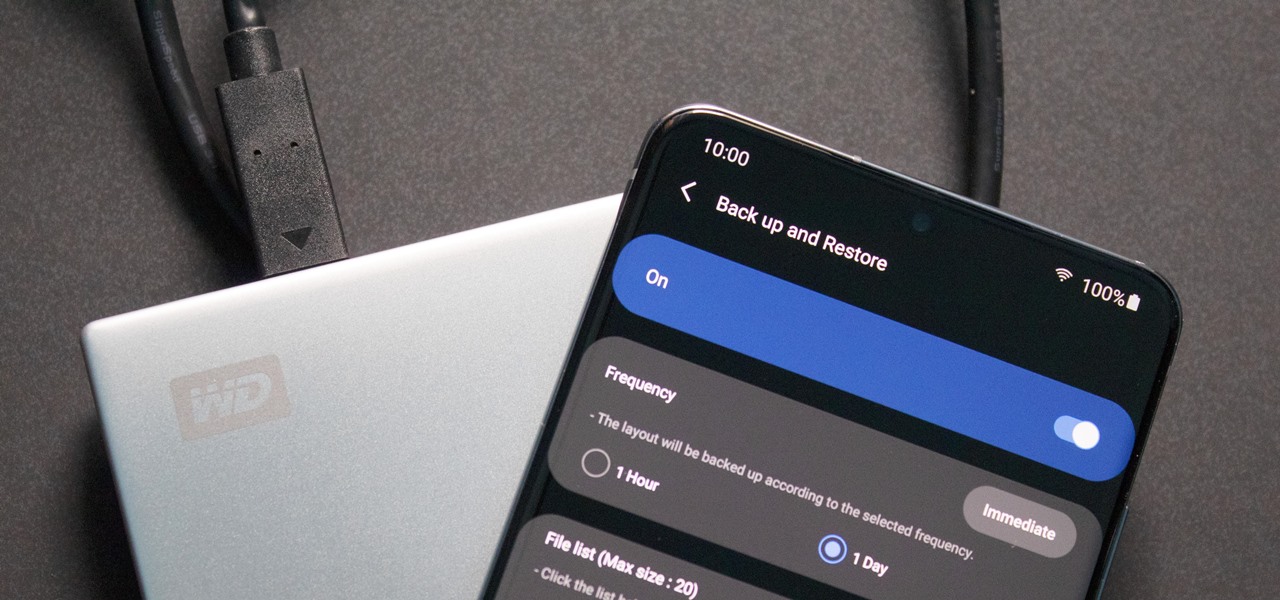
In the past, if you upgraded to a new Galaxy or if you had to factory reset your existing one to fix an issue, you had to restore your home screen layout manually. Your wallpaper, widgets, icon placement, and launcher settings were all dependent on you to be put back in their place. Thankfully, this isn't an issue anymore.
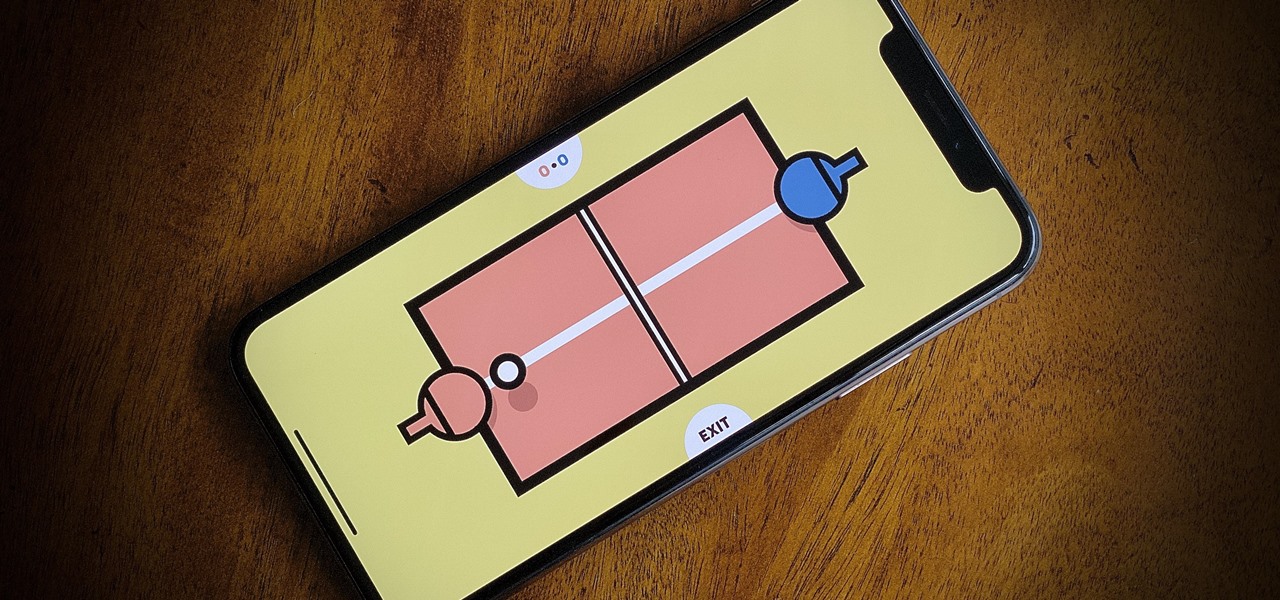
If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.
