Tired of the Instagram wave? If you're sick of having to view the world through low-contrast and sepia-toned filters, there's a way to get them back to how they're supposed to look, and it's called Normalize, which undoes the magic filtering that Instagram and similar photo filter apps provide. The process of un-Instagramming your (or anyone else's) photos with Normalize is perhaps easier than Instagramming them in the first place. All you need to do is copy and paste them into the app and wa...

How do you make a 1950 Studebaker even cooler? By installing an iPod Nano in the dashboard, of course! The folks over at MAYA Design hacked their way to a touch-controlled sound system with this project they've dubbed the "Nano-Baker" (or "Stude-iPod") using a pair of Apple ear buds, a USB cable, a voltage regulator and a set of speakers. Here's how they pulled it off.

I've never really liked to type on a flat or low keyboard. Even the small flip-up stands underneath most keyboards were not good enough for me, as those little legs aren't usually more than 2 or 3 centimeters high. I'd like a minimum of 5 cm, so I decided to make this keyboard base for myself. Aside from giving me the right height and angle, this DIY keyboard base also features LEDs that light up my monitor, the table, and gives a nice background to my desktop. It's even got a built-in stand ...

Linux is generally a pretty stable OS, but occasionally things happen. However, as long as your keyboard has a SysRq key, you'll never need to worry about freezes again.

Fabulous and creamy, make this scrumptious low-country carb stew. Follow along as Paula Deen shows you how to make it. This cooking how-to video is part of Paula's Home Cooking show hosted by Jamie Deen, Paula Deen. Paula Deen, owner of Lady and Sons, a famous Savannah restaurant, is Food Network's resident southern chef. Step inside her kitchen and discover delicious food that's both uncomplicated and comforting, like this recipe. Watch how easy this low-country crab stew is to prepare and c...

In this how-to video, you will learn how to tune a guitar with the help of an online tuner. You will need a guitar. Listen to the low e string note being played and tune your guitar's low e to that tuning. Listen to the a note being played and tune the a string accordingly. Listen to the d string open note being played and tune the d string. Listen to the g string open note being played and tune your g string accordingly. Listen to the b note being played and tune the b string accordingly. La...

Want greener and healthier grass around your home? With some care and a little work, you could have the greenest landscape in the county. Lowe's has the tips you need in this five-part video series on lawn maintenance.

You can never have too much mac & cheese! In addition to her fabulous creamy stovetop recipe, Betty unveils her fabulously gooey baked recipe in this tutorial. This dish has a delicious sharp cheddar bite to it and a crispy crustiness that is to die for! Impress your friends with this very easy and very tasty recipe.

Maybe you get bored with plain old mac & cheese once in a while. Why not spice it up with a bit of an Italian flair? Betty adds a hint of tomato to your traditional family dish; try it out! You won't be disappointed.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Watch this video tutorial from the Polish Guy to see how to polish a chrome faucet fixture. In this demonstration we use a Faucet & Fixture Care Kit that includes Simichrome and Flitz Faucet & Fixture Wax to polish a chrome bath tub faucet spout.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about capturing digital photos with the Meade Deep Sky Imager. The universe is out there, and you can take a picture of it.

Inserting a tampon is a rite of passage for every teenage girl, so it's important to know how to insert a tampon the right way. It could seem tricky at first, but after trying several times, tampon insertion becomes as easy as putting on a glove. It just takes practice, & this video will show you the animated process. The key is to RELAX! Worrying about it may make you tense, making insertion even harder.

Learn how to do downhill ski series exercises. Presented by Real Jock Gay Fitness Health & Life. Benefits

During Snap Inc.'s quarterly earnings report, released on Tuesday, the company disclosed that it snagged a revenue total of $230.8 million for the first quarter of 2018, an increase of 54% compared to last year, largely fueled by its augmented reality offerings and other advertising products.

It might seem like an inconvenience but it is important to take the time to find out what has caused your oil light to come one in your car. You may just be low on oil or you may have a more serious problem but ignoring the warning will only lead to further damage.

In this instructional tutorial hosted by Robert Renman, get a thick, distorted sound on your guitar without cranking it to 11. Robert uses a Maxon SD-9 distortion pedal, a Zonkin Yellow Screamer and a blueSky Reverberator, paired with a Marshall Class 5 amp to make it all come together.

Are you on a low-salt diet and need some healthy recipes that are friendly on your taste buds and wallet? This superb video serves up an easy and delicious recipe that will please everyone, whether or not the doctor has advised them to cut down on the sodium. The tutorial, one in a fantastic and free video series, offers excellent tips on how to properly cook your rice, as well as how to dress it up without damaging your health.

Here is a tutorial for the type of low-fundamental throat singing I did in my previous "harmonic/throat singing.

Learn the correct position for playing defense on the low post as a basketball player.

