
If you've ever wondered how to resize a T-Shirt to a smaller perfect fit, then follow these simple steps presented by Stacey from Sewing Republic. To shrink down your T-Shirt, follow theses steps: You will need an oversized shirt, a smaller shirt to use as a pattern and your sewing machine. 1. Turn both shirts inside out, and lay the fitted shirt on top. 2. Fold the sleeves back and pin the shirts together. 3. Trace around the fitted shirt with a fabric marking pen. Add 1/2 inch for your seam...

To make a hollow clay bell pepper, you will first need four thin strips of aluminum foil. Roll each one into a tiny, thin strip. You will also need pearlized white clay rolled out very thin (number seven on a pasta machine), and rolled out green, red, or yellow clay (number four on a pasta machine). Take your four strips of tin foil and line the up on one end placing them together in a bundle. Place on the white clay and the clay around it one time, remove the excess. Use your fingers to make...

Our instructor will choose set 2, 6 and 8 to show you what the company offers. On the wrappers are pictures of the types of beads possible with each set. She will create from set 2 today, which makes oval beads. Inside of the packages, such as this package which holds set 2 are several items. First is the thin metal pins or rods that can go into the baking oven with the polymer clay molded around them. Next, two pieces for the mold, a bottom and top that fit together with grooves. There are a...
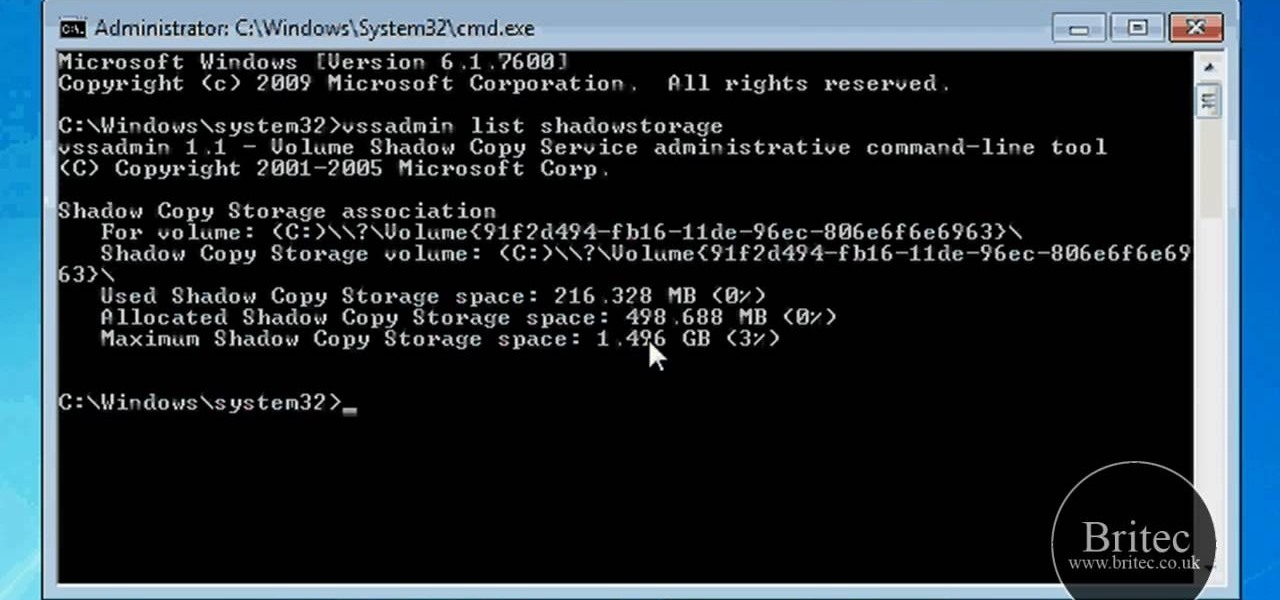
Is your computer getting up in its years and running slower than when you first purchased it? Your problem may lie in the machine's System Volume Information. Watch this video to see how to reclaim or resize disk space from SVI.

