Your Skype contact list might contain a sea of names that make it tough to find a specific person you're trying to reach. The same goes for your loved ones and colleagues, especially if you have a common name like Jennifer or John. Knowing that, you might want to change your Skype display name to set yourself apart.

Your Google history is mostly a binary choice — either you enable it fully, taking advantage of all its features while letting Google record your activity, or you disable it, staying incognito but also missing out on some fun stuff. But now, Google will let you auto-delete your history, allowing you to utilize all the perks that come with recording your history while maintaining some level of privacy.

Visitors to the Unity booth at the Game Developers Conference in San Francisco will get a special augmented reality treat courtesy of Magic Leap and Weta Workshop.

Samsung just announced the Galaxy S10 lineup, but we already knew each device's every nook and cranny. Thanks to leaks and hands-on demos, we know the OEM kept the coveted headphone jack, but omitted one treasured feature in its place — the notification LED. Why did Samsung strip the S10 of this light, and can users expect something to replace it?

After some social media teasing, the Star Wars universe's Magic Leap debut has finally arrived. On Tuesday, Magic Leap announced the release of Star Wars: Project Prog, which is available for free via Magic Leap World.
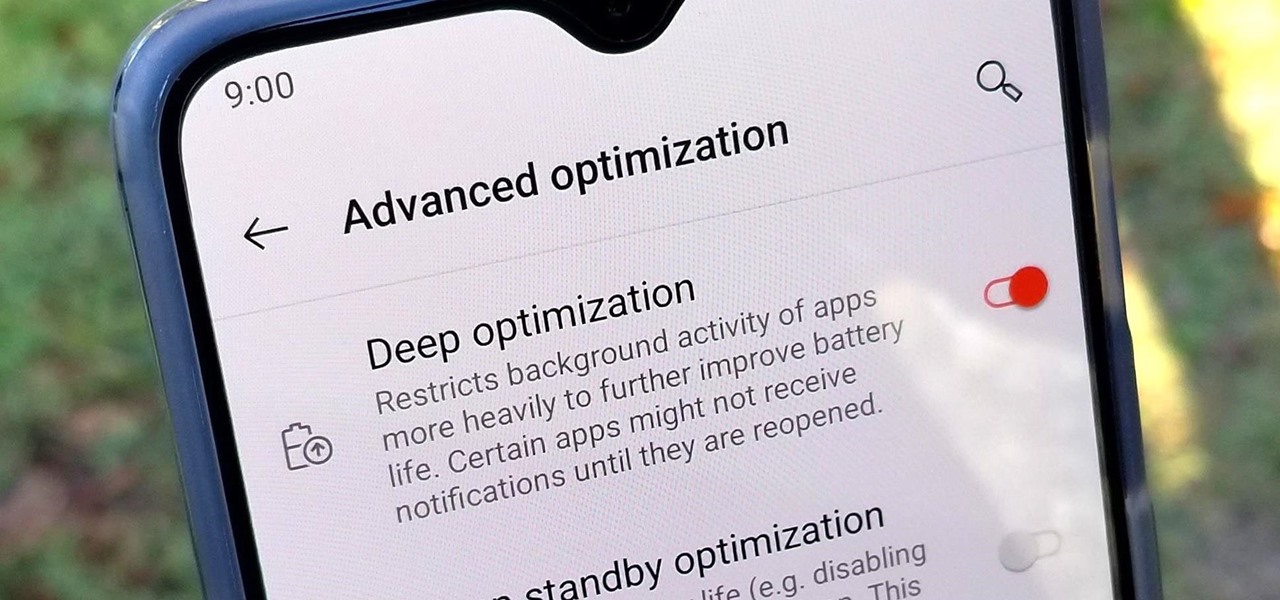
OnePlus is known for pushing the boundaries of what we thought was possible for a mid-range price. One of the best things about OnePlus phones is that their battery life is fantastic in general, but to achieve this, Oxygen OS will disable or delay notifications by default once your phone goes into deep sleep mode. You will not be notified until you wake the phone up — this could be an issue for some.

