Songs new and old are given a fresh purpose through the TikTok meme machine, but it can be tricky to figure out where a track originally comes from. Sure, you can tap the name of the song to see the source on TikTok, but if it were a snippet uploaded by someone other than the track's creator, the song title likely wouldn't be listed. Luckily, there is an easy way to figure it out.

Less than a month after the worldwide launch of HoloLens 2, call center consultant BellSystem24 has already prepared an augmented reality solution for one of its clients.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

The marketing team for Marvel Studios is doing "whatever it takes" to make sure you see Avengers: Endgame when it hits theaters in a couple of weeks, including offering an updated set of augmented reality Playmoji for the Playground app on Google Pixel.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Despite Huawei's ongoing battle with the US government, the Chinese company has continued to release phones in the US under its Honor brand. The Honor X series has been consistently released for several years, offering midrange specs at ridiculously low pricing, and the Honor 8X is no exception.

Apple often cites its tight integration of hardware and software for its success. Startup Illumix is looking to do the same thing for AR gaming by building an AR platform for its apps.

Despite the popularity of Pokémon GO, augmented reality gaming hasn't quite caught on yet. The makers of the popular World of Tanks game aren't taking a shot at Niantic's crown yet, but they are looking at giving spectators a new way to watch the game.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Now that the cat's out of the bag, Magic Leap has published videos of a pair of apps that will be available to Magic Leap One early adopters.

With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

What's black and white, sounds like actress Kristen Bell, and is standing in your living room talking to your kids right now? Don't worry, that's just Genius the Panda, an augmented reality character from the Yakables app for iPhones and iPads.

Space might be the final frontier, but NASA is making a detour into augmented reality first. The Spacecraft AR app, developed by NASA's Jet Propulsion Laboratory (JPL) in collaboration with Google, debuted exclusively for Android this week (an iOS version is also in the works).

A very low-key update to the ARCore developer's site has expanded the universe of officially-supported devices for Google's augmented reality toolkit to include the Samsung Galaxy S7, S8+, and Note 8 handsets.

The Galaxy S9 and S9+ have a new camera feature that Samsung is calling "Dual Aperture." On the surface, that may sound like your typical techno-jargon, but it actually has some significant implications for the future of smartphone photography.

The latest and greatest in Qualcomm's long line of mobile processors, the Snapdragon 845, is now set to touch down along with the Galaxy S9 and S9+. And as gorgeous as Samsung's newest flagships are, the processor that powers them under the hood is just as highly anticipated.

So you want to do Kendrick Lamar's "HUMBLE." in Animoji Karaoke, but you need the lyrics. Well, now you can see those rhymes spit out in augmented reality.

Apple has billed ARKit as a means to turn millions of iPhones and iPads into augmented reality devices. The refrain is similar for Kaon Interactive, a developer of product catalog apps for businesses.

While you may not notice them at first, iOS 11 included some pretty significant improvements to the Photos app on your iPhone. These upgrades will help you make your Live Photos livelier, surprise you with photos you totally forgot about, keep your photos and videos organized, and more.

Global design and technology services company Tata Elxsi says it has licensed its advanced autonomous vehicle middleware platform "AUTONOMAI" to a "leading automotive OEM."

While the technology continues to mature, businesses from various industries continue to adopt augmented reality to improve the efficiency of business processes. In this edition of Brief Reality, as conference season continues, we see examples of augmented reality applied to logistics processes and marketing of industrial supplies, as well as the topic of discussion at another trade show.

