Anuja and Hetal from Show Me the Curry! teaches how to make a vegetarian Indian dum aloo. 2 lbs. Baby Potatoes, boiled and peeled, 2 Tbsp Oil, 1 inch piece Cinnamon Stick, 1 Bay Leaf, 6 Whole Cloves, 1/4 tsp. Asafoetida, 2 tsp. Ginger, minced, Salt, Red Chili Powder, 1 tsp. Roasted Aniseed Powder (Star Anise), 2 tsp. Roasted Coriander Powder, 1 tbsp. Paprika, 1 Cup Yogurt, 1 Cup Water, Cilantro and Ginger (Julienned, cut into matchsticks); for garnishing. Preheat oven to 400 degrees Fahrenhei...

If you don't have room for a full-scale compost heap, you can always employ the services of some worms. In this handy vermiculture how-to, you'll learn how to build your very own wormery.

As your home ages, so does your deck in the backyard, but there are ways to resolve this issue. If that wooden deck is looking weathered or worn, you can simply replace the components with composite materials without a complete rebuild. Composite doesn't splinter or have knots, and it's low maintenance. This two-part video, brought to you by Lowe's, will show you exactly how to renew your deck with composite decking.

Chef John from FoodWishes prepares a grilled halibut steak with corn and chanterelle mushrooms. You can find chanterelle mushrooms in most upscale markets. Before cutting into chanterelle mushroom make sure you remove as much dirt as possible by using a brush or the edge of a fork. Next, cut chanterelle mushrooms into thick meaty slices.

This video tutorial shows you how to cook braised beef shanks. Ingredients:

Chocolate. Everybody loves chocolate. Unless you're allergic. If you want to melt chocolate, then this video tip is the perfect recipe for melting chocolate, straight from Real Simple.

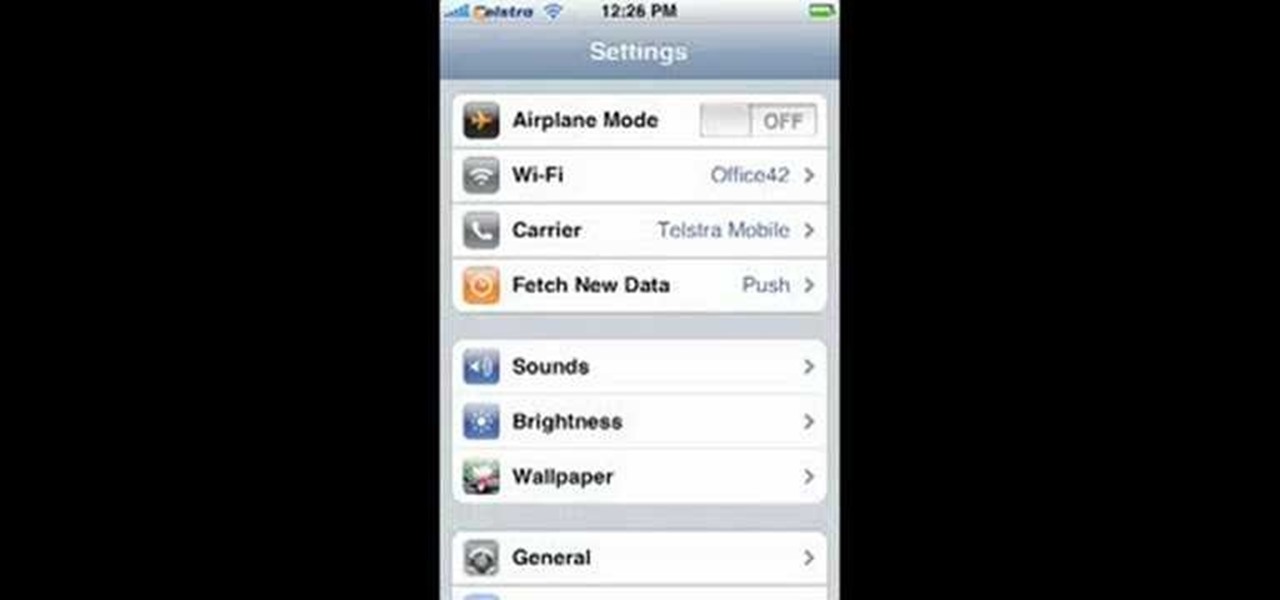
Can't tell if you need sunscreen or a rain poncho? Checking the forecast is a breeze. Learn how to check the weather on your iphone.