Despite the hype and potential of immersive computing, the augmented reality industry is showing that it is not invincible, as another AR hardware maker, this time Osterhout Design Group (ODG), is reportedly going out of business.

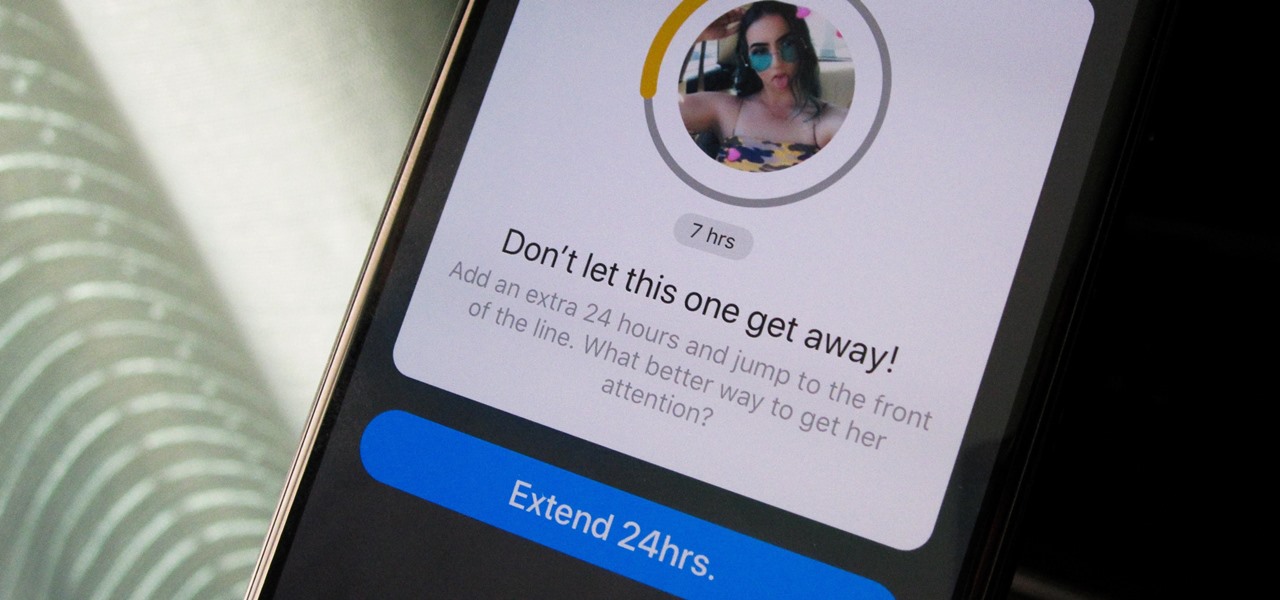
You've had your fun swiping, but now it's time to walk away from all of your online dating apps. Whether it's because you found someone you're interested in or just need some time away, it's important to know how to permanently erase your online dating footprint — and that includes deleting your Bumble account.

On Bumble, you only have 24 hours to connect with a match. If no message is sent, your match disappears and your chance of a connection is gone, but that doesn't necessarily mean that the other person isn't interested. If they lose their phone or don't receive notifications, they might miss your message on accident. Life happens, so what can you do if your 24 hours to connect are almost up?

So, you accidentally sent a voice message to someone in an Instagram DM. Maybe it contains an unflattering conversation about the recipient. Maybe it's a record of something embarrassing you said. Whatever your message contains, it's out there, on someone else's smartphone. You might think you're out of luck, and that your life is over. If you act quick, however, it won't be.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

We already know that Magic Leap is working with Hollywood motion capture legend Andy Serkis on a new immersive content experience but, so far, all we've heard are descriptions of the work. Well, now the mystery is over, and the character of Grishneck, who Magic Leap mentioned just last month, has finally been revealed.

The display is one of the most critical components in augmented reality hardware, and on Tuesday, one of the companies making that component, Avegant Corp., closed a funding round of $12 million to support development of next-generation AR displays.

