This four-part tutorial series presents a look at how to combine traditional keyframe animation with DOPs simulation. This first part contains an overview of how DOPs differs from SOPs and how to examine DOPs data using the Details View. It then looks at the RBDKeyFrameActive node as a method for combining keyframe and simulation animation. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself wi...

In order to propagate plants from cuttings, you will need the following: plants that can grow from clippings, a container, potting soil, water, and a rooting hormone.
Warnings this only for educational use i dont take responsiblety for any use of this article if you want to use this for use at a school plz contact me at sebzy4@hotmail.com hi im a computer enginer/programmer (NOT games) but i am good at hacking and i want to help. notise that this is just a help site not hacking site but this will help firstimers

What separates Metro 2033 from other FPS games? Life. There are underground towns, markets, children, music, and so much background chatter than sometimes you can't single out a particular conversation.

Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.

The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor.

Bitcoin is a new currency built off "Satoshi Nakamoto's" (alias) 2008 Bitcoin white-paper. Bitcoin provides its users with a way to make peer-to-peer (P2P) transactions without having to use a bank as a mediator. There is no middle man, no corporation backing it, and no one has access to your money, except you. It's decentralized from government, run by the people, for the people.

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.

This Null Byte is a doozey.

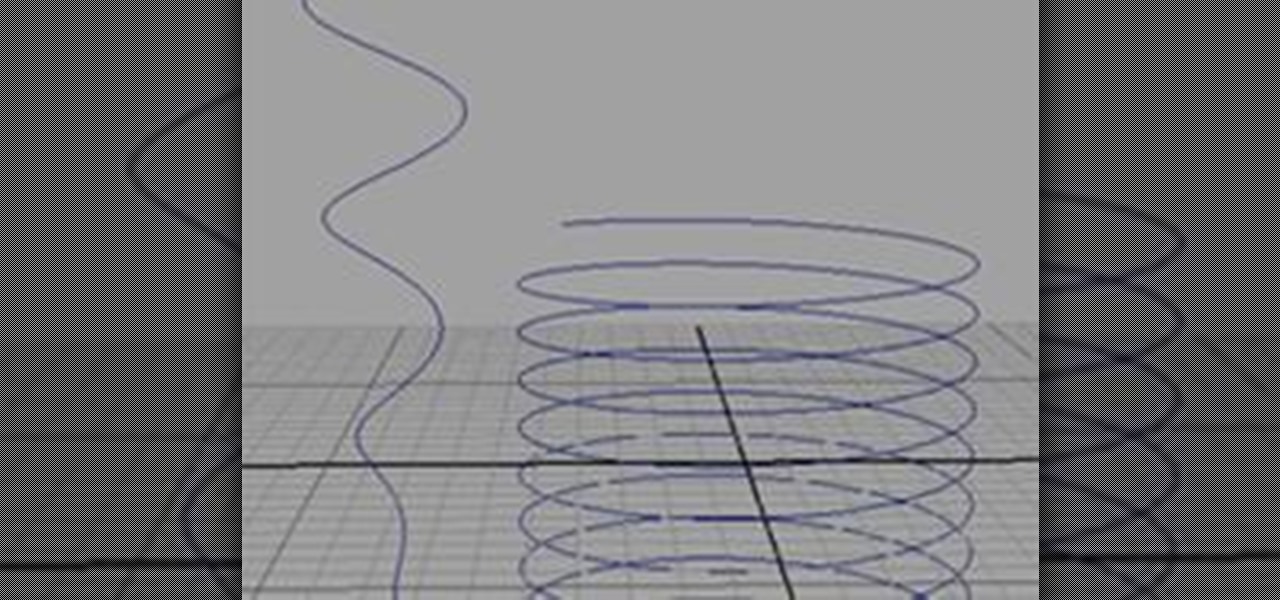
There are several ways you can go about creating your NURBS helix curve in Maya; I will demonstrate the two easiest ones.

General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them.

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!

There’s no point to playing all of the different tower defense games available today. Most adhere to the original formula, so playing 2 or 3 really good ones (like those mentioned in my previous post) would be more efficient.

Spending five days with the game is enough to know it's not to my liking. Is it a horrible MMO? Yes, yes it is. There are better Free to Play MMOs launched years ago that are better than this. As a fan of the Final Fantasy series (I am currently playing and liking Final Fantasy 13), this MMO is so bad that at some point I couldn't justify the awful environment, game play, and interface.