Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Watch this instructional knitting video to hang a cast on comb on a knitting machine. Watch this video a few times to master this little trick. You may want to reference some written knitting instructions in addition to following these visual guidelines.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. Use a three prong tool to twist a stitch. Once you set the twist, you can knit an entire stretch of fabric with an elegant twisted stitch pattern. This creates a light knit with open spaces for a warm yet breathable garment.

If you use a knitting machine to knit your projects, follow this simple example to knit ribbing. This instructional knitting video demonstrates how to e-wrap for double bed knitting and transfer the carriage. You may want to reference some written instructions in addition to watching this knitting video. With a little practice, you can make it look as easy as this.

While any form of gambling is set up to make you lose, there are some tips and tricks, shown in this how-to video, to help even the playing field. Penny arcade slots are a reasonable place to start, as the stakes aren't too high, so neither side (you or the arcade) has that much to lose. Watch this video conning tutorial and learn how to beat an arcade penny slot machine.

Watch this video sewing tutorial and learn how to use a ruffler attachment on a sewing machine. Use a ruffler attachment to sew small individually adjustable tucks.

An important part of sewing involves knowing how to make button holes. This sewing how-to video demonstrates how to cut a button hole and insert a button footer on a vintage Kenmore sewing machine. Watch and learn how easy it is use a Kenmore sewing machine to make button holes.

This video tutorial shows how to use the Cuttlebug paper embosser. Learn how to make embossed designs in paper projects with a Cuttlebug paper embossing machine.

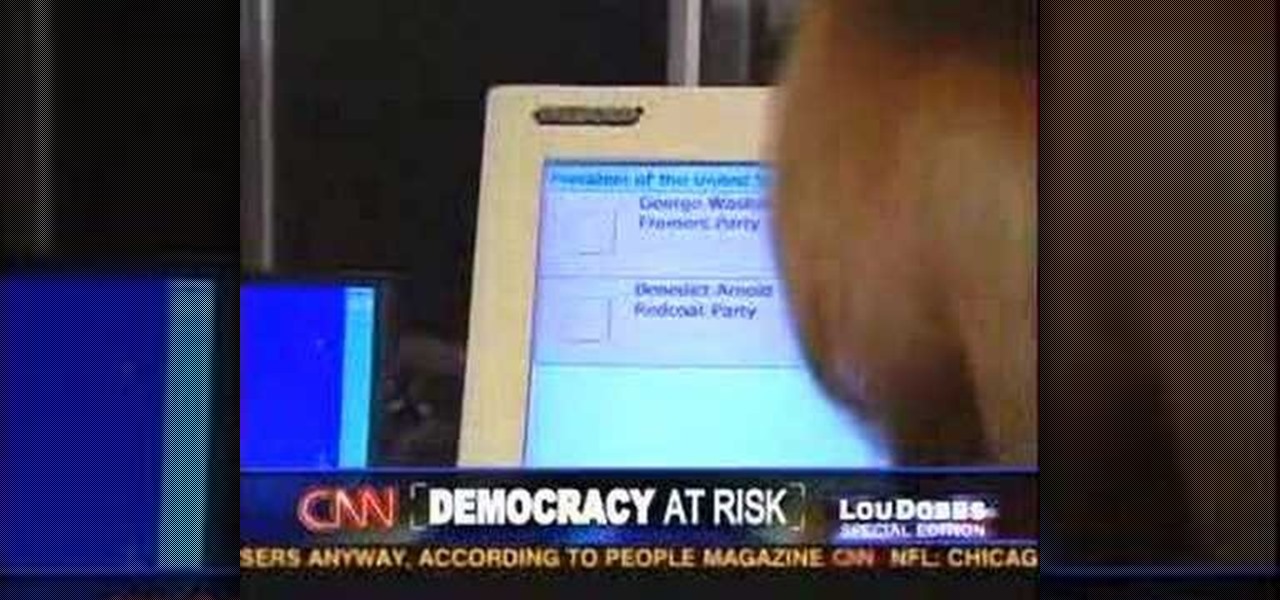
It only takes a minute to steal a U.S. Election!

Learn how to use the Miller Concrete Landscape Curbing Machine. You will also learn the basics of making curbing mix.

You can learn how to use the stock market as your own ATM machine. You can make 500 dollars in less than 15 minutes. Then you can take that 500 dollars and use it to get professional advice.

In this video series, our expert shows you how to operate the common stair step machine. Though the stair stepper has amazing potential to burn calories, it can be dangerous if not used properly. Sheila Lindsey illustrates the proper way to use the stair master machine. She also shows you how to monitor and stay within your heart rate. Shelia also gives you great advice on organizing a cardio workout routine. So, before stepping up to the challenge, learn how to get the most out of your stair...