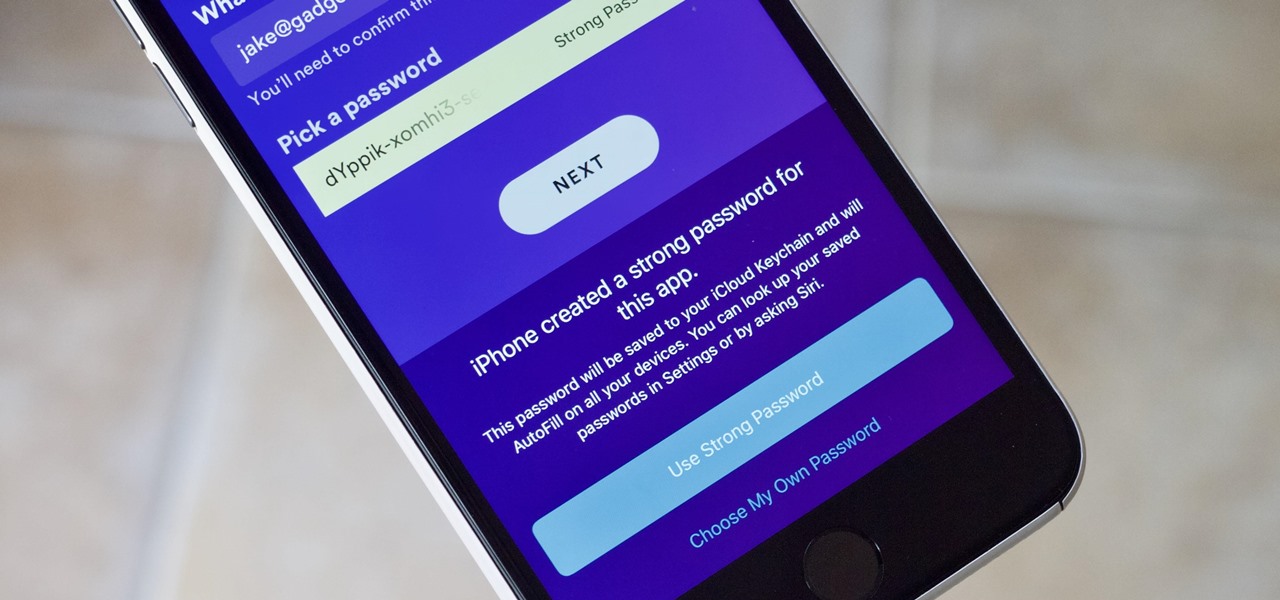
Maybe you prefer writing passwords in a notebook. Maybe you like creating your passwords yourself. Whatever the case, you don't like iOS 12's new automatic password generator, and you don't need it to pop up every time you enter a new password in Safari or a third-party app. Lucky for you, iOS 12 lets you disable the feature altogether. Unfortunately, that perk comes with a catch.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.

