This video explains how to make an inexpensive compost roller. The video begins with a composed pile shown covered with a tarp to keep rain away from. The materials needed for this project consists of 3" barrel nuts(2), 3" hinges(3) and machine screws(3pk) from a local Wall-Mart. The tools needed for this project consist of an electric drill with drill bit, screw driver, wrench, jig saw or key saw and a heavy duty utility knife. The compost roller made was just a simple plastic drum with a hi...

Paper or plastic is a thing of the past; both options are equally terrible for the environment. With this tutorial, learn how to turn your old bed sheets into funky grocery tote bags. You will be the envy of everyone at the store with these adorable, homemade bags.

In this tutorial you are inside a music store. From the beginning you are told stringing a Nylon string guitar is different than other guitars. You start by removing the old string from the machine head. You thread the new string through the head towards you. You will need to loop two times over and under and hold both ends of the string in place. As soon as the string is tight you can bring the end that is in the back over and through the main part of the string. Once the new string is in pl...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

This video tutorial program is designed to promote ground crew safety when working under and around helicopters during external load operations. This is not a safety-training and is only intended to be used with the participation of a ground crew safety officer, trainer or other qualified personnel. All training and refresher courses must be done in accordance with federal and provincial regulations and the Canada Labour Code.

Creating drum beats is a crucial part of making a great song. Learn how to use Logic Pro 8 Ultrabeat drum machine feature to create and mix your recordings in this free music production tool tutorial from a professional audio engineer.

This is the final step of learning how to sew on a vintage Kenmore sewing machine. Watch this how to video to learn how to sew a straight stitch on a this type of sewing machine. Run the motor as you press the reverse button, this locks up the thread.

This series will teach you the basics of sewing machine operation. Our expert will identify the parts of the sewing machine for you, as well as explain some of the general functions and abilities of the machine. Tips include how to thread a sewing machine, winding and installing the bobbin, selecting the proper foot, and turning the fabric.

This tutorial goes over how to edit the text document that controls the hot key (shortcut key) commands. It doesn't go into the advanced commands or even begin to describe the various commands that you can invoke by changing the text document, but most of the users who will be editing this are ADVANCED USERS. NEVER. NEVER change the shortcut settings on a machine that is not yours and ALWAYS. ALWAYS make a backup copy of the document before you start to work on it.

Parts of the Rowing Machine: Exercise & Training on Health & Fitness Equipment Part 1 of 15 - How to Do rowing machine exercises.

Anne Beckett is going to take you through this 15 part series on how to set up a custom embroidery design on a machine embroiderer. In this first part she'll cover how to tell if your design is good for the embroiderer.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

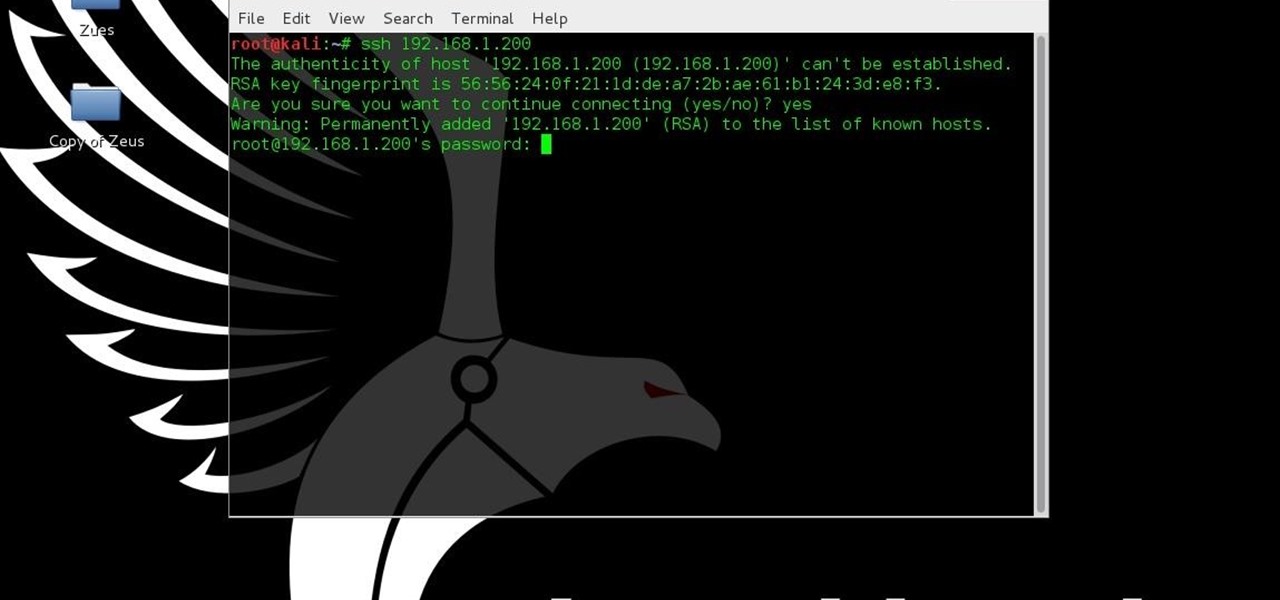
While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

Microsoft's Monday keynote introduced the fourth generation of the company's Kinect sensor during Build 2018 in Seattle.

With the heavily anticipated installment of the God of War game series arriving on April 20, PlayStation has taken the opportunity to make its first foray into mobile augmented reality with a companion app.

Ride-sharing firm Lyft says it will continue to rely on drivers in the near and long term even as it replaces them with driverless cars, Taggart Matthiesen, Lyft's director of product, said during a Podcast with Recode.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

The National Transportation Safety Board (NTSB) said it is still investigating the circumstances of a fatal Tesla crash last year to determine if the car or Tesla's Autopilot driverless system was at fault, but revealed more details about the circumstances of the crash.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Greetings my fellow hackers.

This cardmaking tutorial shows you how to make a floral Christmas card that is complete with embossing using a die cutting machine. This is a very pretty card and once you have seen the tutorial you will see how easy it is to make. I also show you how I get the embossed lines around my cards to add the pearl drops using a box embossing board.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

The motor coupling goes between the motor and the transmission. If it fails the washer will not spin or agitate. If the washer fills with water but then does not agitate, but you hear the motor running, the coupler could be the problem. You may hear some clicking noises as the broken pieces spin around. You may also see a pile of black rubber pieces on the floor under the middle of the machine. You can follow the steps in this video to help you do the repair.

This video gives you a step by step tutorial how to recover the seats of your car. If you are a little familiar with sewing, this is easier as you imagine. All you need for this repair is new fabrics and a normal sewing machine.

Ever wonder how to make an engine out of soda cans? Not even sure if it's possible? These videos will show you how to build a working Stirling engine out of cans and other general materials. Here it is in action:

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

D.J. Brasby discusses on this series of videos how to use an Akai MPC drum machine. Part 1 of 14 - How to Use an Akai MPC drum machine.

Circle or infinity scarves became really popular this year, and this little how-to shows you how to knit one up yourself. Knit 1, perl two. You can do it! Follow the steps and fight that cold neck feeling!

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

Learn how to do proper push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

This is an instructional video on how to thread a circular knitting machine. For the demonstration, the circular knitting machine by Innovations serves as our example. Tips are provided based on the experience of a seasoned machine knitter accustomed to using this machine.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

It's no secret that Google is all about AI. In their eyes, machine learning is the future of software development, and you can see evidence of this all over the last couple Android updates. They've used it to power all sorts of features in their Pixel phones, and they've even donated some of their AI smarts to AOSP for all Android manufacturers to share. But it looks like Samsung isn't exactly on board.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.