It is not hard to incorporate Strongman training techniques in your athletes' programs, but you have to make sure the technique is right. Flipping tractor tires is a good and cheap method of training. Unfortunately, it is often practiced incorrectly. This leaves athletes with back problems and pain. Avoid injury while training for StrongMan competitions by following these rules.

Watch this science video tutorial from Nurd Rage on how to restore silver with electrochemistry. You can restore old silver with aluminum foil or a battery by simple electrochemistry.

Pulling off the perfect ponytail is easy once you know a few tricks. You Will Need

This video will show you how to record video on your Apple iPhone 3G for free! This is a complete guide to installing the iPhone Video Recorder on your iPhone 3G, which also works on the First Generation iPhone.

Looking for great summer recipes? Then try this decadent and sweet dessert, serve it hot off the grill. Top off the grilled pineapples with vanilla ice cream or a rum sauce.

Ever wonder how tofu is made? Well here is a how-to video that shows you the step by step process of making fresh homemade tofu from scratch. All you really need to make tofu is dried soybeans and a little arm strength.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Check out this how to video to learn how to make BBQ ribs. Experience a new video cookbook with delicious summertime recipes, perfect for your picnic basket or backyard BBQ table.

Ingredients 3 tablespoons unsalted butter, cut in 1/4-inch cubes, divided

How to Find Cheap Airfare In a world with a troubled economy and where travel costs climb daily, getting the cheapest ticket for your flight home can be a scary task. Before you buy, check out this guide to help you find the best deal.

Obesity has ballooned into a worldwide epidemic. The World Health Organization estimates that 2.3 billion adults will be overweight and 700 million will be obese by 2015. Over 20 million children are overweight today. The reasons for these distressing figures are common knowledge: The international switch to high sugar, high fat, low nutrient processed junk foods prompted by global fast food chains and their advertising; the increasingly sedentary nature of jobs; children playing video games ...

This week, Google held back on introducing a slew of new Google+ features, and introduced new Chrome extensions instead. The new additions won't replace of your favorite Chrome extensions, but they are very useful, and elegant.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

Whatever it is you're into, Facebook Groups are a great way to connect with others that share your interests. And beyond matching you up with like-minded people, Groups also give you access to deals on items, help you organize play dates with families in the same area, and so much more.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

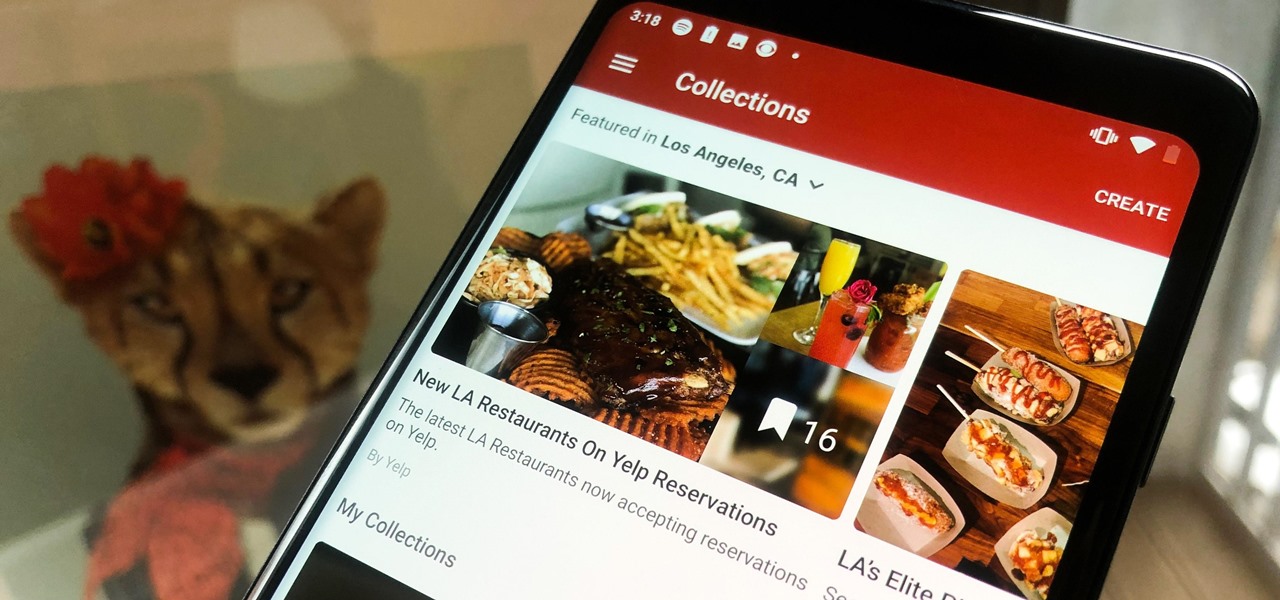
In the past, if you stumbled upon a Yelp listing you liked, you could bookmark it and check it out later on your profile. You can still take advantage of this feature in the mobile apps, but it's more refined now than it ever was thanks to Collections, a feature Yelp first added back in May 2018. You get more power over organizing, accessing, sharing, and discovering favorite businesses.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