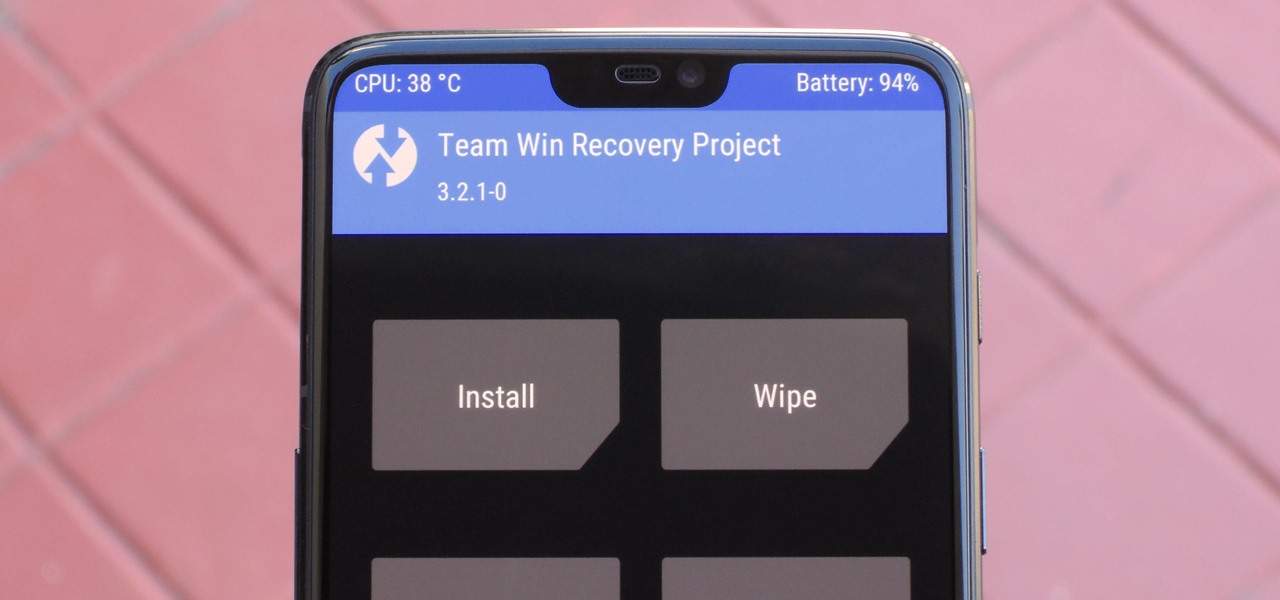
When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Badges? We don't need no stinkin' badges! That is, unless they have augmented reality content embedded in them and give us full access to Facebook's annual F8 developers conference — in that case, yes, we'll take all the badges.

Taking photos that are actually printed and hung on a real wall, versus being shot and shared via a social wall, is a seemingly lost art, but PhotoBloom AR wants to change that with augmented reality.

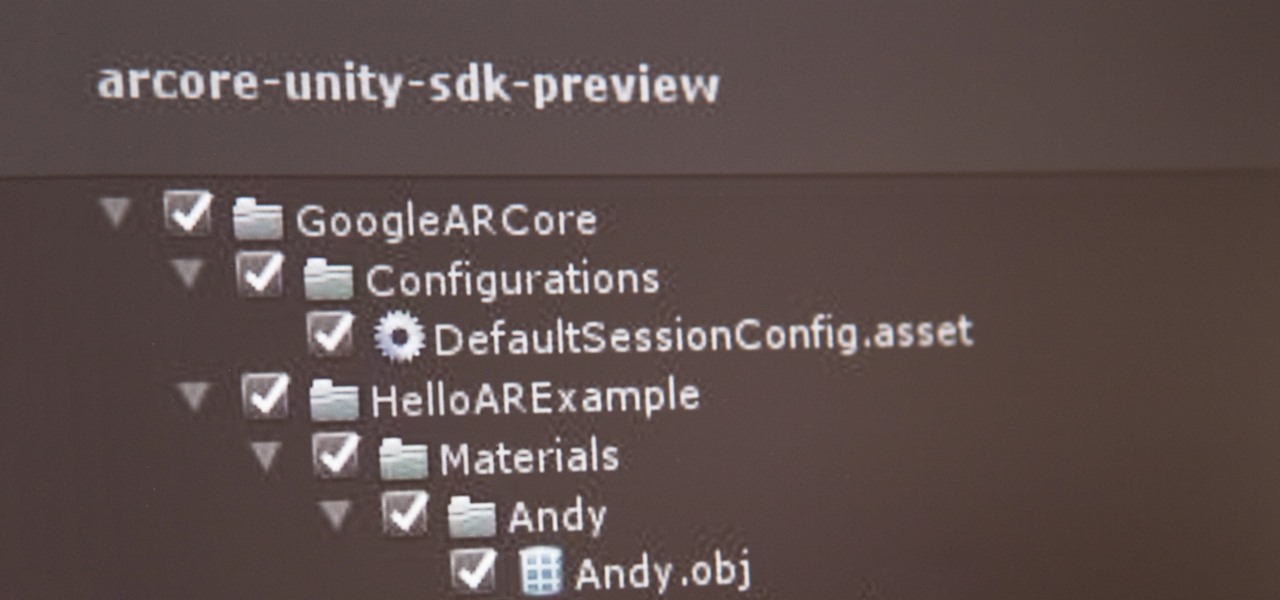
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

What many thought was inevitable, based on recent hints, has been revealed to be in the planning stages: Snapchat is working on smartglasses. The surprising information came out on March 2 in a report that also claims Snap Inc. is planning to release version two of its Spectacles product in the third quarter of 2018.

