Do you believe you just don't have an intuitive sense of math? Sadly, this is the case for many people. The reality is that math is learned with practice. No one is born with a math gene making them more intuitive than others.
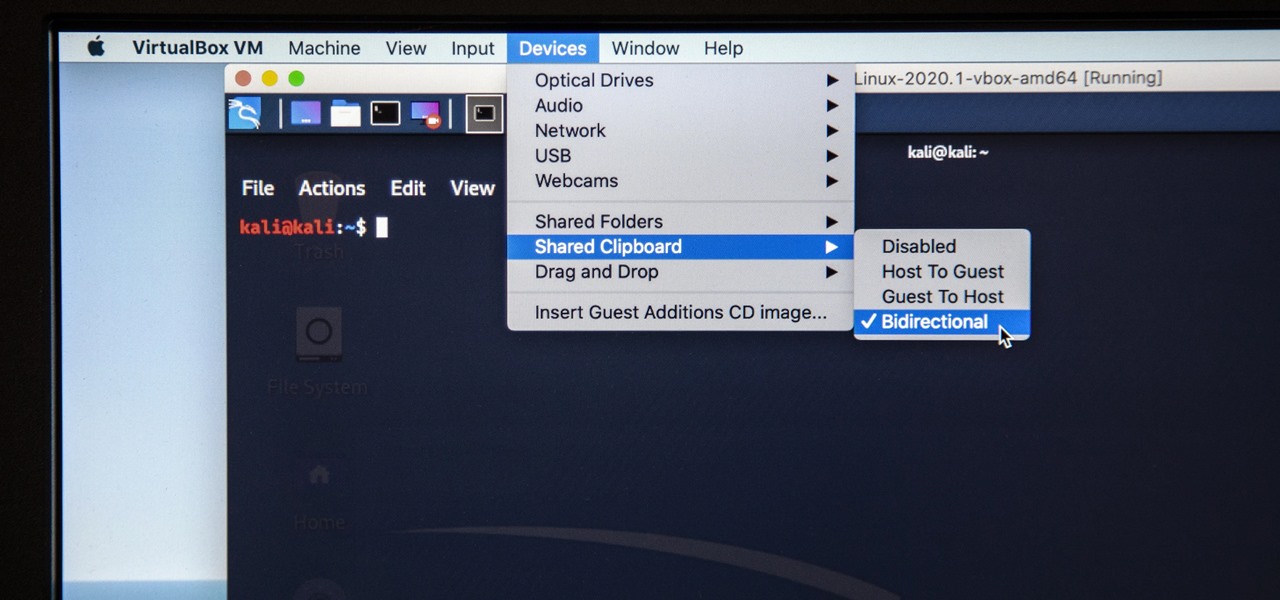
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

The fatal crash of Air France Flight 447 is one of the most tragic accidents in avionic history — while it also serves as a stark reminder of what can go wrong when humans rely too much on driverless vehicles.

On Wednesday, Microsoft launched a chatbot on social media that learns from conversation, and trolls quickly taught it how to be a shameless, Nazi-loving bigot. Oh Internet, an opportunity for a Hitler joke never slips past you, does it? This Is Why We Can't Have Nice Things

Three smart devices shown at CES 2016 are making it easier for you to make stupid decisions. PicoBrew, Somabar, and 10-Vins demonstrated their systems for beer, mixed cocktails, and wine, respectively, and each one is attempting to change the way we enjoy our favorite potent potables at home.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

When I first heard about the Thermomix, an all-in-one kitchen appliance from Australia, it sounded like an old SNL commercial parody: It slices! It dices! It heats! It kneads! Is there ANYTHING this machine CAN'T do?

It sounds like a dream come true: just press a button on your phone, and 30 seconds later, a machine produces a custom-made, ready-to-eat meal. Finally, science comes through for the truly lazy!

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Coffee is a topic that everyone has a strong opinion about, especially when it comes to brewing the perfect cup. Even if you buy the best beans and grind them yourself, chances are you're skipping one necessary step to make sure your coffee tastes the best it can: cleaning your coffeemaker the right way.

