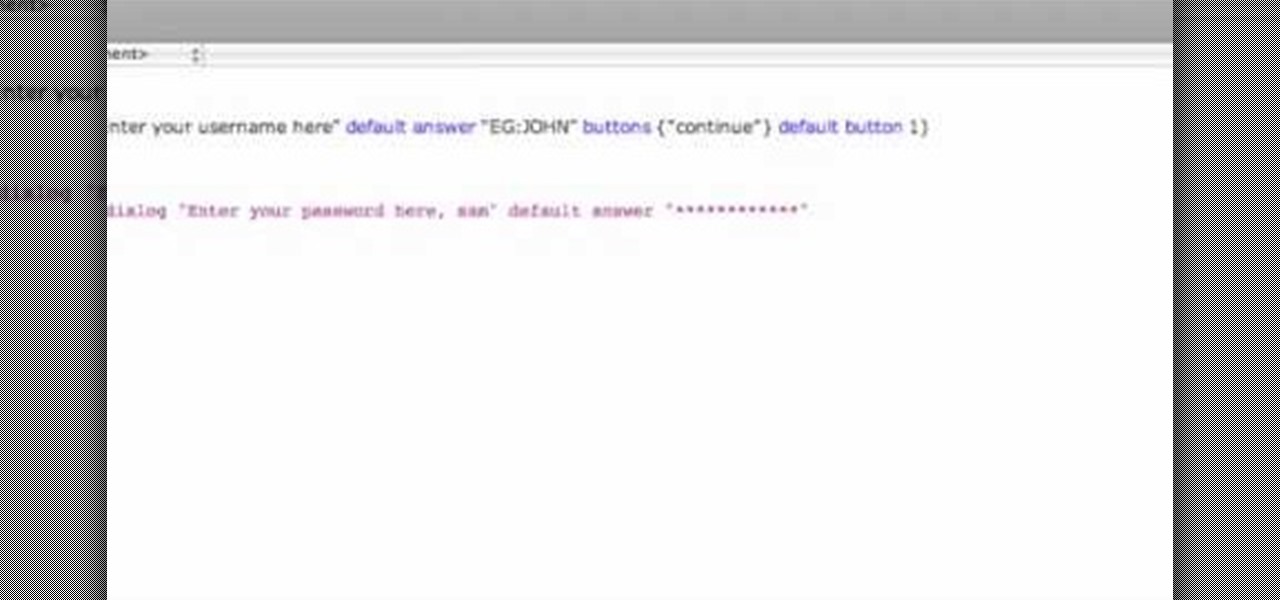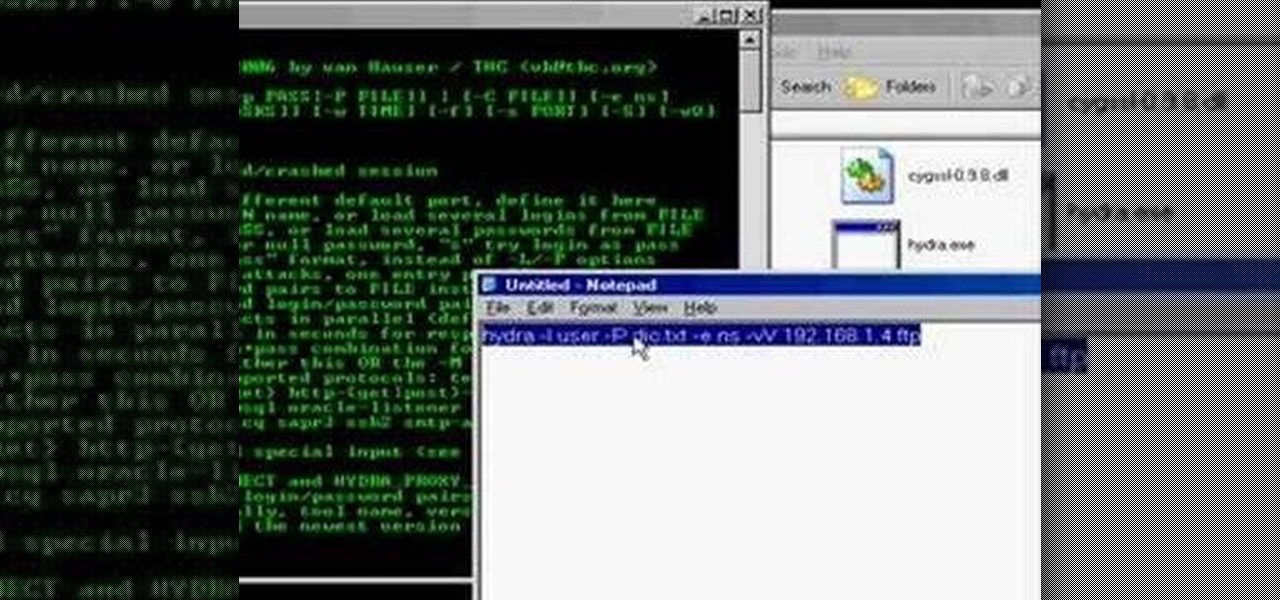
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved.