Oreo, the latest and greatest Android OS, lets you enjoy a ton of new features such as app shortcuts and an improved keyboard. But thanks to a feature that's required of all phones that ship with Android Oreo out of the box, your S9 may be the first Galaxy phone to finally receive timely software updates.

Sure, you just got your Galaxy S8. But now, Samsung came out with their latest and greatest device — the Galaxy S9. While the S8 is still a great device, it's possible that the Galaxy S9 completely outclasses it, almost forcing you to pick it up. It is worth it though? That's a harder question to answer than you may think.

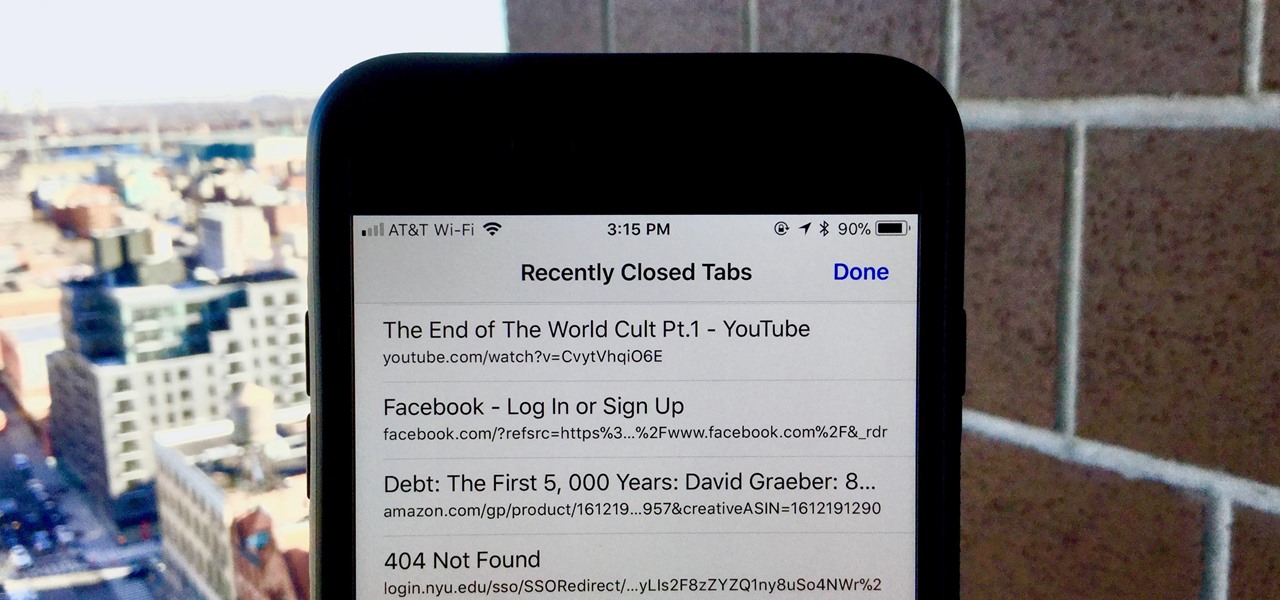
Almost certainly, you've closed out of a webpage that you didn't want to at some point in your iPhone-owning life. Whether you accidentally swiped the tab away or closed it only to need it moments later, tab-regret is just a part of our internet culture. Luckily, Safari on iOS includes an easy way to open recently closed tabs.

