Legendary drum-and-bass artist Squarepusher, the Warp records labelmate of fellow electronic music legend Aphex Twin, is back with his fifteenth album called Be Up a Hello, which is set to drop on Feb. 1.

Whenever a new Apple event invite arrives, the entire tech industry begins tearing the invite's graphics apart in a bid to decipher what the company may be planning on releasing in the coming weeks.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Many of us know that you can make a few bucks from Amazon by helping the company sell its wide array of products, but now there's a very different way to make a buck with the company, and it involves 3D technology.

There's no shortage of augmented reality platforms for remote video assistance, but startup Streem is looking to give its offering a leg up with an infusion of new technology.

As the tech world patiently waits for the advent of mainstream consumer smartglasses, Google is content to stick to the business world (for now).

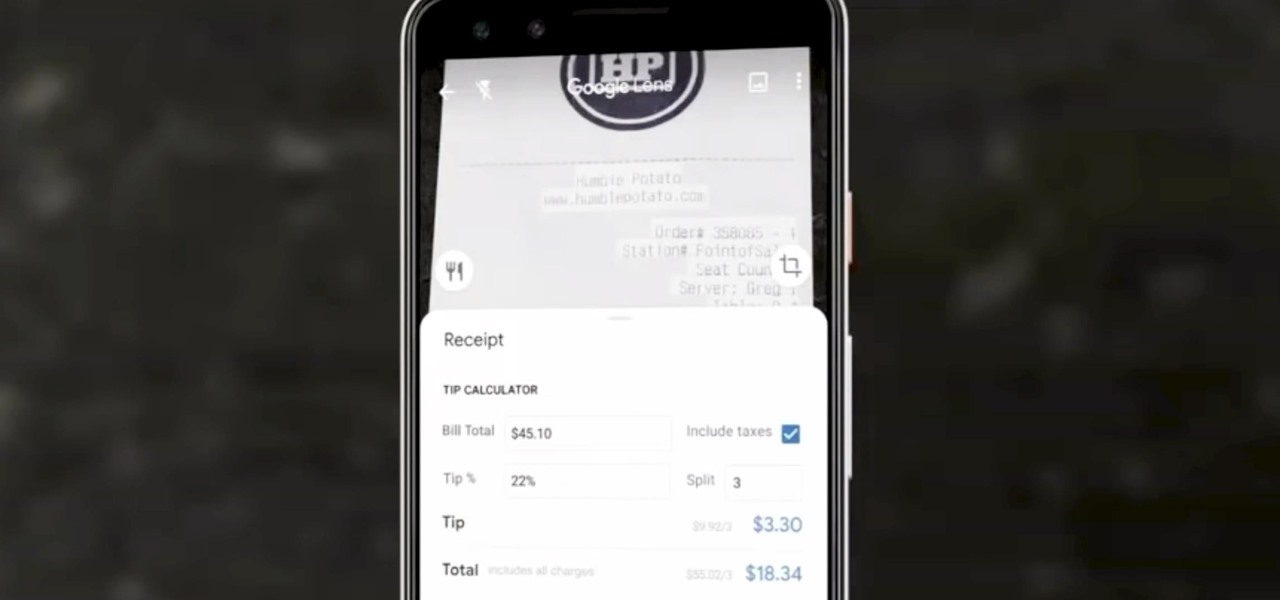
Google Lens can perform many different tasks with your smartphone's camera thanks to advanced machine learning, such as foreign text translations, landmark identification, and business cards to contacts conversion, to name a few. With this year's Google I/O conference, we have another cool Lens feature to look forward to — receipt calculations.

The Avengers aren't the only shiny new toys available to Pixel handset owners, as the animated stars of the upcoming Pokémon Detective Pikachu movie have arrived in the Google Playground app.

The great thing about augmented reality is that so much is possible using the emerging tools and software, your only real limit is your imagination — that includes making real versions of imagined products.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

News junkies who own the Magic Leap One received some good news on Thursday, as CNN has published an app for the headset to display the network's news coverage in augmented reality.

It's confession time. Through a couple of sources, I managed to get an early look at the HoloLens 2. But I was sworn to secrecy, and I take my tech oaths seriously (shame on you, leakers).

With HoloLens and its enterprise-focused software offerings, Microsoft continues to make an impression on companies looking to adopt augmented reality, with Toyota Motor Corporation among the latest.

With barely a whisper of augmented reality during the first day of its developer's conference, Samsung came out swinging on day two with the introduction of its version of the AR cloud and a partnership with Wacom that turns Samsung's S-Pen into an augmented reality magic wand.

Adding another arrow to its quiver of augmented reality acquisitions, Apple has reportedly acquired Spektral, a computer vision company with technology for real-time compositing (otherwise know as the "green screen" technique in broadcast TV and film).

While many of the latest content partnerships announced by Magic Leap appear to lean towards entertainment and gaming, a new partnership with medical technology provider Brainlab has Magic Leap getting down to more serious business.

