If you've ever played the game of Would You Rather, you've probably been given the ultimatum between eating insects or doing something else that sounds absurd, like licking a cactus. I'm advising you to always choose the insects, and here's why:

Whether you're heading to a frat party, out for Halloween or just looking for a cool way to tie your towel at the beach - this video is here to help! Learn how to tie a toga, the ancient Greek way of dressing, and be ready for whatever costume situation may arise with a quick and cheap outfit!

Summer is just around the corner and those jeans that seemed perfect for winter aren't looking so hot. Put those jeans to use, and make your very own jean skirt. Grab a pair of scissors and a sewing machine and get started.

See how fast and precisely you can transfer glass onto the mandrel using our electric mandrel spinner. An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. This video shows you how to build transfer glass from the cane using a lampwork torch and an ele...

This video shows the features of the Deluxe electric mandrel spinner. An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. This video shows you how to use all of the features of an electric mandrel spinner.

See how you can quickly, easily, and consistently you can make uniform lampwork spacers using the Electric Mandrel Spinner. An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. This video shows you how to make glass spacer beads using a lampwork torch an...

Here is a tutorial on getting a perfect 1/4" seam allowance for quilt piecing. The sewing machine foot will sometimes have a groove to allow you to make a perfect quarter inch seam automatically. If you don't have one of these, there are a few ways to make your own quarter inch seam guide.

This video animation tutorial demonstrates a technique for creating a fabric-like effect out of clay for stop motion figures, or armatures. Instead of smooth clay, try to give a more authentic finish to clay that will be used to create clothing. This technique will also create patterned fabrics. You'll need to chop the clay up first in a food processor, and then put it through a pasta machine. Watch this instructional video and learn how to make clay look like fabric for claymation armature c...

Check out this tutorial that teaches you how to make a cotton reusable grocery bag out of bandanna. All you need is 2 bandanas, sewing thread, a sewing machine, scissors, and marking pens. This is a great, fashionable way to go shopping and cut down on plastic bags. Watch this how to video and you can save the earth in style with reusable grocery bags.

This video will show you the proper technique for getting your snowmobile out of the snow after it falls and gets stuck in a snowdrift. Snowmobile safety is important and this video will show you just how you can keep your machine out of the snow.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

With the success of Iron Man in 2008, a video game adaption quickly hit the market, so it's no surprise that when Iron Man 2 came out this year, that a video game would follow close behind. Sega released Iron Man 2 in a variety of gaming formats, including the Xbox 360, PlayStation 3, PlayStation Portable, Nintendo Wii, Nintendo DS, along with iPhone and other mobile devices. The story of the game takes place after the plot of the film, except the iPhone game, which mimics the movie's plot.

Tech-savvy programmers and developers usually apply their unique talents exclusively to creating apps and websites — two high-paying and exciting pursuits that can open countless doors and opportunities in multiple fields.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

The Pixel 3 XL versus Galaxy Note 9. Stock Android versus Samsung Experience. When I began this comparison, I thought the Pixel 3 XL would be unfairly outmatched. But after looking at the specs side-by-side, you'll see a different picture. This year, Google delivered a worthy alternative to Samsung's best offering.

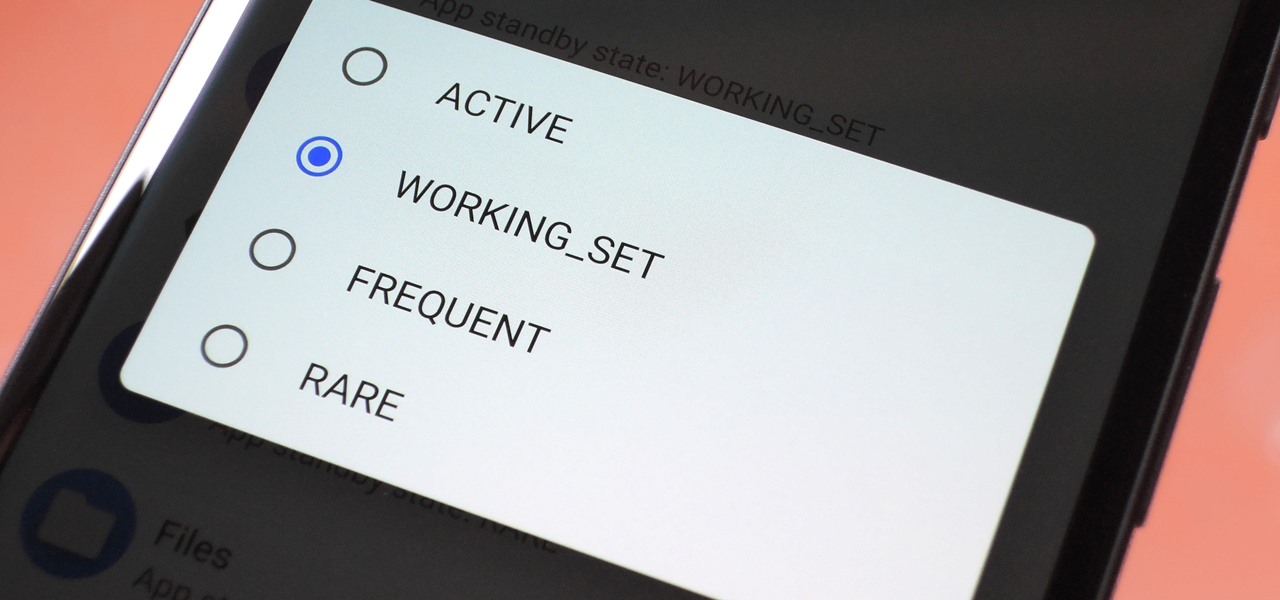
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Mobile World Congress is a four-day event that is both a showcase and conference starring prominent figures in the mobile industry. Oftentimes, OEMs will use this event to announce new products for the upcoming year — and this year shouldn't be any different. Here are all the phones we expect to be announced.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.