One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

To the best of my recollection, Fruit Ninja was one of the first touchscreen games that appeared to really take advantage of the new paradigm of user input, turning the player's finger into a produce-slicing katana.

Augmented reality headsets with larger eye boxes than any device currently available could make their way to market by the end of next year if current timelines hold true.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Directive Games received the enviable honor of unveiling their ARKit game, The Machines, on stage as part of Apple's iPhone launch presentation.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

Like a strong-tasting cup of joe, but want more caffeine out of it? Start double brewing your coffee. To paraphrase a big fan of the double brew process on Reddit, it'll make you feel like you can throw an orange at 60 percent the speed of light. It's that strong. Really.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Normally, office supplies and food don't mix, but you can use a paper shredder to make fresh pasta in your very own home (...or office). In other words, you don't have to buy a bulky and expensive piece of equipment to make fresh pasta. If you already have a paper shredder, you can simply feed pasta dough through it for perfect tagliatelle noodle strips that will taste far better than anything you can buy at the store. Step 1: Clean Your Machine

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

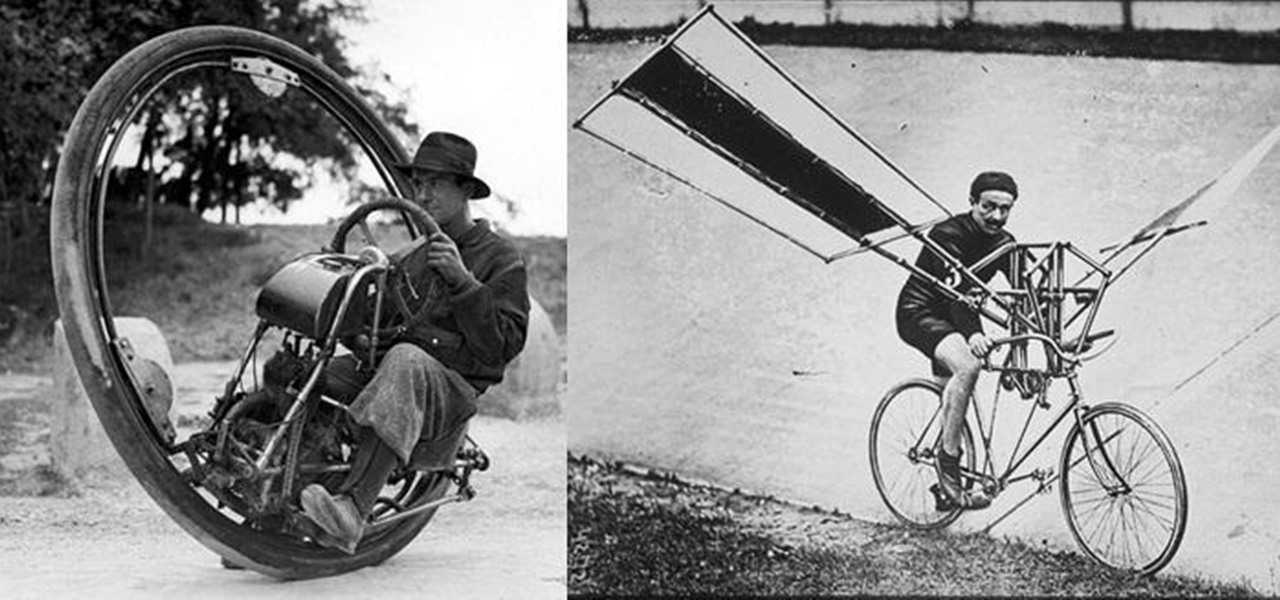
We don't spend much time thinking about bicycles today, do we? Sure, they're a "green" alternative to driving everywhere in cars, but the vast majority of America has dismissed them as simply being too much work, or more importantly—too slow. That wasn't always the case, though, I assure you!