This video shows the method to SSH into iPod Touch 1G or 2G. You need an iPod touch 1G/2G with Firmware 2.2.1 or previous (Windows), a Windows based computer and a jailbroken iPod Touch which has Wi-Fi connectivity. Open Cydia, go to search and type OpenSSH and install it. Go to settings, Wi-Fi and click on the blue arrow next to the network. Copy down your IP address from the resultant window. Open WinSCP.net and go to Downloads, installation package. Install the package and open WinSCP from...

Research shows that color can have a powerful effect on our emotions. Start harnessing that power today. Watch this video to learn how to improve your life with chromotherapy.

Learn how to use more English phrasal verbs with this instructional English language lesson. get...over with
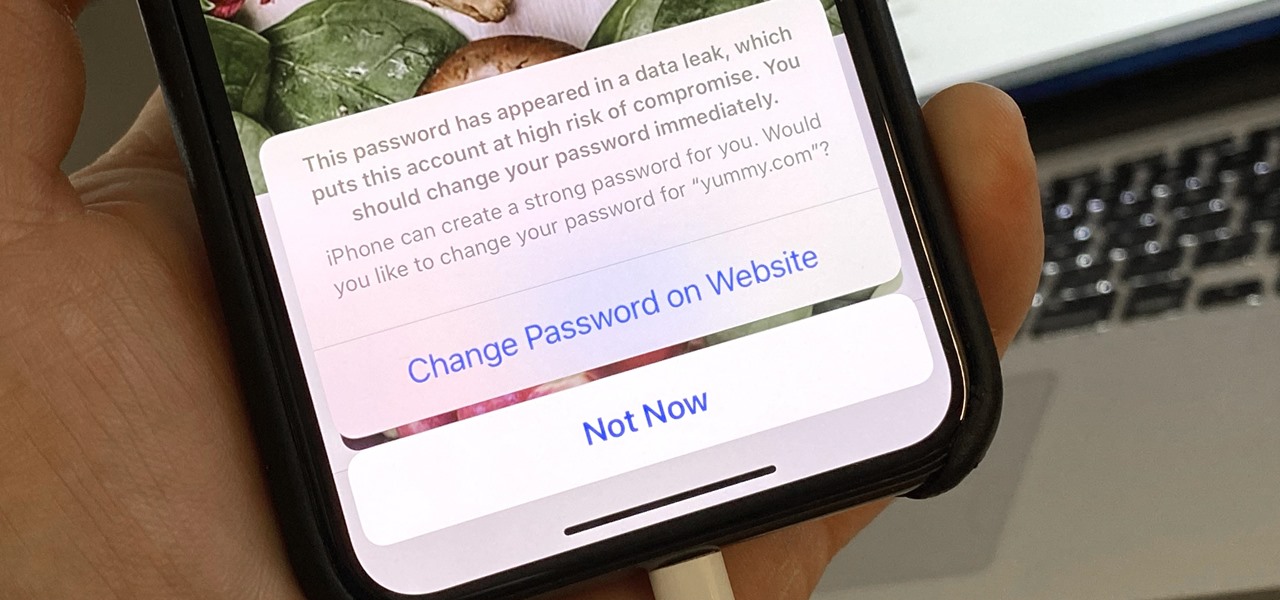
Everything lives online these days, so it's not uncommon to have hundreds of credentials for different accounts on apps and websites. That's why a password manager is a must, and your iPhone has one built right into iOS that you can start using today. In iOS 14, it's gotten even more useful since it can now monitor your passwords regularly to see if any match leaked password lists online.