Snapchat has officially unveiled its Visual Search service for Amazon (teased a month ago), a tool the company began testing on Monday.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Better known among consumers for its virtual reality apps, Jaunt is now pivoting toward solutions for augmented reality developers.

When you drive along the deceptively sedate streets of Silicon Valley, there are few hints that all those nondescript office parks and low-rise buildings contain the very future of the planet, but they really do. On a recent trip to tech's epicenter, I found that out firsthand when I got to visit the offices of Meta, the startup that produced the Meta 2 augmented reality headset.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

With developers chomping at the bit to play with ARKit 2.0, Unity has updated its ARKit plugin to enable access to the new augmented reality superpowers of the toolkit.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Mobile augmented reality developer Blippar's mission is to construct a computer vision map the world, with visual recognition of thousands of notable buildings, bridges, castles, holy places. A major step toward that goal has been taken by the company this month with the announcement of its landmark recognition API.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

While the mainstream consumer market waits for cool augmented glasses to arrive from Magic Leap, or maybe even Snap Inc. (Spectacles 2.0??), AR headset maker DAQRI and its business customers are finding new, money-saving and time-saving use cases for the technology today.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

For some, going to the dentist can be a terrifying experience, but a new use of augmented reality could go a long way toward making the trip feel more like it's worth the orthodontic angst.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

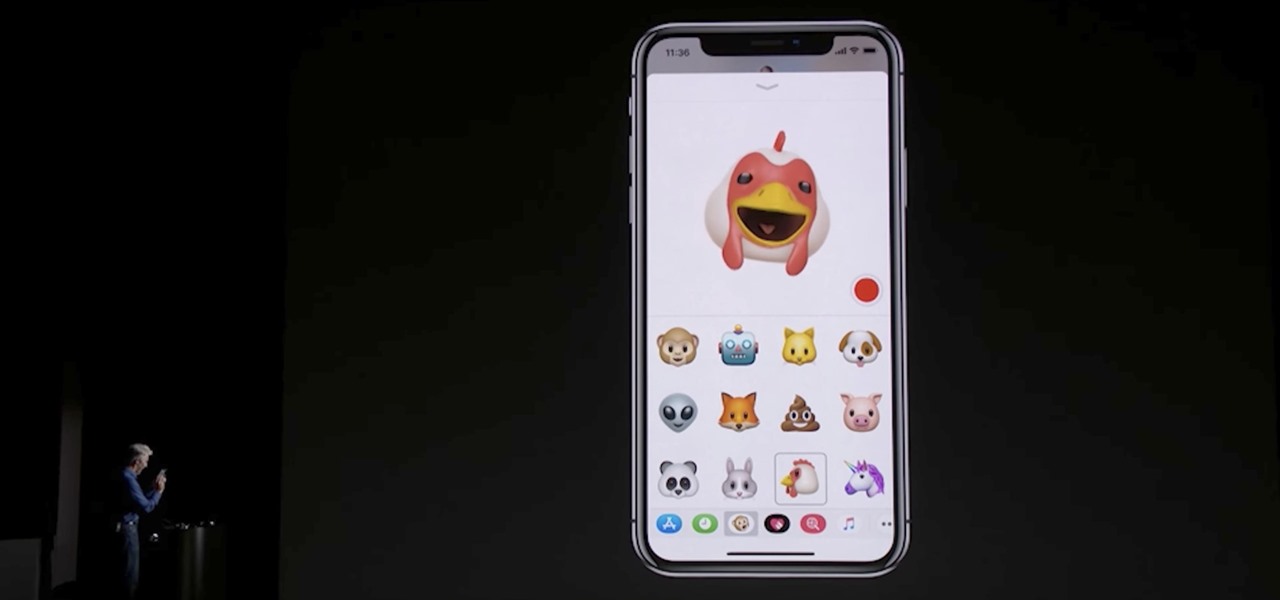
Animoji, short for animated emoji, was a focal point of the iPhone X presentation at the Sept. 12 Apple event. The reactions were split, to be sure, as some considered the attention to this feature on a $1,000+ smartphone to be a bit, well ... too much. As goofy as Animojis may seem at first, the tech behind them is undeniably impressive. In fact, it's possibly the most technically advanced feature of the iPhone X.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

With Apple ready to unleash ARKit to millions of iPhones and iPads and ARCore on its way to supporting millions of Android devices, is there room in the world for a cross-platform mobile AR platform?

Tesla CEO and founder Elon Musk has repeatedly said this year all Tesla models made since October 2016 have the requisite hardware for "full self-driving" capabilities, yet the company has reportedly begun to add a second graphics processor (GPU) to its computer platform for Autopilot — without officially saying why.

Intel's driverless division will be managed by Israel-based Mobileye, as the chip giant emerges from relative obscurity in the driverless space to become a major supplier after completing its $15.3-billion purchase of Mobileye this week.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.