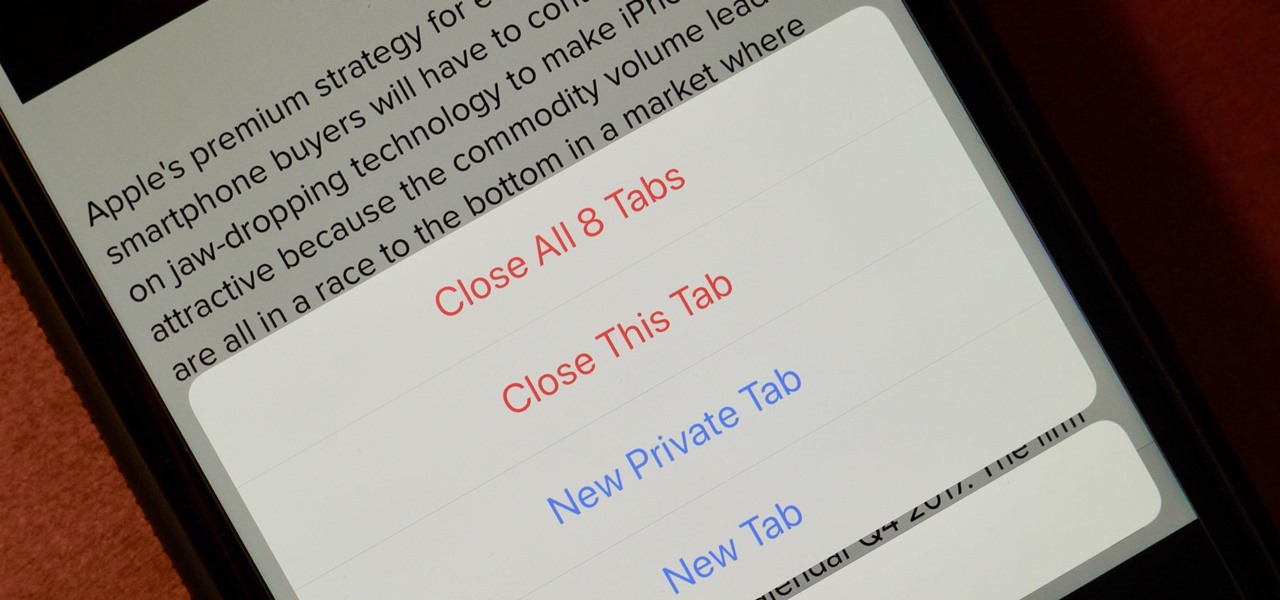
If you're like me, your iPhone has way too many Safari tabs open. Links from other applications open up new tabs automatically, it's too easy to open up new tabs to search, and sometimes you're skittish about closing pages you don't want to forget about. This all creates a massive mess that requires cleaning house, and there's an easy trick to doing just that.

