Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

While mobile gaming, in the 10 years since the App Store launched, has matured to console-level quality, premium augmented reality games built with ARKit (or ARCore) have been scarce.
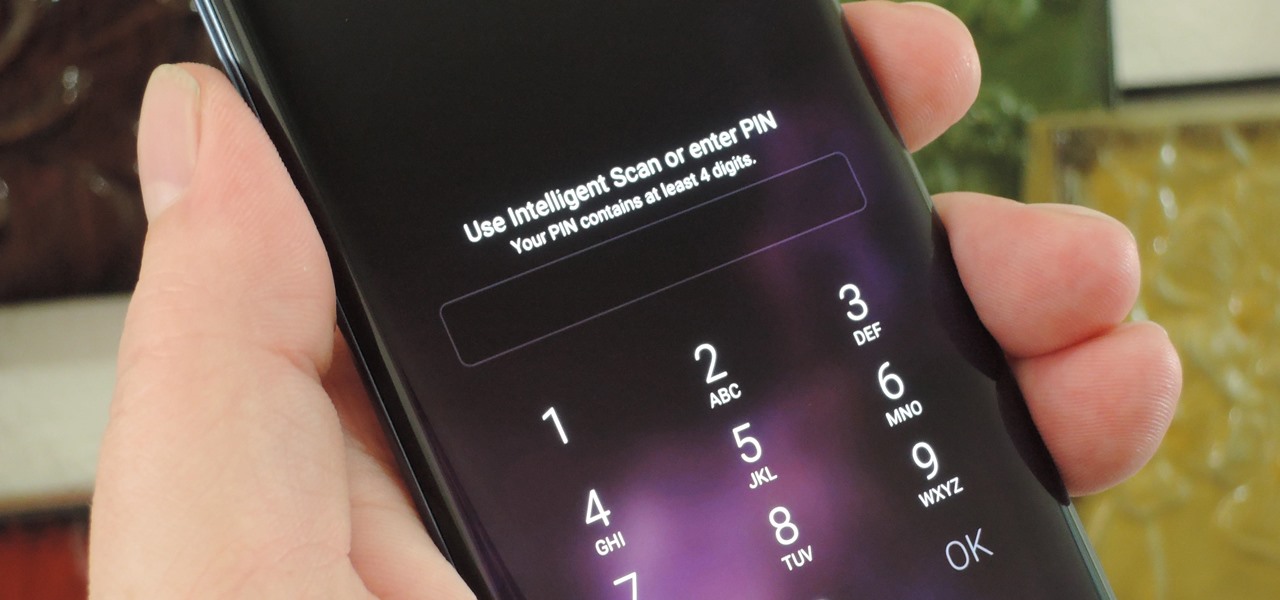
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these efforts is called Intelligent Scan.

Google's new AI-powered camera, Google Clips, seems to be targeted at parents of young children in its current form, but the idea itself has unique potential. Just set it up somewhere, then you'll never miss a moment trying to capture the moment — you'll have a robot photographer taking care of that stuff for you.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Former Google employee Tristan Harris claims there's an easy way to combat phone addiction without installing any new software. By enabling grayscale on your phone, checking your apps and notifications will be less appealing and thus stop you from obsessively checking your phone.

Mirror, mirror on the wall, who's the smartest of them all? Since Max Braun's Medium post went viral back in January of 2016, smart mirrors have been appearing on tech blogs in all shapes and sizes. Some are technically sound, some incredibly easy, but all are visually compelling. However, we've never seen one with a fully functional operating system and gesture support—until now.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

I was on our new #nullbyte IRC channel when someone told me how tedious it is to install an OSX Virtual Machine on Virtual Box (I think it was wawa). We all know Linux rocks (gets acknowledgement from the crowd), but there are morons out there, multiplying at a never before seen rate, who use OSX. We at nullbyte should be prepared for anything and everything. So, in this guide I take you step by step to creating your OSX Yogemite VM.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

If you're like most people, you've stretched before a workout or playing sports. Doing so should help you get your muscles ready to work. While stretching is good for your muscles, you're wasting your time if it's the first thing you do. I talked to Dr. Brian Parr, professor at the Dept. of Exercise and Sports Science at the University of South Carolina Aiken, who explained this misconception and what you can do about it:

Unless your work clothes require dry cleaning, you probably only go to the cleaner a few times a year. And for those few items in your closet for which you do, you have to then find the time and extra budget to make a trip all the way to the cleaners and back again. In the end, it can be quite the hassle.

