Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

In 2018, notches are the hot trend with smartphones. Essential was first to release a phone with a notch in mid-2017, but Apple kicked off the fad in earnest with the iPhone X. Unfortunately, unlike the iPhone X, every Android phone with a notch has a noticeable bottom chin. Let's take a deep dive to find out why.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Some types of bacterial infections are notoriously tough to treat — and it's not all due to antibiotic resistance. The bacteria themselves are rugged and hard to penetrate with drugs.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

I was on our new #nullbyte IRC channel when someone told me how tedious it is to install an OSX Virtual Machine on Virtual Box (I think it was wawa). We all know Linux rocks (gets acknowledgement from the crowd), but there are morons out there, multiplying at a never before seen rate, who use OSX. We at nullbyte should be prepared for anything and everything. So, in this guide I take you step by step to creating your OSX Yogemite VM.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

What type of person are you in group settings? Are you the social butterfly, eager to get to know everyone and interested in the people more than the setting? Or are you a wallflower, afraid to catch anyone's eye out of fear?

I have never been a morning person, and that's a trait that I don't think is going away. Combine my distaste for early hours with being a heavy sleeper, and it adds up to a lot of alarms being dismissed in a haze, with no real intention of ever waking up.

Unless your work clothes require dry cleaning, you probably only go to the cleaner a few times a year. And for those few items in your closet for which you do, you have to then find the time and extra budget to make a trip all the way to the cleaners and back again. In the end, it can be quite the hassle.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

This is a video showing how to make a perfect latte at home. First the coffee is ground and then she pours some milk. The presenter says that 1/3 of the daily requirement of milk can be found in a latte. Once the coffee is ground it is brewed. She uses a lot of coffee so that it is richer. While the espresso is being made, the milk is steamed. The espresso should drip out like honey. The steamed milk is then poured over the coffee.

Watch this instructional knitting video to bond a vinyl hem with a knitting machine. Hang an elastic or ravel cord and push it against the bed. Fold the hem over the ravel cord. If you knit with a knitting machine, this is an essential trick for getting started with larger projects.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to decrease the size of your knit piece. Use a single prong tool to unhook and tie off a single stitch on either side of the piece before completing each row to gradually decrease the width of the knit work. You may want to reference written instructions in addition to watching this knitting video.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. This is a demonstration of how to use a knitting machine to weave a cast on. This is a cast on that many people find difficulty with. You may want to reference written instructions in addition to watching this knitting video.

This is the final step of learning how to sew on a vintage Kenmore sewing machine. Watch this how to video to learn how to sew a straight stitch on a this type of sewing machine. Run the motor as you press the reverse button, this locks up the thread.

Using a sewing machine entails knowing how to fill a bobbin with thread properly. This sewing how to video will show you how to fill a bobbin on a vintage Kenmore sewing machine. Happy sewing!

This flower arrangement tutorial shows you how to make a candle centerpiece using a pick machine. A pick machine attaches steel picks to the stems of your silk flowers. This makes arranging your flowers in floral foam much easier. Watch this how to video and you will be making this beautiful candle flower arrangement in no time.

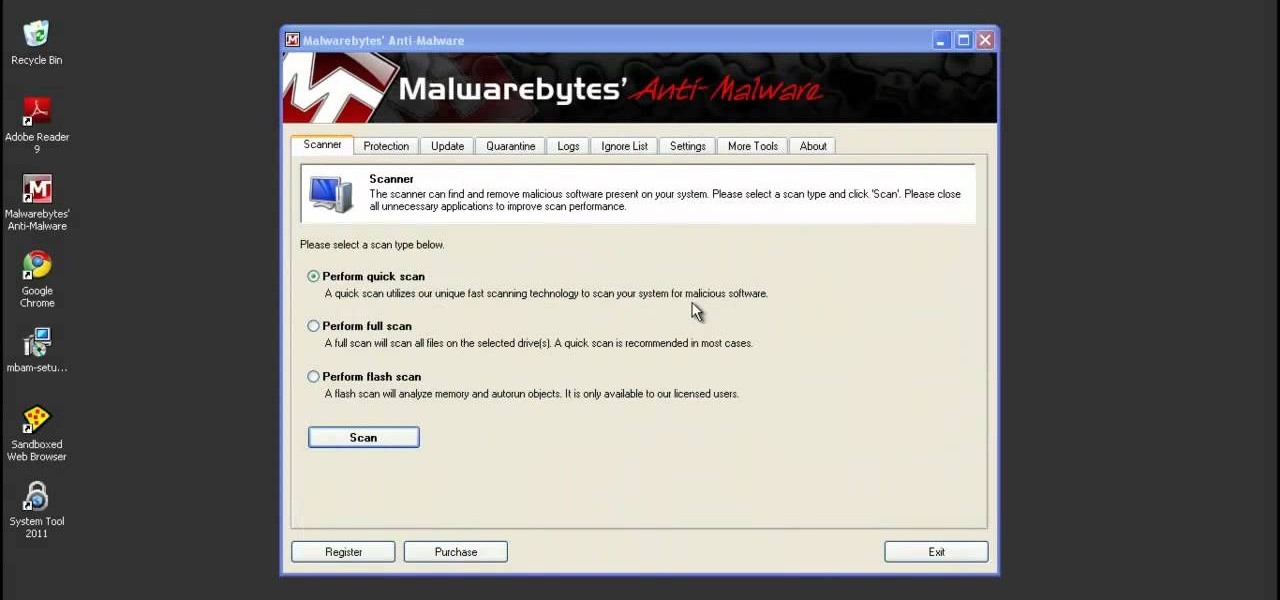
System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.