You would think most people would agree that you shouldn't use your smartphone while driving. Apparently, most people would be liars, according to recent data from the National Safety Council (NSC) and Zendrive.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

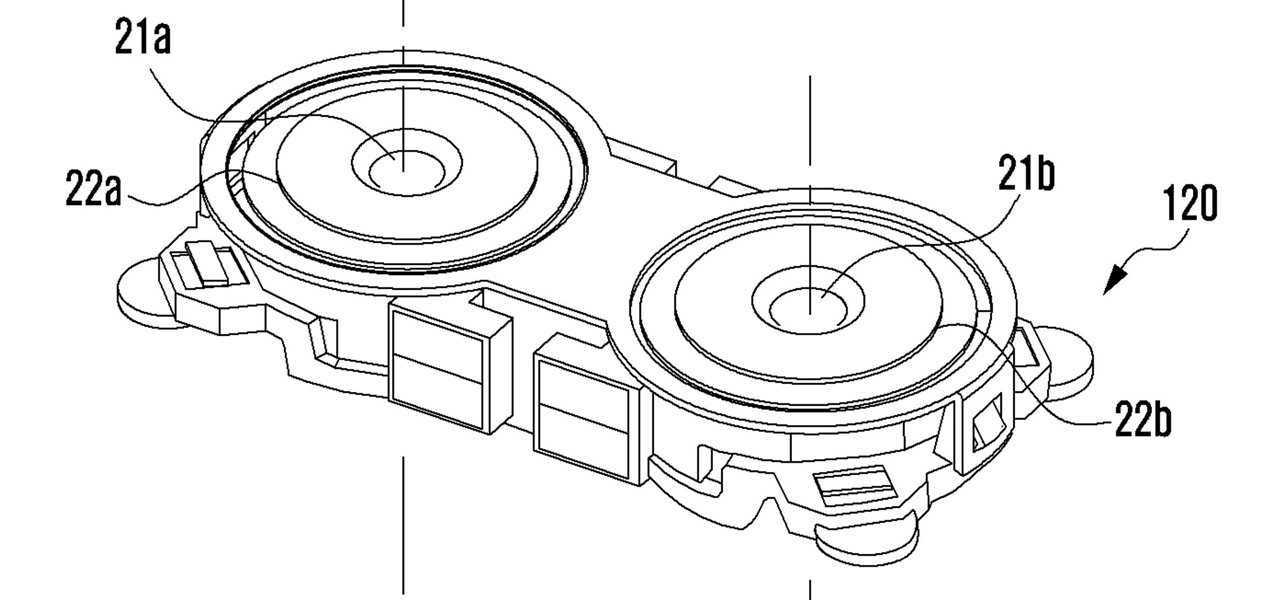
Dual cameras are increasingly popular right now for smartphones, but so far, Samsung has steered clear of all the hype. However, a new patent application shows that Samsung has been working on a dual camera system of their own, featuring tech potentially more advanced than what is currently on the market.

In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our refined hacking Ubuntu container. Before we dive right in, though, let's make sure we still have a functional Docker installation.

At the WinHEC Shenzen 2016 Keynote, Microsoft showed off a system running Windows 10 smoothly on an ARM processor. This could be great news for developers of mixed reality software.

