Hands down, chips and dip are the best entertainment foods to ever exist. This fact can be confirmed in an instant by any grocery shopper strolling down the chip isle on Super Bowl Sunday or New Year's Eve. However, you may want to hold off on buying those standard salsas or dips at the store—especially if you own a food processor.

Whatever you want to call it for now—Android Nutella, Android Nougat, or Android 7.0—the upcoming "N" release of Android will surely bring in tons of new features and functionality. We know it will be named after a dessert, and we know that Google uses an alphabetical naming system, so something starting with "N" is next in line after Android 6.0 Marshmallow.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Okay, so you finally got around to rooting your Android device—now what? Well, to get the most out of your Superuser status, you'll need to find some good root apps, which will allow you to easily add features, reduce battery drain, remove ads, and much more.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

The way in which cooking can be used to both illustrate science and create a beautiful bite of food is fascinating to me. And emulsions, the results of combining liquid fat and water, are a fantastic example of science in harmony with great cooking.

The software released in the 2015 iterations of the Samsung Galaxy line of devices—the S6, S6 Active, S6 Edge, S6 Edge+, and Note 5—have some pretty neat camera features that give these devices arguably the best smartphone camera on the market today.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

My daughter moved into her first apartment last year, a huge rite of passage in any young person's life. With a mother and two grandmothers who are good cooks (to say the least, in the case of the latter), it's not surprising that she turned to us for some advice about how to improve her own skills in the kitchen. Without question, the single best piece of advice we have given her is to employ mise en place each and every time she prepares a meal.

The Microsoft Surface has been the go-to device for many professional artists since its initial release back in 2012. Since then, the Surface line has continued to offer customers a portable, high-powered machine that's a near perfect value for both casual and professional artists. And the Surface Book is its best model yet—a full laptop convertible with a detachable screen and a dedicated GPU.

Smartphones have been a hot button issue around school campuses for several years now—some schools allow them, others confiscate them on sight. But the fact of the matter is, when used correctly, a smartphone can be just as much of a learning tool as a textbook or school-issued laptop.

If you open your refrigerator door and find leftovers there, then you are fortunate—even if you don't realize it right away. Leftovers are the ultimate budget hack because they maximize the value of your meals; and it's a smart way to save money while making the most of your food purchases.

Oven space is scarce on that fated fourth Thursday of November. Even if you can find a spare space for pumpkin pie on the bottom shelf, you risk turkey drippings overflowing from above and ruining your beautiful dessert — not to mention a burnt crust from different temperature requirements. The bottom line is: oven real estate is valuable, and it's tough to multitask cooking for Thanksgiving when every dish requires baking or roasting.

If I could only eat one food for the rest of my life, it would definitely be potatoes. In fact, when I recently saw The Martian, I didn't feel that badly for Matt Damon. I mean, sure... he was stranded on a hostile planet, millions of miles from home. But he got to eat potatoes all the time! Pretty fair trade, if you ask me.

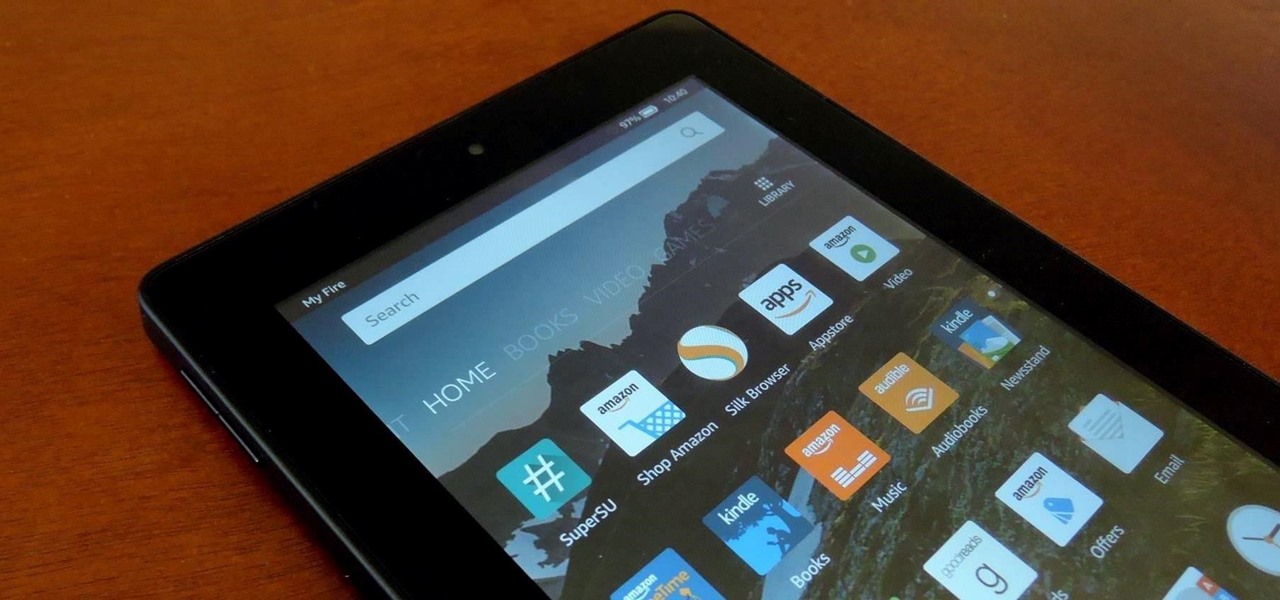
Amazon is slowly trying to gain as much influence in the tech world as it has in the consumer market, and with the Amazon Fire HD 7, they have their eyes set on taking on the "budget tablet" space.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

In 1987, two brothers, Thomas and John Kroll, began work on an image editing software, which was eventually acquired in 1988 and released to the world in 1990 by Adobe. That software was Photoshop 1.0, initially exclusive for the Macintosh platform. Over the years, Photoshop became a great wizard of image editing and gained application rockstar status.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

Taste is certainly relative. When you look at Central American architecture and notice all of the bright pastel colors, then move just a thousand or so miles to the north and see that buildings in the United States are mostly painted in earth tones, this becomes abundantly clear. Imagine if you were to switch hemispheres altogether—what would you see in East Asia?