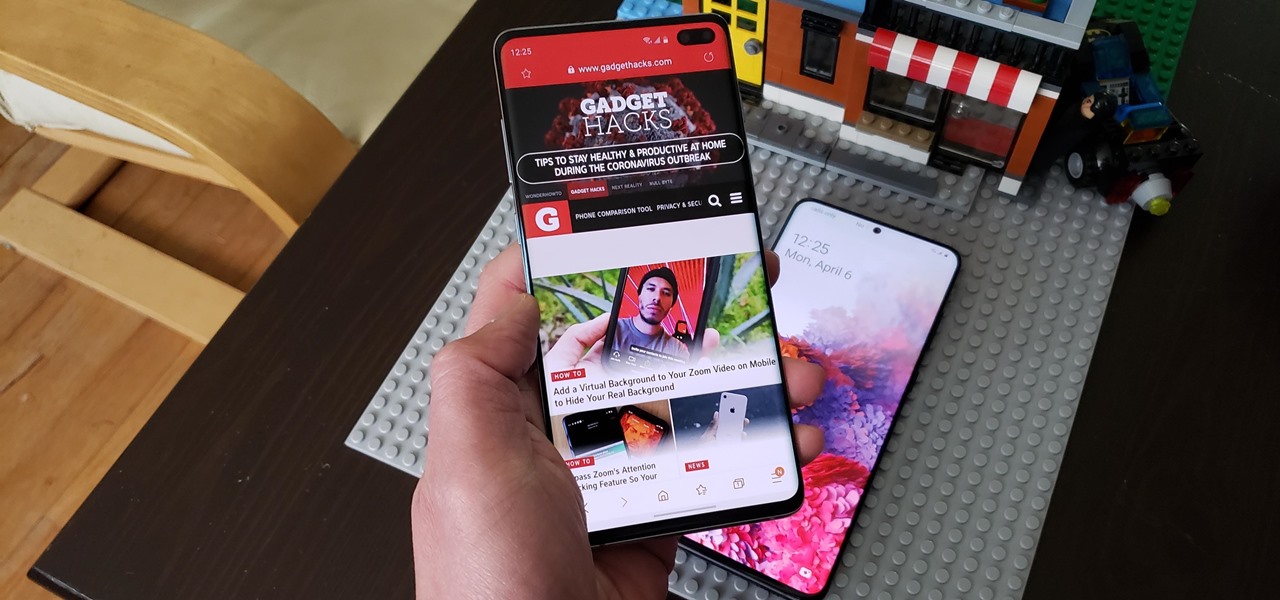
We're all feeling the impact of the economic recession underway due to the coronavirus. With millions of Americans filing for unemployment benefits, now more than ever should we focus on the best deal rather than the best model. And in no industry is that more evident than smartphones.
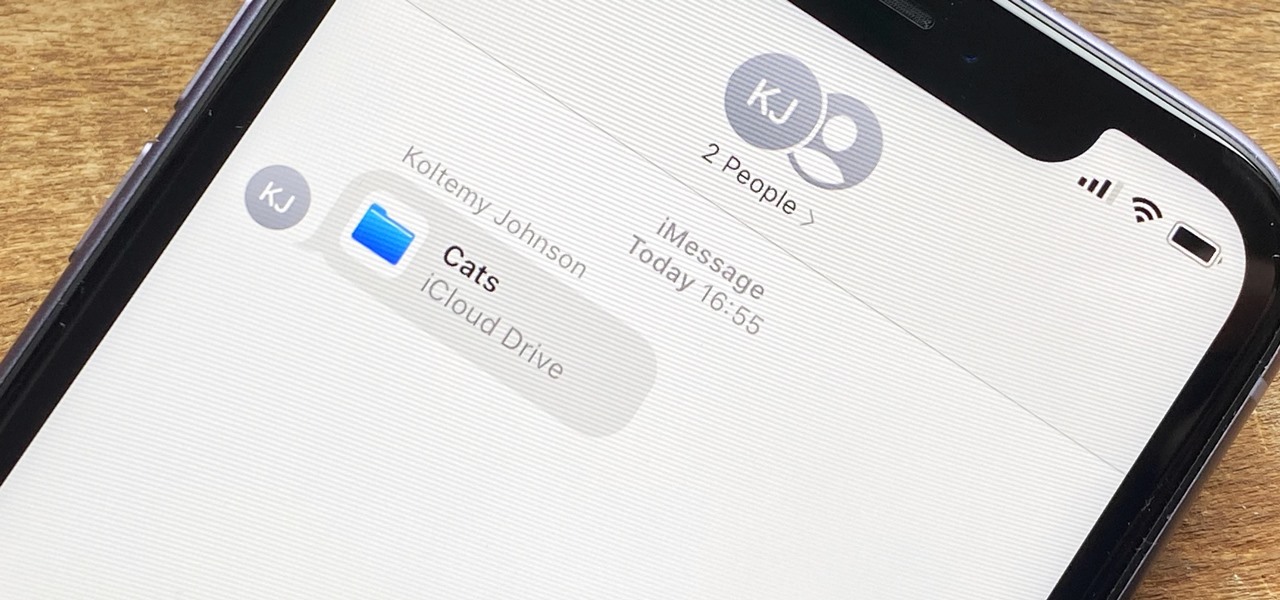
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