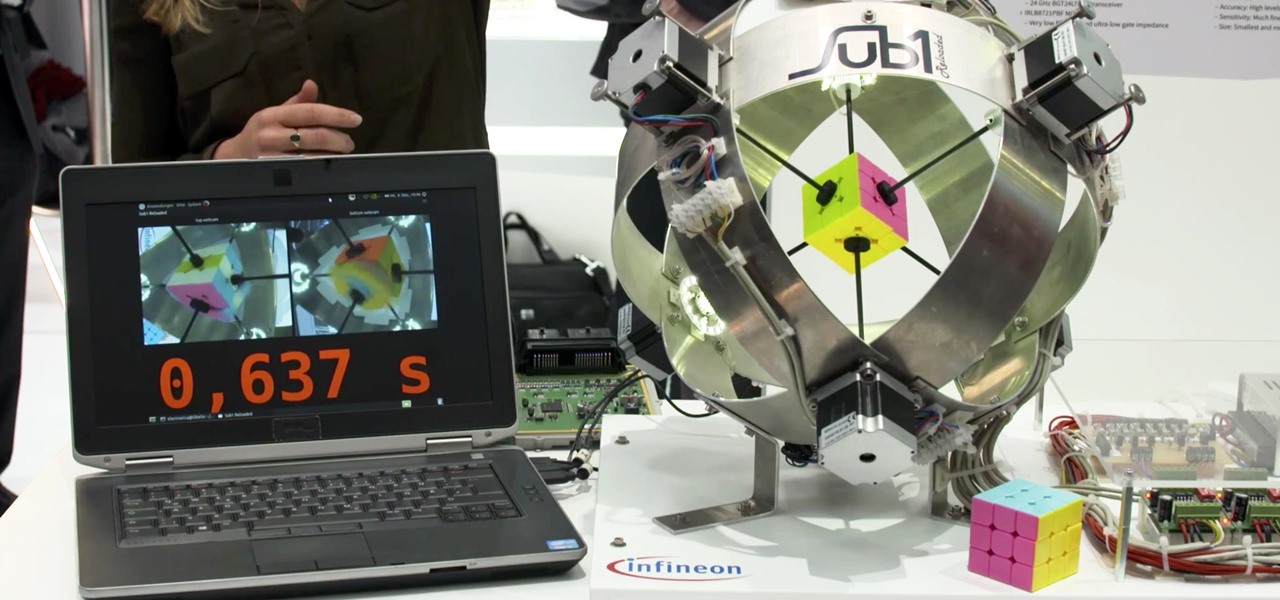
In December of last year, Australian Feliks Zemdegs broke the human world record for solving a Rubik's Cube with a time of 4.737 seconds. Well, this robot did it way, way faster by solving one in under 1 second. Don't tell me a robot takeover isn't real possibility.

In the past, creative chefs and bakers have been rewarded for their daring in the kitchen with viral attention from the internet—like the rainbow bagel or cronut. These sensations weren't crafted for the sake of going viral, but ended up generating an insane amount of buzz anyway.

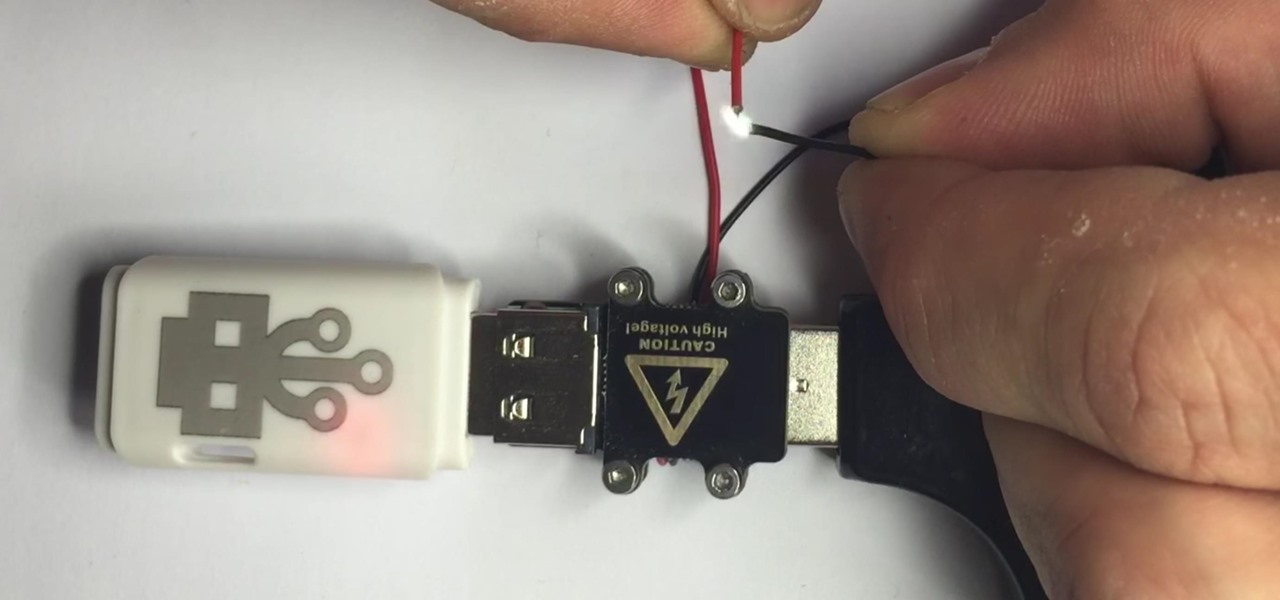
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

We can't be in two places at once, but with virtual touch interfaces we can theoretically use a machine to act as our second body in a remote location. Over at MIT, Daniel Leithinger and Sean Follmer, with the advisement of Hiroshi Ishii, created an interface that makes this possible.