There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

To become a tried-and-true Pokémon master in Pokémon GO, there's an incredibly important decision that needs your attention: Team Instinct, Team Mystic, or Team Valor?

Earlier this week we showed you how to use multiple accounts on Instagram, and now Facebook is rolling out a similar feature for its Messenger app, as well as a few other features.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

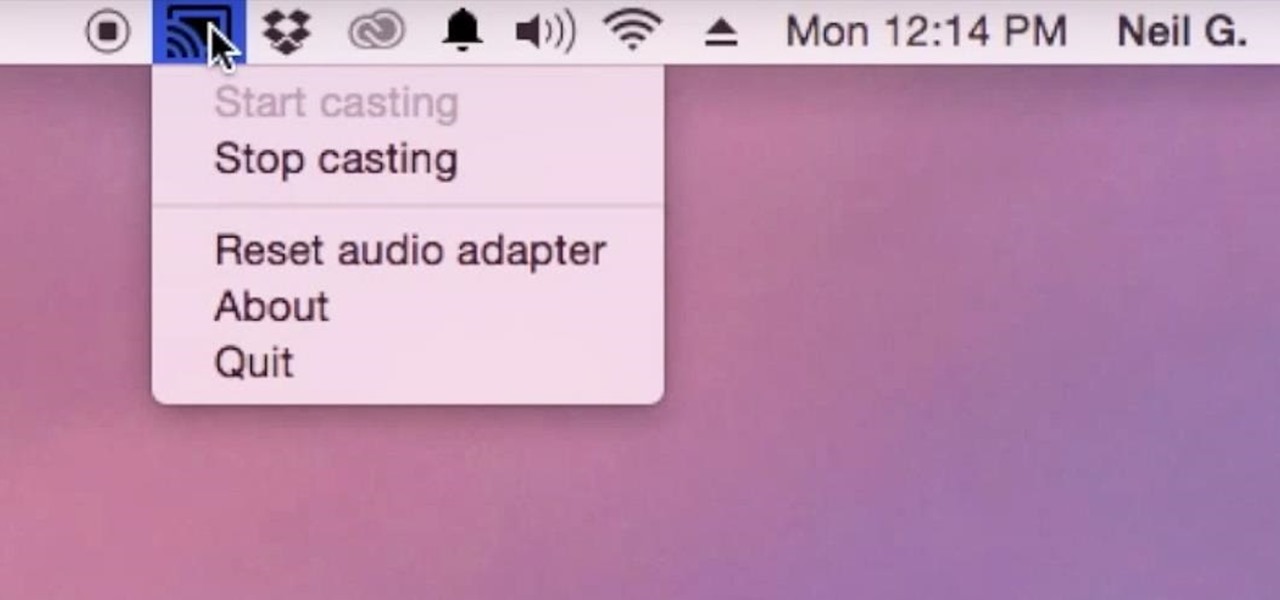
Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

All of those keys on your keyboard can do much more than just help to update your Facebook status or fire off a scathing tweet. By learning all of the keyboard shortcuts for apps on your Mac, you can cut back on mouse or trackpad usage to perform actions faster and more efficiently.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