As a native of Alabama, Apple CEO Tim Cook has a special place in his heart for the state. He also empathizes with the struggles that African-Americans have historically faced in the state, particularly during the 1950s and '60s civil rights era.

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

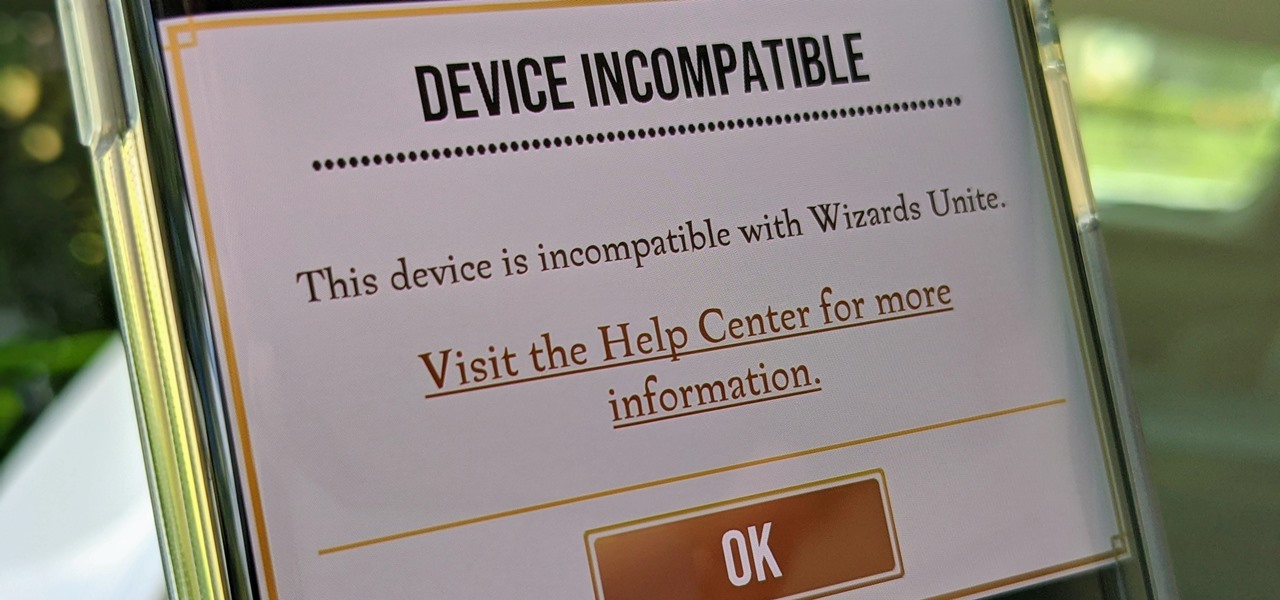
Harry Potter: Wizards Unite has gained quite the fan base since its launch, but not without a few bumps along the way. Niantic, the game's developer, has a long-running history with trying to block all root users on Android. The methods will vary for each game, but this time around with Wizards Unite, they appear to have a new detection feature at play from the recent 2.9.0 update. Let's find out what's going on.

The top five apps of the 2010s were all social media apps of some kind, and the fact that's not surprising to you says a lot. We may use them for other reasons here and there, but our phones are social media machines at their cores. The thing is, some make better machines than others.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

It seems like each day our phones become more integrated into our lives. School, work, shopping — so many tasks either require a phone or heavily benefit from one. But our phones are a double-edged sword that can easily distract us and harm our mental health as well.