No pain no gain, ladies and gents. If you want a fabulous body, trying to take the easy way out by trying those hokey "As Seen On TV" exercise machines or just by starving yourself is going to get you nowhere fast. Neither serve to encourage long term weight loss results, and while you may lose weight, most of that weight is going to be loss of muscle mass because you're not exercising.

When you clean the carpet in your home or apartment, it seems like that dirt just comes right back the next day. It's never really clean. Well, that could be changed with a deeper clean. Deep-cleaning your carpet can offer benefits including getting rid of dust mites and allergens. Not to mention dirt.

It's amazing what you can create with a few, everyday household and office supplies. Most of these items are already sitting in your junk drawers, so there's no need to spend money! Kipkay shows you 4 awesome hacks you can make in this "household hack pack" video.

In this how-to video, you will learn how to create your own tube top dress with lace and tulle. This will be useful if you need a unique dress for prom. You will need a sewing machine, scissors, pins, ruler, measuring tape, thread, a half yard of gray knit, tulle, and a yard of lace. First, cut out a rectangular piece that can fold in half. The lower half is a trapezoidal piece. This will be the jersey skit. The smaller end should fit around your waist. Lay the rectangle first and then put th...

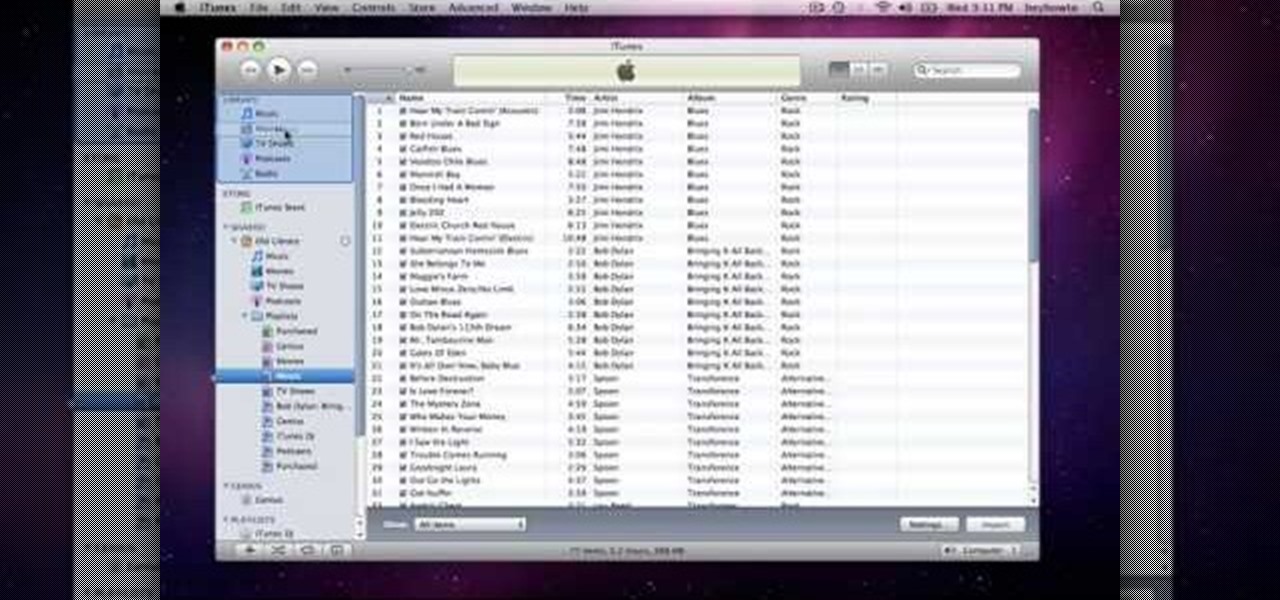
How to use Home Sharing in iTunes 9 to transfer music files to another computer. First make sure both computers have iTunes version 9 installed. To check this go to the iTunes 9 menu next to file in upper left and select the about item. On windows machines this will be in the help menu. In the computer with the music files we need to make sure the iTunes library is nicely organized. Again go to iTunes menu, this time open the preferences menu, and advanced icon. Check mark both sections "Keep...

You can add USB ports to your PS3 at home. Put two new ports onto the back of your PS3 for a total of six ports to get even more out of your machine. You will need a basic knowledge of circuitry and some electrician equipment to do this the right way. This video will show you how to add USB ports to your PS3. Keep in mind that this video does not show you how to reassemble it so be sure to keep track of your work.

Southwest Yard and Garden teaches viewers how to prepare garden soil for planting. You can use compost to work this into your soil. You can make your own compost and you can also buy compost. First, you can use a flat bladed spade or a sharp shooter spade to double dig your garden soil. First, you should dig double deep into the soil and turn the soil to the side. What you want to do is dig a trench. Go back to the beginning of the trench and dig a second depth. You will want to get below the...