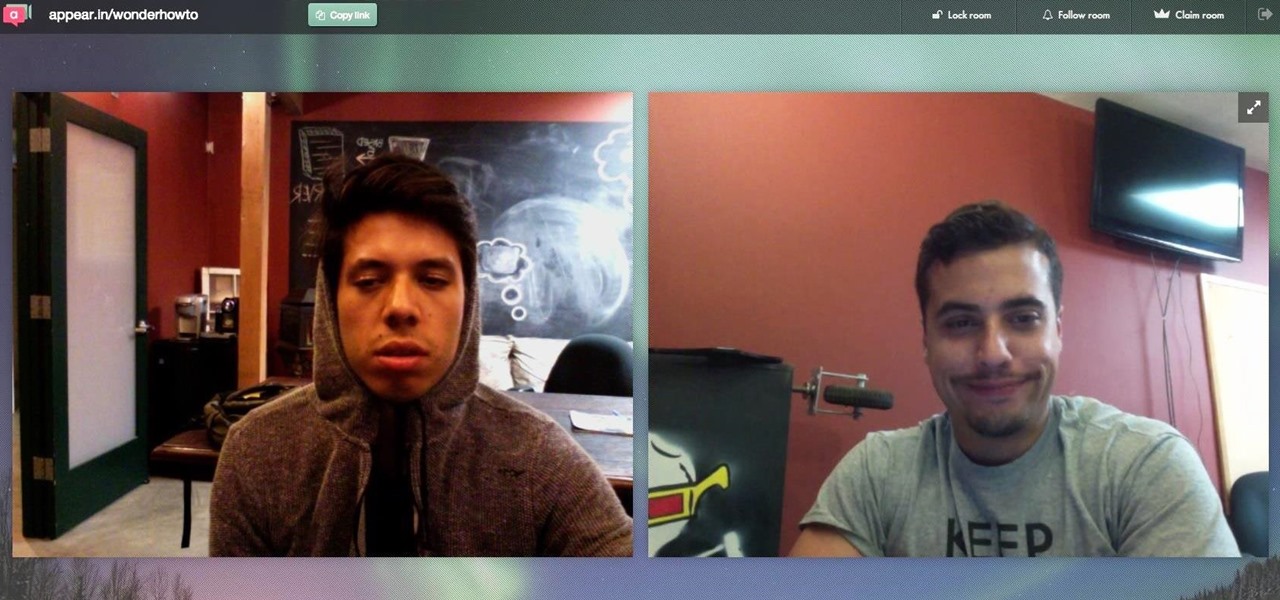
These days, phone calls aren't always the best way to communicate with others. Maybe you need to reach people out of the country, or you simply want to have a more visual conversation. Either way, there's a reason why video calling has become so popular.

Staying healthy is a progressive challenge we all face throughout our lives, and figuring out just how to do that can be a challenge when it's not your job. For doctors, however, it is. Here's how they keep themselves healthy day to day.

