I have owned quite the plethora of electronics in my life. A commonality between most of these devices' screens is frozen or dead pixels. This is probably the most annoying thing about buying new hardware—your LCD, or worse, LED display has one or more pixels that continues to stay lit. Most of the time, this will appear in the form of a brightly colored pixel that never changes, or a pixel that never displays the right color. Once you notice it's there, you just can't stop staring at it. It ...

There are many ways to jailbreak the iPhone, found all over the internet. This method explains how to jailbreak the iPhone or iPod touch using Quickfreedom 2.0 BETA on a machine running Windows Vista.

Expert tattoo artist Rick Wyckoff offers a wealth of knowledge on the history of tattoos, explains how the tattoo machine works, and offers tips on how to care for a new tattoo, how to preserve the pigment, and how to deal with the pain that comes with being tattooed.

In this series of online video tutorials you'll learn how to use Reason 3.0 music recording software. Expert Jerus Arte demonstrates how to use the program, from installing it on your computer and setting it up with the right preferences, how to control the master volume, and how to use features like the NN-19, the NN-XT, the Dr, Rex loop player, and the Redrum machine. He shows you how to use effects like the compressor and reverb, and how to mix down your song into a format that can be burn...

Mosaics are a cool type of art. You can use mosaics to liven up your home or garden and they are cheap and fun to make. Check out this video for tips and instructions for making mosaics.

It’s easy to gain a little extra weight in college but there are ways to defy this weight gain trend. It won’t work without will power but you can limit your unhealthy food intake and sneak in some unconventional exercise routines.

In these music studio recording and production videos, learn how to use a 4-track reel to reel tape recorder to capture your vocals, guitar parts, drums, record songs, or even make a demo CD. Our expert will walk you through the operation of a fairly simple reel to reel machine in several steps, including the basic and advanced functions, rear components, using mics and connecting to other mixing boards, recording on four different tracks, mixdown, bouncing tracks, and final tips for masterin...

In this tutorial video, learn how to use the audio sampling features of the Akai MPC 4000 drum machine. Our expert music producer will give you a tour of the basic interface for the MPC, and then show you how to load, chop, and slice samples, use the sequencer, and create your own samples and sequences for your music.

In this informative video clip series, our expert seamstress will show you everything you need to begin a sewing project either by machine or by hand. Learn how to measure fabric and what types of measuring devices are available, see the types of scissors, rulers, thimbles and pins are available to choose from, and get pointers on fray checkers and seam rippers. Everything you'll need to begin a sewing project is right here!

In this DIY home improvement video series, learn how to pressure wash the exterior of your house—as well as the sidewalks, driveway and deck. Our expert will show you where to get a pressure washing machine, how to hook it up, what wands and tips to use, and how to start the pressure washer. Then follow him as he takes you around the house—from roof, to eaves, to windows, to exterior walls—showing you the proper pressure washing techniques for cleaning. After watching these videos, you should...

In this series of expert videos, you will learn more about lawnmower maintenance. Watch these videos to see how easy do-it-yourself lawnmower maintenance can be! You will learn how to clean your lawn mowing machine, and keep it free of dirt, rust, and grass clippings. Get tips on changing the oil and air filter on your lawnmower. Learn how to mix two-stroke fuel for your mower. Watch as our expert removes gas, foam filters, and dirty spark plugs from a lawnmower. When changing the blades of y...