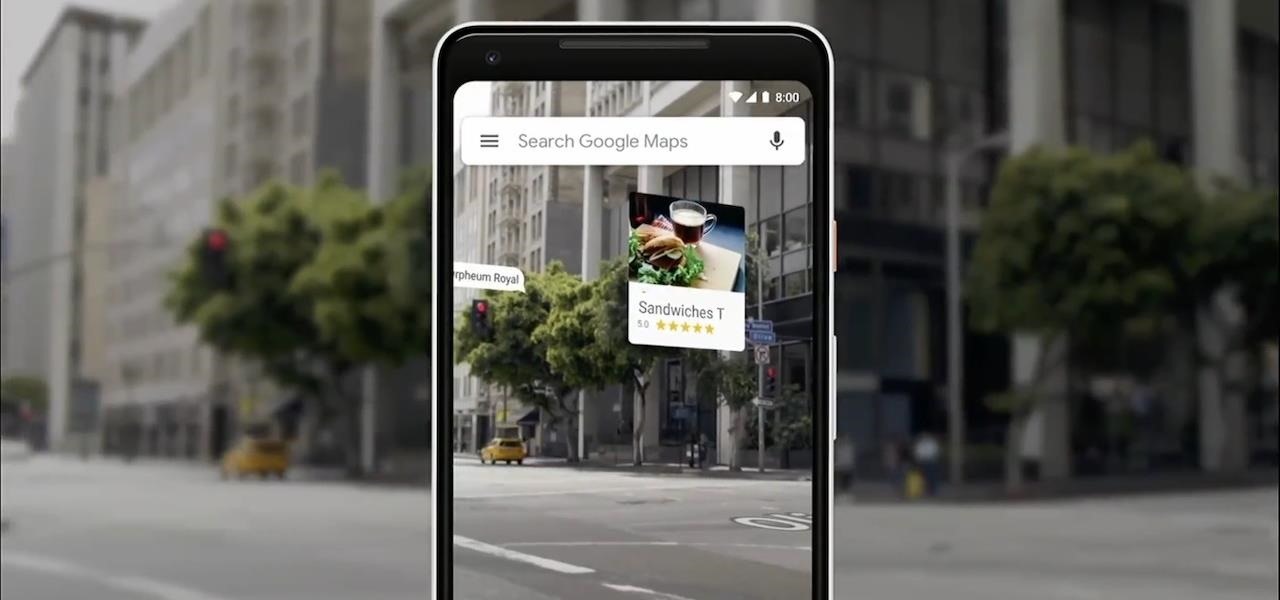
The augmented reality walking navigation mode for Google Maps appears to be closer to an upcoming release for the general public.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Razer took to the stage this month to unveil their new flagship phone, fittingly called the Razer Phone. The device is targeted at gamers, but has a list of specs that make it an intriguing daily driver for any user. Its headlining feature is an 120 Hz IGZO display, the first of its kind in a flagship smartphone released in the US. Tonight, Razer officially opened up orders for the new phone on their website.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Are you looking for a get-rich-quick scheme? Need a way to buy that Tesla you lied about having? Well, I don't know how to get you that. But what I can tell you is there is an emerging market that pays pretty darn well, for work that's more than interesting. I'm talking, of course, about iPhone repairs.

Great news: you don't have to give up grains if you're avoiding gluten.

Finger limes are one of those foods that bring out the little kid in even the most staid grown-up. I dare you not to squeal when you cut one open, squeeze, and see all that bubbly goodness emerge.

Lenovo brought out the big guns for CES 2014, with the Vibe Z showcased as the Chinese company's' first foray into the LTE smartphone space. Slated for a February release, the ultra-thin and extremely light smartphone will certainly be in the running for top smartphones of this very new year. Photo via CNET

The internet is a great place to find information for pretty much anything you can think of. So why shouldn't it be a place for official higher learning? I'm not talking about a course in Wikipedia or SparkNotes, but real colleges offering real college courses completely online. And guess what—it's FREE.