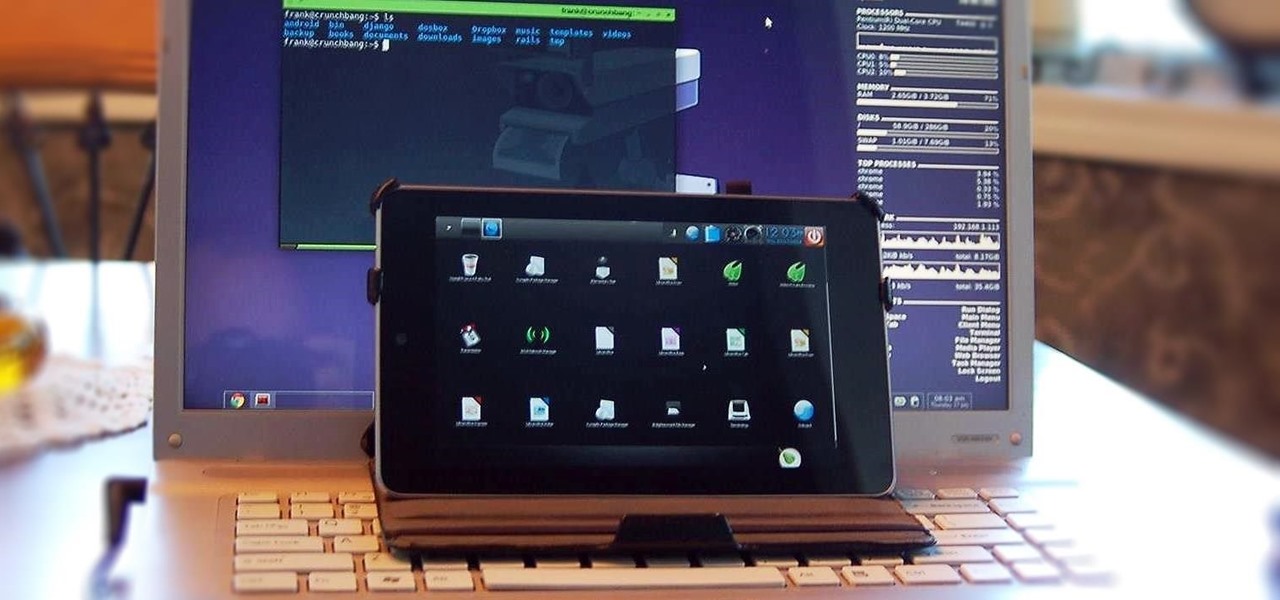
When people first learn that their Android device is capable of dual-booting different operating systems, e.g. Linux, they almost universally respond with, "That's so cool." And for those of us ambitious enough to actually try one out, we are typically filled with glee as we see Ubuntu, or something similar, boot up for the first time on our tablet or phone.

Fasting—or the practice of regularly abstaining from ingesting anything except water—is a pretty drastic move. I tried to fast for two days and made it to the 12-hour mark, which is when I broke down and ate a quart of ice cream.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

In this clip, Dr. Savant tells us how to improve our memory by exercising on a regular basis. By maintaining fitness levels we can improve our minds as well as out bodies.

Research says babies are comforted by scents associated with their mothers. Fragrances baby experiences with you regularly will remind her of you even when you're not right by her side, providing a feeling of comfort and "home." You can comfort your baby with just your scent with the tips in this how to video.

This video shows how to program a password and user protected application in AppleScript.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

A major software tool first promised during the reveal of the HoloLens 2 earlier this year is finally available.

The partnership between Magic Leap and leading South Korean wireless carrier SK Telecom took on an added importance earlier this week as the company unveiled the world's first nationwide 5G network.

The last time The Weather Channel showed off its broadcast augmented reality, the internet couldn't stop talking about how immersive the presentation looked, despite being shown on a 2D display.

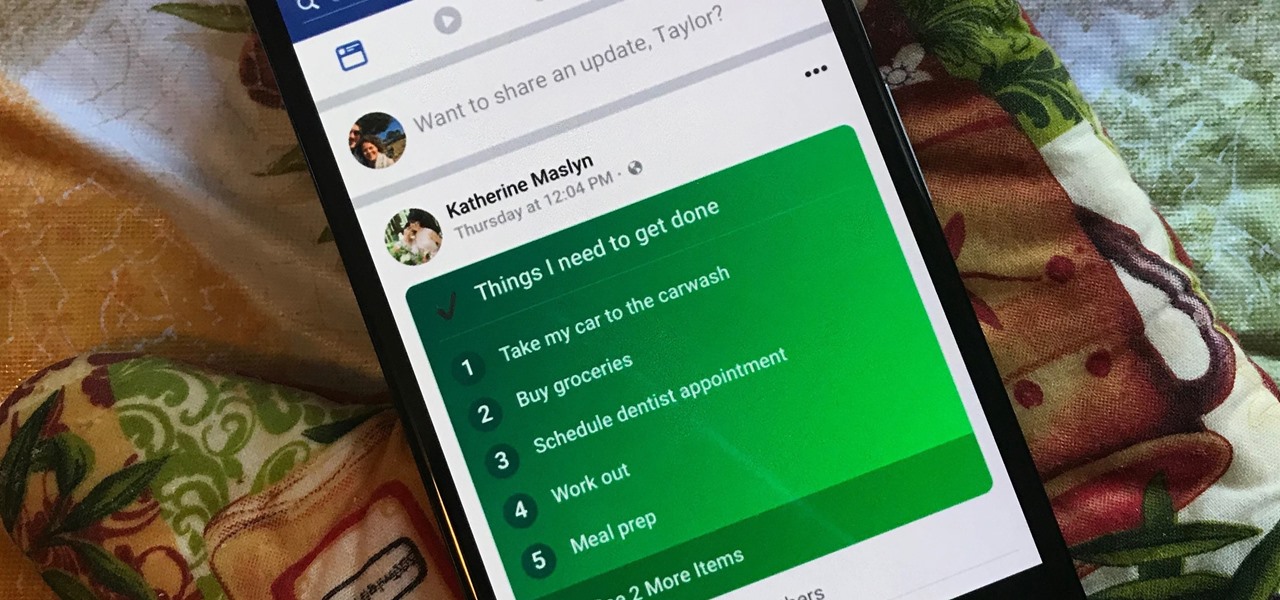
Facebook's status update box has received many new features over the years. You can go live, sell something, and even create a poll. But since all this was added, the status update box has been relatively stagnant. That's finally changing again with Facebook's newest addition: Lists.