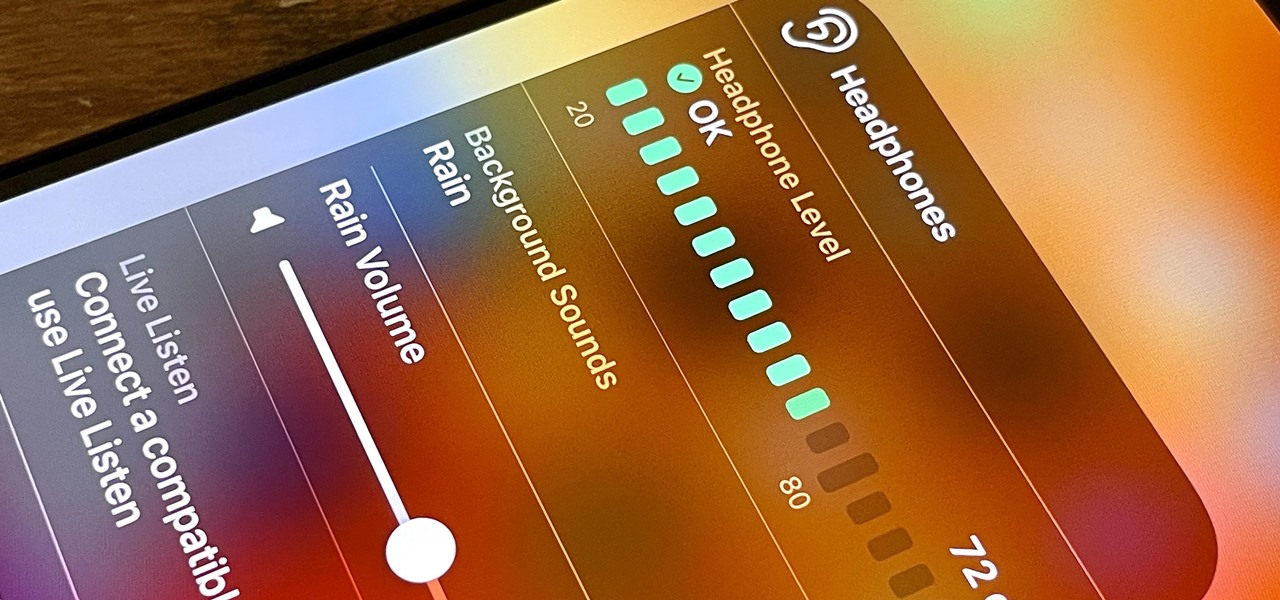
If you get distracted or stressed out easily, your iPhone might be able to help you focus or calm you down. It can even help you fall asleep with white noise, and you don't have to install a third-party app or buy an audio track to turn your iPhone into a personal sound machine.

The top five apps of the 2010s were all social media apps of some kind, and the fact that's not surprising to you says a lot. We may use them for other reasons here and there, but our phones are social media machines at their cores. The thing is, some make better machines than others.

It's always a big deal when the company that makes Android releases a new phone. Google's Pixel series has made a name for itself in three short years behind its camera prowess, but now it's time to start competing with the major players. That said, Google should like how their Pixel 4 and 4 XL stack up against the iPhones and Galaxies of the world.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Skulls. What spooky Halloween décor or staging of Hamlet is complete without a skull or two popping up? For ghoulish special effect and/or setting a dramatic scene, skulls are absolutely integral. Well, with some artistry, hardware supplies, and a good dose of patience, you can create your own inexpensive prop skulls for use however you please.

This video illustrates the method to removing 3D acrylic nail art without a drill machine. This process is composed of the folowing steps-

In this series of health and fitness videos you’ll learn how to use a pilates reformer and several exercises you can do with the machine. Expert April Plank shows you how to do a number of pilates exercises, including leg circles, bicep curls, roll backs, and Y position exercises just to name a few.

These are some tricks for advanced computer use. These are PC only and meant for use on Windows XP machines.

Apple's Live Voicemail lets you preview what an incoming caller is speaking to your voicemail system in real time. It's a revolutionary feature like Visual Voicemail on the original iPhone, only better since it helps you screen calls to quickly decide whether to answer or ignore callers. It's similar to answering machines, whose popularity peaked in the mid-90s, but you quietly read transcribed messages instead.

We usually focus on augmented reality here, but when something important in VR happens, we highlight it as part of the overall immersive computing story.