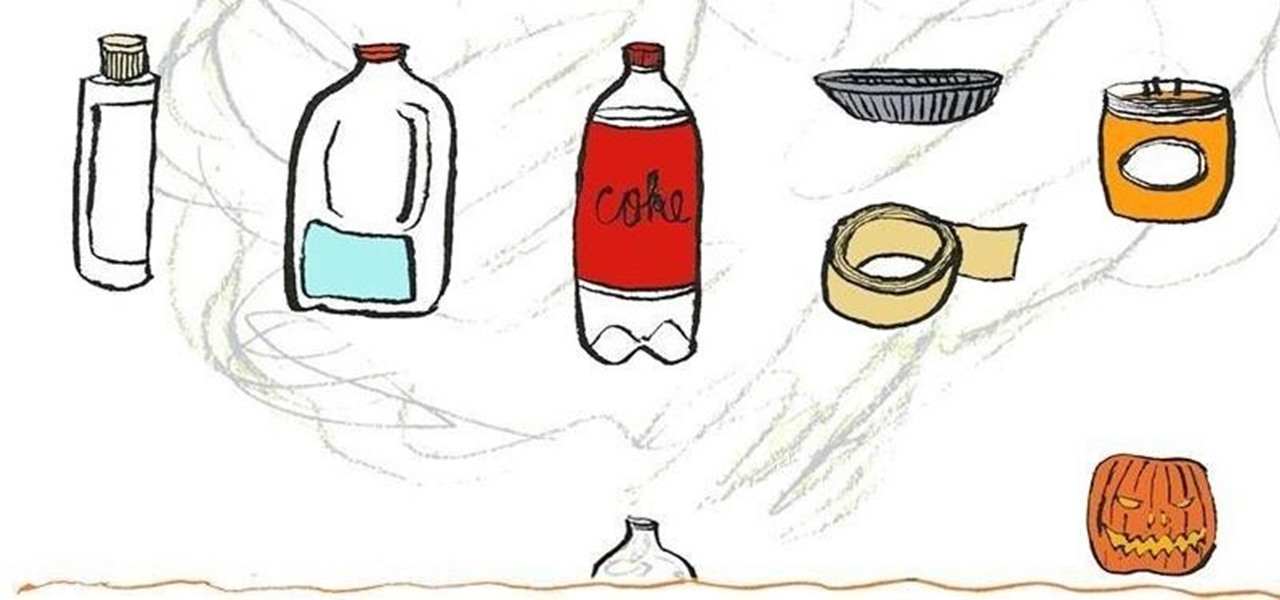
Need to add some spooky ambient fog to your super-scary Halloween party? Rather than shelling out money for a fog machine you'll probably only use once a year, make a trip to the nearest drug store and pick up a bottle of glycerin, a gallon of distilled water, a 2-liter bottle of cola, a disposable mini-pie tin, and a big candle in a jar.

Sometimes you just want to grill. It doesn't matter where you are, what you have, or whom you're with—you just want a delicious burger and you don't care what it takes.

In this how-to video, you will learn how to create your own tube top dress with lace and tulle. This will be useful if you need a unique dress for prom. You will need a sewing machine, scissors, pins, ruler, measuring tape, thread, a half yard of gray knit, tulle, and a yard of lace. First, cut out a rectangular piece that can fold in half. The lower half is a trapezoidal piece. This will be the jersey skit. The smaller end should fit around your waist. Lay the rectangle first and then put th...

This is a video showing how to make a perfect latte at home. First the coffee is ground and then she pours some milk. The presenter says that 1/3 of the daily requirement of milk can be found in a latte. Once the coffee is ground it is brewed. She uses a lot of coffee so that it is richer. While the espresso is being made, the milk is steamed. The espresso should drip out like honey. The steamed milk is then poured over the coffee.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Watch this instructional knitting video to bond a vinyl hem with a knitting machine. Hang an elastic or ravel cord and push it against the bed. Fold the hem over the ravel cord. If you knit with a knitting machine, this is an essential trick for getting started with larger projects.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to decrease the size of your knit piece. Use a single prong tool to unhook and tie off a single stitch on either side of the piece before completing each row to gradually decrease the width of the knit work. You may want to reference written instructions in addition to watching this knitting video.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to weave a cast on. This is a cast on that many people find difficulty with. You may want to reference written instructions in addition to watching this knitting video.

While any form of gambling is set up to make you lose, there are some tips and tricks, shown in this how-to video, to help even the playing field. Penny arcade slots are a reasonable place to start, as the stakes aren't too high, so neither side (you or the arcade) has that much to lose. Watch this video conning tutorial and learn how to beat an arcade penny slot machine.

Watch this video sewing tutorial and learn how to use a ruffler attachment on a sewing machine. Use a ruffler attachment to sew small individually adjustable tucks.

An important part of sewing involves knowing how to make button holes. This sewing how-to video demonstrates how to cut a button hole and insert a button footer on a vintage Kenmore sewing machine. Watch and learn how easy it is use a Kenmore sewing machine to make button holes.

Using a sewing machine entails knowing how to fill a bobbin with thread properly. This sewing how to video will show you how to fill a bobbin on a vintage Kenmore sewing machine. Happy sewing!

