Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Greetings my fellow hackers.

This cardmaking tutorial shows you how to make a floral Christmas card that is complete with embossing using a die cutting machine. This is a very pretty card and once you have seen the tutorial you will see how easy it is to make. I also show you how I get the embossed lines around my cards to add the pearl drops using a box embossing board.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

Like a strong-tasting cup of joe, but want more caffeine out of it? Start double brewing your coffee. To paraphrase a big fan of the double brew process on Reddit, it'll make you feel like you can throw an orange at 60 percent the speed of light. It's that strong. Really.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

This step-by-step tutorial will show you how to install Mac OS on Windows 7 on Virtual Box. Video: .

The motor coupling goes between the motor and the transmission. If it fails the washer will not spin or agitate. If the washer fills with water but then does not agitate, but you hear the motor running, the coupler could be the problem. You may hear some clicking noises as the broken pieces spin around. You may also see a pile of black rubber pieces on the floor under the middle of the machine. You can follow the steps in this video to help you do the repair.

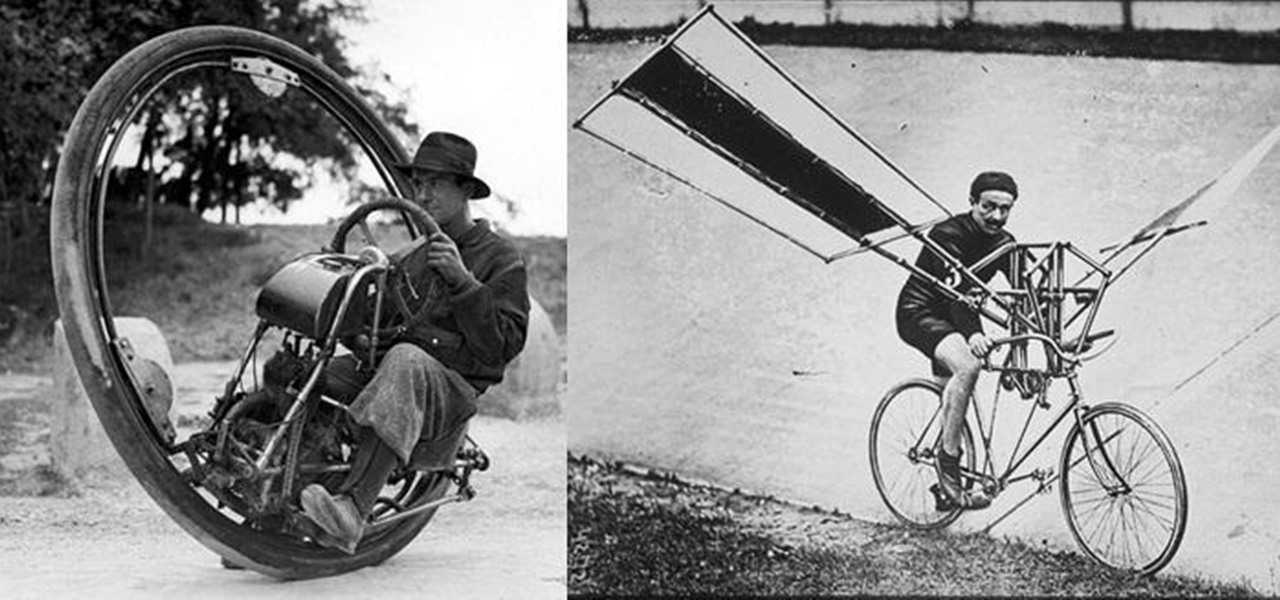
We don't spend much time thinking about bicycles today, do we? Sure, they're a "green" alternative to driving everywhere in cars, but the vast majority of America has dismissed them as simply being too much work, or more importantly—too slow. That wasn't always the case, though, I assure you!

This video gives you a step by step tutorial how to recover the seats of your car. If you are a little familiar with sewing, this is easier as you imagine. All you need for this repair is new fabrics and a normal sewing machine.

Ever wonder how to make an engine out of soda cans? Not even sure if it's possible? These videos will show you how to build a working Stirling engine out of cans and other general materials. Here it is in action:

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

In this video clip series full of instructions and advice for sewing and using a Serger, you will learn how to use the controls, the parts of the machine, threading techniques and much more.

Parts of the Rowing Machine: Exercise & Training on Health & Fitness Equipment Part 1 of 15 - How to Do rowing machine exercises.

D.J. Brasby discusses on this series of videos how to use an Akai MPC drum machine. Part 1 of 14 - How to Use an Akai MPC drum machine.

In this tutorial video, learn how to get started using the Akai MPC 2000XL drum machine. Our expert music producer, Amir Tauheed, will give you a tour of the basic interface for the MPC, and then show you how to load, chop, and slice samples, layer a beat, use the sequencer, and create a basic hip-hop beat of your own.