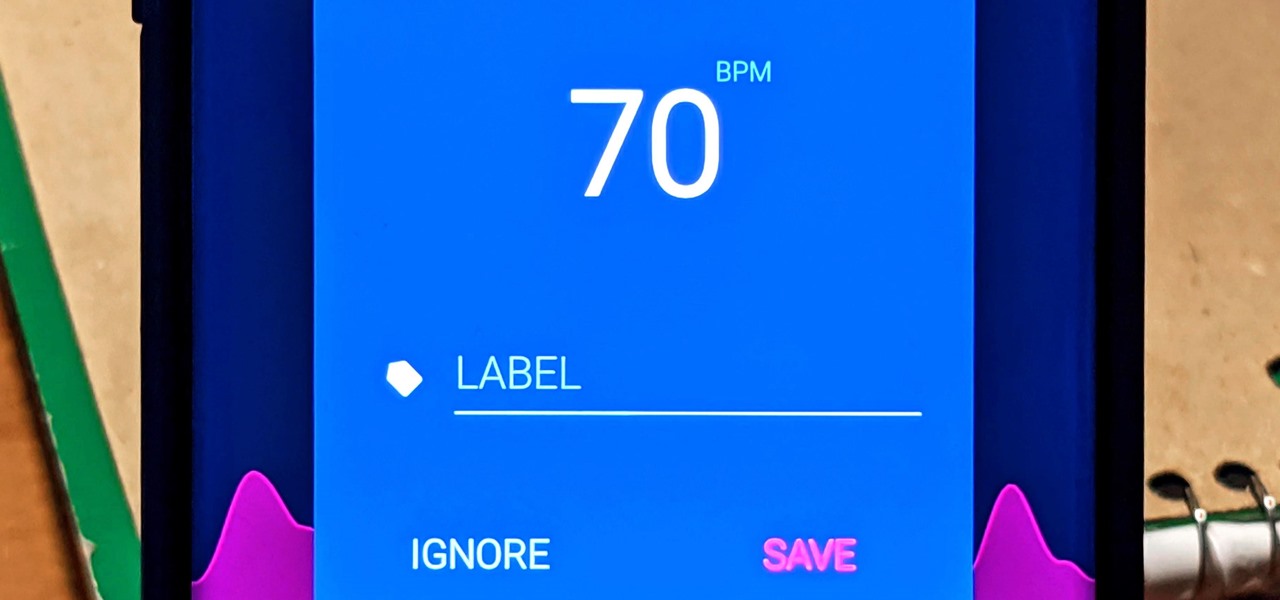
With the rise of smartwatches and wearables, you'd almost expect to need one to get a heart rate reading. While these devices can be helpful, not everyone has or wants to wear a gadget all the time to track their BPM. Luckily, when you combine Google Fit with a popular third-party heart rate measuring app, it will make things easy for you.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

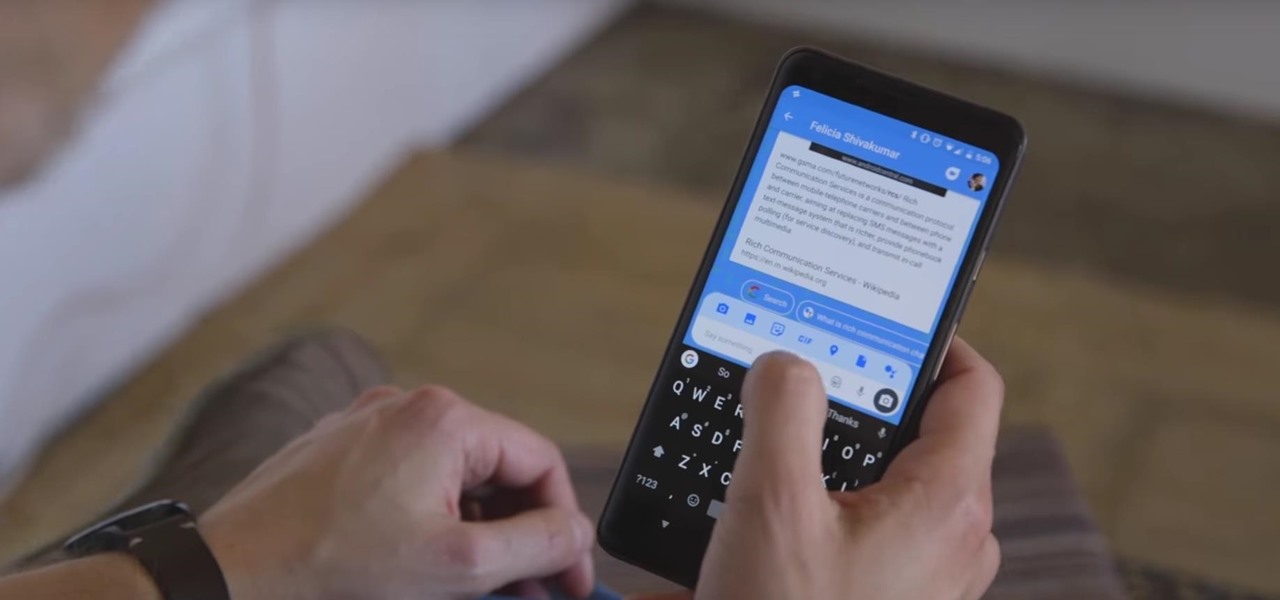
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SMS or MMS. The only thing is, your carrier needs to support RCS-UP to use the feature. Thankfully, the list is growing.

If reaching up to access Camera controls like the flash, HDR, and timer wasn't bad enough, it's gotten a lot more tedious on recent iPhones like the X, XS, and 11 series thanks to their tall displays. If you have a jailbroken iPhone, however, you can easily fix this issue using a free tweak.

Smartglasses from Apple have become the holy grail of augmented reality, and 2020 has been the rumored time horizon for the product's arrival for the past two years. The latest analyst report sheds more light on its potential debut next year.

The 15-year-old star of the 1980s-inspired hit series Stranger Things, Millie Bobby Brown, may have (spoiler alert) lost all her powers as the character "Eleven," but in the real world, she still has augmented reality in her arsenal.