Augmented reality has a variety of applications, but lately the face has been a major point of concentration for many companies. We're all pretty familiar with face swapping by now, but ModiFace employs similar technologies for more practical purposes.

Facebook announced at its F8 Developer's Conference on April 12th that, in addition to the VR-ready Oculus Rift we have today, it plans to bring Augmented Reality (AR) into the fold of their social machine.

For the past three or four months, Microsoft has been pushing advertisements onto the lock screens of some Windows 10 users as part of its "Windows Spotlight" feature. This feature normally shows you scenic photographs and gives you the option to learn more about them by launching an Edge window once you log in. However, the aforementioned users have reported seeing the image below for the new Rise of the Tomb Raider game. Rather than taking you online in Edge to learn about it, you're given ...

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

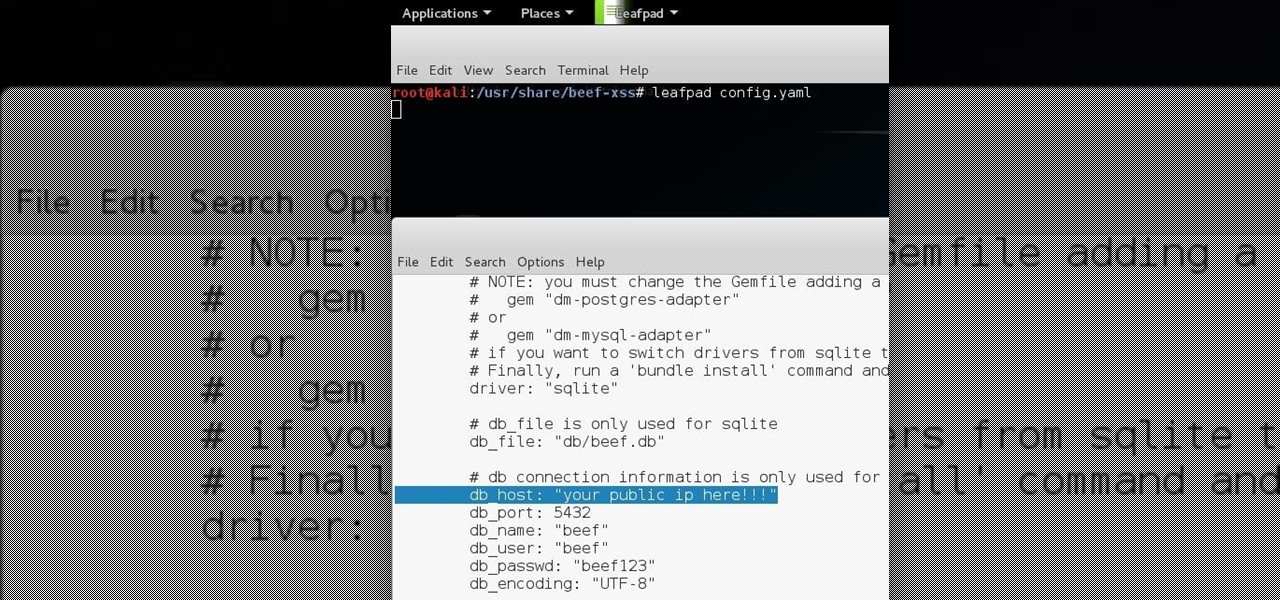
Hello all Just thought id share how ive managed to get beef working over the internet.

The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.