Most use wireless computer mice these days for their computers, but there are still people stuck on wired optical mice, especially in an office environment. Those people are our targets. As pranking someone's computer may be frowned on, peripherals are fair game, and this prank from Kipkay takes their wired optical computer mouse and turns it into a foul-smelling smoke machine.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Your ironing skills are rusty, and so is your iron. Now you’ve got rust stains on your blouse. What to do?

You can learn to confidently and accurately sew a straight seam. You Will Need

Learn to please a true coffee connoisseur with a hand-crafted caffe macchiato. Watch this recipe video to learn how to make your own Caffe Macchiato at home.

Become your own favorite barista by learning to create an authentic cappuccino at home. This Howcast guide demonstrates and provides a recipe for homemade cappuccinos.

Make your coffee maker sparkle with these easy tips. This Howcast video presents a helpful guide on cleaning your coffee maker.

Learn how to do Gravitron speed wide grip pull ups. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do Gravitron wide grip drop set pull ups. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do wide grip pull ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do speed tricep dips on a Gravitron. Presented by Real Jock Gay Fitness Health & Life. enefits

Learn how to do power press single leg presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do cable bar pull down triceps. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do single arm rope press downs. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do a single cable scissor squat and row. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do single cable squats and rows. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do speed single cable reverse flys. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do tube rows. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do alternating T push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

Ask 100 chefs what the most important tool in their kitchen is, and you'll get 100 chefs saying the exact same thing: their set of knives. For home cooks and professional chefs alike, nothing is more important (or exciting) than a good knife. A good knife allows you to work more quickly, more efficiently, more consistently, and more safely. And best of all, they're just a lot of fun.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Your car is a well-oiled machine...when you first get it. Once the new car smell wears off and the excitement of driving the latest and greatest model lessens, car maintenance becomes a chore and some of us even forget to do it regularly.

Altair from Assassin's Creed is an incredibly stylish and well-realized character, which makes him a perfect costume choice for Halloween or a cosplay convention. Watch this video to learn how to sew the red sash for an Altair costume quickly and easily.

Altair is one of the sexiest video games characters your could be this Halloween or at your next cosplay convention. The Dutchman who made this video clearly is devoted to the character, and in this video you'll learn how to make a perfect Altair under tunic for your costume. Watch this video before you start to learn how to make the template.

In this video, we learn how to reconstruct a t-shirt into an off the shoulder top. First, take a large shirt of your choice color and cut along the line on the shoulder, leaving a 1/4" seam allowance. Next, roll the hem and sew with a sewing machine. Next, cut a strap 4" wide and fold in half, then sew along the edge. After this, use a safety pin to pin one side to the shirt and then to the other side of the shirt. After these are secure, draw marks along the neck line of the shirt. Cut out t...

Create your own macro lens using the standard 50 mm lens that is shipped with your Digital SLR camera.

In this tutorial, we learn how to make a hedgehog plushy. First, choose a fabric to use, then cut out the shape of it. Once you have done this, cut it out again and pin the two pieces of fabric together. After this, use a sewing machine to sew all of the sides together, leaving a hole in the bottom. Now, turn the hedgehog inside out and then iron him flat. Place some stuffy cotton into the plushy until it is as full as you would like it. Then, sew the hole together so none of the stuffing can...

Homer Simpson would have an absolute fit over this delicious-looking kawaii donut pillow. Embellished with a thick layer of strawberry frosting and then topped lightly with candy-colored sprinkles, this pretty donut looks almost good enough to eat.

Suspension training offers an unparalleled way to train your entire upper body, from your pecs to your core to your triceps and biceps. So if you're lucky enough to have the TRX Suspension Training machine at home, or have one at the gym, then try commiting yourself to actually using it once in a while.

We know those big exercise machines at the gym can be intimidating, but the next time you hit the gym you should consider making friends with one of them because they offer a resistance (often adjustable) that you can't get with workout tapes at home.

Kipkay is at it again with his pranks. In this video, he shares four fun and easy pranks that anyone can do to drive their friends (or victims) crazy! Their all very simple. They include a cell phone prank, a floss prank, and more!









