XDA recently reported on a leaked version of the upcoming Pixel 4's camera app. By testing the app, they were able to find upcoming Pixel 4 features like a new Night Sight mode that can photograph stars. Well that leaked version has leaked itself, so now you can install it on your own Pixel phone.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

In iOS 13, Apple is taking the Reminders app more seriously. With its long list of helpful new changes, the app finally stacks up to other task managers like Todoist or Wunderlist. One of the changes is small but mighty — the ability to add custom icons to lists. Doing so lets you personalize each collection of reminders to your liking and can help you identify lists with just a glance.

As you already know, the Galaxy Note 10 and 10+ have gotten rid of the beloved audio jack (RIP). Fortunately, it has never been a better time to switch to wireless. There are Bluetooth headphones and earbuds for every budget and every need.

The latest immersive production from Magic Leap Studios finally got its debut on Monday at Siggraph, during which the company also released the app to the general public, so we took it for a spin.

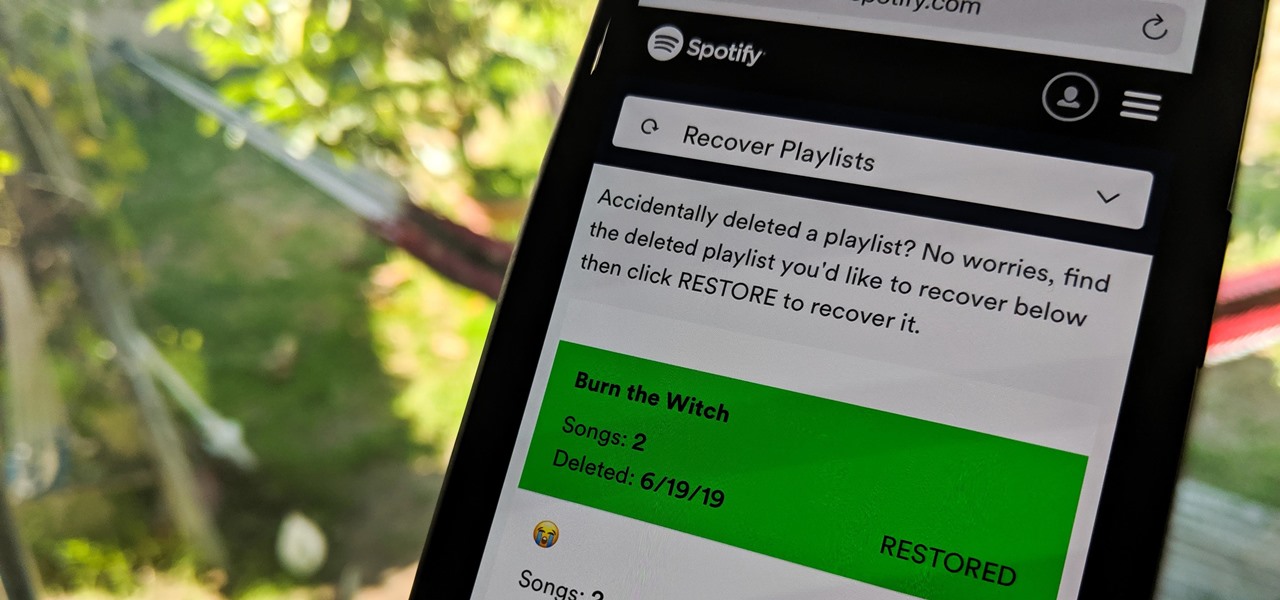
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.

Whether you're used to 3D Touch or Haptic Touch, deleting and rearranging apps and folders on your iPhone is a little bit different in iOS 13.

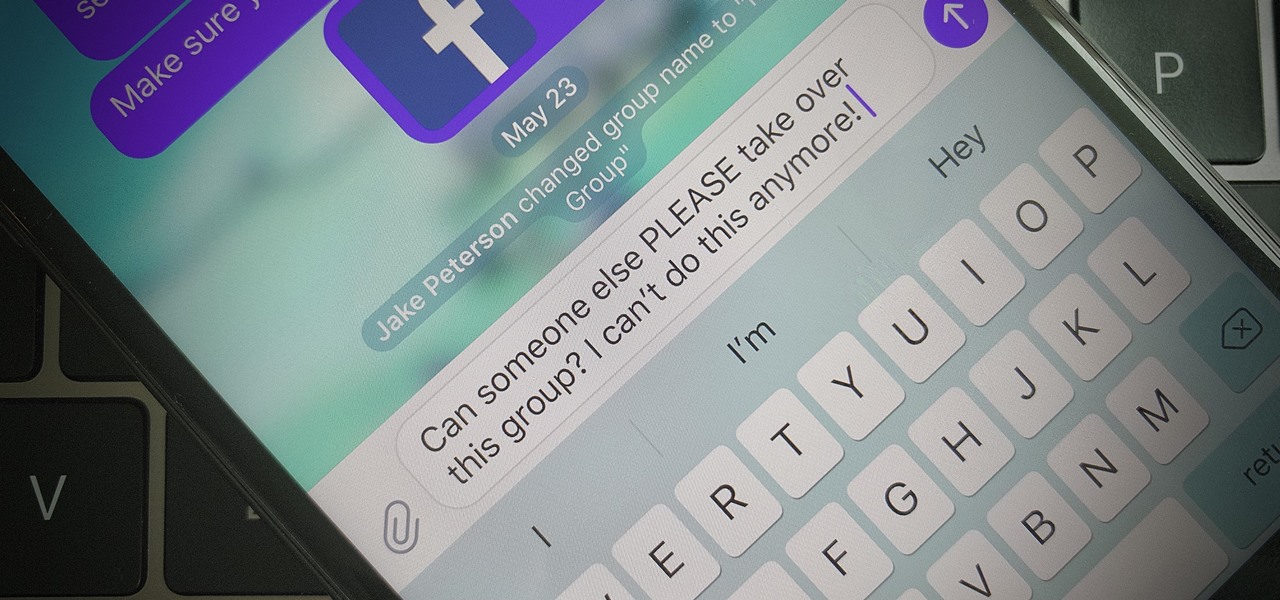
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling overwhelmed with administrative responsibilities, why not pass on that burden to another member of the Telegram group?

