Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

If you've ever spent any serious time examining the Chinese tech startup world, you know that it moves fast — very fast. The tech startups hailing from Beijing and Shenzhen are moving so fast that they're now in serious competition with Silicon Valley.
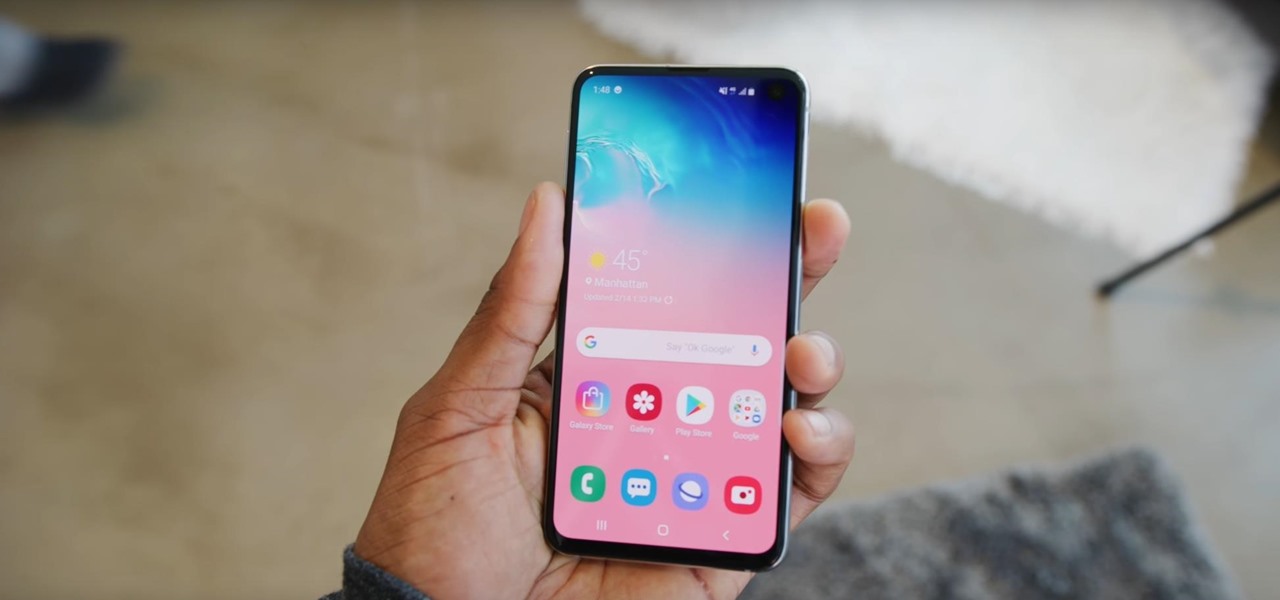
With Apple releasing the iPhone XR, it appears Samsung is looking to challenge this "budget flagship" option head-on. They brought their usual two phone releases this year, but also threw in another three for a total of five phones, including the Samsung Galaxy S10e. And for many, this might be the option to look at.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

By now, there's no way you haven't stumbled upon a TikTok video, whether it was on Facebook, Instagram, Twitter, or YouTube. Just watching these addictive short-form videos is enough to make you want to join up and make your own, and when you do, we've got some tips that will help get your TikTok account in order.

We recently set out to find the best phones for people whose primary usage revolves around social media apps like Facebook and Instagram. Samsung, Apple, and Google were the three brands that made our top five, and while the latter only had one finalist, the two bigger OEMs had a pair of phones each. What struck us, however, was that Samsung's phones edged out Apple's not once, but twice.