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

I may be in the minority when I say this, but I love leftovers. Whenever I'm cooking for less people than the recipe calls for, I cook the full yield anyway. And when I go to a restaurant, I order whatever I want—regardless of how much I can actually eat in one sitting.

Apple's special September event just wrapped up with the company unveiling several new products, including the iPhone 6S, iPhone 6S Plus, iPad Pro, and the new Apple TV set-top box. In addition to hardware, Apple also discussed a couple of its latest software platforms, iOS 9 and watchOS 2. Check out everything that Apple unveiled below.

Ah, the joys of bottomless brunch. Paying a flat rate for endless mimosas while having a long gossip over eggs Benedict is exactly how many of us love to spend our Saturdays. However, in practice, this isn't the sophisticated affair we all like to imagine. After refill number four we sway in our chair, doze off into our porridge, and end up tipping 50% because math is too hard. In short, not a very successful brunch.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

As our lives grow busier, we get secluded in our indoor activities, consuming all types of fatty junk food and what not. Obesity is a very obvious yet unfortunate outcome of our unhealthy living standards. With it comes the predictable rush towards efforts to lose weight. Consequently, we have designed hundreds if not thousands of ways to lose fat and grow slimmer. To ease out your choice of ways, here is a list of the best ways to lose stomach fat. Step 1: Don't Eat Sugar

When most people think of "gaming computers," they're probably thinking of Windows-based PCs. They offer a huge variety of devices with better equipped software and hardware for a cheaper price, and there are more available games than there are for OS X-based systems.

Your freezer is no one-trick pony. While it does excel at keeping your food fresh for as long as possible, it has a few secret talents it doesn't want you to know about. Like making soda slushies and pyro-friendly smoke mix, as well as reviving dead hard drives. Even better—it can help you do laundry.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

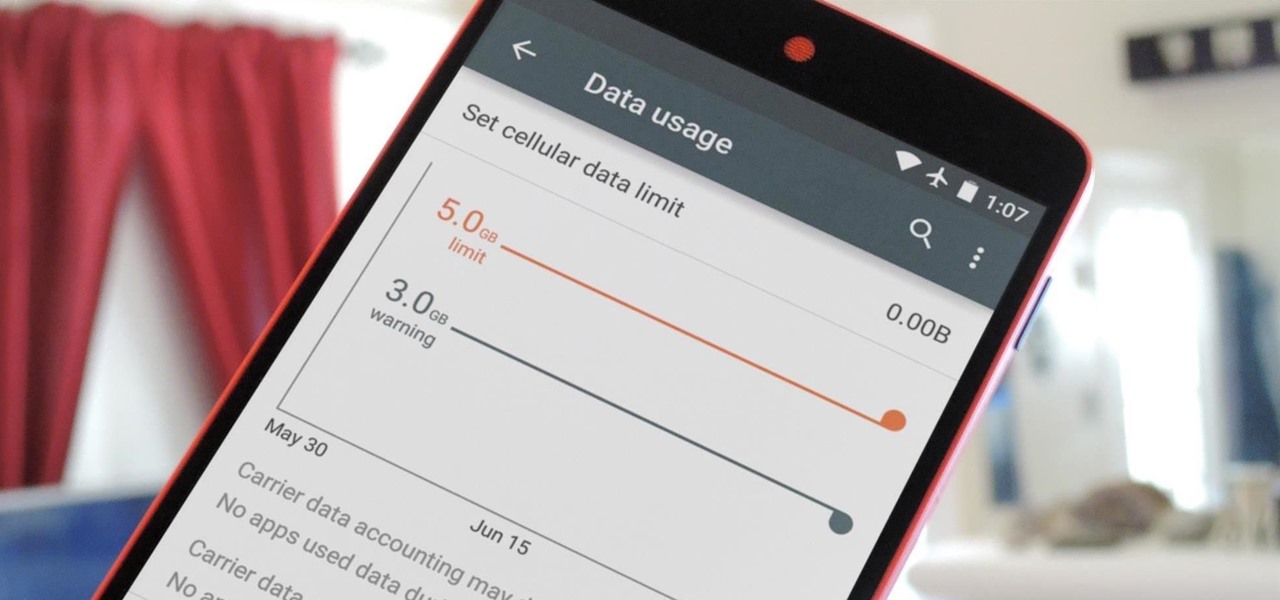
Ever watched Netflix on your phone only to realize an hour later that you forgot to turn Wi-Fi on? That's a whole lot of data used.

Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new features you need to know about on the new iOS 9 for iPad, iPhone, and iPod touch.

Summer's coming, and that means burger season. Okay, never mind... every season is burger season. Burgers are universally loved; they're the one meal you can find at numerous fast food shacks and haute cuisine spots.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receiver, be it tap-and-pay with Google Wallet, a file transfer via Android Beam, or a Tasker profile triggered by a specific NFC tag.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...