Socket programming in Unix allows multiple computer programs to "talk" to each other in the form of open "pipes". This is used in many popular programs for the Linux system (see any distribution). This how-to is created to understand the simple creation of a socket and what the various parts of the call mean.

its essentually a rube goldberg machine of the jackass cast. such as preston getting feathers (big chicken) and getting launched into a bucket of eggs(raw) that has a switch that launches wee man(bungie cord/surgical rubber cording) into a foam filled trash ben (huge one that you rent) he musty then climb out of it hop on a minimoto throwing a baseball at a button that drops england threw a trap door into a room of mousetraps. he has to run to the otherside of the room to hit a switch. i unde...

Run up to people and try to convince them that you are from the future and if they do not come with you then they're life is at severe risk. Throw in some crazy outfits and "evil" people from the future chasing you. It wouldn't hurt to get some fuckin explosions to make it seen legit. Now, if you've got them semi convinced, tell them they must come to the future with you and get into a time machine with them and then when your all in there it will be shaking and what not to give it the full e...

Label Profile: Night-People [Night-People founder Shawn Reed, playing live in Montreal as Wet Hair]

If you ever wondered how to keep your car looking great and protect the paint for years to come, read on.

so victim gets in the shower. person locks/blocks them in the shower. victim does not know they are locked in. let victim get all wet and fill the shower up with a bit of water. (before victim gets in shower) hook up a stun gun, or some other low voltage torture machine to the drain of show (which is usually metal). so, victim is stuck in shower, soaking wet, naked, water at the bottom of the tub, turn on electricity, watch the fun.

A press release should be about news. It should have a sense of urgency about it and grab the reader’s attention from the outset. A good press release must quickly answer the journalist’s immediate questions:

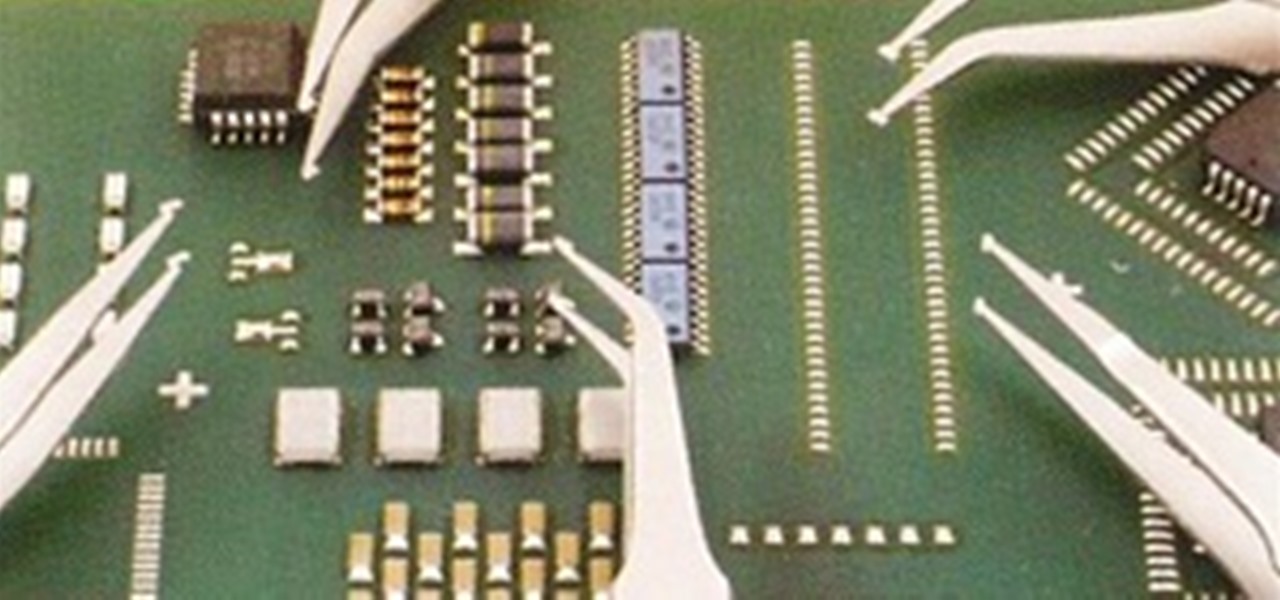
Whenever we make a homemade circuit, we use what are called through-hole components. Any components with long metal leads is a through-hole component. They are great for soldering to, but it's tough to fit enough through-hole resistors and capacitors into a smartphone. To get those last microns, we have surface-mount components for SMDs (surface-mount devices). These are all of those teeny, tiny things you see when you crack open your digital camera or laptop case.