There is nothing more refreshing than an ice cream in a hot summer day. And even though, here in Australia, summer is "just" a couple of months away, I still like to have a scoop or two every now and then. However, I like to make the ice cream on my own. In this way, you can make whatever flavour you want, plus you know what type of products you have used and it usually tastes better than a commercial one.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

This step-by-step tutorial will show you how to install Mac OS on Windows 7 on Virtual Box. Video: .

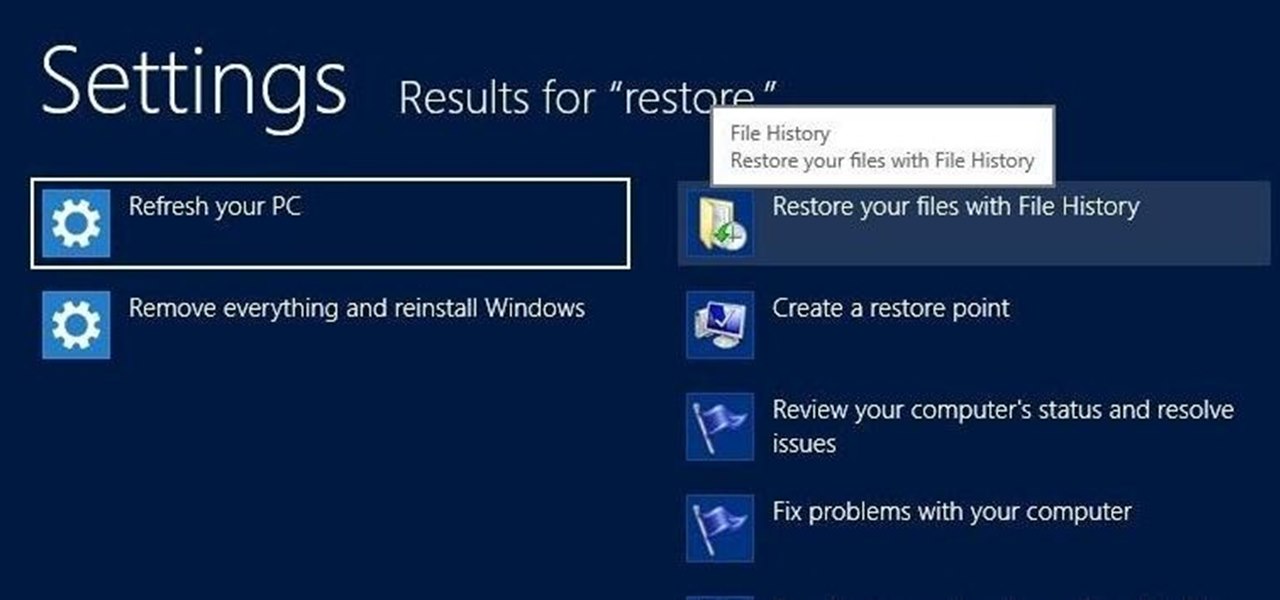
There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be.

With a little practice a cushion cover can be made at home easily. The materials/equipments required are as follows: fabric of your choice (having appropriate dimensions) to make the cover, scissors, measuring tape and ruler, needles, threads, sewing machine and an iron.

If you've been looking for a sexy contemporary video game character to cosplay or dress as for Halloween, consider Altair from Assassin's Creed. He's sexy, distinctive, and armed with this video you'll be well on your way to having sewed the costume yourself. Specifically, this video will teach you how to sew Altair's hood quickly and easily.