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

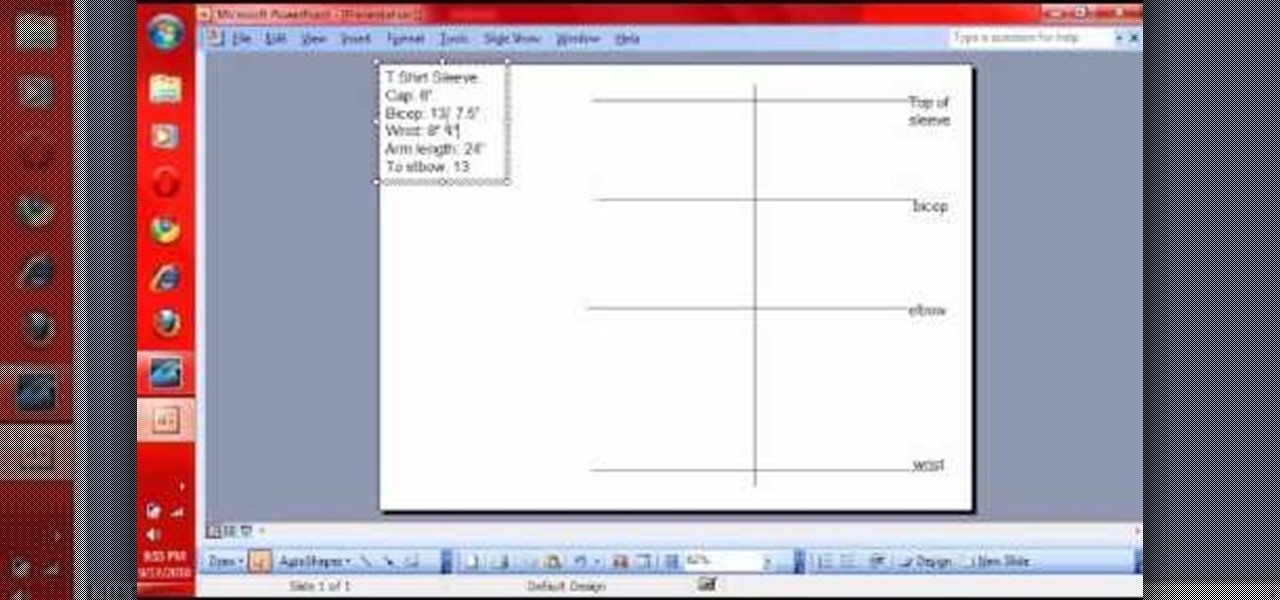
Ever wondered how to make a tee shirt? With a little cloth, some thread, a sewing machine and some direction, it's as easy as baking a cake. If you want to start designing your own cool T-shirts with your favorite fabrics, watch and learn!

Rick Pitts takes us through how to do a push up using a coffee table. First, he starts by doing a push up for shoulders and triceps. You do this by placing your hands slightly wider than shoulders with fingers pointing forward. Keep your elbows near body as you lower yourself towards the table.

Watch this instructional knitting video to complete and open cast on with a knitting machine. Push your needles back into forward position and knit across one row. You will want to use clips and claw weights to keep your knit work straight. If you knit with a knitting machine, this is an essential trick for getting started with larger projects.

Watch this instructional knitting video to hang a rag hem on your knitting machine. Add weights to the inside of the knitted hem to keep your knit work straight. You will need a single pronged tool or a three pronged tool. If you knit with a knitting machine, this is an essential trick for getting started with larger projects.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to crochet cast on. This is one way to cleverly weave your yarn onto the knitting machine and begin the piece of knit work. You may want to reference written instructions in addition to watching this knitting video.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to crochet a cast off. This is one way to cleverly remove your work from the knitting machine and complete the piece of knit work. You may want to reference written instructions in addition to watching this knitting video.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to pick up and hang stitches. Use a three prong tool to attach one piece of knitting work to the knitting machine. Once you set the set the machine up, you can knit a wearable piece with an altering pattern.

This is a cool technique for machine knitters to use. It's a hand technique that converts quite easily to machine. Sew a phony seam when with a small knitting tool to alter pieces on a knitting machine.

If you knit with a knitting machine, a cone of yarn proves much more useful than a standard ball of yarn. This instructional knitting video demonstrates how an electric cone winder works. This little machine allows one to quickly wind a ball of yarn onto a cardboard cone.

Use the Martelli Stitch in the Ditch Binding Foot for top stitching and with a double needle to get a professional finish to your quilting and sewing projects. Watch this video sewing tutorial and learn how to top stitch with a double need on a sewing machine.

This Mig Welding Video Demo shows how simple and easy it is to use a MIG welding machine. Mig Welding Machines are use throughout the world. They are the suited for many welding applications. This video demonstration demonstrates Mig welding by welding two pieces of sheet metal together. Watch this video welding tutorial and learn how to fuse two pieces of sheet metal together with a Mig welder.

Using a sewing machine entails knowing how to thread it properly. This sewing how-to video demonstrates how to insert thread into a sewing machine. Follow the users instruction to properly insert the thread into your sewing machine.

Using a sewing machine entails knowing how to the tension knob properly. This sewing how-to video demonstrates how to properly adjust the tension knob on a vintage Kenmore sewing machine. The tension knob is located near the front of the sewing machine. It has a dial numbered from 1 to 9. The larger the number, the tighter the tension.

Using a sewing machine entails knowing how to insert a bobbin properly. This sewing how-to video demonstrates how to insert the bobbin into the feed dog of a vintage Kenmore sewing machine. The bobbin in the feed dog part of the sewing machine makes up the bottom of the thread needed for sewing.

Watch this video from the Concrete Network to learn how use a buffing machine and its accessories.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

There are a total of 242 stars in Super Mario Galaxy 2 on the Nintendo Wii — 120 normal stars, 120 green stars and 2 bonus stars. If you've already found all of the stars in Worlds 1, 2, 3 & 4, now it's time for World 5!

Learn how to use the Miller Concrete Landscape Curbing Machine. You will also learn the basics of making curbing mix.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Smartglasses maker Epson remains the top gun in the drone market with its Moverio line of wearables, and the company is further elevating its offerings with its new Drone SoAR app for DJI drones.