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

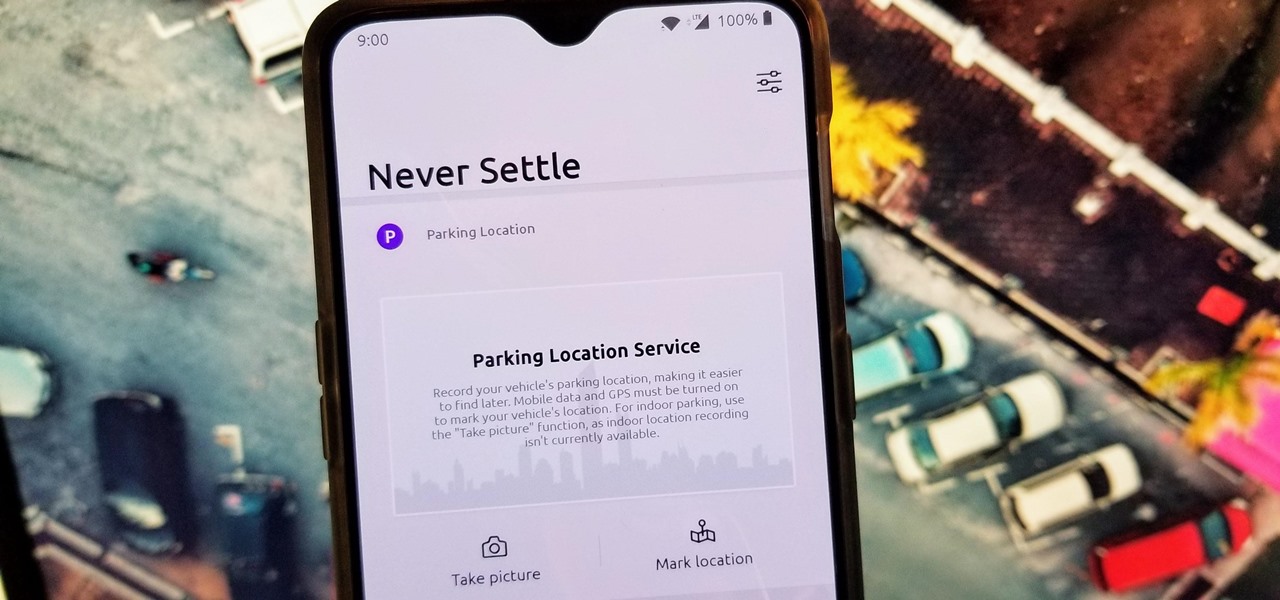
There once was a time before smartphones when you had to actually remember where you parked your vehicle. This really sucked when visiting a location with a large parking lot — they even made a whole Seinfeld episode about it. But now you can just tap a button to solve this problem. Who says we're not living in the future?

Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beautiful display.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

The story of Meta and its Meta 2 augmented reality headset isn't over, there's a new development that could impact its ultimate fate.