This video on typhoon preparedness comes from Andersen Air Force Base in Guam, where typhoons are common. The key to surviving a typhoon or other disaster is preparation. Stock up on enough food and supplies to last your family for about a week. Routinely check expiration dates on food, water and batteries and rotate your stock. Be sure window screens are in place and in good condition in the event the power is off for several days.

Master Gardener Rosamarie Maddox asks John White, Doña Ana County Extension Agent, about problems facing her pecans, grapevines, and native shrubs. An unidentified insect found on her pecan tree is identified by John White as a Twice Stabbed Ladybug. This ladybug is a useful insect that often over-winters on the tree and helps takes care of the aphid problems faced by pecans. Pink fuzzy coating on pecan nuts is also brought up. The coating is normal for pecan and contains bitter tannin. Too m...

Blue corn is a special variety of corn which can be differentiated by the majority of the corn species by looking at the unusual top growth of the corn. It is a hybrid and grows very uniformly throughout. Now take a corn from the field and peel it off. You shall notice that it has a blue color corns. Blue color corns are hard from outside but they are very soft and tender in the middle. You can use these blue corns in making commercial products like blue corn chips, tortillas, and atole ’,‘ c...

This video tutorial demonstrates tips for how to organize your home office when you are visually impaired. Here a rehabilitation specialist is helping a visually impaired person. The person who is visually impaired should know what is visually important to him/her. Mostly these people obviously need to know where every thing is because they don’t have their eyes to depend anymore. Here visually impaired person is 66 year old Deanne Jackson. She has wet macular degeneration. In order to set up...

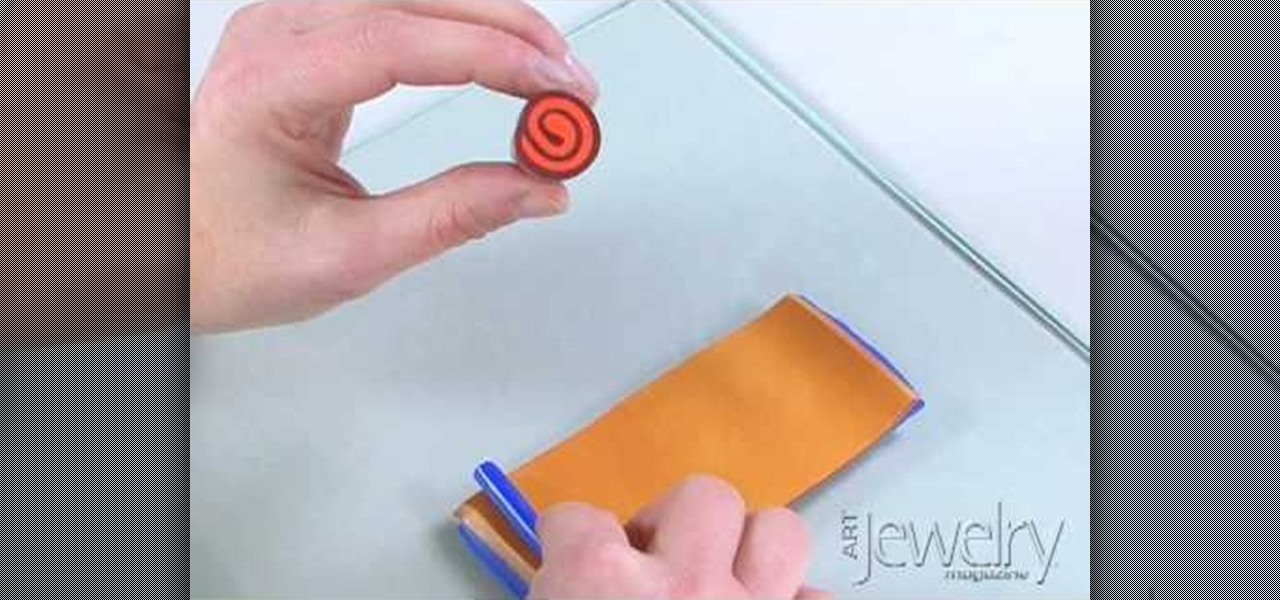
Jill Erickson from Art Jewelry Magazine demonstrates how to make a Jellyroll cane with polymer clay. Condition two different colors of clay by running them through a pasta machine set on medium. Then, trim off any rough edges. Stack the clay on top of each other and place a little bit of pressure on it to confirm the two layers. Using a blade slightly bevel the edges. Slide the blade underneath the two layers of clay for easier handling. Place a think snake of clay in the contrasting color on...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

It's no secret that Google is all about AI. In their eyes, machine learning is the future of software development, and you can see evidence of this all over the last couple Android updates. They've used it to power all sorts of features in their Pixel phones, and they've even donated some of their AI smarts to AOSP for all Android manufacturers to share. But it looks like Samsung isn't exactly on board.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.