This flower arrangement tutorial shows you how to make a candle centerpiece using a pick machine. A pick machine attaches steel picks to the stems of your silk flowers. This makes arranging your flowers in floral foam much easier. Watch this how to video and you will be making this beautiful candle flower arrangement in no time.

This video tutorial shows how to use the Cuttlebug paper embosser. Learn how to make embossed designs in paper projects with a Cuttlebug paper embossing machine.

You can learn how to use the stock market as your own ATM machine. You can make 500 dollars in less than 15 minutes. Then you can take that 500 dollars and use it to get professional advice.

Everybody's favorite food is pizza. But not everybody knows how to actually make a pizza, which is practically a sin. And this "margherita" style pizza is a great one to learn, full of Italian simplicity— red tomato sauce, mozzarella cheese, and green basil— all the colors of the Italian flag. Check out the recipe for this delicious margherita pizza.

Chef Hubert Keller is known for his ingenuity in cooking, like when Frank Sinatra came into his restaurant and ordered something not on the menu — a pizza. Quickly, he had to come up with a great pizza recipe and this is what's come of it. Check out the recipe for this mouthwatering pizza from Chef Hubert Keller. You learn the whole process, from dough to sauce to baking.

The Battle of Forli: This is downloadable content that fills in the missing pieces and has Ezio defending the town of Forli from the Orsi Brothers. There are six new memories and Leonardo's flying machine makes a return allowing players to fly it across Romagna. Ezio is joined by Machiavelli and Caterina Sforza to protect a Piece of Eden from the Templars. For more info, watch the whole gameplay.

San Marco's Secret: Tomb 5 is not easy, so be careful. Getting into the Basilica without the use of Leonardo's flying machine is tricky. However, chances are that you've already penetrated the massive building's defenses in the mission If at First You Don't Succeed.... But if you haven't yet completed that mission, here's how to get to the tomb's entrance.

Nothing Ventured, Nothing Gained: But everything is on the tightrope. Find Leonardo's new shop in Venice and pay him a visit. He and Ezio move to a rooftop to test out Leo's rad flying machine. As the cut scene ends, you get to play with the flight controls a bit. You don't really have to do anything—in fact, we crashed into the first building we came to (...the controls are inverted...). After you've landed or crashed, the mission is over. For more info, watch the whole gameplay.

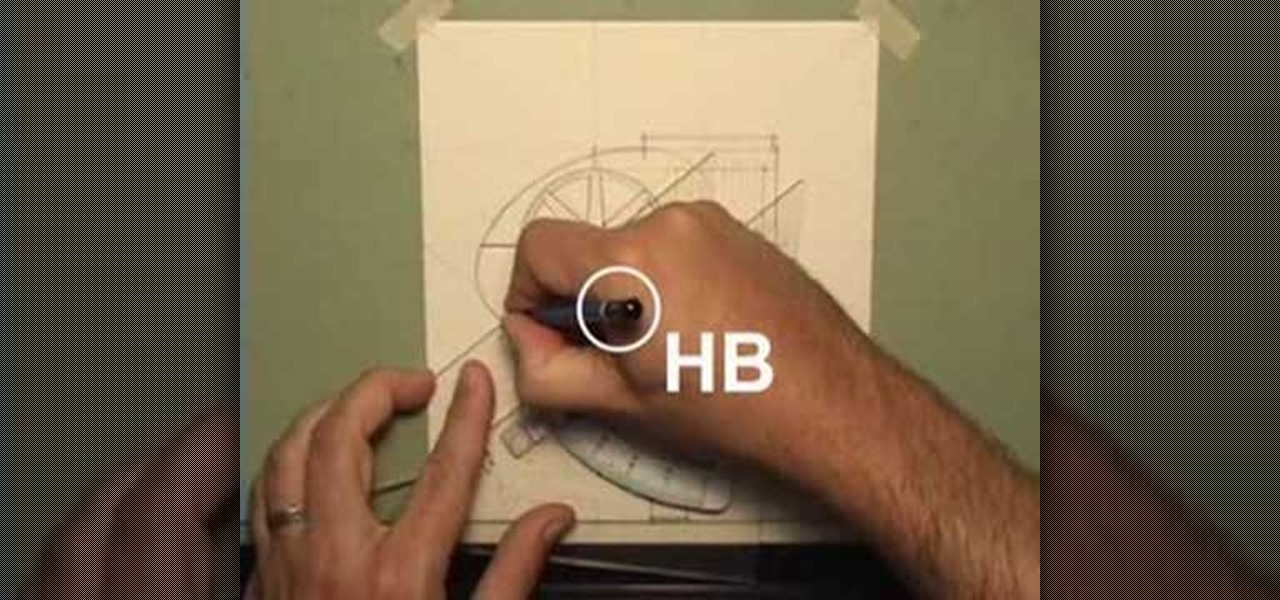
Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw with lead like an architect.

Learn how to do seated one leg presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do hanging leg raises. Presented by Real Jock Gay Fitness Health & Life. Benefits