Sometimes a simple drowning trap is too boring, and you want something that's a little more stylish and exciting. That's where this trap comes in!

Fans of Doctor Who know that the sonic screwdriver is the ultimate tool. It can unlock doors, turn on lights, detect life forms, solder wires, and sabotage weapons.

Microcontrollers are great. You can do anything from water your garden to catch wildlife trash diggers in the act—and on the cheap. I prefer to use the Arduino microcontroller because of the large and helpful community built around the website. Though it is my favorite, there are some drawbacks to using an Arduino board in every project. It gets expensive, the board can take up too much space, and the rat's nest of breadboard wires are a pain to repair.

I think it's fair to say that every maker yearns for a 3D printer. You can replace circuit board connectors, fix your glasses, create ski grips, and make whole machines out of printed plastic parts—even a 3D printer. But without a 3D printer on hand, you can always resort to Sugru.

If you are a pet owner, going on vacation can be stressful. Usually, you need a friend or neighbor to come over everyday and feed your pets. However, by enslaving robots you can keep your pet happy and enjoy a stress-free holiday.

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

TOP MOVIES 2011 The Artist (2011)

Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read online articles about elliptic curve cryptography applications to C++? Well, then this article is for you!
Yes it’s the 21st century and yes, everyone’s busy, everyone’s connected. Accept it. Move on. Be happy.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

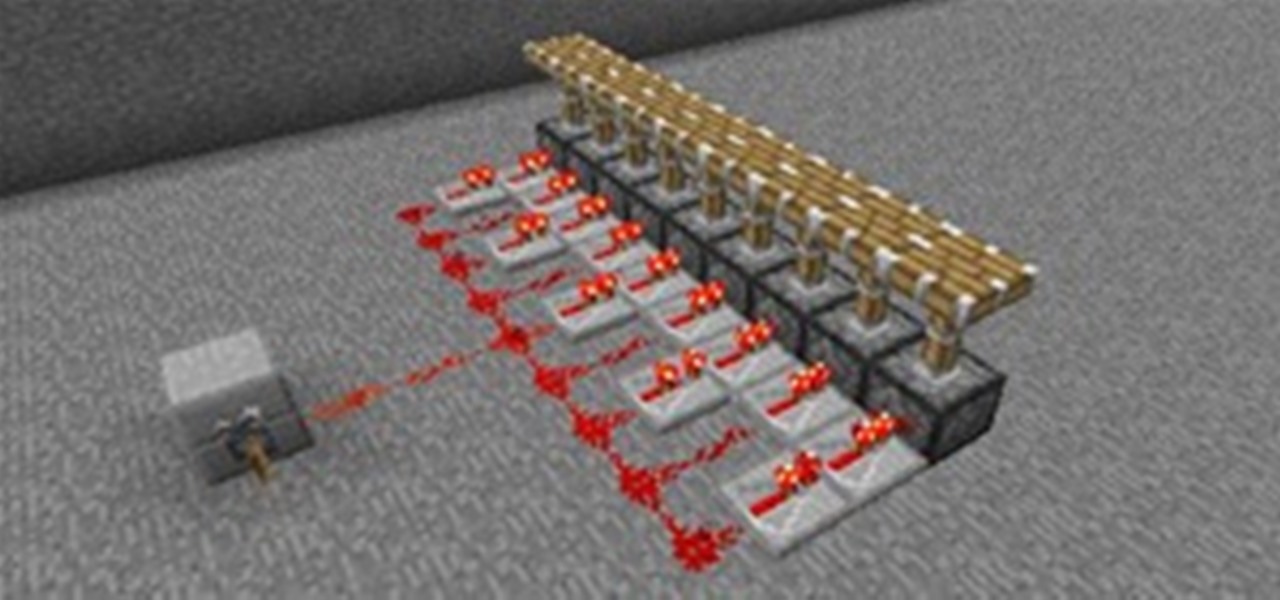
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Real time redstone clocks are a marvel of redstone technology. Not only can they keep track of time, they are capable of powering other more complicated redstone machines. Regardless of whether a redstone clock runs a ten second or twenty-four hour time span, they operate on the same principles, which can be easy and straightforward to understand.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. As we all know, redstone can be a very useful tool for make basic things in Minecraft more complex and intricate. For beginners to redstone, today's article will give you a basic understanding of how it functions, as well as its many uses.