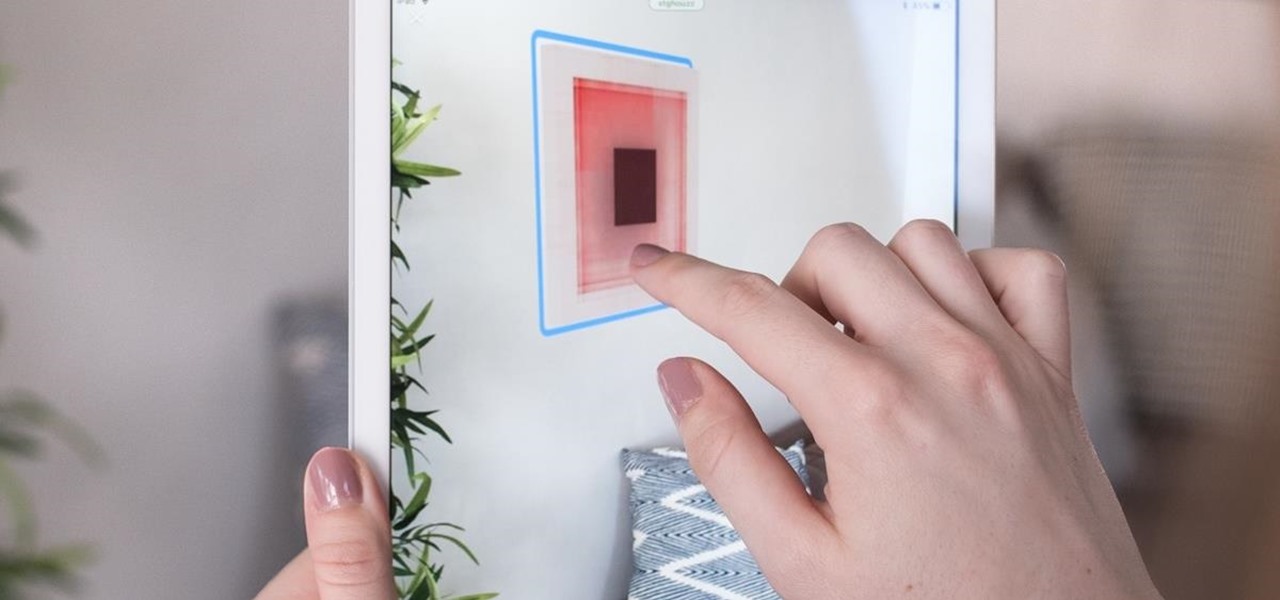
One of the more obvious benefits that vertical surface detection will bring to iPhone and iPad apps with the spring 1.5 update to Apple's ARKit platform is the ability to hang virtual artwork that rests realistically on walls.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

With today's augmented reality experiences, we can see and hear virtual content, but Ultrahaptics wants you to be able to feel those experiences, too.

The Force was awakened in many a household on Christmas morning this year, as evidenced by numerous recipients of newly unwrapped Star Wars: Jedi Challenges systems sharing their first lightsaber battles in augmented reality on social media.

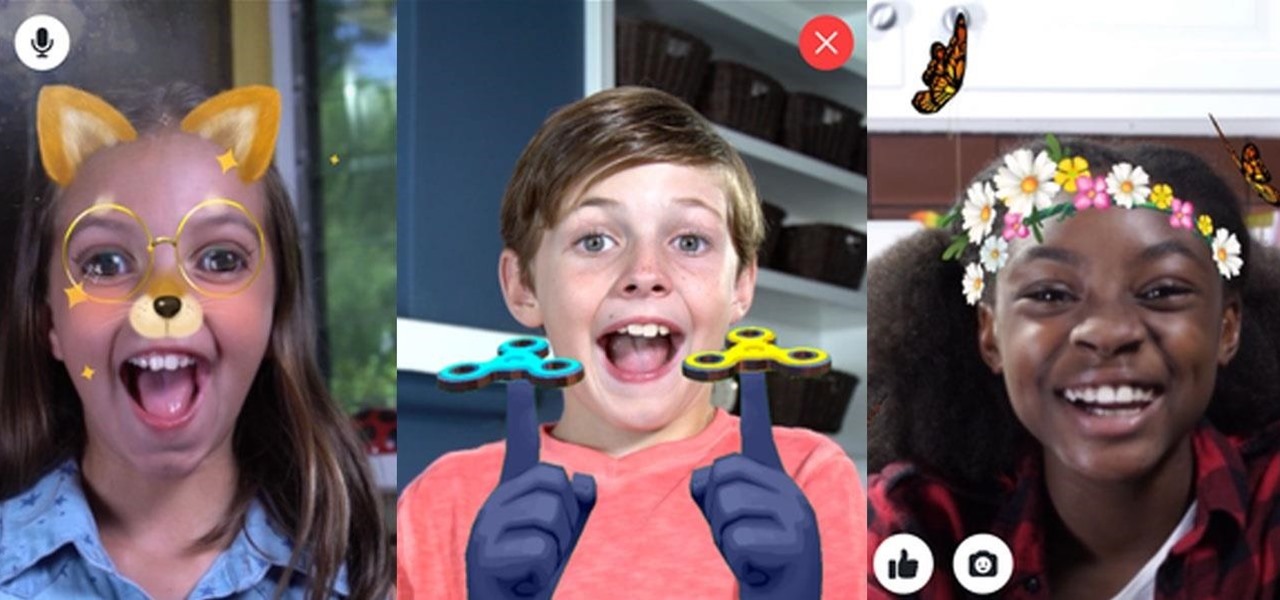
Next to millennials, one of the groups most coveted by brand marketers is "Generation Z," the consumers of tomorrow who were born between 1996 and 2010. On Monday, Facebook established a beachhead with that demographic in the realm of augmented reality by launching Facebook Messenger Kids.