After tapping Nvidia for its first AR headset, Magic Leap is calling in reinforcement for its future enterprise-focused efforts.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

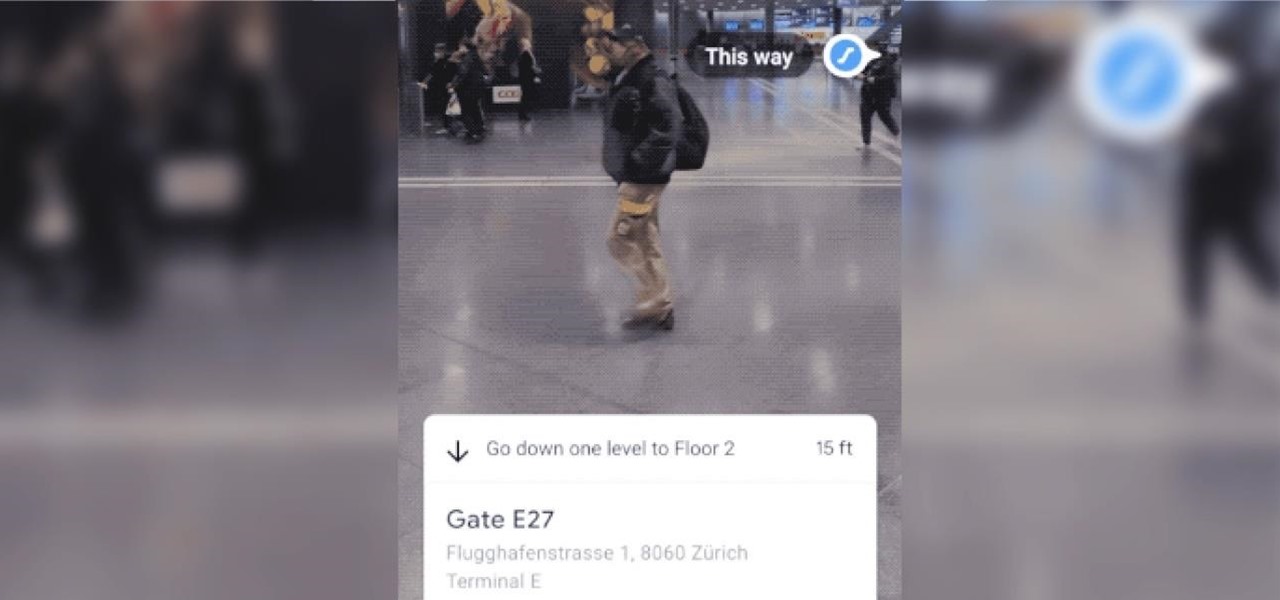
The AR walking navigation feature in Google Maps, which is arguably one of the most useful mobile augmented reality to available to consumers, is about to get even more indispensable for travelers.

While Apple has been rather secretive about its work on AR wearables (despite the abundance of leaks revealing details about their unannounced devices), Facebook has been rather chatty about its plans for smartglasses.

After the mobile augmented reality platforms of ARKit and ARCore moved Google's previously groundbreaking Project Tango (the AR platform that gave us the first smartphones with depth sensors) into obsolescence in 2018, we've seen a bit of a resurgence of what was then a niche component for flagship devices.

Now that 3D display maker Looking Glass Factory is closing in on $2.2 million raised in its crowdfunding campaign for the consumer-grade Looking Glass Portrait device, the company now has a 3D content generator to go with it.

This year, as part of the Next Reality 30, in partnership with Snap, we're spotlighting an up-and-coming innovator in augmented reality. Specifically, we were searching for an independent developer or creator who embodies the bleeding edge spirit of AR and its ability to leverage machine learning. This year's honoree is Aidan Wolf.

Your iPhone's Voice Memos app is an easy tool for quickly recording lectures at school, jam sessions at the studio, or just verbal notes to yourself. While it's a straightforward app, there are several hidden features you might not know about that can improve the quality of your recordings.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.