If you love to hear yourself talk, you can now enjoy seeing your words materialize in augmented reality with an ARKit-compatible iPhone or iPad.

In the years leading up to the release of the Apple Watch, we were frequently teased with concept designs of what Apple's smartwatch might look like. Of course, many of those outlandish designs were off the mark, but the attention to the idea itself hinted that the public was ready for a mainstream wearable from a high-end hardware maker like Apple. Now smartglasses are getting the same treatment.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

If social media apps were houses in a neighborhood and augmented reality photo effects were candy, then Facebook went to Costco and brought home a full pallet of treats.

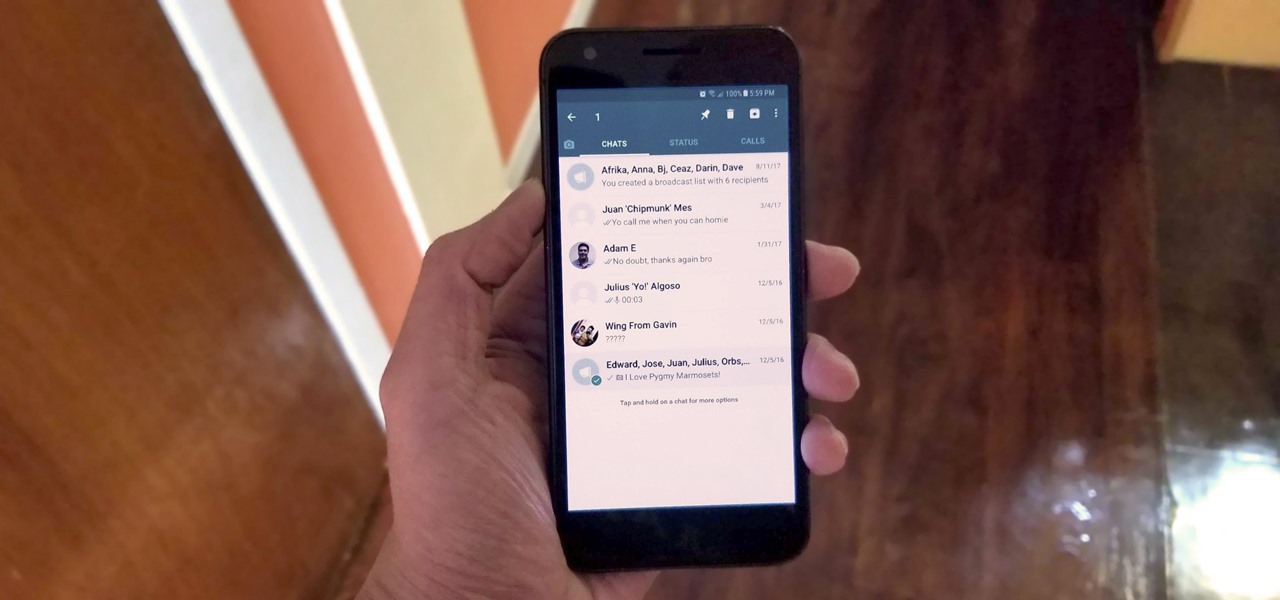
One of the downsides of living in an unprecedented age of connectivity is the near-constant bombardment of information. WhatsApp, the go-to messaging app for people the world over, is just as susceptible to buildup of useless media files, thanks to awesome features that allow us to communicate in multiple ways, such as broadcasting to friends and family. Luckily, the app makes it easy to remove old and unwanted data from your iPhone or Android.