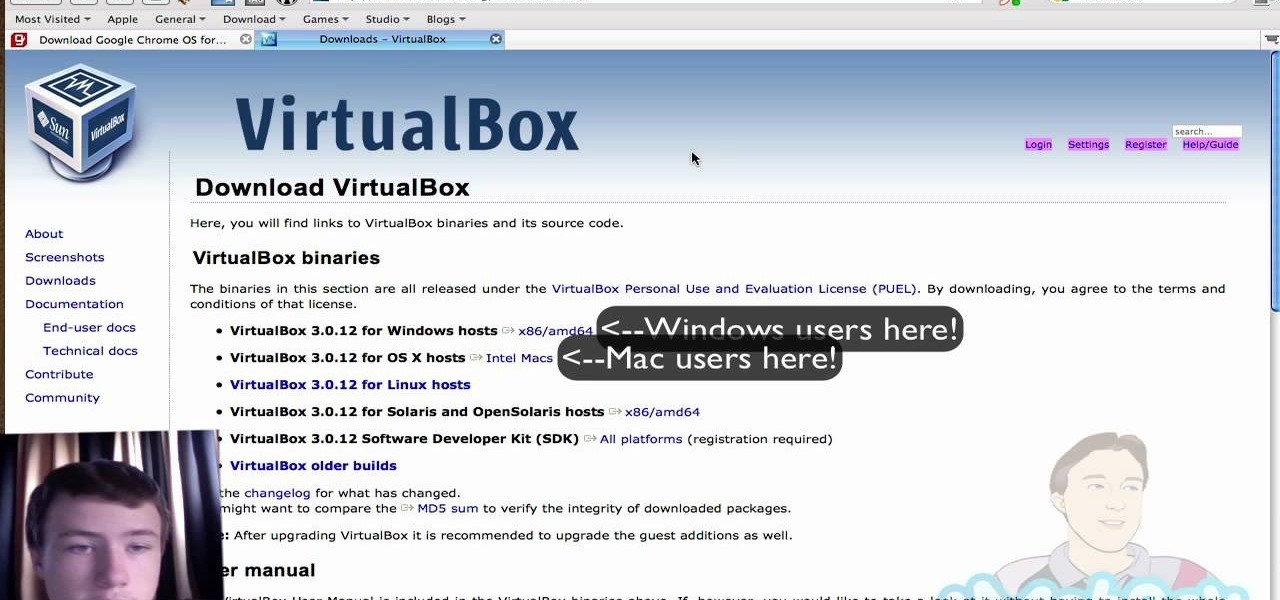
First download the virtual box, download it for Mac and install it. Now download the Chrome OS and extract it. Now launch your virtual box and click new. A "create new virtual machine" wizard will open, click next, put the name of the OS and choose Linux in operating system and Ubuntu in version now click next. Now give memory atleast 1000 MB and click next. Select "use existing hard disk" and tick the "boot hard disk" and choose the OS file by clicking the folder icon next to it, click add a...

If you own a Ryobi trimmer and wish to perform some regular maintenance work on it, you may want to check out this next video. In the tutorial, you find out how to clean a 2 cycle engine carburetor from the Ryobi trimmer using some simple pieces. It's not too difficult to do and can be really handy when you want to make sure your machine is working at optimal capability. So check out the video above, pay attention, be careful, and enjoy!

If you constantly are vacuuming hard floors, the internal hose of your machine may become damaged. If it has become damaged, don't call a repairman just yet. This can be a relatively easy fix that can save you and arm and leg.

If you are finding out that your dishwasher is leaking, then you need to get it fixed soon. A leaky machine means there will be water on your floor and this can lead to possible injury for you or others.

Better your lumbo-pelvic stability with a Pilates Reformer exercise machine. With pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates. For complete instructions, give this free exercise video a gander.

Owning a lawn tractor is a big responsibility. Just like a car, there are many areas that need constant care and attention. One area that needs to be checked regularly is the law tractor's deck belt. This is needed to help spin the blad that is located underneath the machine.

If you're the new owner of a lawn tractor, congrats! This machine makes cutting your yards grass much easier for your body. But just like a car, there are certain buttons, levers, and gauages that have to be checked on before cutting any grass.

T-shirts are practical and unfailingly comfortable, but not particularly known for looking either sexy or fashionable (they're more, shall we say, frumpy, than anything else). But did you know that within the ugly duckling that is your blank gray T-shirt is a beautiful swan of a tank top just waiting to get out?