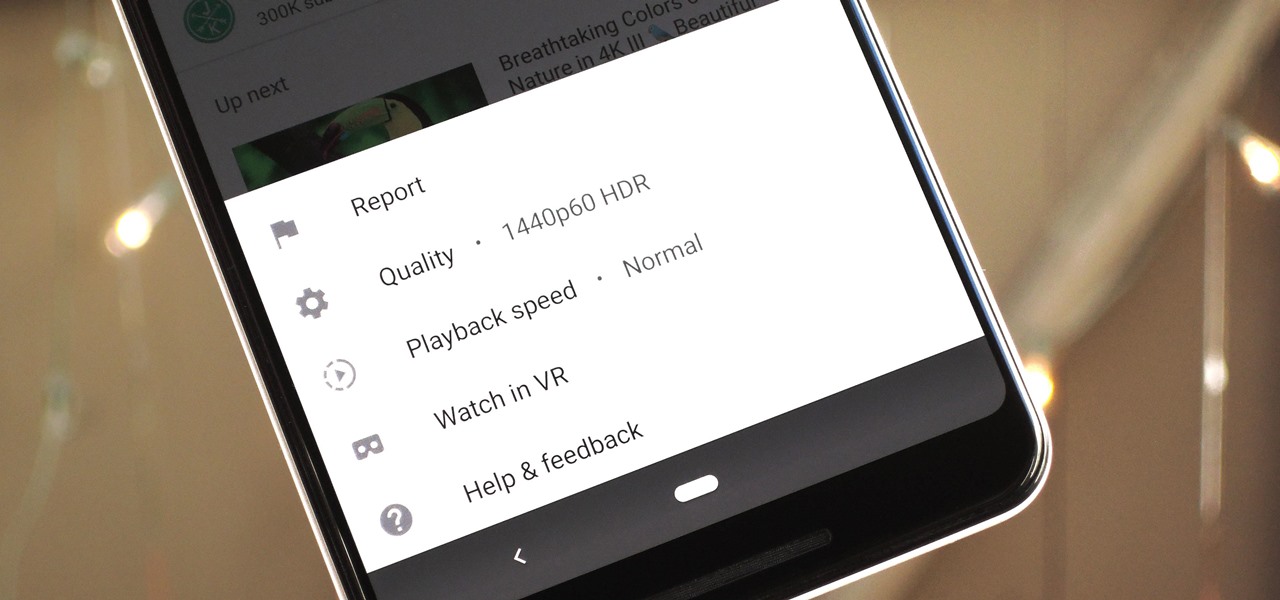
The YouTube app will default to 480p playback when you first open a video. It's supposed to switch to your screen resolution a few seconds in, but this isn't always the case. The regular YouTube app doesn't let you change this behavior, but like most things with Android, there is still a way.

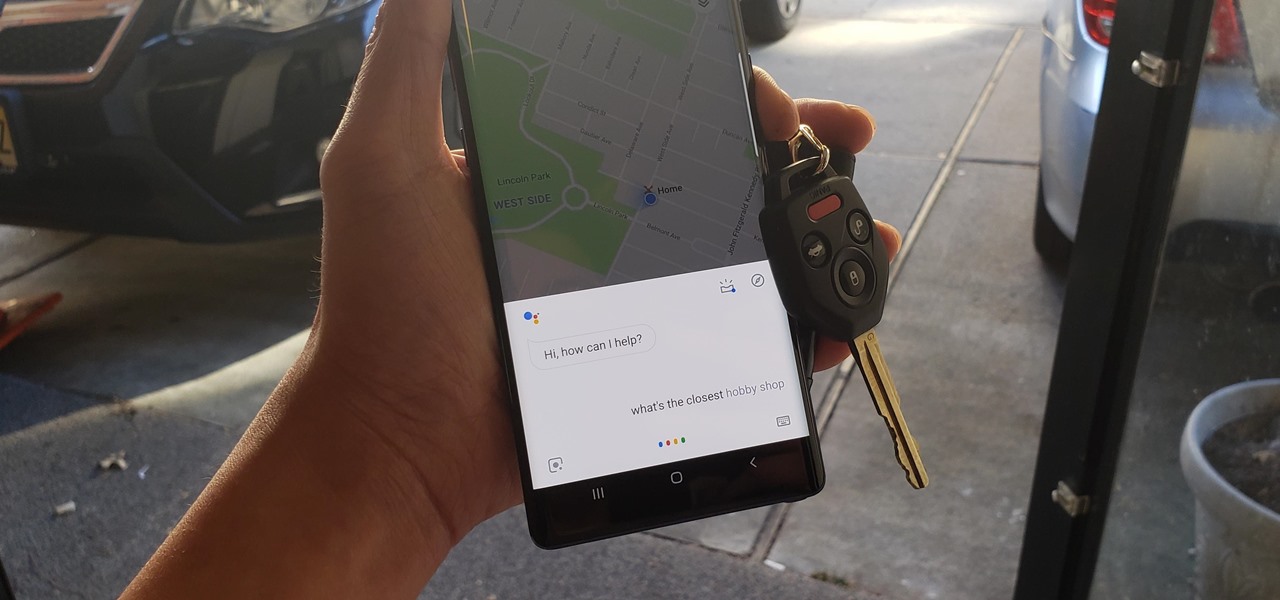
Millions depend on Google Maps for directions, and it's easy to see why. The app comes with tons of features like offline navigation, location sharing, and more. Google is far from done, however, and continually improves upon its navigation app to make it even more efficient and safer to use.