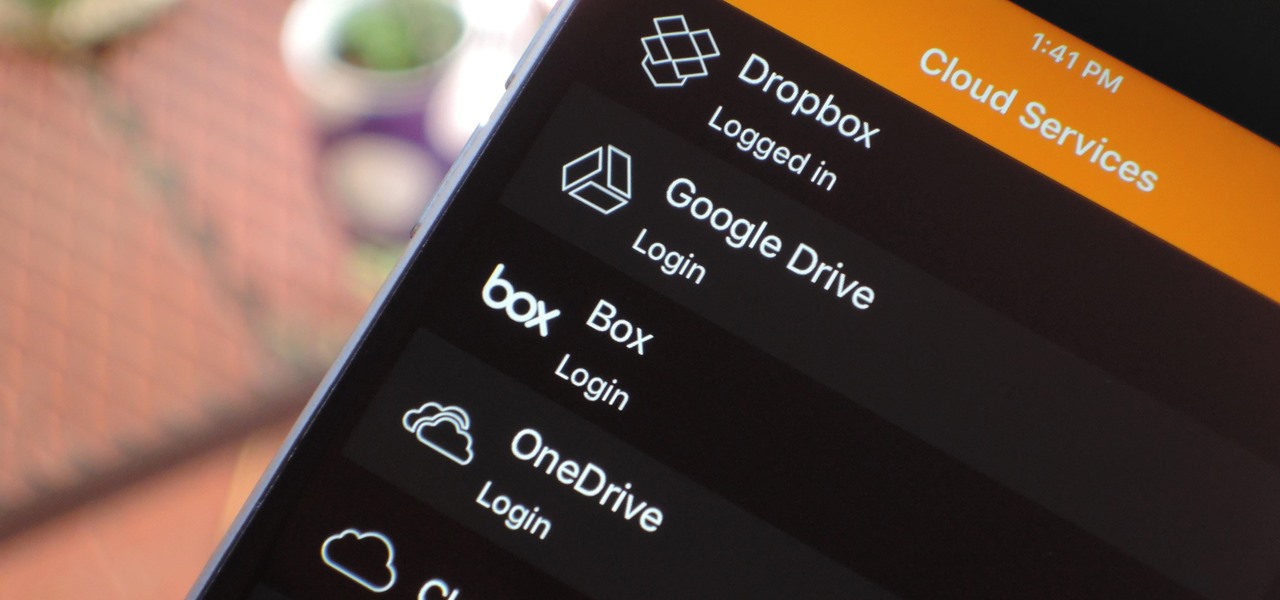
If you have movies and videos stored on Box, Google Drive, Dropbox, or OneDrive, you should definitely be using the VLC app for iPhone. After setting a few things up, VLC will let you stream videos directly from any of these services with a proper video player UI, complete with gesture controls.

Soy sauce is a sushi essential for most Americans and we don't often consider its exact origins whilst chowing down on that tuna roll.

Since its purchase by Microsoft in 2014, Minecraft has regularly been pushed to new platforms such as Windows 10, Wii U, and Fire TV. In that spirit, Microsoft-owned Mojang has been developing virtual- and augmented-reality versions of the blocky sandbox game.