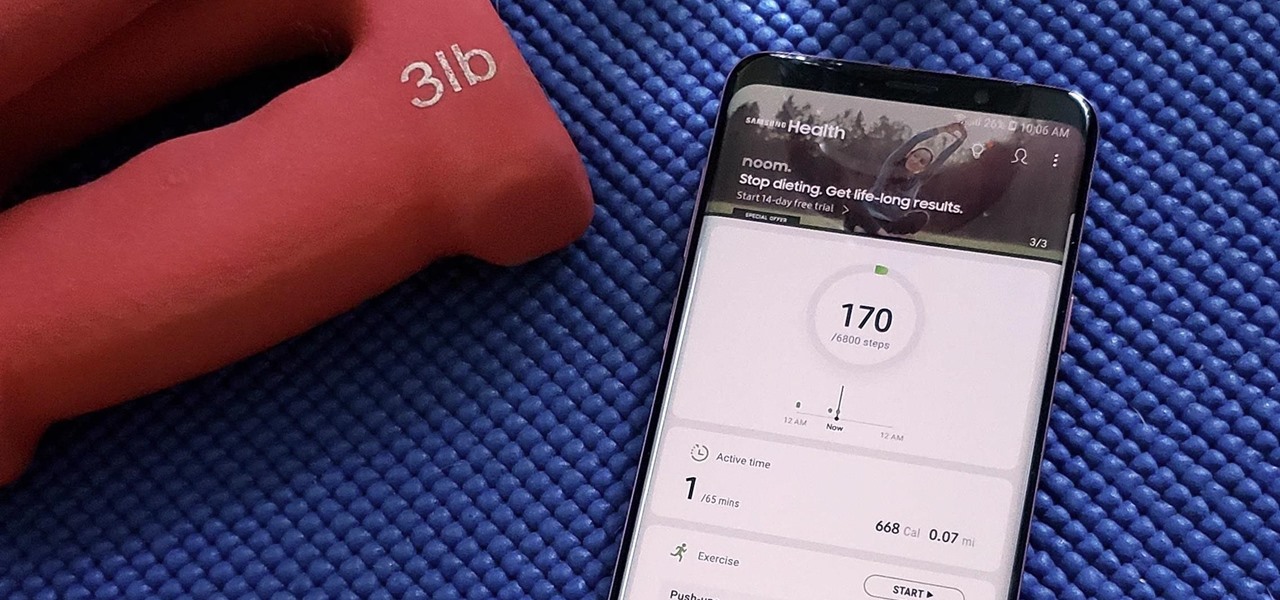
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

No matter how good a display is, the idea of perfect color calibration is subjective — some prefer warmer more saturated colors, while others prefer the calmer cooler side of the color spectrum. It is almost impossible to create a single color calibration that everyone can agree on out of the box. The display on the Pixel 2 XL was specifically calibrated with a more realistic color profile in mind.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

While the iPhone XS actually comes with a smaller battery than the iPhone X, Apple claims it, along with the XS Max and XR, offer users longer battery life than last year's first Face ID model. While that may be true, your new iPhone still ships without meeting its full battery-saving potential. There are, however, steps you can take to make sure your X, XS, XS Max, or XR makes it from morning until night.

While there are over 100 cool features iOS 12 has to offer, there are some things Apple has made more annoying on iPhones or just has not addressed yet.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

I was in college, and my 15-inch Sony Vaio laptop was my prized possession. It was my first PC and probably the most important thing I brought with me to my dorm — it was both how I completed my assignments and my primary source of entertainment. How could it turn its back on me in my time of need?

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.

2017 was a down year for HTC. First, the U11 and U Ultra were widely criticized. Later, Google purchased a large chunk of HTC's manufacturing division, leaving the Taiwanese company running with a skeleton crew after losing 2,000 key employees. But that's not stopping HTC — their flagship U12+ was just announced, and it's quite impressive.

When OnePlus announced the 5T, many were disappointed that it wasn't shipping with Android Oreo. To curb some of this disappointment, OnePlus quickly introduced an open beta for both the 5 and 5T and promised that each would receive the official version by Q1 2018. Well today, OnePlus has met this promise and pushed the OTA out for the official stable version of Android Oreo.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

The last quarter of 2017 brought us some downright excellent smartphones. Between the iPhone X, Pixel 2, and Note 8, consumers have more fantastic options than ever when choosing a new device. It's now the perfect opportunity for Samsung to set the tone for 2018 smartphones with their exceptional S9 and S9+.

If preorder delays are any indication, the iPhone X certainly has some buzz. But does the X have the quality to support that buzz in the long run? After all, a $1,000 (or more) iPhone feels more like an investment than a smartphone purchase. The question on any prospective buyer's mind should be, "Is this thing worth it?"

"I'm Rey." That's what a lot of people will be saying again this Halloween, as Rey costumes are sure to be another favorite of trick-or-treaters and cosplayers. Yes, on Oct. 31 we all have a chance to be the scavenger of Jakku who just so happens to be the "new hope" for a Jedi renaissance.

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

Super Mario Run has been one of the most insidiously addicting iOS games to come out in recent years for iPhone. And now, as of March 22, Android users can get in on the fun, too.

Fresh herbs are a surefire way to enhance a dish, but buying them at the store each time you need them is costly. Luckily, growing your own herbs is a lot easier than it seems: You can even using cuttings from the herbs you already buy to start your own little herb garden.

Knowing if your meat is cooked properly is both the difference between a delicious meal and an inedible one... and the difference between making your guests sick and keeping them safe.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.