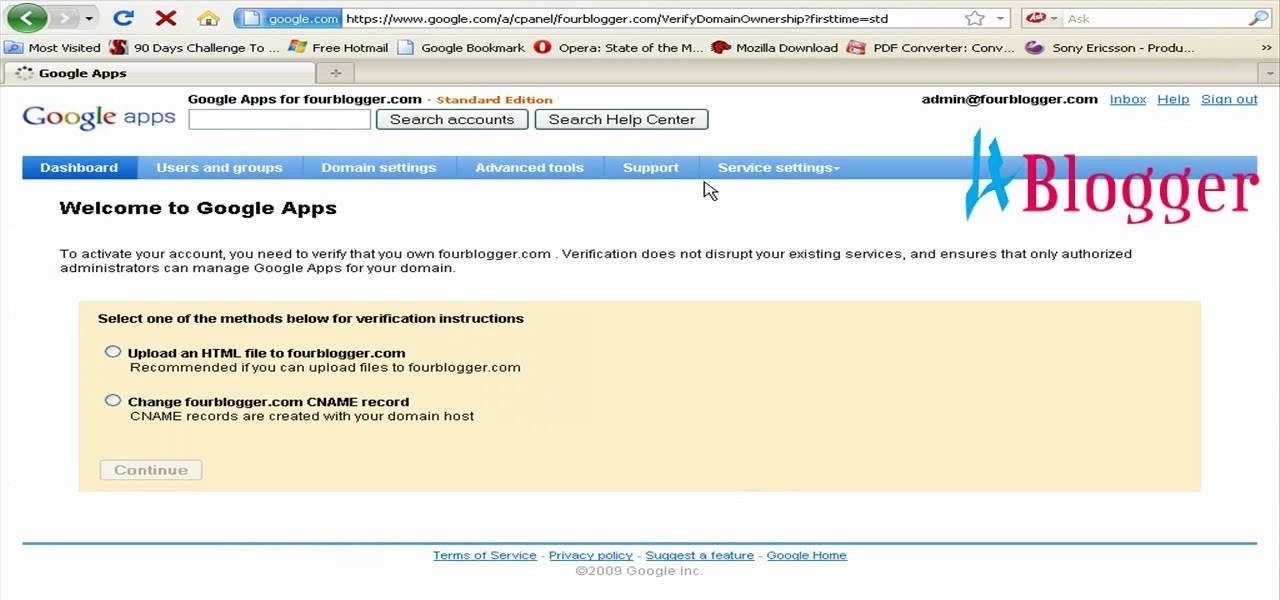
You can create the Google apps email like Gmail for your domain. So to do this first you need to go to the google.com/a and click on the standard in "other Google apps editions". Now click on "get started". Now select "administrator: I own..." and enter your domain name and click get started. Now on next page create your account by filling all the fields and click continue and now fill the info of your administrator account and click I accept button. Now next step is for the verification of y...

One of the best parts about cooking is feeling the cold, hard steel of your cooking knife in your hand. The sleek skillful edge doesn't stand a change against any delicacy, unless it's dull. A dull knife takes the fun out of cooking and is actually more dangerous than a sharp knife, so take a moment to sharpen and care for your tools.

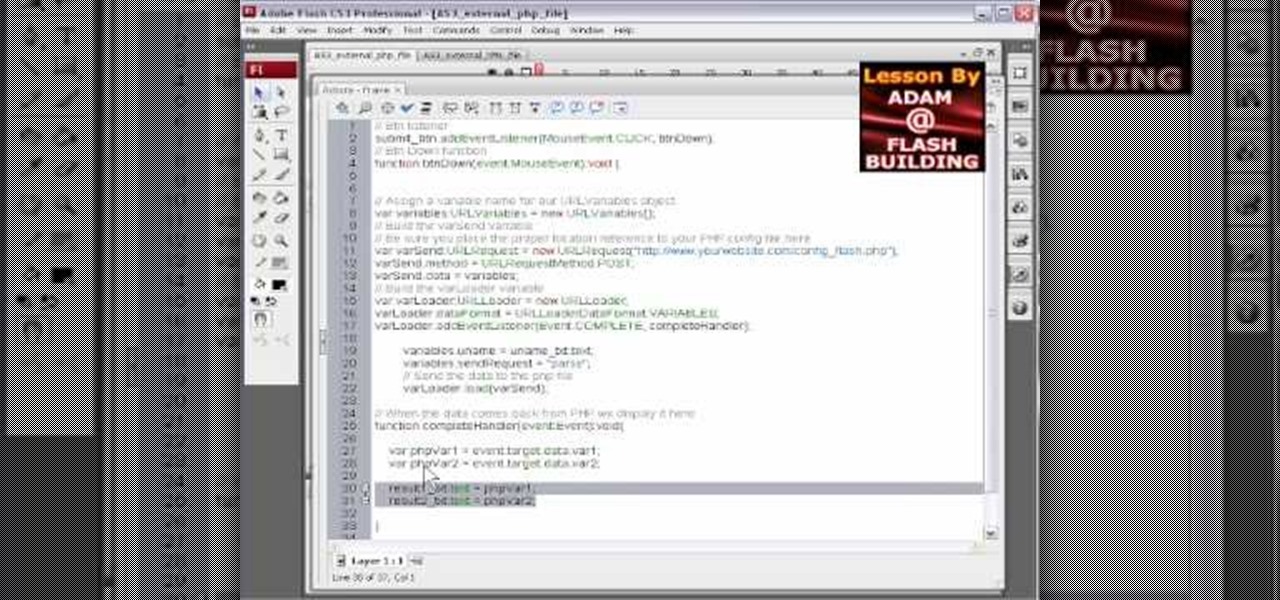
All the files you need are in a free download on DevelopPHP. PHP has to be on a server. It will not run on a local machine. Type your name. There are two variables which show up in the dialog boxes (which are stacked.) You can change the user name. It sets up a URL request and a URL loader and sends some URL variables and are placed into the value of names and pairs. They get posted to the PHP file. Place the URL reference location of where the PHP files are on your server in the line that sa...

In this video from rscp1050 we learn how to SSH into a jailbroken ipod touch or iphone. First go into Cydia and search for SSH. You need to download OpenSSH. Then also install Toggle SSH. After installed, restart the iphone. Now on your computer, download WinSCP. Once installed, open it. Type in your IP address which can be found by going to your settings on your iphone. Click wifi, and click the blue arrow next to your network. There is your IP address. Then, User name is root. Password is a...

1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.

John Roy demonstrates the tutorial to view or retrieve layouts that ens with .swf. SWF files can be viewed by pasting the url in the address box.

Steps to Configure Your Modem/Router are: 1. Open Network connection and click properties