Anne Beckett is going to take you through this 15 part series on how to set up a custom embroidery design on a machine embroiderer. In this first part she'll cover how to tell if your design is good for the embroiderer.

Learn how to model the infamous drive-by shooter, the Mac 10, in MAXON Cinema 4D. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, including complete instructions, watch this 3D modeler's guide.

In this tutorial, we learn how to make cotton candy with a cotton candy machine. First, you will want to take your choice of flavored sugar and pour it into the top of the cotton candy machine. Next, you will take your paper cone for cotton candy and place it in your hand. Turn on the machine on and when it's heated up and sprays out sugar strings, move your hand quickly around the machine and gather the cotton candy up with the cone! You can enjoy as soon as it's done and layer different fla...

This is an instructional video on how to thread a circular knitting machine. For the demonstration, the circular knitting machine by Innovations serves as our example. Tips are provided based on the experience of a seasoned machine knitter accustomed to using this machine.

Creating drum beats is a crucial part of making a great song. Learn how to use Logic Pro 8 Ultrabeat drum machine feature to create and mix your recordings in this free music production tool tutorial from a professional audio engineer.

Paper or plastic is a thing of the past; both options are equally terrible for the environment. With this tutorial, learn how to turn your old bed sheets into funky grocery tote bags. You will be the envy of everyone at the store with these adorable, homemade bags.

Do you believe you just don't have an intuitive sense of math? Sadly, this is the case for many people. The reality is that math is learned with practice. No one is born with a math gene making them more intuitive than others.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Smartglasses maker Epson remains the top gun in the drone market with its Moverio line of wearables, and the company is further elevating its offerings with its new Drone SoAR app for DJI drones.

While mobile gaming, in the 10 years since the App Store launched, has matured to console-level quality, premium augmented reality games built with ARKit (or ARCore) have been scarce.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Microsoft's Monday keynote introduced the fourth generation of the company's Kinect sensor during Build 2018 in Seattle.

With the heavily anticipated installment of the God of War game series arriving on April 20, PlayStation has taken the opportunity to make its first foray into mobile augmented reality with a companion app.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

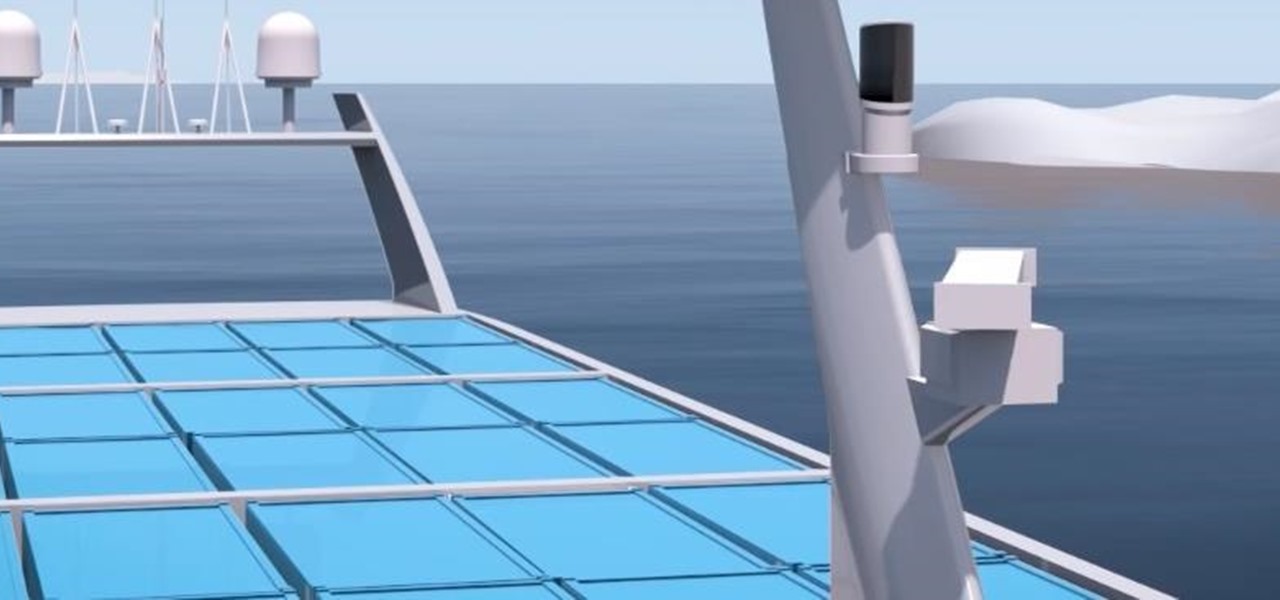
A Norwegian carrier's launch of a pilotless container ship next year could lead the way to a new era in sea transportation and shipping if successful.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

The National Transportation Safety Board (NTSB) said it is still investigating the circumstances of a fatal Tesla crash last year to determine if the car or Tesla's Autopilot driverless system was at fault, but revealed more details about the circumstances of the crash.