One of iCloud Photo's biggest perks is its ability to store large video files taken with your iPhone, so you can fill up your iPhone's storage with other items. That said, when you play back those videos, you may not be watching the footage in its original quality. Instead, they may be low-res versions. To view the high-quality originals — or to make sure that's what you see — just follow this trick.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

The nemesis of music streamers is data caps, cell phone or otherwise. Restricting monthly data and forcing users to decide between quantity and quality of music has had audiophiles tearing their hair out since streaming toppled the iPod. While the problem regarding music quality seems difficult to tackle, it's far from impossible.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

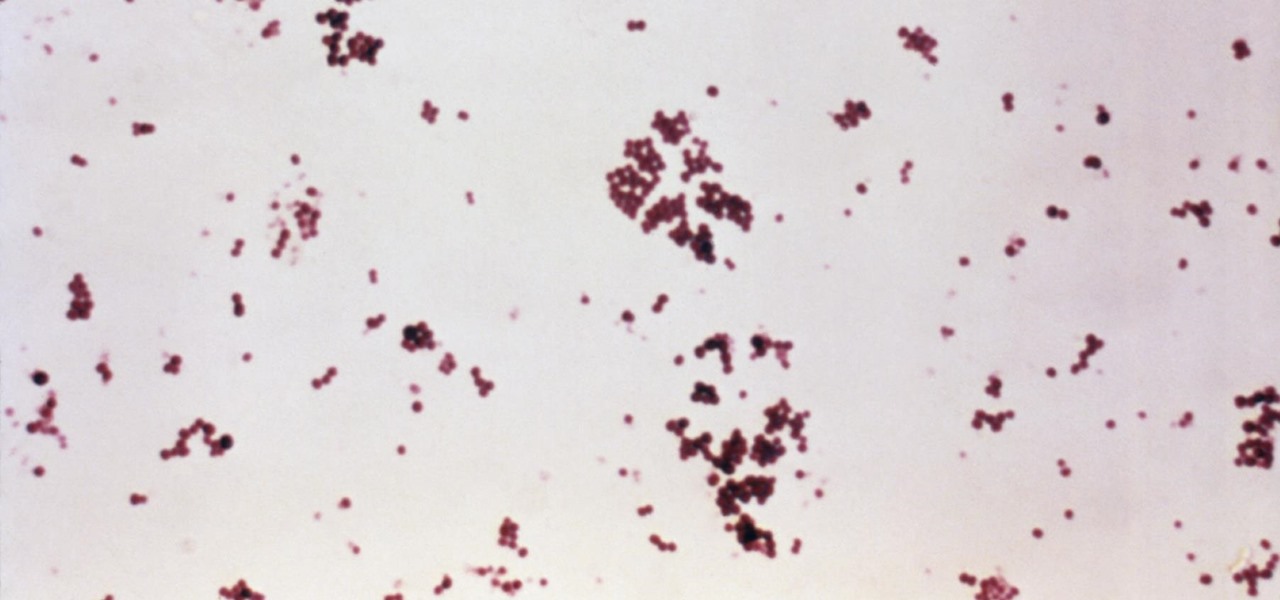
Infections with group A streptococcus, like Streptococcus pyogenes, claim over a half million lives a year globally, with about 163,000 due to invasive strep infections, like flesh-eating necrotizing fasciitis and streptococcal toxic shock syndrome.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

The new iOS 11 was just released by Apple, and you can install it right now. Overall, it's got some great features, but how does it fare battery-wise on your iPhone? And how can you increase daily battery life for more juice and less charging every day?

Nineteen days ago, several hundred people could have been exposed by a traveler with measles in Nova Scotia, Canada. The next day, someone flying from Minnesota to Nebraska may have spread the measles to other passengers. A couple weeks ago, it's possible that a man and his six-month old child spread the measles in several Seattle-based locations. Authorities are trying to locate persons who may have been in contact with these people. None of the persons with measles were vaccinated. Why?

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

Cats give us so much—companionship, loyalty, love... and now the bird flu. Several weeks ago, a veterinarian from the Animal Care Centers of New York City's Manhattan shelter caught H7N2 from a sick cat. According to a press release from the NYC Health Department on December 22, "The illness was mild, short-lived, and has resolved." This isn't the first time cats have passed infections on to humans, but it is the first time they passed on the bird flu—avian flu H7N2, to be exact.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

Great news: you don't have to give up grains if you're avoiding gluten.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Common knowledge is a funny thing: it represents a majority's opinion on a particular subject and somehow makes that opinion fact. If that 'fact' goes unopposed and unchallenged, then it is passed on and preserved from one generation to the next—regardless of whether it is true or not.

The beauty of a grilled cheese sandwich is that even a mediocre one still tastes pretty good (I find the same is true with pizza). However, chefs and cooking pros have come up with some great tricks that will turn a regular grilled cheese sandwich into something sublime.

Lenovo brought out the big guns for CES 2014, with the Vibe Z showcased as the Chinese company's' first foray into the LTE smartphone space. Slated for a February release, the ultra-thin and extremely light smartphone will certainly be in the running for top smartphones of this very new year. Photo via CNET