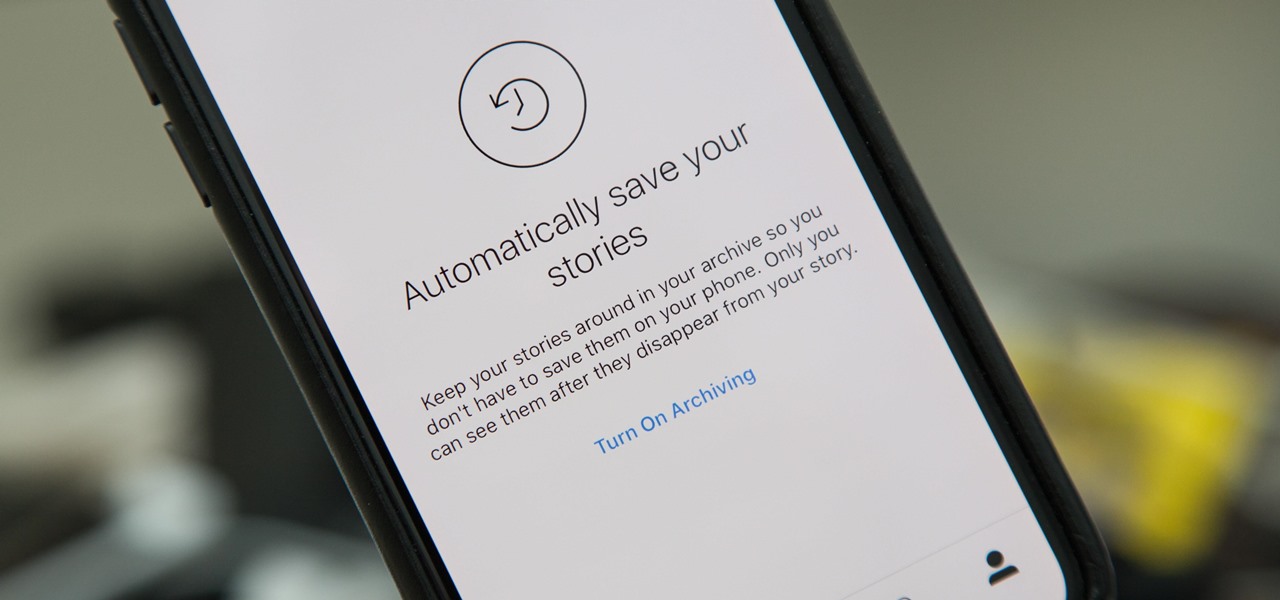
If you're familiar with Instagram Stories, you know that you can download your story to your iPhone or Android device for offline viewing. Those downloaded stories can easily get lost, and Instagram is finally doing something to keep that from happening with a new archive option for stories, similar to the regular posts archive.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

With the raw, visceral feeling of zooming around on the open road, it's easy to get carried away when you're out for a ride on your chopper, super bike, or scooter. This increases your chances of getting lost, plus routes can differ slightly for motorcyclists and cagers, unbeknownst to most drivers. Luckily, Waze has rolled out a feature that caters specifically to bikers.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

With the holidays fast approaching, our smartphones are more important than ever — keeping in constant contact with family, organizing trips and gatherings, and online shopping is only a taste of what we put our smartphones through. All of that means a big strain on your smartphone's battery. That's why portable chargers are so necessary, and what better time to pick one up than on Black Friday.