Overclocking is quite an awesome thing. When computer components are designed, they are made to run at a certain speed, otherwise known as their clock and bus speeds. These limits are not actually limits. You can overclock components, which essentially makes them go faster than their set limitations. This can save you a lot of cash when newer components come out and you don't have enough money to upgrade. However, when you overclock components, you must be careful and make sure that the machi...

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Are you finding that the Google+ features you've been waiting for are still not rolling out quickly enough for you? Although we've provided many solutions to Google+ issues with different Chrome extensions, it still seems like it's not enough. Now that we've been using Google+ for almost two months, our priorities have changed, and we're finding that we want and need different extensions to make Google+ work better. From filtering to circles, these Google+ Chrome extensions will solve many of...

Deep in their heart of hearts, most Americans dream of having their car festooned with missile launchers and machine guns. Anyone who cuts them off or looks at them funny in traffic could be dispensed with quick and extreme justice, leaving a real-life James Bond and his passengers free to pursue their American dreams faster than everyone else. Racing games and shooting games are among the two most popular types of video games. So why aren't there more games where one can race cars and shoot ...

There's no doubt about it—the most elite military force in the United States is hands down, the Navy SEALs. They can operate at sea, in the air and on land, and their ability to conduct missions underwater separates them from most other military units in the world. They've fought in World War II, Vietnam, Granada, Afghanistan and Iraq, but have gained some serious hype in recent years thanks to SEAL Team Six, aka DEVGRU, aka NSWDG, who saved Captain Richard Phillips from Somali Pirates in 200...

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

A woman from space that who has been dead hundreds of years has been resurrected on the internet and you're the IT assigned to fight the viruses attacking her. Child of Eden is a mesmerizing musical game, with fluid animations, great game play, and lots of replay ability.

I love my laptop. It goes wherever I go. Unfortunately, that means that it also gets pretty grubby after a while. The screen gets dusty. The frame gets smudgy. The spaces between the keys fill up with crumbs of questionable origins. And my desktop? That thing is a dust bunny magnet.

In 2007, Nintendo introduced the world to motion control video games with the Wii. Microsoft and Sony built on Nintendo's phenomenal success and released their own motion control products for the XBox 360 and Playstation 3 late in 2010: the Kinect and the Move. The Move is basically an improved Wiimote that looks like a sci-fi Harry Potter wand, but the Kinect just might be the most important video game peripheral of all time.

Guiding internet users to useful content is one of the most lucrative businesses in the world. This process is called aggregation. Google and other search engines form the top of the food chain, aggregating all of the content on the web in response to queries. There are all sorts of other important aggregators though, and you probably use at least one every day: Fark and Reddit for web content, Rotten Tomatoes for movie reviews, and Metacritic for a variety of media, but most importantly, vid...

No time for elaborate practical jokes this April Fool's? Not a problem, it's 2011—meaning, apps can do just about anything these days. Measure beauty, check for STDs, even fix late night drunken social media stupidity. So why not pranks? Below, 10 digital solutions for your April Fool's Day wickedness.

In Google definitions a macro is defined as "a single computer instruction that results in a series of instructions in machine language". Basically a macro is a programming script that tells the computer what to do. You can tell a computer (via a macro) to move a mouse, click, type or do any task that a computer can do with automation. There are also many (primitive) computer viruses that are coded entirely in a macro script. There are many ways to create a macro script but I will only go ove...