Why would you blow upwards of $200 or $300 on a bikini when you can craft a perfect good one yourself? Don't believe us? Then watch this video by fashion DIY expert Gianny L to prove yourself wrong.

Live in an area where you won't be needing your gas-powered tools for the winter? Such as your lawnmower, trimmer, and any other tools you need gas to operate. If you store them away for the winter and come back to use them during the spring time and realize your tools are acting funny, it may be because the gas you left in them has turned into a gel and has damaged the carburetor. You can do a number of things to protect your power tools from such a thing, you can dump all the gas out of the...

An animated GIF is a great idea for a banner to advertise your website or services. In this tutorial, you will see just how easy it is to make one of these moving objects using Photoshop CS or Adobe ImageReady. Animations draw the eye to your logo much more than an image that is standing still, so if you are looking to get noticed - this is the way to go.

Although cars are these thousand pound machines that can make travel so much easier for everyone, accidents can occur. So it's important to know what's wrong with your car and how to fix it. If you have a bad or damaged radiator, that is something you need to fix and soon. So, in this video tutorial you'll find out how to replace the radiator to a 2002 Dodge Neon. Enjoy and good luck!

Navigating on your HP TouchSmart 3.0 PC is easy, fun and takes nothing more then your fingers. To click, simply create a single point of precise contact between your finger and the screen. The HP TouchSmart uses optics to determine clicks so avoid leaning on it with your hands, knuckles, large jewelry or the random fly. The screen is not pressure sensitive so pressing harder has no effect. To right click you simply press and hold. For tasks that require multi-touch input use more than one fin...

First cut out card stock using the Big Shot Dye. This card stock is great as a template to make sure you are getting the most out of your felt. Cut out pieces of your felt around your card stock template trying to get as close as you can to the border of the card stock. Next take your Big Shot machine and place your cutting plates on the bottom, as well as your dye. Then layer your cut out felt pieces on top of your dye. Start rolling your felt through by cranking the handle on your Big Shot....

TrueCrypt is a free application that lets you encrypt designated programs on your Ubuntu system to prevent unwanted access. Provided you select a strong password, intruders will not be able to open your personal files and documents. This instructional video walks you through the process of installing TrueCrypt on your Ubuntu operated machine and demonstrates an example on how to create an encrypted volume within a select partition.

Watch this video to create realistic hot cross buns for your dollhouse! Start off with some white clay, and glass marble beads. Take your clay and make a nice little ball and pour in some of the marble beads. Squish the clay together so all the little "raisin" beads get mixed in. Roll it through the pasta machine on setting number one. Next take your square cutter and press it down on the clay. You then have your first hot cross bun. Use different colored chalks to color the bun. Then bake yo...

This video fully explains how to correctly use the Breville Juice Fountain. The product is 850 watts and has both a high and low setting for your convenience. Everything, except the motor itself, is dishwasher safe. One container collects all the juice, and another container on the opposite side collects all the skin from whatever it is you are juicing. Using a whole apple (with a sticker still on it) as an example, our demonstrator inserts an apple into the top of the machine, pushes down wi...

Looking to make this Christmas a DIY Christmas? Why not make your own Christmas tree skirt, customized to fit your personality and home decor! Nothing says it’s Christmas like a beautiful Christmas tree. Now you can decorate the area below with a handmade Christmas tree skirt that you can be proud of.

ThreadBanger give us a great recipe to make a unisex bomber hat using just a flannel shirt, white faux fur, a measuring tape, the bomber hat pattern, a sewing machine, and two and a half hours of your creative time. Add pom-poms at the ears to give it extra flavor! Super cool look for both dudes and ladies.

Hacker Defender is one of the most widely deployed rootkits in the world. It is a user-mode rootkit that modifies several Windows and Native API functions, which allows it to hide information (files, processes, etc.) from other applications. In addition, Hacker Defender implements a backdoor and port redirector that operates through TCP ports opened by existing services. This means it is not possible to find the hidden backdoor through traditional means, like launching a remote port scan agai...