Circle or infinity scarves became really popular this year, and this little how-to shows you how to knit one up yourself. Knit 1, perl two. You can do it! Follow the steps and fight that cold neck feeling!

Late in the Dwarf Fortress game building machinery can allow you to pump water around the map and power mill stones to make more advanced food. This video will show you how to build and use machines safely, without destroying your fortress and the lives of your dwarves.

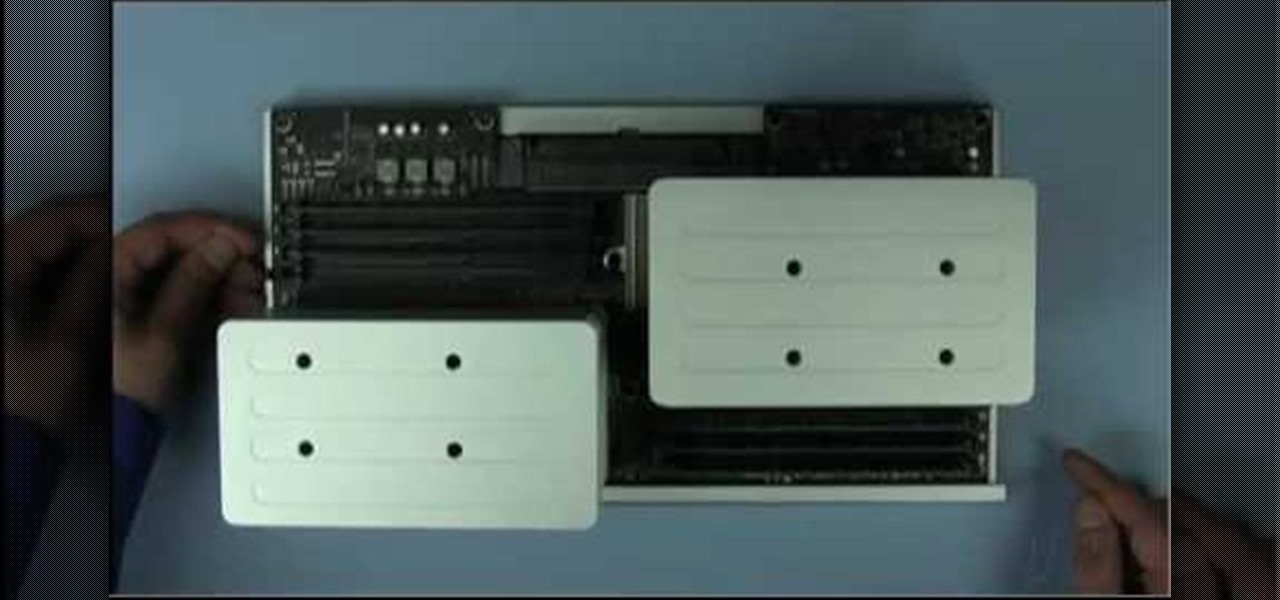
MacOSG demonstrates how to install memory in a 2009 Mac Pro. When performing this upgrade, be sure to take precautions for static by discharging static electricity before beginning. Shut down, unplug and place the Mac Pro on a static-free surface. To access the memory, you need to open the side access door by lifting the latch located on the rear of the Mac until it locks in the open position. You can then the door forward and then remove from the body. The memory is attached to the processor...

What's better than one prank? Five pranks! This video from the notorious Kipkay provides five fantastic, funny, and facile pranks to pull off on your friends and family… maybe even your enemies.

In this video Sarah Magid shows how to make dark chocolate cupcakes with espresso butter cream along with sugar flowers as follows:

Release your inner wild thing with a costume based on the classic children's book. You Will Need

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

Watch this video tutorial from the Polish Guy to see how to polish a stainless steel roller using Autosol. In this polishing tip we polish a stainless steel roller using Autosol Metal Polish. The tutorial includes detailed work instructions and best practices.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Watch this instructional knitting video to hang a knitted hem. Add weights the inside of a hem to keep your knitted piece straight. If you knit with a knitting machine, this is an essential trick for getting started with larger projects.

Use the Martelli Stitch in the Ditch Binding Foot for top stitching and with a double needle to get a professional finish to your quilting and sewing projects. Watch this video sewing tutorial and learn how to top stitch with a double need on a sewing machine.

This Mig Welding Video Demo shows how simple and easy it is to use a MIG welding machine. Mig Welding Machines are use throughout the world. They are the suited for many welding applications. This video demonstration demonstrates Mig welding by welding two pieces of sheet metal together. Watch this video welding tutorial and learn how to fuse two pieces of sheet metal together with a Mig welder.

Watch this video from the Concrete Network to learn how use a buffing machine and its accessories.

This video demonstrates how to hook up a washing machine. This can save the high price of hiring a handyman.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.