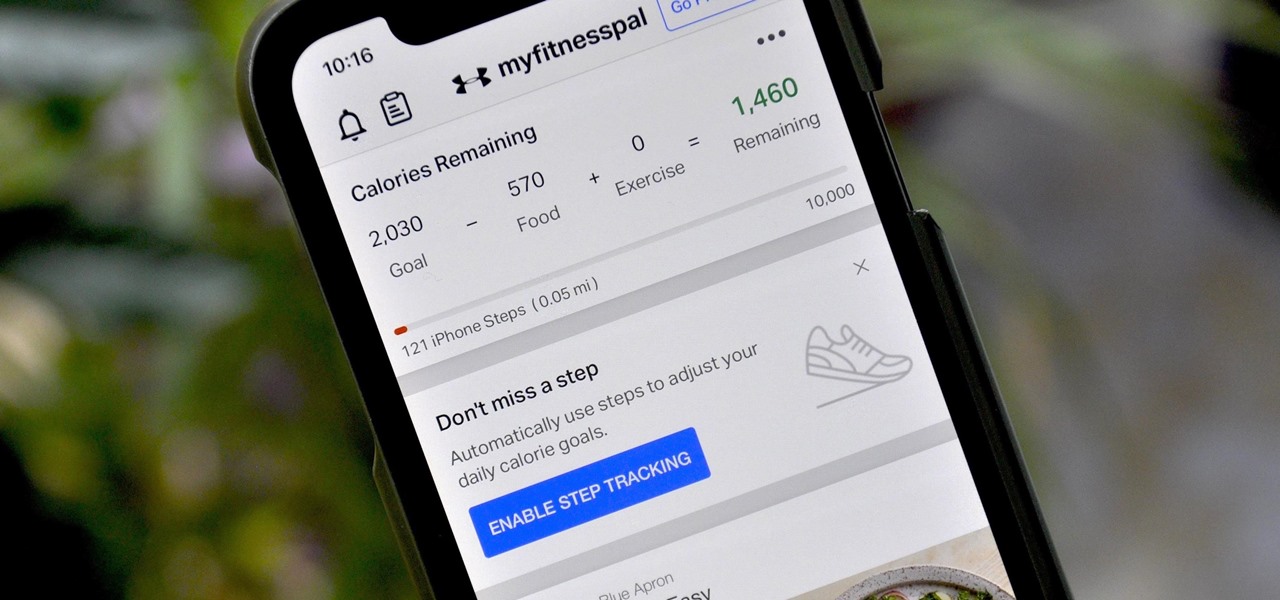
If you're new to MyFitnessPal, it might seem daunting. The app is way more than just a calorie counter, but that's because getting fit is just as much about changing your lifestyle as it is about watching what you eat. So don't let it overwhelm you — there are just a handful of tips you should know to hit the ground running.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

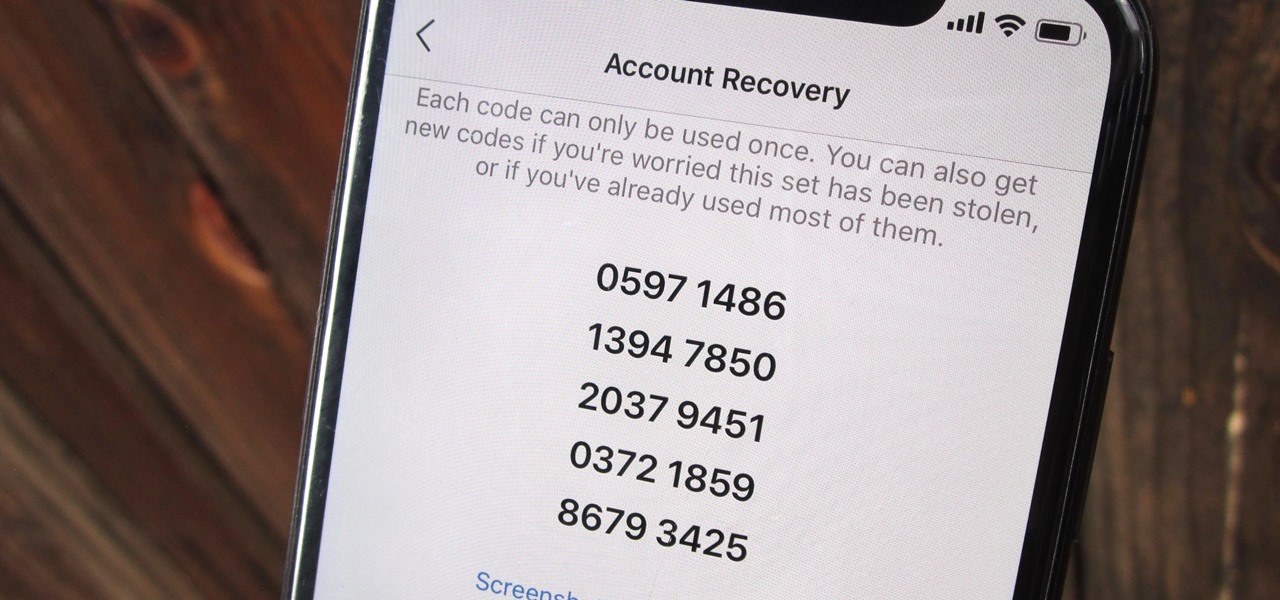
Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

On Monday, with just days left before Christmas, Lowe's dropped a surprise augmented reality treat in everyone's lap: a brand new Magic Leap One app.

With the rapid demise of the 3.5 mm headphone jack, Bluetooth is fast becoming our best option for universal audio. The problem is, with over a decade of it being a standard component, many of us still own a reliable pair of wired headphones that we don't want to gather dust. Well with one tool, you can have your cake and eat it, too.